环境说明
本实验使用华为eNSP,主要由3台USG6000V防火墙来完成实验内容
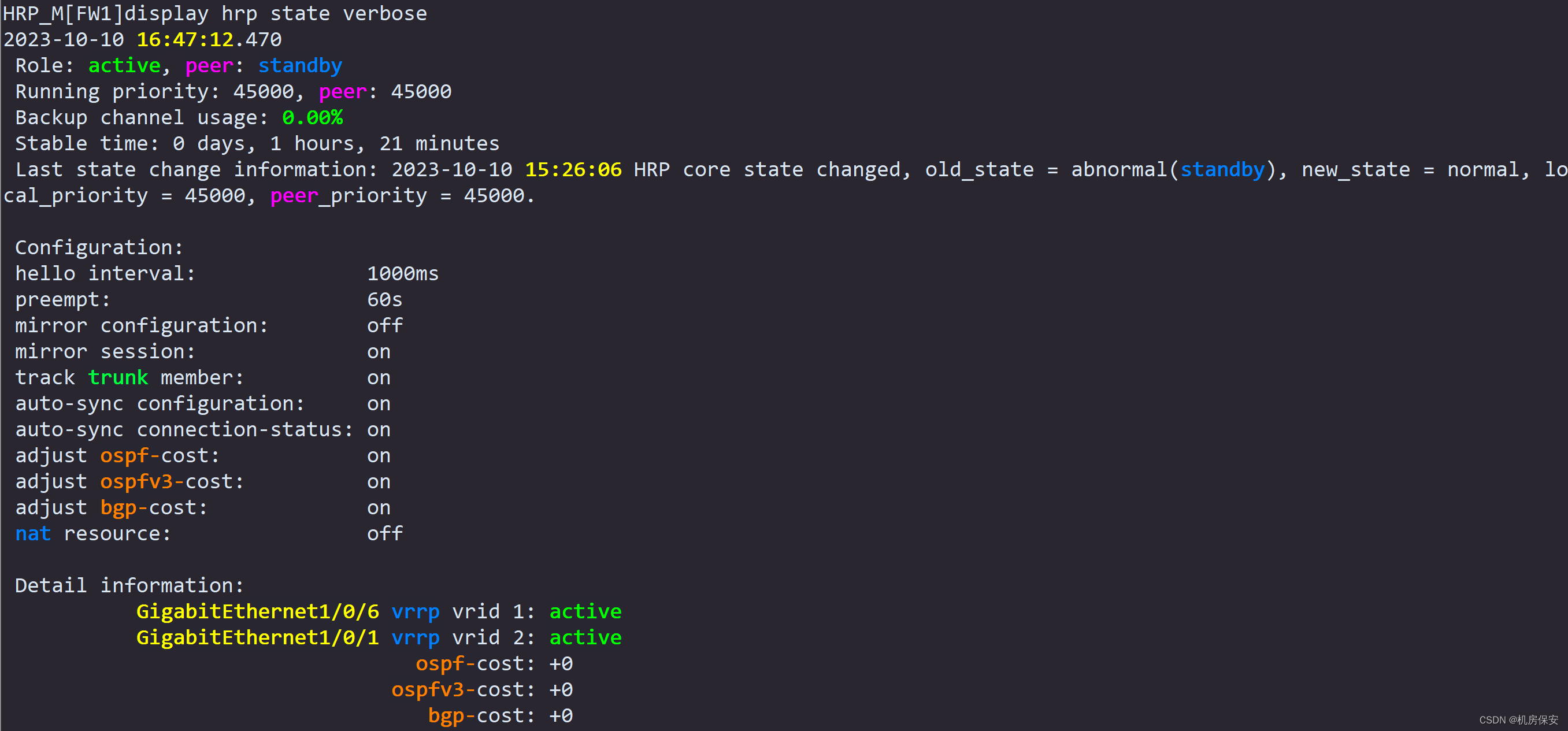
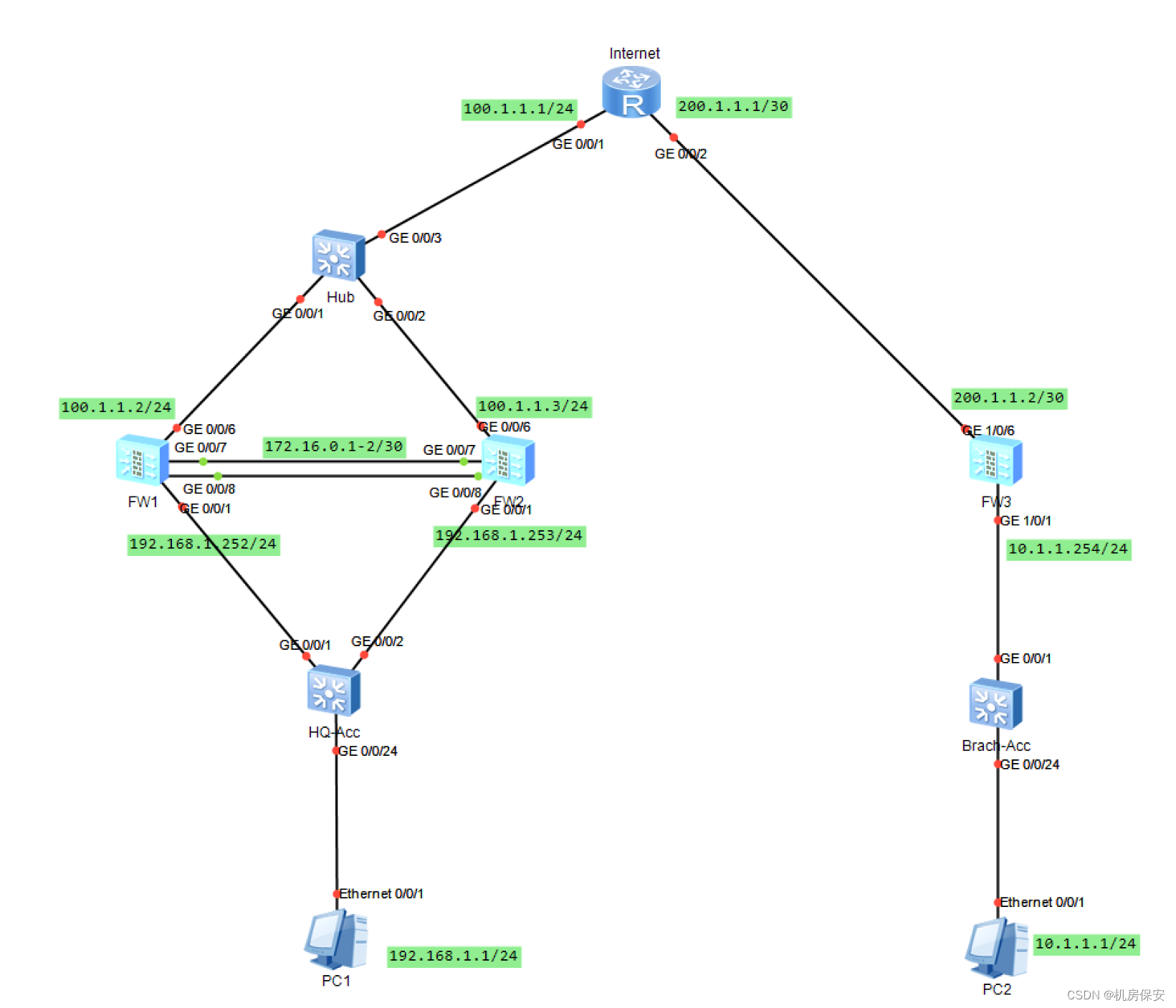
总部两台防火墙配置HRP以及VRRP,使用VRRP虚拟地址与分部建立IPSec隧道
拓扑图
配置过程
一、IP地址省略
二、安全区域配置
#FW1
[FW1]firewall zone untrust
[FW1-zone-untrust]add interface GigabitEthernet 1/0/6
[FW1]firewall zone trust
[FW1-zone-trust]add interface GigabitEthernet 1/0/1
[FW1]firewall zone dmz
[FW1-zone-dmz]add interface Eth-Trunk 0
#FW2
[FW2]firewall zone untrust
[FW2-zone-untrust]add interface GigabitEthernet 1/0/6
[FW2]firewall zone trust
[FW2-zone-trust]add interface GigabitEthernet 1/0/1
[FW2]firewall zone dmz
[FW2-zone-dmz]add interface Eth-Trunk 0
#FW3
[FW3]firewall zone untrust
[FW3-zone-untrust]add interface GigabitEthernet 1/0/6
[FW3]firewall zone trust
[FW3-zone-trust]add interface GigabitEthernet 1/0/1三、静态路由配置
#FW1
[FW1]ip route-static 0.0.0.0 0 100.1.1.1
#FW2
[FW2]ip route-static 0.0.0.0 0 100.1.1.1
#FW3
[FW3]ip route-static 0.0.0.0 0 200.1.1.1四、总部VRRP配置
FW1
[FW1]interface GigabitEthernet 1/0/6
[FW1-GigabitEthernet1/0/6]vrrp vrid 1 virtual-ip 100.1.1.10 active
[FW1]interface GigabitEthernet 1/0/1
[FW1-GigabitEthernet1/0/1]vrrp vrid 2 virtual-ip 192.168.1.254 active
#FW2
[FW2]interface GigabitEthernet 1/0/6
[FW2-GigabitEthernet1/0/6]vrrp vrid 1 virtual-ip 100.1.1.10 standby
[FW2]interface GigabitEthernet 1/0/1
[FW2-GigabitEthernet1/0/1]vrrp vrid 2 virtual-ip 192.168.1.254 standby 五、总部HRP配置
#FW1
[FW1]hrp interface Eth-Trunk 0 remote 172.16.0.2
[FW1]hrp enable
[FW1]hrp mirror session enable
#FW2
[FW2]hrp interface Eth-Trunk 0 remote 172.16.0.1
[FW2]hrp enable
[FW2]hrp mirror session enable
[FW2]hrp standby-device六、安全策略配置
#FW1
[FW1]interface GigabitEthernet 1/0/1
[FW1-GigabitEthernet1/0/1]service-manage ping permit
[FW1]interface GigabitEthernet 1/0/6
[FW1-GigabitEthernet1/0/6]service-manage ping permit
[FW1]security-policy
[FW1-policy-security]rule name PC_TO_FW
[FW1-policy-security-rule-PC_TO_FW]source-zone trust
[FW1-policy-security-rule-PC_TO_FW]destination-zone local
[FW1-policy-security-rule-PC_TO_FW]source-address 192.168.1.1 mask 255.255.255.0
[FW1-policy-security-rule-PC_TO_FW]destination-address 192.168.1.254 mask 255.255.255.0
[FW1-policy-security-rule-PC_TO_FW]action permit
[FW1-policy-security]rule name FW_TO_ISP
[FW1-policy-security-rule-FW_TO_ISP]source-zone local
[FW1-policy-security-rule-FW_TO_ISP]destination-zone untrust
[FW1-policy-security-rule-FW_TO_ISP]source-address 100.1.1.10 mask 255.255.255.0
[FW1-policy-security-rule-FW_TO_ISP]destination-address 100.1.1.1 mask 255.255.255.255
[FW1-policy-security-rule-FW_TO_ISP]action permit
[FW1-policy-security]rule name HQFW_TO_BranchFW
[FW1-policy-security-rule-HQFW_TO_BranchFW]source-zone local
[FW1-policy-security-rule-HQFW_TO_BranchFW]source-zone untrust
[FW1-policy-security-rule-HQFW_TO_BranchFW]destination-zone local
[FW1-policy-security-rule-HQFW_TO_BranchFW]destination-zone untrust
[FW1-policy-security-rule-HQFW_TO_BranchFW]source-address 100.1.1.0 mask 255.255.255.0
[FW1-policy-security-rule-HQFW_TO_BranchFW]source-address 200.1.1.2 mask 255.255.255.255
[FW1-policy-security-rule-HQFW_TO_BranchFW]destination-address 100.1.1.0 mask 255.255.255.0
[FW1-policy-security-rule-HQFW_TO_BranchFW]destination-address 200.1.1.2 mask 255.255.255.255
[FW1-policy-security-rule-HQFW_TO_BranchFW]action permit
[FW1-policy-security]rule name HQPC_TO_BranchPC
[FW1-policy-security-rule-HQPC_TO_BranchPC]source-zone trust
[FW1-policy-security-rule-HQPC_TO_BranchPC]source-zone untrust
[FW1-policy-security-rule-HQPC_TO_BranchPC]destination-zone untrust
[FW1-policy-security-rule-HQPC_TO_BranchPC]destination-zone trust
[FW1-policy-security-rule-HQPC_TO_BranchPC]source-address 192.168.1.0 mask 255.255.255.0
[FW1-policy-security-rule-HQPC_TO_BranchPC]source-address 10.1.1.0 mask 255.255.255.0
[FW1-policy-security-rule-HQPC_TO_BranchPC]destination-address 192.168.1.0 mask 255.255.255.0
[FW1-policy-security-rule-HQPC_TO_BranchPC]destination-address 10.1.1.0 mask 255.255.255.0
[FW1-policy-security-rule-HQPC_TO_BranchPC]action permit
#FW3
[FW3]interface GigabitEthernet 1/0/1
[FW3-GigabitEthernet1/0/1]service-manage ping permit
[FW3]interface GigabitEthernet 1/0/6
[FW3-GigabitEthernet1/0/6]service-manage ping permit
[FW3]security-policy
[FW3-policy-security]rule name PC_TO_FW
[FW3-policy-security-rule-PC_TO_FW]source-zone trust
[FW3-policy-security-rule-PC_TO_FW]destination-zone local
[FW3-policy-security-rule-PC_TO_FW]source-address 10.1.1.1 mask 255.255.255.255
[FW3-policy-security-rule-PC_TO_FW]destination-address 10.1.1.254 mask 255.255.255.255
[FW3-policy-security-rule-PC_TO_FW]action permit
[FW3-policy-security]rule name FW_TO_ISP
[FW3-policy-security-rule-FW_TO_ISP]source-zone local
[FW3-policy-security-rule-FW_TO_ISP]destination-zone untrust
[FW3-policy-security-rule-FW_TO_ISP]source-address 200.1.1.2 mask 255.255.255.255
[FW3-policy-security-rule-FW_TO_ISP]destination-address 200.1.1.1 mask 255.255.255.255
[FW3-policy-security-rule-FW_TO_ISP]action permit
[FW3-policy-security]rule name BranchFW_TO_HQFW
[FW3-policy-security-rule-BranchFW_TO_HQFW]source-zone local
[FW3-policy-security-rule-BranchFW_TO_HQFW]source-zone untrust
[FW3-policy-security-rule-BranchFW_TO_HQFW]destination-zone local
[FW3-policy-security-rule-BranchFW_TO_HQFW]destination-zone untrust
[FW3-policy-security-rule-BranchFW_TO_HQFW]source-address 100.1.1.0 mask 255.255.255.0
[FW3-policy-security-rule-BranchFW_TO_HQFW]source-address 200.1.1.2 mask 255.255.255.255
[FW3-policy-security-rule-BranchFW_TO_HQFW]destination-address 200.1.1.2 mask 255.255.255.255
[FW3-policy-security-rule-BranchFW_TO_HQFW]destination-address 100.1.1.0 mask 255.255.255.0
[FW3-policy-security-rule-BranchFW_TO_HQFW]action permit
[FW3-policy-security]rule name BranchPC_TO_HQPC
[FW3-policy-security-rule-BranchPC_TO_HQPC]source-zone trust
[FW3-policy-security-rule-BranchPC_TO_HQPC]source-zone untrust
[FW3-policy-security-rule-BranchPC_TO_HQPC]destination-zone trust
[FW3-policy-security-rule-BranchPC_TO_HQPC]destination-zone untrust
[FW3-policy-security-rule-BranchPC_TO_HQPC]source-address 10.1.1.0 mask 255.255.255.0
[FW3-policy-security-rule-BranchPC_TO_HQPC]source-address 192.168.1.0 mask 255.255.255.0
[FW3-policy-security-rule-BranchPC_TO_HQPC]destination-address 10.1.1.0 mask 255.255.255.0
[FW3-policy-security-rule-BranchPC_TO_HQPC]destination-address 192.168.1.0 mask 255.255.255.0
[FW3-policy-security-rule-BranchPC_TO_HQPC]action permit七、IPSec配置
(1)配置isakmp服务
#FW1
[FW1]ip service-set ISAKMP type object
[FW1-object-service-set-ISAKMP]service protocol udp source-port 500 destination-port 500
#FW3
[FW3]ip service-set ISAKMP type object
[FW3-object-service-set-ISAKMP]service protocol udp source-port 500 destination-port 500
(2)配置感兴趣流
#FW1
[FW1]acl 3000
[FW1-acl-adv-3000]rule permit ip source 192.168.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
#FW3
[FW3]acl 3000
[FW3-acl-adv-3000]rule permit ip source 10.1.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
(3)放行ISAKMP和ESP服务
#FW1
[FW1-policy-security]rule name HQFW_TO_BranchFW
[FW1-policy-security-rule-HQFW_TO_BranchFW]service ISAKMP
[FW1-policy-security-rule-HQFW_TO_BranchFW]service esp
[FW1-policy-security-rule-HQFW_TO_BranchFW]action permit
#FW3
[FW3-policy-security]rule name BranchFW_TO_HQFW
[FW3-policy-security-rule-BranchFW_TO_HQFW]service ISAKMP
[FW3-policy-security-rule-BranchFW_TO_HQFW]service esp
[FW3-policy-security-rule-BranchFW_TO_HQFW]action permit
(4)配置IPSec安全提议
#FW1
[FW1]ipsec proposal huawei
[FW1-ipsec-proposal-huawei]esp authentication-algorithm sha2-256
[FW1-ipsec-proposal-huawei]esp encryption-algorithm aes-256
#FW3
[FW3]ipsec proposal huawei
[FW3-ipsec-proposal-huawei]esp authentication-algorithm sha2-256
[FW3-ipsec-proposal-huawei]esp encryption-algorithm aes-256
(5)配置IKE提议
#FW1
[FW1]ike proposal 10
[FW1-ike-proposal-10]authentication-algorithm sha2-256
[FW1-ike-proposal-10]encryption-algorithm aes-256
[FW1-ike-proposal-10]authentication-method pre-share
#FW3
[FW3]ike proposal 10
[FW3-ike-proposal-10]authentication-algorithm sha2-256
[FW3-ike-proposal-10]encryption-algorithm aes-256
[FW3-ike-proposal-10]authentication-method pre-share
(6)配置IKE Peer
#FW1
[FW1]ike peer huawei
[FW1-ike-peer-huawei]pre-shared-key Huawei@123
[FW1-ike-peer-huawei]ike-proposal 10
#FW3
[FW3]ike peer huawei
[FW3-ike-peer-huawei]pre-shared-key Huawei@123
[FW3-ike-peer-huawei]ike-proposal 10
[FW3-ike-peer-huawei]remote-address 100.1.1.10
(7)HQ创建IPSec模板以及IPSec策略绑定模板,FW3创建IPSec策略
#FW1
[FW1]ipsec policy-template huawei 10
[FW1-ipsec-policy-templet-huawei-10]security acl 3000
[FW1-ipsec-policy-templet-huawei-10]proposal huawei
[FW1-ipsec-policy-templet-huawei-10]ike-peer huawei
[FW1]ipsec policy huawei1 10 isakmp template huawei
#FW3
[FW3]ipsec policy huawei 10 isakmp
[FW3-ipsec-policy-isakmp-huawei-10]security acl 3000
[FW3-ipsec-policy-isakmp-huawei-10]proposal huawei
[FW3-ipsec-policy-isakmp-huawei-10]ike-peer huawei
(8)公网口下发IPSec策略
#FW1
[FW1-GigabitEthernet1/0/6]ipsec policy huawei1
#FW3
[FW3]interface GigabitEthernet 1/0/6
[FW3-GigabitEthernet1/0/6]ipsec policy huawei八、现象验证
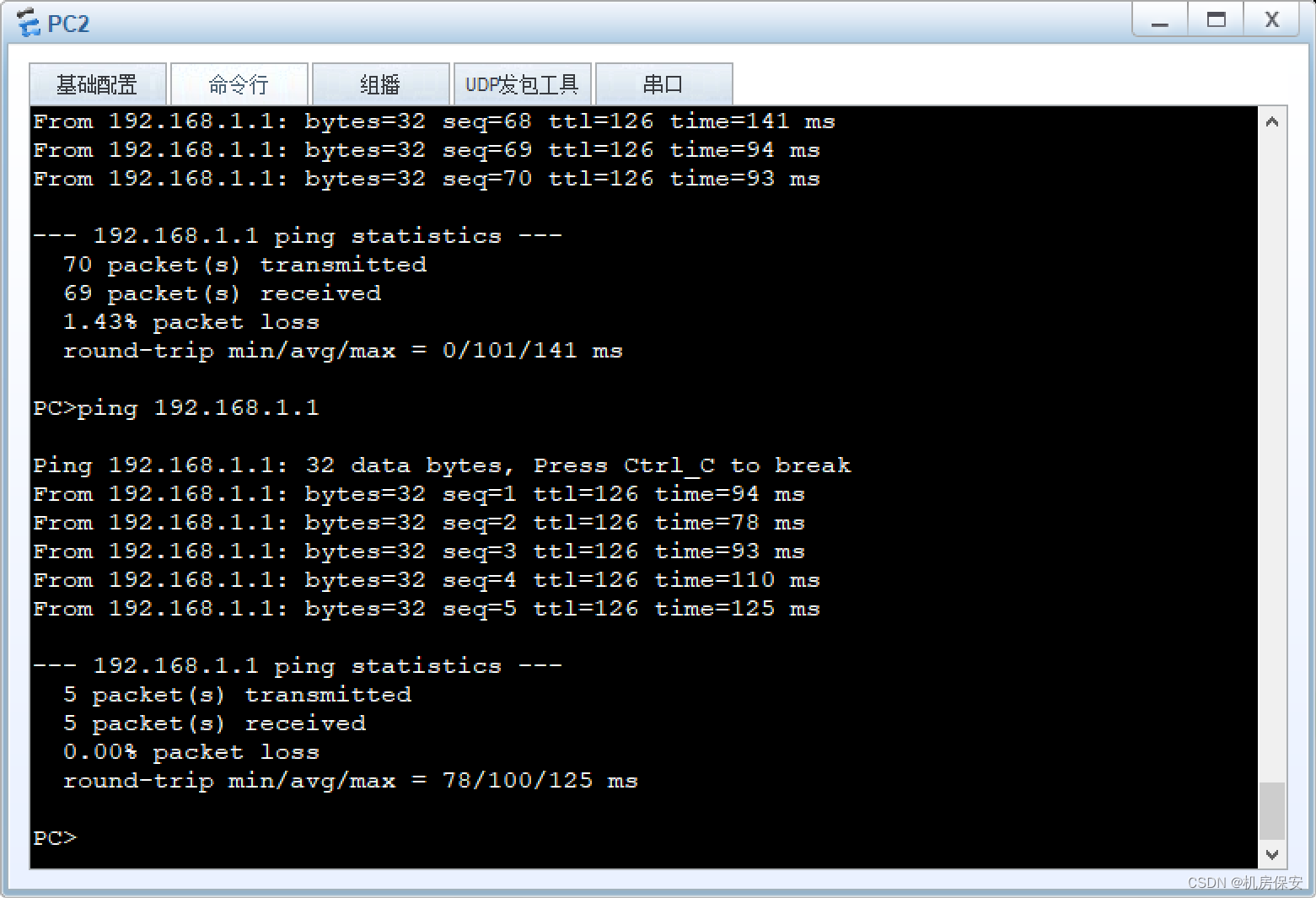
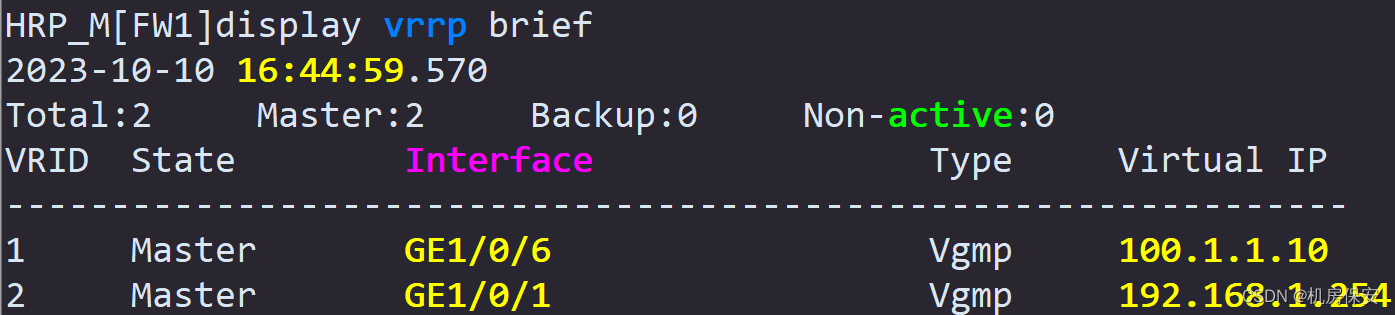
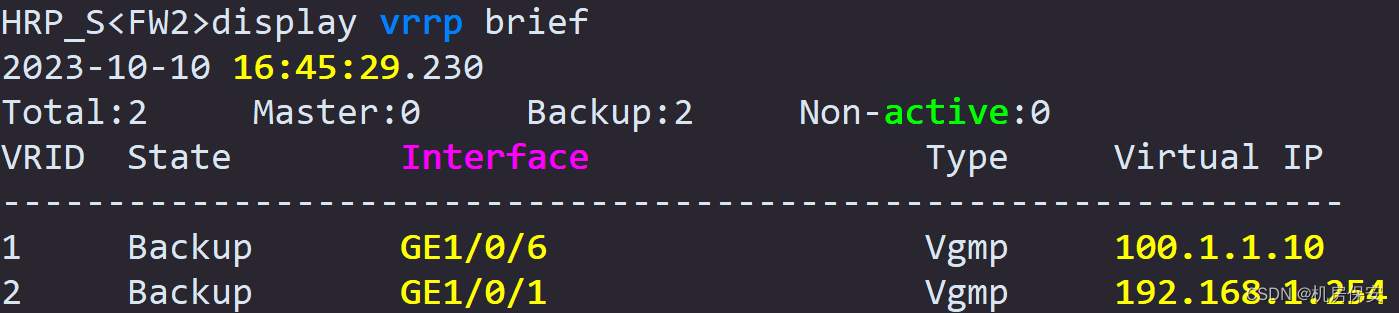
1、VRRP验证
2、HRP验证
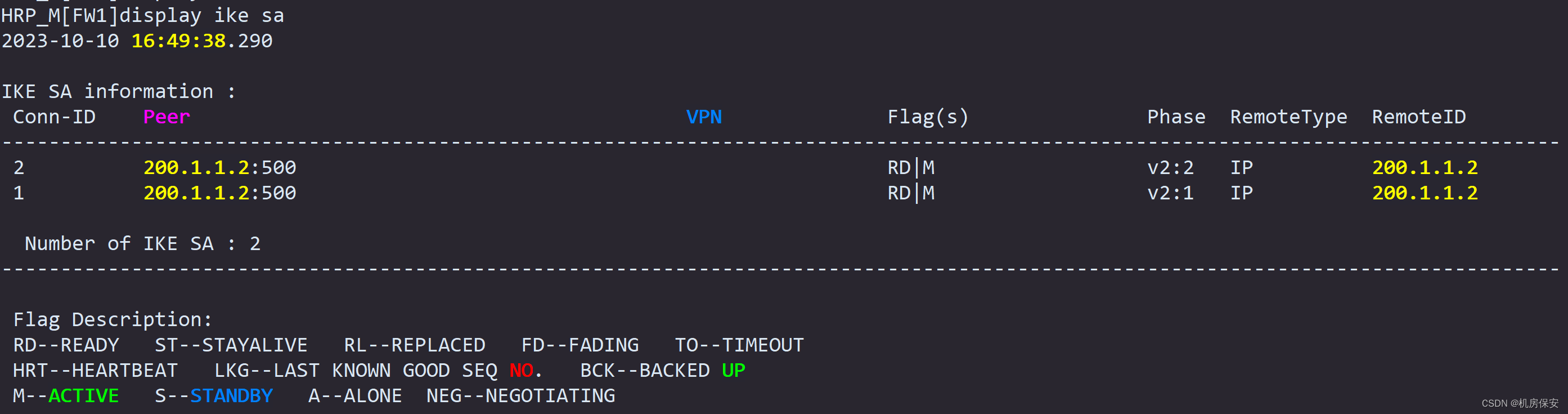
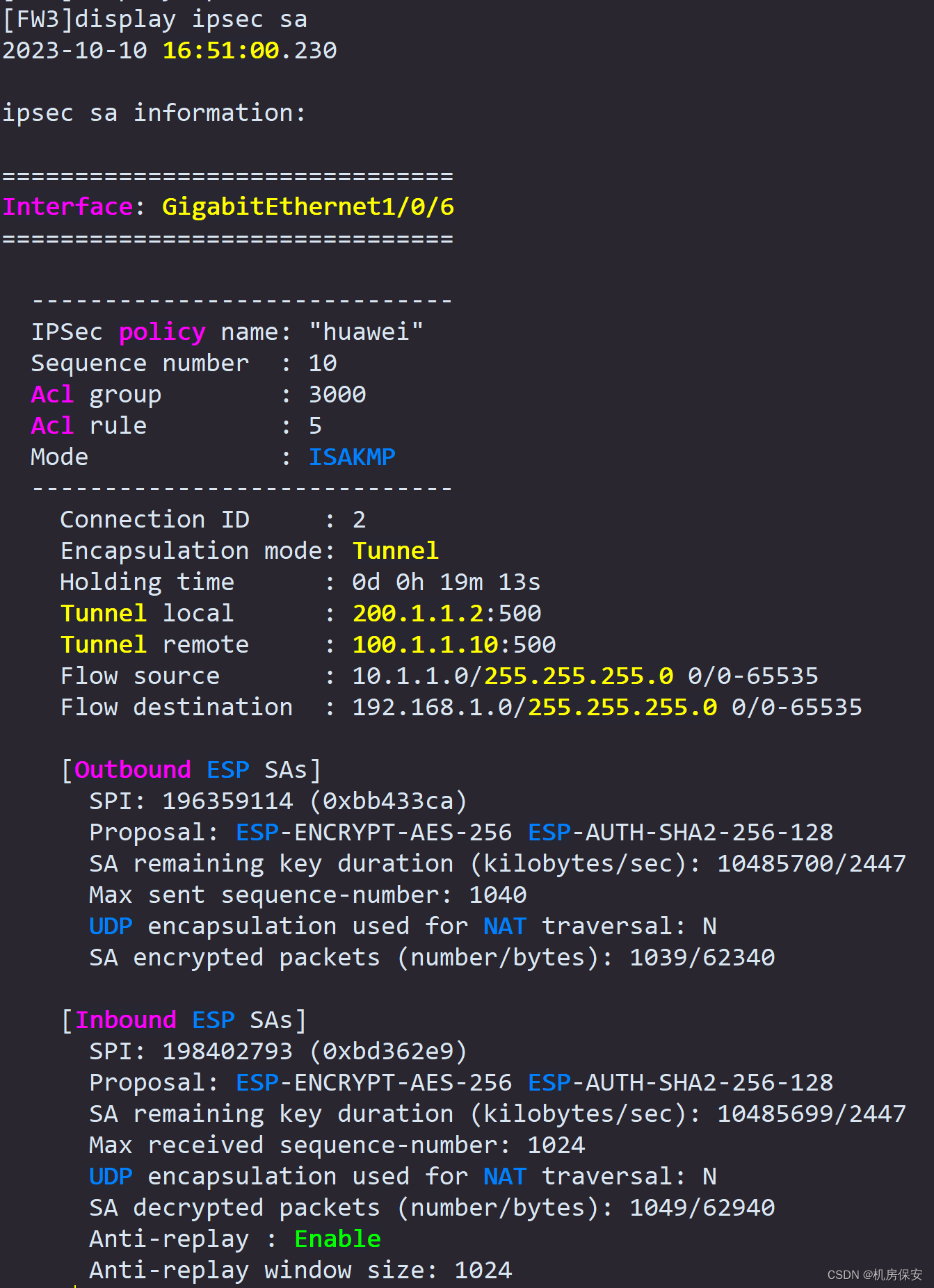
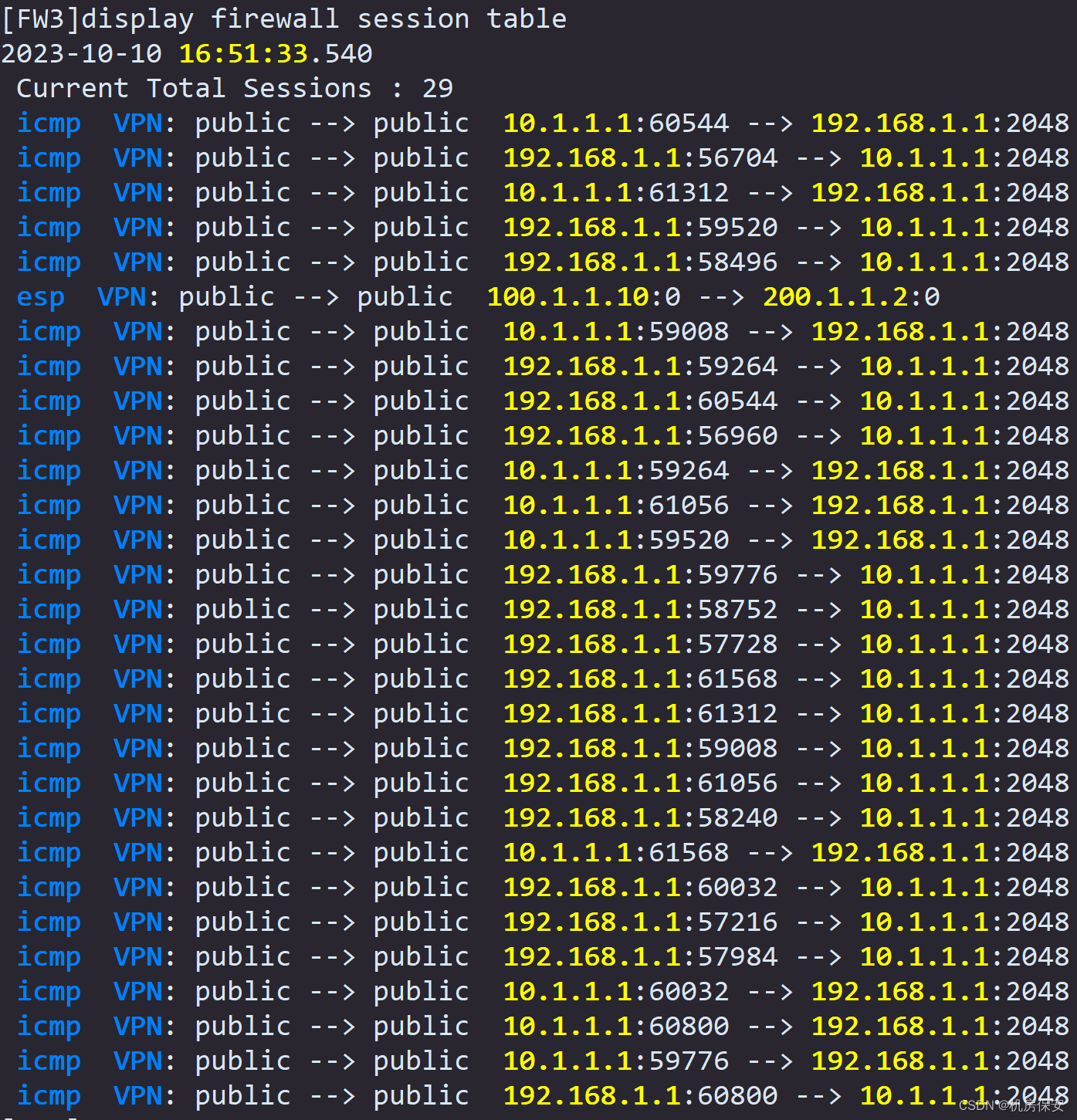
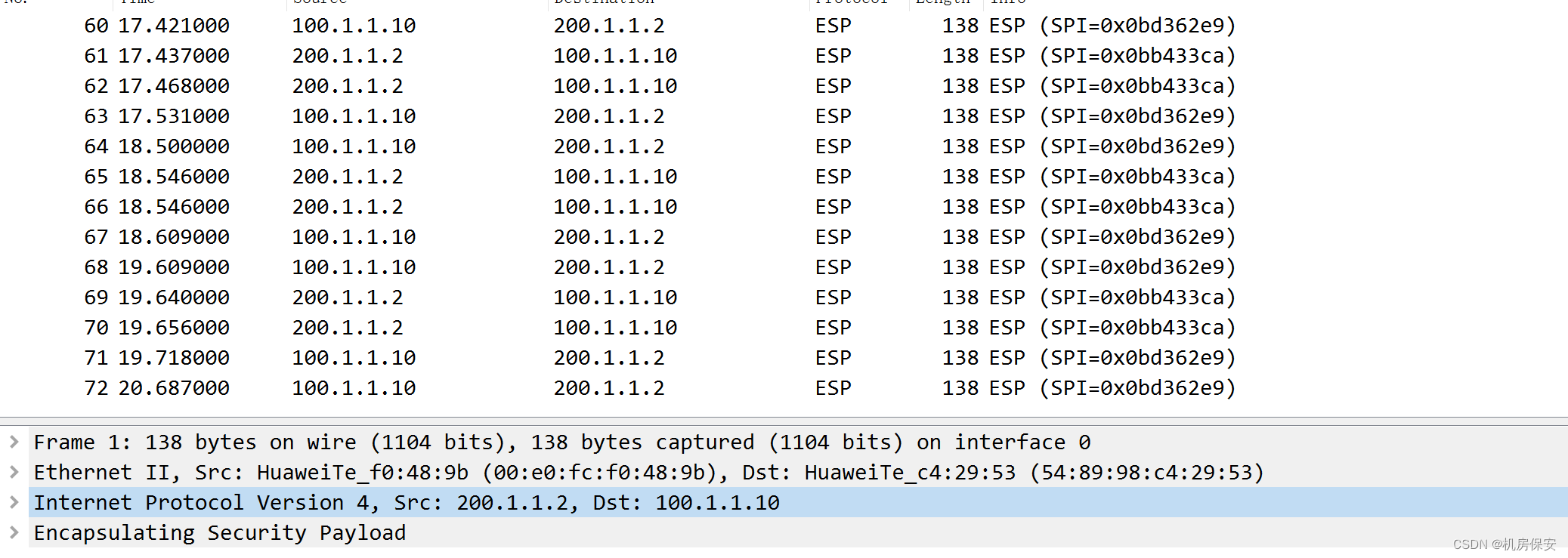
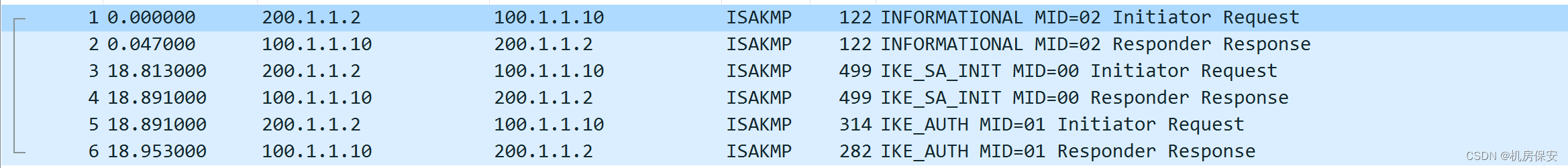
3、IPSec相关验证