目录
IPSEC介绍:ipsec是一种基于网络层,应用密码学的安全通信协议簇,目的是在网络层环境ipv4,ipv6提供灵活的安全传输服务。
ipsec vpn 基于ipsec构建在ip层实现的安全虚拟专用网。
实验拓扑:
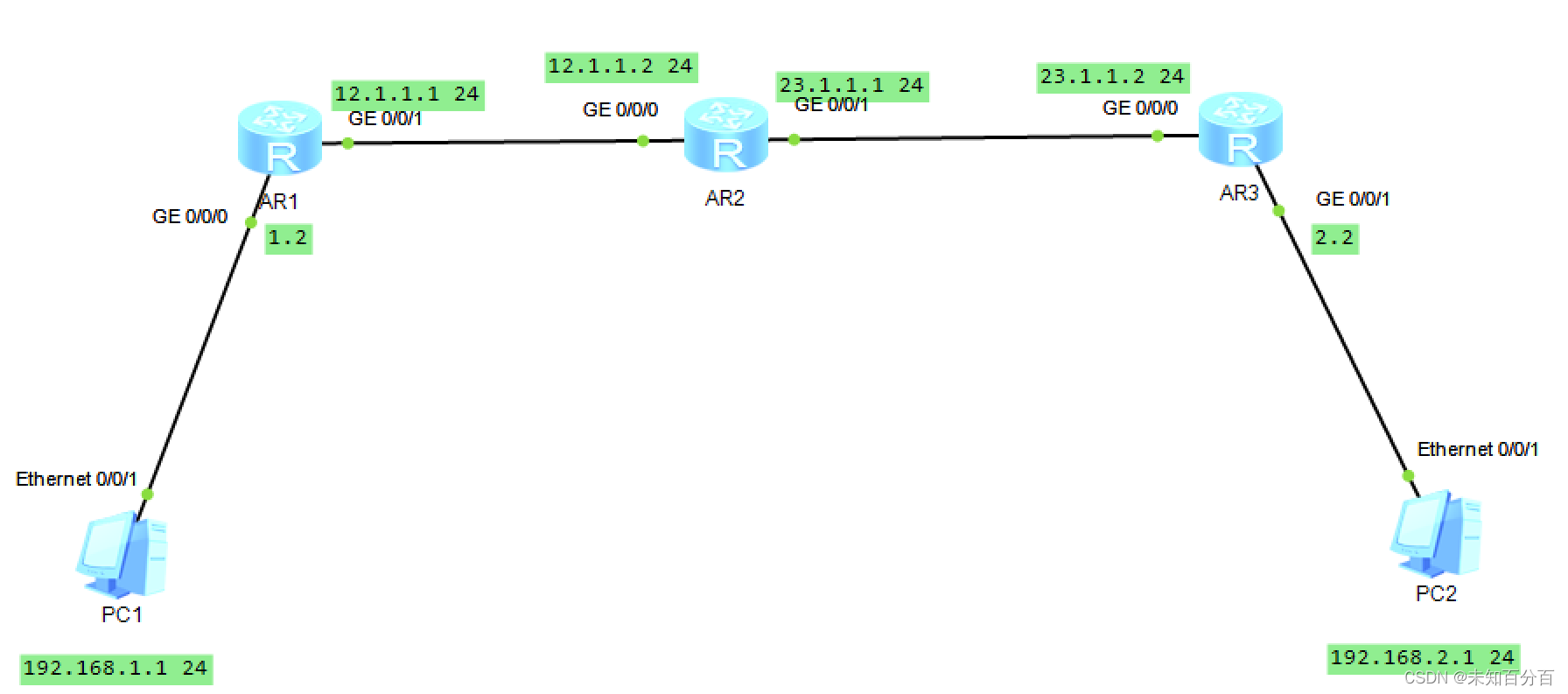
1、首先为各个接口配置ip(如图中)
2、实现公网互通
在r1上写一条缺省到r2:
[r1]ip route-static 0.0.0.0 0 12.1.1.2在r3上写一条缺省到r2:
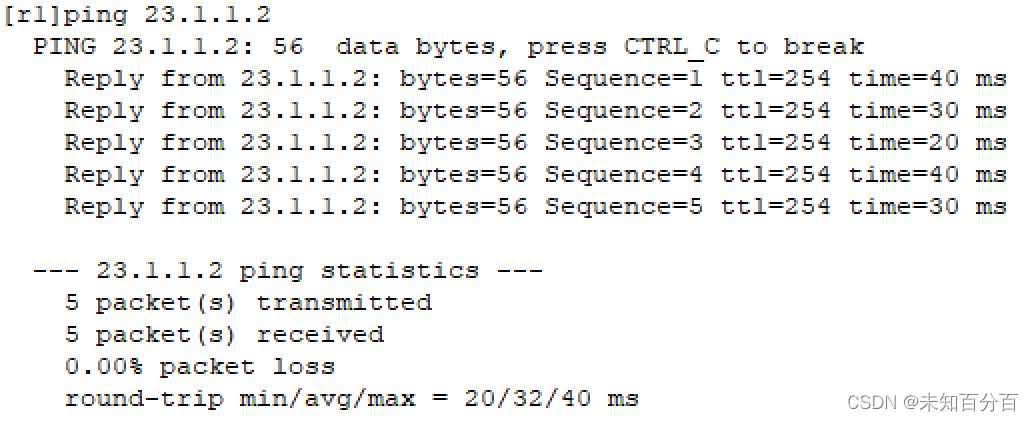
[r3]ip route-static 0.0.0.0 0 23.1.1.1 3、测试是否全网互通
4、R1配置
(1)ike sa第一阶段
[r1]ike proposal 1 编写提议名为 1
[r1-ike-proposal-1]encryption-algorithm aes-cbc-128 加密算法
[r1-ike-proposal-1]authentication-algorithm sha1 认证算法
[r1-ike-proposal-1]authentication-method pre-share 认证模式
[r1-ike-proposal-1]dh group2 DH算法
[r1-ike-proposal-1]sa duration 86400 时间(默认就是86400)
[r1-ike-proposal-1]q
[r1]ike peer jjj v1
[r1-ike-peer-jjj]pre-shared-key cipher 123456 预共享密钥
[r1-ike-peer-jjj]exchange-mode main 选择主模式
[r1-ike-peer-jjj]remote-address 23.1.1.2 对方的地址
[r1-ike-peer-jjj]ike-proposal 1 将前面写的提议关联(2)ipsec sa第二阶段
[r1]ipsec proposal jjj
[r1-ipsec-proposal-jjj]encapsulation-mode tunnel 封装模式设定为 隧道模式
[r1-ipsec-proposal-jjj]esp encryption-algorithm aes-128 加密算法
[r1-ipsec-proposal-jjj]esp authentication-algorithm sha1 认证模式
[r1-ipsec-proposal-jjj]q
[r1]acl 3000 高级acl
[r1-acl-adv-3000]rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168
.2.0 0.0.0.255 匹配流量
[r1]ipsec policy jjj 1 isakmp 新建一个策略 并且动态的
[r1-ipsec-policy-isakmp-jjj-1]proposal jjj 匹配proposal
[r1-ipsec-policy-isakmp-jjj-1]ike-peer jjj 匹配ike邻居
[r1-ipsec-policy-isakmp-jjj-1]security acl 3000 匹配3000流量
[r1-ipsec-policy-isakmp-jjj-1]pfs dh-group2 完美向前
(3)进入对应接口调用ipsec policy
[r1-GigabitEthernet0/0/1]ipsec policy jjj 5、R3配置
(1)第一阶段
[r3]ike proposal 1
[r3-ike-proposal-1]encryption-algorithm aes-cbc-128
[r3-ike-proposal-1]authentication-method pre-share
[r3-ike-proposal-1]authentication-algorithm sha1
[r3-ike-proposal-1]dh group2
[r3-ike-proposal-1]q
[r3]ike peer jjj v1
[r3-ike-peer-jjj]pre-shared-key cipher 123456
[r3-ike-peer-jjj]exchange-mode main
[r3-ike-peer-jjj]remote-address 12.1.1.1
[r3-ike-peer-jjj]ike-proposal 1(2)第二阶段
[r3]ipsec proposal jjj
[r3-ipsec-proposal-jjj]encapsulation-mode tunnel
[r3-ipsec-proposal-jjj]esp encryption-algorithm aes-128
[r3-ipsec-proposal-jjj]esp authentication-algorithm sha1
[r3]acl 3000
[r3-acl-adv-3000]rule permit ip source 192.168.2.0 0.0.0.255 destination 192.16
8.1.0 0.0.0.255
[r3]ipsec policy jjj 1 isakmp
[r3-ipsec-policy-isakmp-jjj-1]proposal jjj
[r3-ipsec-policy-isakmp-jjj-1]ike-peer jjj
[r3-ipsec-policy-isakmp-jjj-1]security acl 3000
[r3-ipsec-policy-isakmp-jjj-1]pfs dh-group2(3)接口调用
[r3-GigabitEthernet0/0/0]ipsec policy jjj6、测试
(1)首先在R2的0/0/0接口上进行抓包
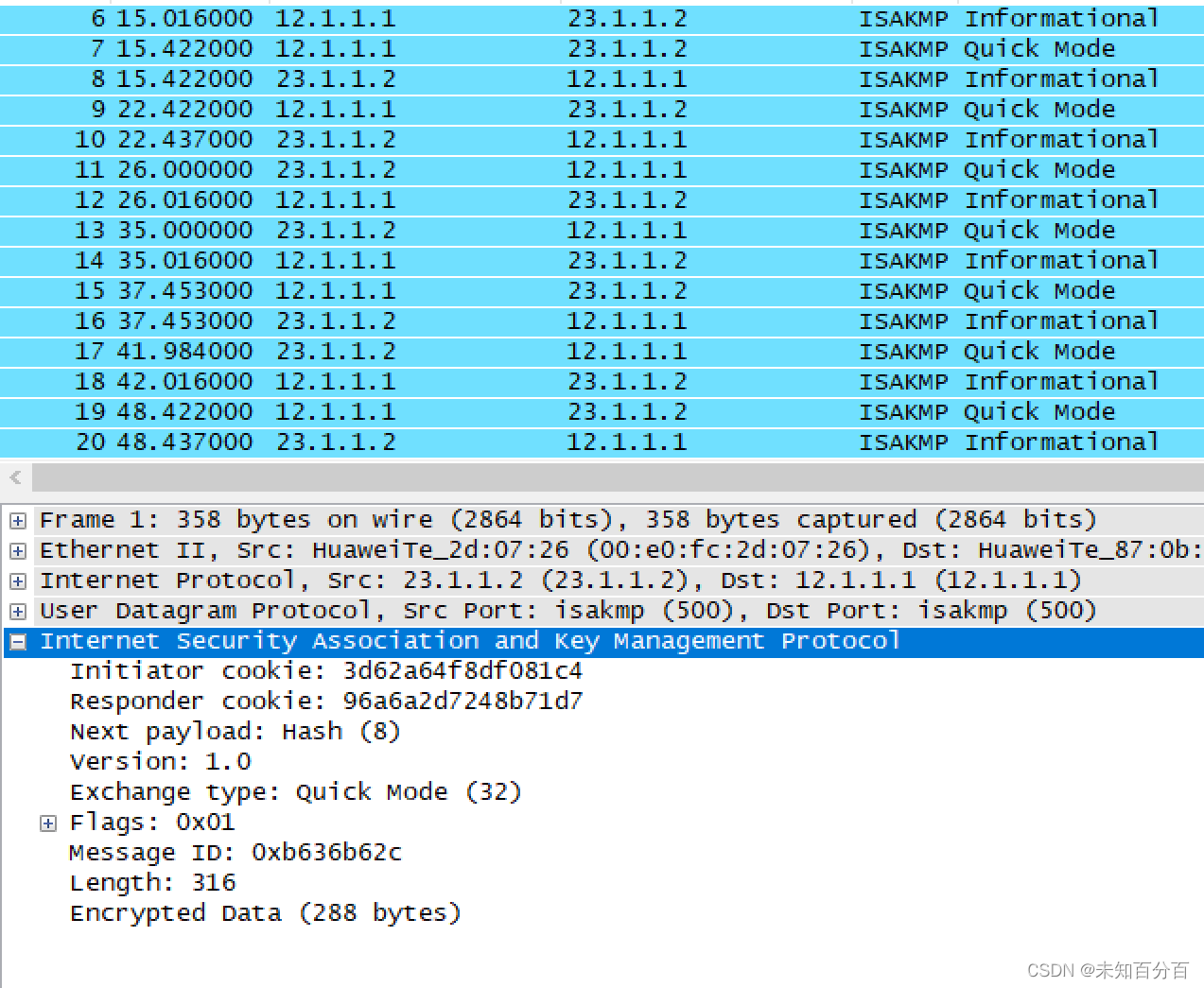
现在还可以正常的看到包的内容
(2)尝试使用 PC1 ping PC2:
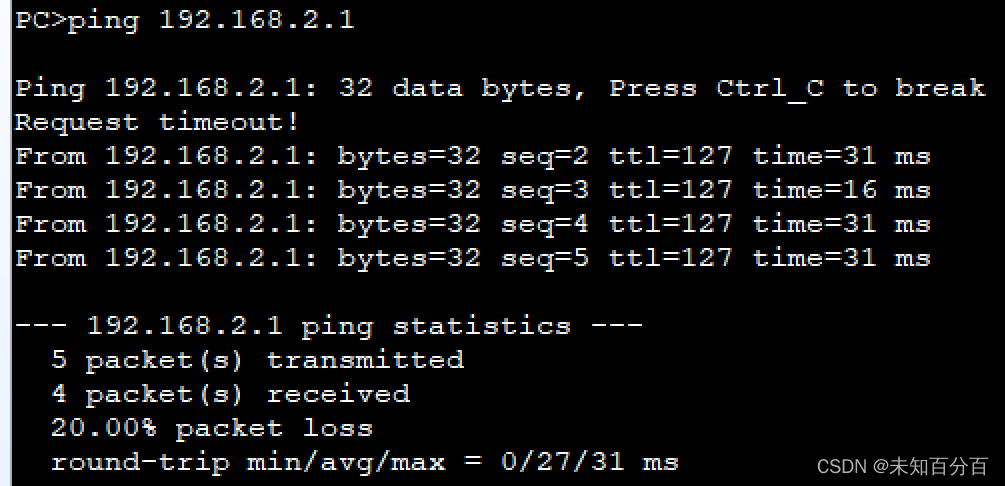
两个私网成功的使用tunnel访问了!!!
(3)再去查看抓的包: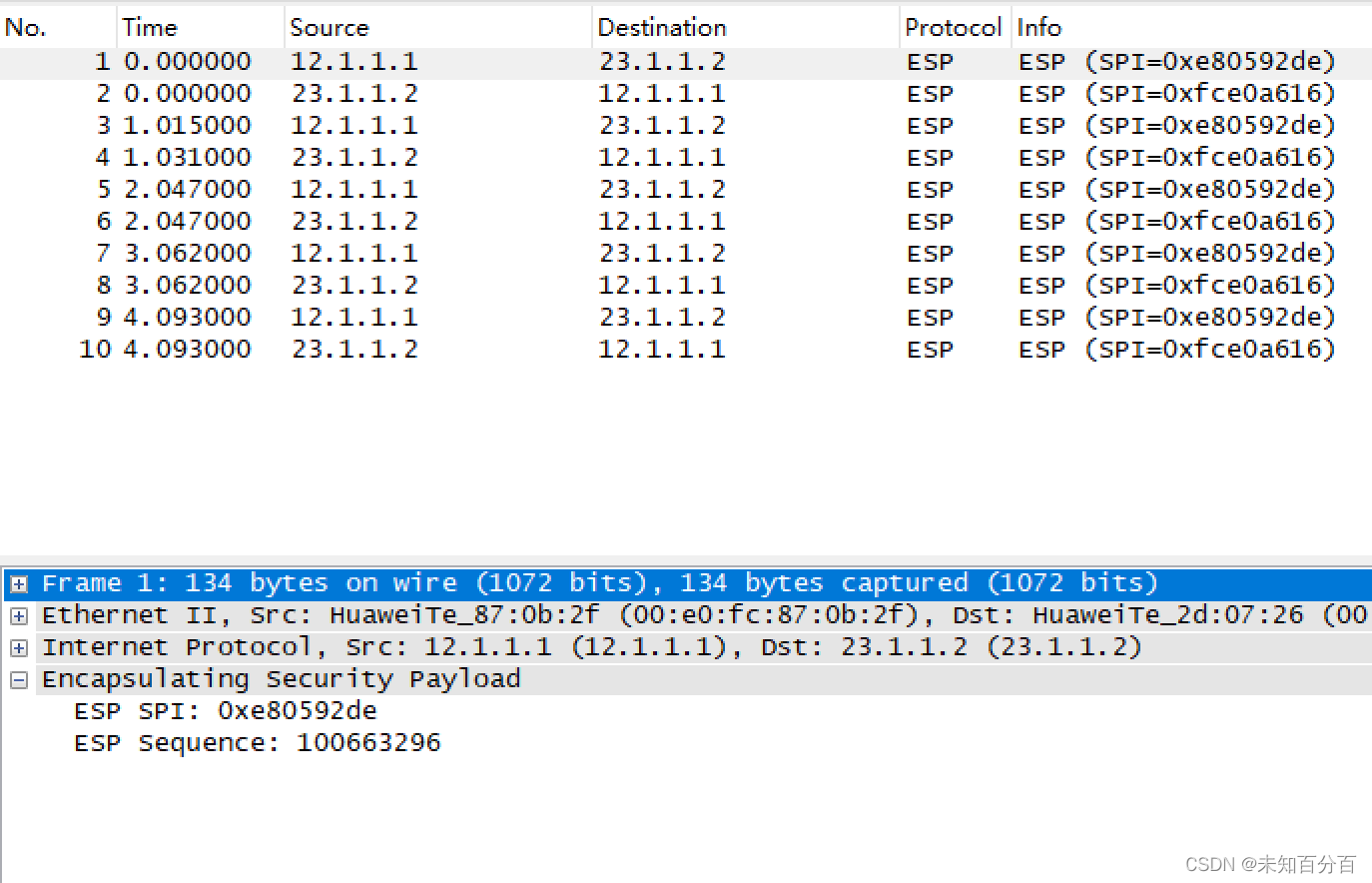
现在的包已经是加密后的了,看不见包中的内容!