【IOS逆向】frida-ios-dump砸壳
前面尝试了dumpdecrypted和Clutch砸壳,均未能砸壳成功,这些工具的更新时间都是2016年以前了,技术上没有迭代,所以我们在尝试新的砸壳思路
https://github.com/AloneMonkey/frida-ios-dump
frida-ios-dump
这里除了frida还有一些额外的环境
usbmuxd
brew install usbmuxd
pip依赖
sudo python3 -m pip install -r requirements.txt --upgrade
✘ ~/Downloads/VulnTools/SecurityForIOS/frida-ios-dump master python3 -m pip install paramiko
Looking in indexes: http://mirrors.aliyun.com/pypi/simple/
Collecting paramiko
Downloading http://mirrors.aliyun.com/pypi/packages/ae/fe/3ab1540ee3f956fed7c738ac60b17586b3e57629a6b8f8dcbb790fca00c2/paramiko-3.0.0-py3-none-any.whl (210 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 210.8/210.8 kB 88.9 kB/s eta 0:00:00
Requirement already satisfied: cryptography>=3.3 in /Users/huangweihong/.pyenv/versions/3.8.13/lib/python3.8/site-packages (from paramiko) (37.0.2)
Collecting pynacl>=1.5
Downloading http://mirrors.aliyun.com/pypi/packages/ce/75/0b8ede18506041c0bf23ac4d8e2971b4161cd6ce630b177d0a08eb0d8857/PyNaCl-1.5.0-cp36-abi3-macosx_10_10_universal2.whl (349 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 349.9/349.9 kB 90.5 kB/s eta 0:00:00
Collecting bcrypt>=3.2
Downloading http://mirrors.aliyun.com/pypi/packages/78/d4/3b2657bd58ef02b23a07729b0df26f21af97169dbd0b5797afa9e97ebb49/bcrypt-4.0.1-cp36-abi3-macosx_10_10_universal2.whl (473 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 473.4/473.4 kB 85.7 kB/s eta 0:00:00
Requirement already satisfied: cffi>=1.12 in /Users/huangweihong/.pyenv/versions/3.8.13/lib/python3.8/site-packages (from cryptography>=3.3->paramiko) (1.15.0)
Requirement already satisfied: pycparser in /Users/huangweihong/.pyenv/versions/3.8.13/lib/python3.8/site-packages (from cffi>=1.12->cryptography>=3.3->paramiko) (2.21)
Installing collected packages: bcrypt, pynacl, paramiko
Successfully installed bcrypt-4.0.1 paramiko-3.0.0 pynacl-1.5.0
~/Downloads/VulnTools/SecurityForIOS/frida-ios-dump master ./dump.py
Traceback (most recent call last):
File "./dump.py", line 22, in <module>
from scp import SCPClient
ModuleNotFoundError: No module named 'scp'
✘ ~/Downloads/VulnTools/SecurityForIOS/frida-ios-dump master python3 -m pip install scp
Looking in indexes: http://mirrors.aliyun.com/pypi/simple/
Collecting scp
Downloading http://mirrors.aliyun.com/pypi/packages/7f/04/4bcc504e6c2fdcfee7d74a6d14a49db0f129baf2cfa19f61148f333e96b9/scp-0.14.5-py2.py3-none-any.whl (8.7 kB)
Requirement already satisfied: paramiko in /Users/huangweihong/.pyenv/versions/3.8.13/lib/python3.8/site-packages (from scp) (3.0.0)
Requirement already satisfied: pynacl>=1.5 in /Users/huangweihong/.pyenv/versions/3.8.13/lib/python3.8/site-packages (from paramiko->scp) (1.5.0)
Requirement already satisfied: cryptography>=3.3 in /Users/huangweihong/.pyenv/versions/3.8.13/lib/python3.8/site-packages (from paramiko->scp) (37.0.2)
Requirement already satisfied: bcrypt>=3.2 in /Users/huangweihong/.pyenv/versions/3.8.13/lib/python3.8/site-packages (from paramiko->scp) (4.0.1)
Requirement already satisfied: cffi>=1.12 in /Users/huangweihong/.pyenv/versions/3.8.13/lib/python3.8/site-packages (from cryptography>=3.3->paramiko->scp) (1.15.0)
Requirement already satisfied: pycparser in /Users/huangweihong/.pyenv/versions/3.8.13/lib/python3.8/site-packages (from cffi>=1.12->cryptography>=3.3->paramiko->scp) (2.21)
Installing collected packages: scp
Successfully installed scp-0.14.5
砸壳
终端1
iproxy 2222 22
终端2
ssh root@127.0.0.1 -p 2222
The authenticity of host '[127.0.0.1]:2222 ([127.0.0.1]:2222)' can't be established.
RSA key fingerprint is SHA256:S1zJ0P1vjW2JU7KPVtdi11dF0YNd1CNUEoK9jdPzBs8.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:23: 192.168.0.103
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[127.0.0.1]:2222' (RSA) to the list of known hosts.
root@127.0.0.1's password:
iPhone:~ root#
iPhone:~ root#
终端3
~ fridadump xxxx
Start the target app xxxxx
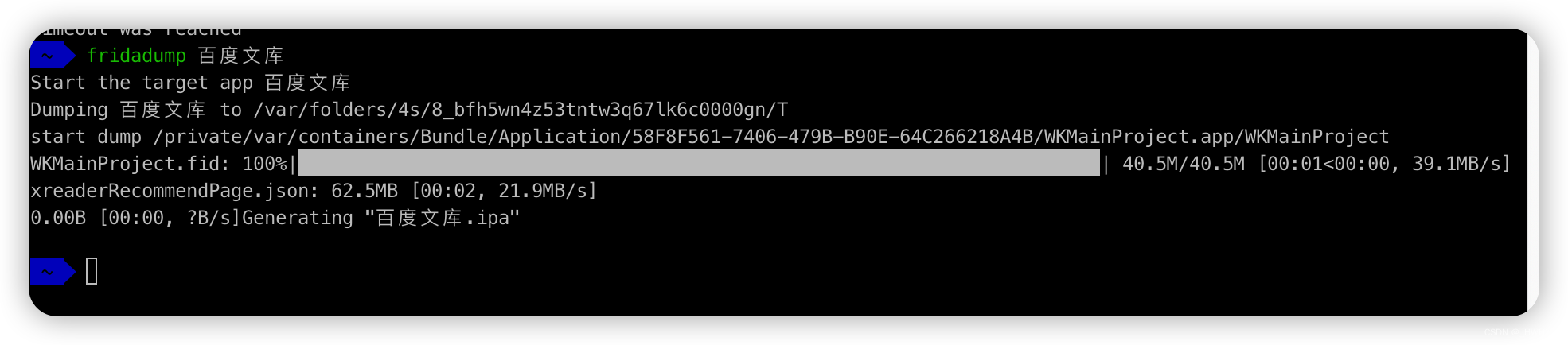
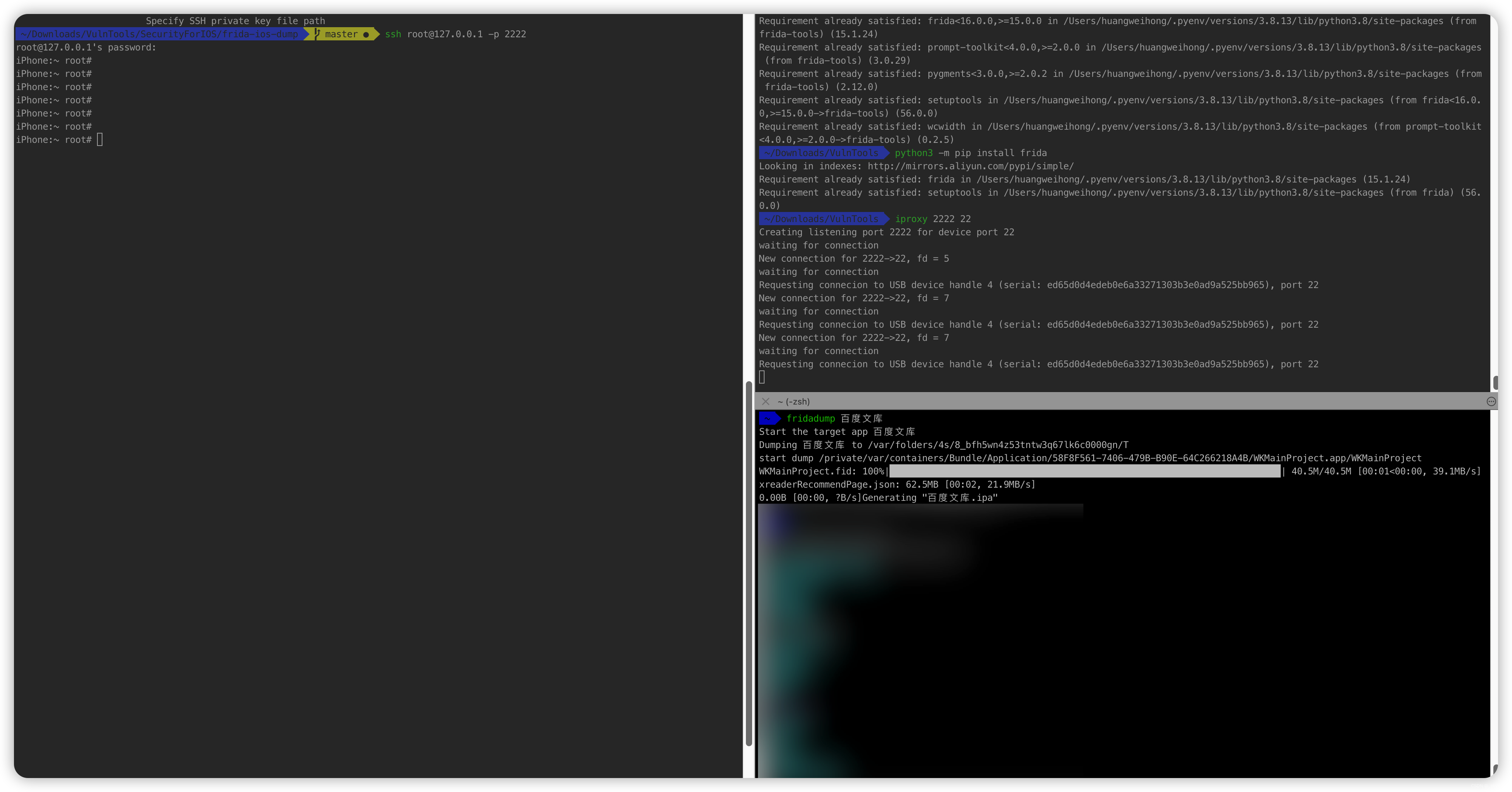
解压
unzip xx.ipa
在当前目录下会出现一个payload文件夹,里面有砸壳完成的app
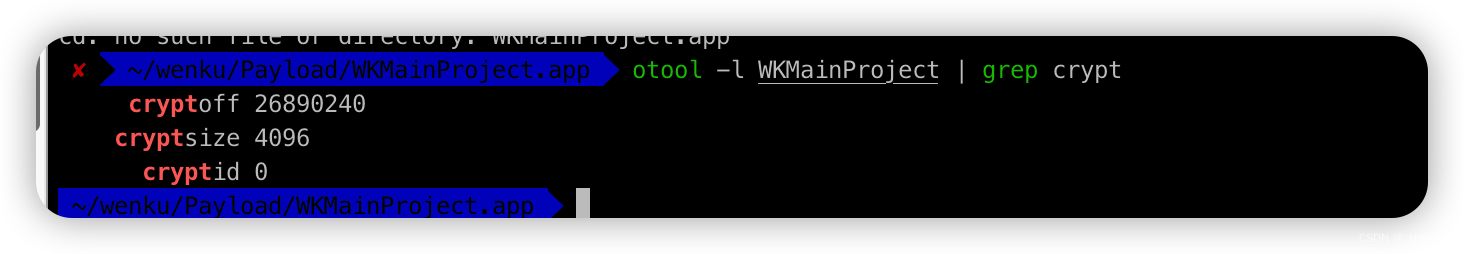
加密查询
✘ ~/wenku/Payload/WKMainProject.app otool -l WKMainProject | grep crypt
cryptoff 26890240
cryptsize 4096
cryptid 0
二进制逆向查看
直接将上述得到的IPA丢给hopper即可查看逆向代码
问题
如果出现
~ frida-ps -U
Failed to enumerate processes: timeout was reached
则可以更新下cydia的frida版本和mac本地的frida版本
如果出现
~ fridadump xxx
Start the target app xxxx
timeout was reached
则需要包吃屏幕常亮和app打开,因为是动态注入的