IDT 结构
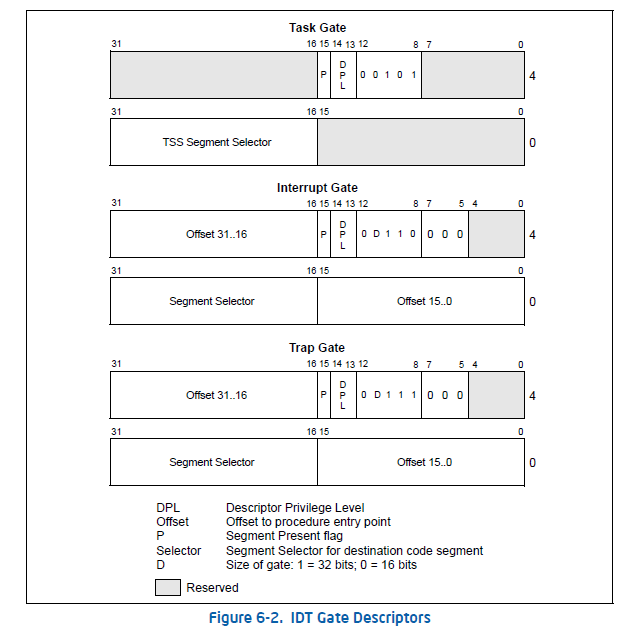
windbg 调试查看idt
!idt -a 查看所有中断处理函数地址
r idtr 查看idtr寄存器
kd> !idt -a
Dumping IDT:
00: 804e0350 nt!KiTrap00
01: 804e04cb nt!KiTrap01
02: Task Selector = 0x0058
03: 804e089d nt!KiTrap03
04: 804e0a20 nt!KiTrap04
05: 804e0b81 nt!KiTrap05
06: 804e0d02 nt!KiTrap06
07: 804e136a nt!KiTrap07
08: Task Selector = 0x0050
09: 804e178f nt!KiTrap09
0a: 804e18ac nt!KiTrap0A
0b: 804e19e9 nt!KiTrap0B
0c: 804e1c42 nt!KiTrap0C
0d: 804e1f38 nt!KiTrap0D
0e: 804e264f nt!KiTrap0E
0f: 804e297c nt!KiTrap0F
10: 804e2a99 nt!KiTrap10
11: 804e2bce nt!KiTrap11
12: Task Selector = 0x00A0
13: 804e2d34 nt!KiTrap13
14: 804e297c nt!KiTrap0F
15: 804e297c nt!KiTrap0F
16: 804e297c nt!KiTrap0F
17: 804e297c nt!KiTrap0F
18: 804e297c nt!KiTrap0F
19: 804e297c nt!KiTrap0F
1a: 804e297c nt!KiTrap0F
1b: 804e297c nt!KiTrap0F
1c: 804e297c nt!KiTrap0F
1d: 804e297c nt!KiTrap0F
1e: 804e297c nt!KiTrap0F
1f: 804e297c nt!KiTrap0F
20: 00000000
21: 00000000
22: 00000000
23: 00000000
24: 00000000
25: 00000000
26: 00000000
27: 00000000
28: 00000000
29: 00000000
2a: 804dfb92 nt!KiGetTickCount
2b: 804dfc95 nt!KiCallbackReturn
2c: 804dfe34 nt!KiSetLowWaitHighThread
2d: 804e077c nt!KiDebugService
2e: 804df631 nt!KiSystemService可以看到0x2e 中断处理函数地址 804df631 nt!KiSystemService
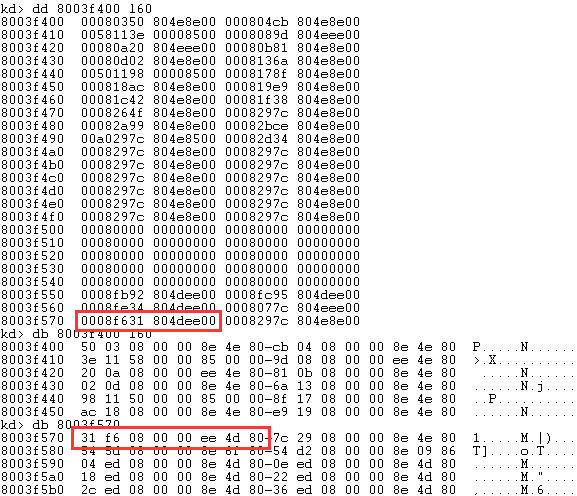
kd> dq 8003f570
8003f570 804dee00`0008f631 804e8e00`0008297c
8003f580 806f8e00`00085d54 86098e00`0008d254
8003f590 804d8e00`0008ed04 804d8e00`0008ed0e
8003f5a0 804d8e00`0008ed18 804d8e00`0008ed22
8003f5b0 804d8e00`0008ed2c 804d8e00`0008ed36
8003f5c0 806e8e00`0008fef0 86388e00`000881ec
8003f5d0 86138e00`0008b49c 86288e00`0008d4b4
8003f5e0 86008e00`00083254 804d8e00`0008ed72代码段选择子为 0008