django-vue-admin demo_project
https://django-vue-admin.com/document/hjbs.html
https://bbs.django-vue-admin.com/article/9.html
https://gitee.com/liqianglog/django-vue-admin/tree/demo_project
/home/jack/work_demo/django-vue-admin-demo_project
https://gitee.com/panjiachen/vue-admin-template
前端开发
进入项目目录
cd dvadmin-ui
安装依赖
npm install --registry=https://registry.npm.taobao.org
启动服务
npm run dev
浏览器访问 http://localhost:8080
后端
-
进入项目目录 cd dvadmin-backend
-
在项目根目录中,复制 ./conf/env.example.py 文件为一份新的到 ./conf 文件夹下,并重命名为 env.py
-
在 env.py 中配置数据库信息
mysql数据库版本建议:8.0
mysql数据库字符集:utf8mb4 -
安装依赖环境
pip3 install -r requirements.txt -
执行迁移命令:
python3 manage.py makemigrations
python3 manage.py migrate -
初始化数据
python3 manage.py init -
启动项目
python3 manage.py runserver 127.0.0.1:8000
定时任务启动命令:
celery -A application worker -B --loglevel=info
注:
Windows 运行celery 需要安装 pip install eventlet
celery -A application worker -P eventlet --loglevel=info
初始账号:admin 密码:123456
后端接口文档地址:http://127.0.0.1:8000/docs/
1
sudo apt install python3-venv -y
cd ~
python3 -m venv python3.8.10_django_vue_admin_demo_env
source /home/jack/python3.8.10_django_vue_admin_demo_env/bin/activate
deactivate
可以运行
参考
dvadmin快速crud教程
https://bbs.django-vue-admin.com/article/9.html
django-vue-admin脚手架快速开发CRUD教程
https://blog.51cto.com/zhangxueliang/4659295
[Django开源学习 1]django-vue-admin — OK — book
https://blog.csdn.net/QAZJOU/article/details/126680407
Django-Vue-Admin项目-搭建本地测试环境
https://blog.csdn.net/catblu/article/details/130907164
二、django-vue-admin开源项目二次开发——修改默认菜单
https://miaojiang.blog.csdn.net/article/details/131112751
django+vue+admin 项目部署上线需要Nginx-Mysql-Redis-python3
https://blog.csdn.net/qq_42095701/article/details/115051013
三、django-vue-admin开源项目二次开发——后端快速实现curd及接口
https://miaojiang.blog.csdn.net/article/details/131113267
django-vue-admin脚手架快速开发CRUD教程
https://zhangxueliang.blog.csdn.net/article/details/121426900
celery
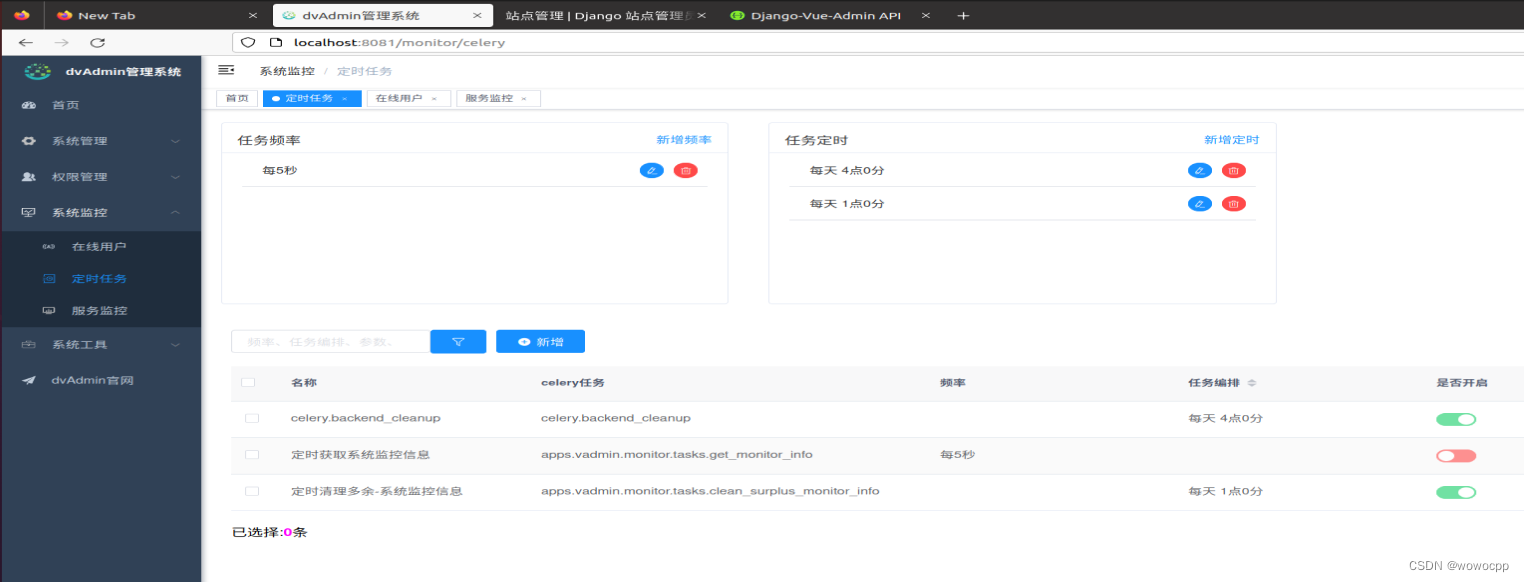
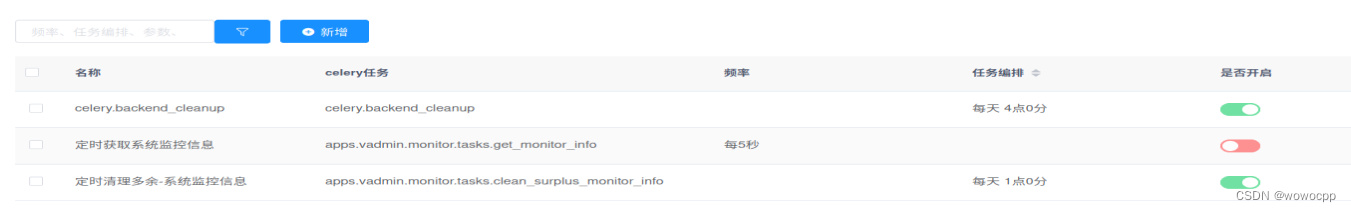
celery.backend_cleanup celery.backend_cleanup 每天 4点0分
定时获取系统监控信息 apps.vadmin.monitor.tasks.get_monitor_info 每5秒
定时清理多余-系统监控信息 apps.vadmin.monitor.tasks.clean_surplus_monitor_info 每天 1点0分
dvadmin-backend/apps/vadmin/monitor/views.py
class MonitorModelViewSet(CustomModelViewSet):
def enabled_monitor_info(self, request: Request, *args, **kwargs):
intervalschedule_obj, _ = IntervalSchedule.objects.get_or_create(every=5, period="seconds")
crontab_obj, _ = CrontabSchedule.objects.get_or_create(day_of_month="*", day_of_week="*", hour="1",
minute="0", month_of_year="*")
权限
conf/env.py:# 接口权限
conf/env.example.py:# 接口权限
apps/project/views.py: extra_filter_backends = [DataLevelPermissionsFilter] # 数据权限类,不需要可注释掉
apps/project/views.py: update_extra_permission_classes = (CommonPermission,) # 判断用户是否有这条数据的权限
apps/project/views.py: destroy_extra_permission_classes = (CommonPermission,) # 判断用户是否有这条数据的权限
apps/project/views.py: create_extra_permission_classes = (CommonPermission,) # 判断用户是否有这条数据的权限
apps/vadmin/system/apps.py: verbose_name = "权限管理"
apps/vadmin/scripts/permission/permission_menu.sql:INSERT INTO `permission_menu` (id, description, modifier, update_datetime, create_datetime, menuType, icon, name, orderNum, isFrame, web_path, component_path, interface_path, interface_method, perms, status, visible, isCache, creator_id, parentId_id, dept_belong_id) VALUES (2, '', 'admin', '2021-02-27 07:51:14.500722', '2021-02-27 07:51:14.500768', '0', 'peoples', '权限管理', 2, '1', '/permission', '', '', 'GET', NULL, '1', '1', '1', 1, NULL, '1');
apps/vadmin/op_drf/views.py: # 仅当GET方法时会触发该权限的校验
apps/vadmin/op_drf/views.py: # 仅当POST方法时会触发该权限的校验
apps/vadmin/op_drf/views.py: # 仅当DELETE方法时会触发该权限的校验
apps/vadmin/op_drf/views.py: # 仅当PUT方法时会触发该权限的校验
apps/vadmin/op_drf/viewsets.py: raise APIException(message='该对象不存在或者无访问权限')
apps/vadmin/op_drf/viewsets.py: 获取已配置的action权限校验,并且实例化其对象
apps/vadmin/op_drf/viewsets.py: 逐个校验action权限校验
apps/vadmin/op_drf/viewsets.py: action方法的专属对象权限校验
apps/vadmin/op_drf/viewsets.py: (1)新增action的权限校验
apps/vadmin/op_drf/viewsets.py: (1)新增action方法的专属对象权限检查入口
Binary file apps/vadmin/op_drf/__pycache__/middleware.cpython-38.pyc matches
Binary file apps/vadmin/op_drf/__pycache__/filters.cpython-38.pyc matches
Binary file apps/vadmin/op_drf/__pycache__/viewsets.cpython-38.pyc matches
apps/vadmin/op_drf/filters.py: 数据 级权限过滤器
apps/vadmin/op_drf/filters.py: 3. 根据角色的最大权限进行数据过滤(会有多个角色,进行去重取最大权限)
apps/vadmin/op_drf/filters.py: 4. 只为仅本人数据权限时只返回过滤本人数据,并且部门为自己本部门(考虑到用户会变部门,只能看当前用户所在的部门数据)
apps/vadmin/op_drf/filters.py: 5. 自定数据权限 获取部门,根据部门过滤
apps/vadmin/op_drf/filters.py: # 3. 根据所有角色 获取所有权限范围
apps/vadmin/op_drf/filters.py: # 4. 只为仅本人数据权限时只返回过滤本人数据,并且部门为自己本部门(考虑到用户会变部门,只能看当前用户所在的部门数据)
apps/vadmin/op_drf/filters.py: # 5. 自定数据权限 获取部门,根据部门过滤
apps/vadmin/op_drf/middleware.py: 权限模式拦截判断
apps/vadmin/op_drf/middleware.py: 接口权限验证,优先级:
apps/vadmin/op_drf/middleware.py: (1)接口是否接入权限管理, 是:继续; 否:通过
apps/vadmin/op_drf/middleware.py: (3)user的角色有该接口权限, 是:通过, 否:不通过
apps/vadmin/op_drf/middleware.py: auth_code含义: auth_code >=0, 表示接口认证通过; auth_code < 0, 表示无接口访问权限, 具体含义如下
apps/vadmin/op_drf/middleware.py: -10: 该请求已认证的用户没有这个接口的访问权限
apps/vadmin/op_drf/middleware.py: 10: 该接口没有录入权限系统, 放行 请求中认证的用户为超级管理员, 直接放行
apps/vadmin/op_drf/middleware.py: 30: 请求中认证的用户对应的角色中,某个角色包含了该接口的访问权限, 放行
apps/vadmin/op_drf/middleware.py: 4. 获取此用户关联角色所有有权限的接口
apps/vadmin/op_drf/middleware.py: # (1) 接口是否接入权限管理, 是:继续; 否:通过
apps/vadmin/op_drf/middleware.py: # (3)user的角色有该接口权限, 是:通过, 否:不通过
apps/vadmin/op_drf/middleware.py: if method == 'GET': # GET 不设置接口权限
apps/vadmin/op_drf/middleware.py: logger.info(f"[{user.username}] {method}:{view_path}, 权限认证:{auth_code}")
apps/vadmin/op_drf/middleware.py: return ErrorJsonResponse(data={
}, msg=f'无接口访问权限!')
apps/vadmin/permission/views.py: export_field_data = ['角色序号', '角色名称', '角色权限', '角色排序', '数据范围', '角色状态', '创建者', '修改者', '备注']
apps/vadmin/permission/apps.py: verbose_name = "权限管理"
Binary file apps/vadmin/permission/__pycache__/permissions.cpython-38.pyc matches
Binary file apps/vadmin/permission/__pycache__/views.cpython-38.pyc matches
apps/vadmin/permission/models/role.py: ('1', "全部数据权限"),
apps/vadmin/permission/models/role.py: ('2', "自定数据权限"),
apps/vadmin/permission/models/role.py: ('3', "本部门数据权限"),
apps/vadmin/permission/models/role.py: ('4', "本部门及以下数据权限"),
apps/vadmin/permission/models/role.py: ('5', "仅本人数据权限"),
apps/vadmin/permission/models/role.py: roleKey = CharField(max_length=64, verbose_name="权限字符")
apps/vadmin/permission/models/role.py: dataScope = CharField(max_length=8,default='1', choices=DATASCOPE_CHOICES, verbose_name="权限范围",)
apps/vadmin/permission/models/role.py: dept = ManyToManyField(to='permission.Dept', verbose_name='数据权限-关联部门', db_constraint=False)
apps/vadmin/permission/models/role.py: menu = ManyToManyField(to='permission.Menu', verbose_name='关联菜单权限', db_constraint=False)
apps/vadmin/permission/models/menu.py: perms = CharField(max_length=256, verbose_name="权限标识", null=True, blank=True)
Binary file apps/vadmin/permission/models/__pycache__/role.cpython-38.pyc matches
Binary file apps/vadmin/permission/models/__pycache__/menu.cpython-38.pyc matches
apps/vadmin/permission/migrations/0001_initial.py: ('perms', models.CharField(blank=True, max_length=256, null=True, verbose_name='权限标识')),
apps/vadmin/permission/migrations/0001_initial.py: ('roleKey', models.CharField(max_length=64, verbose_name='权限字符')),
apps/vadmin/permission/migrations/0001_initial.py: ('dataScope', models.CharField(choices=[('1', '全部数据权限'), ('2', '自定数据权限'), ('3', '本部门数据权限'), ('4', '本部门及以下数据权限'), ('5', '仅本人数据权限')], default='1', max_length=8, verbose_name='权限范围')),
apps/vadmin/permission/migrations/0001_initial.py: ('dept', models.ManyToManyField(db_constraint=False, to='permission.Dept', verbose_name='数据权限-关联部门')),
apps/vadmin/permission/migrations/0001_initial.py: ('menu', models.ManyToManyField(db_constraint=False, to='permission.Menu', verbose_name='关联菜单权限')),
Binary file apps/vadmin/permission/migrations/__pycache__/0001_initial.cpython-38.pyc matches
apps/vadmin/permission/permissions.py: self.message = getattr(self.__class__, 'message', '无权限')
apps/vadmin/permission/permissions.py: 通用权限类,判断用户是否有这条数据的查询权限,如没有则直接没有操作权限
apps/vadmin/permission/permissions.py: 3. 根据所有角色 获取所有权限范围
apps/vadmin/permission/permissions.py: 3.1 判断用户是否为超级管理员角色/如果有1(所有数据) 则有权限操作
apps/vadmin/permission/permissions.py: 4. 只为仅本人数据权限时只有操作本人数据权限,并且部门为自己本部门(考虑到用户会变部门,只能看当前用户所在的部门数据)
apps/vadmin/permission/permissions.py: 5. 自定数据权限 获取部门,根据部门判断,是否有权限操作
apps/vadmin/permission/permissions.py: message = '没有有操作权限'
apps/vadmin/permission/permissions.py: self.message = "该用户无部门,无权限操作!"
apps/vadmin/permission/permissions.py: self.message = "该用户无角色,无权限操作!"
apps/vadmin/permission/permissions.py: # 3. 根据所有角色 获取所有权限范围
apps/vadmin/permission/permissions.py: # 3.1 判断用户是否为超级管理员角色/如果有1(所有数据) 则有权限操作
apps/vadmin/permission/permissions.py: # 4. 只为仅本人数据权限时只有操作本人数据权限,并且部门为自己本部门(考虑到用户会变部门,只能看当前用户所在的部门数据)
apps/vadmin/permission/permissions.py: # 5. 自定数据权限 获取部门,根据部门判断,是否有权限操作
apps/vadmin/permission/permissions.py: self.message = f"没有此数据操作权限!"
apps/vadmin/permission/permissions.py: 部门删除权限校验:判断部门下是否有用户存在,存在不可删除
apps/vadmin/permission/permissions.py: message = '没有有操作权限'
application/settings.py: 'vadmin.op_drf.middleware.PermissionModeMiddleware', # 权限中间件
application/settings.py:# 接口权限
logs/server.log:[2023-06-30 17:44:37,333][vadmin.op_drf.middleware.process_view():157] [INFO] [admin] POST:/admin/celery/operate_celery/, 权限认证:10