[SWPUCTF] 2021新生赛之Crypto篇刷题记录①
NSSCTF平台:https://www.nssctf.cn/
PS:记得所有的flag都改为NSSCTF
[SWPUCTF 2021 新生赛]crypto6
一串字符串 Base家族 套娃加密 最后Base64解密得到flag。
var="************************************"
flag='NSSCTF{' + base64.b16encode(base64.b32encode(base64.b64encode(var.encode()))) + '}'
print(flag)
4A5A4C564B36434E4B5241544B5432454E4E32465552324E47424758534D44594C4657564336534D4B5241584F574C4B4B463245365643424F35485649534C584A5A56454B4D4B5049354E47593D3D3D
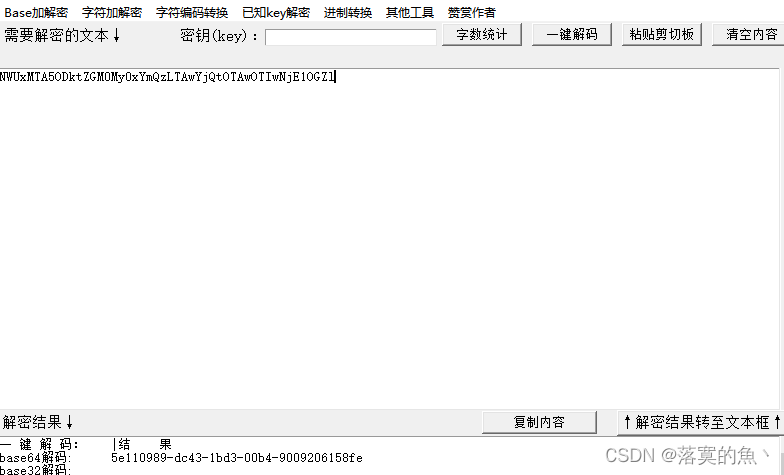
NSSCTF{5e110989-dc43-1bd3-00b4-9009206158fe}
[SWPUCTF 2021 新生赛]ez_caesar
下载下来一个py脚本 里面有输入的值 先Base64解码在凯撒解密最终得到flag。
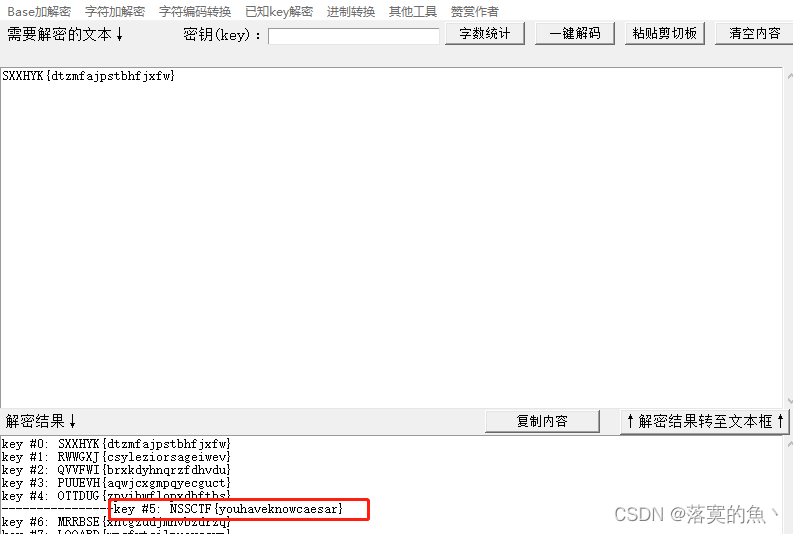
NSSCTF{youhaveknowcaesar}
[SWPUCTF 2021 新生赛]crypto10
直接ROT13解密,直接随波逐流一把梭
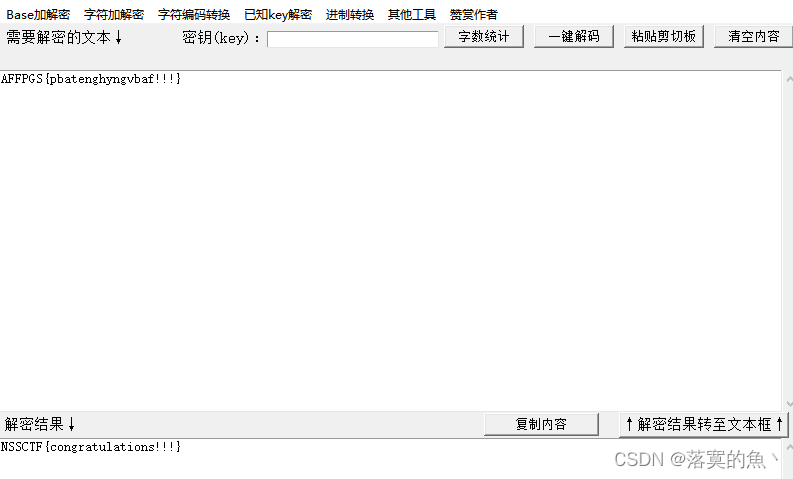
NSSCTF{congratulations!!!}
[SWPUCTF 2021 新生赛]pigpig
猪圈密码 直接参照图 对应找出flag即可。
猪圈密码在线解密网站:http://www.metools.info/code/c90.html

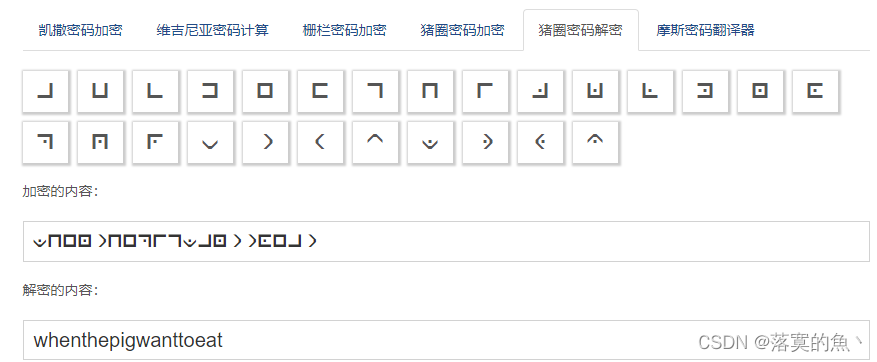
NSSCTF{whenthepigwanttoeat}
[SWPUCTF 2021 新生赛]traditional
西方的二进制数学的发明者莱布尼茨,从中国的八卦图当中受到启发,演绎并推论出了数学矩阵,最后创造的二进制数学。二进制数学的诞生为计算机的发明奠定了理论基础。而计算机现在改变了我们整个世界,改变了我们生活,而他的源头却是来自于八卦图。现在,给你一组由八卦图方位组成的密文,你能破解出其中的含义吗? 震坤艮 震艮震 坤巽坤 坤巽震 震巽兑 震艮震 震离艮 震离艮
八卦图解密 根据八卦图上面的 判断 阴阳不同化为0和1 (二进制)再根据题目进行对照

这种的二进制为:001000100 001100001 000110000 000110001 001110011 001100001 001101100 001101100
十进制为:68 97 48 49 115 97 108 108转为ascii码
NSSCTF{Da01sall}
[SWPUCTF 2021 新生赛]crypto2
> from gmpy2 import * from Crypto.Util.number import *
>
>
>
> flag = '***************'
>
> p = getPrime(512) q = getPrime(512) m1 =
> bytes_to_long(bytes(flag.encode()))
>
>
> n = p*q e1 = getPrime(32) e2 = getPrime(32) print()
>
> flag1 = pow(m1,e1,n) flag2 = pow(m1,e2,n) print('flag1= '+str(flag1))
> print('flag2= '+str(flag2)) print('e1= ' +str(e1)) print('e2=
> '+str(e2)) print('n= '+str(n))
>
>
> #flag1= 100156221476910922393504870369139942732039899485715044553913743347065883159136513788649486841774544271396690778274591792200052614669235485675534653358596366535073802301361391007325520975043321423979924560272762579823233787671688669418622502663507796640233829689484044539829008058686075845762979657345727814280
> #flag2= 86203582128388484129915298832227259690596162850520078142152482846864345432564143608324463705492416009896246993950991615005717737886323630334871790740288140033046061512799892371429864110237909925611745163785768204802056985016447086450491884472899152778839120484475953828199840871689380584162839244393022471075
> #e1= 3247473589
> #e2= 3698409173
> #n= 103606706829811720151309965777670519601112877713318435398103278099344725459597221064867089950867125892545997503531556048610968847926307322033117328614701432100084574953706259773711412853364463950703468142791390129671097834871371125741564434710151190962389213898270025272913761067078391308880995594218009110313
[SWPUCTF 2021 新生赛]ez_rsa
p = 1325465431
q = 152317153
e = 65537
计算出d,将d用MD5加密后包裹NSSCTF{}提交
import gmpy2
p = 1325465431
q = 152317153
e = 65537
a = (p - 1) * (q - 1)
b = gmpy2.invert(e,a)
print(b)
#最后别忘了md5加密一下
NSSCTF{08bb8fb628da85923e5734a75ac19ffe}
[鹤城杯 2021]A_CRYPTO
套娃解密: Rot13---Base16--Base32-Base64-Base64
4O595954494Q32515046324757595N534R52415653334357474R4N575955544R4O5N4Q46434S4O59474253464Q5N444R4Q51334557524O5N4S424944473542554O595N44534O324R49565746515532464O49345649564O464R4R494543504N35
## Rot13
4B595954494D32515046324757595A534E52415653334357474E4A575955544E4B5A4D46434F4B59474253464D5A444E4D51334557524B5A4F424944473542554B595A44534B324E49565746515532464B49345649564B464E4E494543504A35
## Base16
KYYTIM2QPF2GWYZSNRAVS3CWGNJWYUTNKZMFCOKYGBSFMZDNMQ3EWRKZOBIDG5BUKYZDSK2NIVWFQU2FKI4VIVKFNNIECPJ5
## Base32
V143Pytkc2lAYlV3SlRmVXQ9X0dVdmd6KEYpP3t4V29+MElXSER9TUEkPA==
## Base64
W^7?+dsi@bUwJTfUt=_GUvgz(F)?{
xWo~0IWHD}MA$<
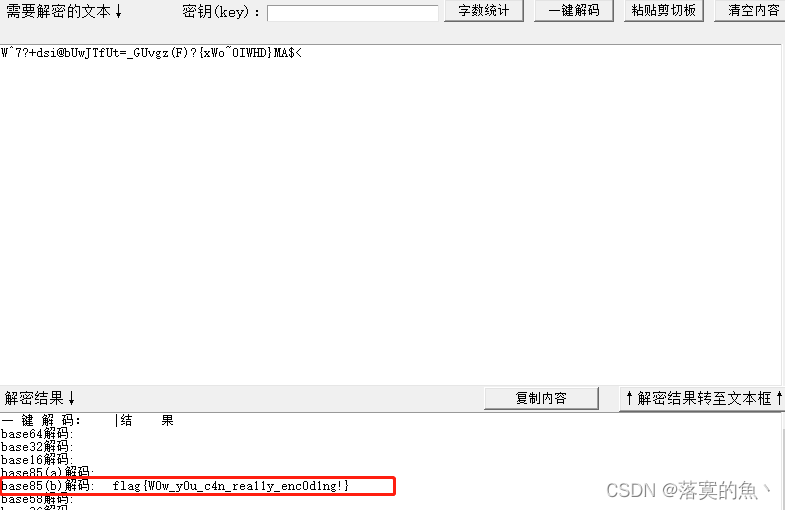
flag{W0w_y0u_c4n_rea11y_enc0d1ng!}
[BJDCTF 2020]base??
import base64
dict={
0: 'J', 1: 'K', 2: 'L', 3: 'M', 4: 'N', 5: 'O', 6: 'x', 7: 'y', 8: 'U', 9: 'V', 10: 'z', 11: 'A', 12: 'B', 13: 'C', 14: 'D', 15: 'E', 16: 'F', 17: 'G', 18: 'H', 19: '7', 20: '8', 21: '9', 22: 'P', 23: 'Q', 24: 'I', 25: 'a', 26: 'b', 27: 'c', 28: 'd', 29: 'e', 30: 'f', 31: 'g', 32: 'h', 33: 'i', 34: 'j', 35: 'k', 36: 'l', 37: 'm', 38: 'W', 39: 'X', 40: 'Y', 41: 'Z', 42: '0', 43: '1', 44: '2', 45: '3', 46: '4', 47: '5', 48: '6', 49: 'R', 50: 'S', 51: 'T', 52: 'n', 53: 'o', 54: 'p', 55: 'q', 56: 'r', 57: 's', 58: 't', 59: 'u', 60: 'v', 61: 'w', 62: '+', 63: '/', 64: '='}
base64_list = ['A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I', 'J', 'K', 'L', 'M', 'N', 'O', 'P','Q', 'R', 'S', 'T', 'U', 'V', 'W', 'X', 'Y', 'Z', 'a', 'b', 'c', 'd', 'e', 'f','g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r', 's', 't', 'u', 'v','w', 'x', 'y', 'z', '0', '1', '2', '3', '4', '5', '6', '7', '8', '9', '+', '/']
cipher='FlZNfnF6Qol6e9w17WwQQoGYBQCgIkGTa9w3IQKw'
res=''
for i in range(len(cipher)):
for j in range(64):
if(dict[j]==cipher[i]):
res+=base64_list[j]
flag=base64.b64decode(res)
print(flag)
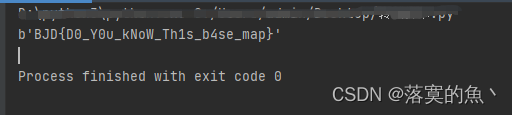
NSSCTF{D0_Y0u_kNoW_Th1s_b4se_map}