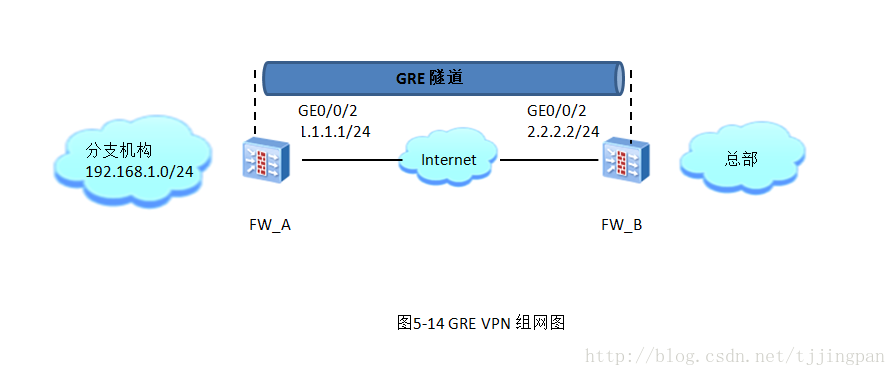
5.2.2 配置GRE基本参数
GRE 隧道的配置也很简单,可以分为两个步骤。
1.配置Tunnel接口
在FW_A 上配置Tunel接口的封装参数。
interface Tunnel1 description 2.2.2.2 ip address 10.1.1.1 255.255.255.0 tunnel-protocol gre source 1.1.1.1
firewall zone dmz set priority 50 add interface Tunnel1 #
在FW_A将Tunnel接口加入安全区域。Tunnel接口可以加入到任意一个安全区域中,这里我们把Tunnel接口加入到DMZ区域
firewall zone dmz set priority 50 add interface Tunnel1 #
在FW_B上配置Tunnel接口的封闭参数。
interface Tunnel1 ip address 10.1.1.2 255.255.255.0 tunnel-protocol gre source 2.2.2.2 destination 1.1.1.1 #
在FW_B上将Tunnel接口加往前安全区域。同样,我们把 Tunnel接口加入 到DMZ区域。
firewall zone dmz set priority 50 add interface Tunnel1
2.配置路由,把需要进行GRE封装的报文引导至Tunnel接口
(1)静态路由
在FW_A上配置静态路由,将去往总部私网的路由的下一跳设置为Tunnel接口。
[FW_A]ip route-static 192.168.2.0 24 Tunnel 1
在FW_B上配置静态路由,将去往分支机构私网的路由的下一跳设置为Tunnel操。
[FW_B]ip route-static 192.168.1.0 24 Tunnel 1
ENSP配置实例:
防火墙使用USG6000V
FW_1配置
# interface GigabitEthernet0/0/0 undo shutdown ip binding vpn-instance default ip address 192.168.0.1 255.255.255.0 service-manage http permit service-manage https permit service-manage ping permit service-manage ssh permit service-manage snmp permit service-manage telnet permit service-manage netconf permit # interface GigabitEthernet1/0/0 undo shutdown ip address 1.1.1.1 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/1 undo shutdown ip address 192.168.1.1 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/2 undo shutdown # interface GigabitEthernet1/0/3 undo shutdown # interface GigabitEthernet1/0/4 undo shutdown # interface GigabitEthernet1/0/5 undo shutdown # interface GigabitEthernet1/0/6 undo shutdown # interface Virtual-if0 # interface NULL0 # interface Tunnel1 ip address 10.1.1.1 255.255.255.0 tunnel-protocol gre source 1.1.1.1 destination 1.1.1.2 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/1 add interface Tunnel1 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/0 # firewall zone dmz set priority 50 # l2tp-group default-lns # ip route-static 192.168.2.0 255.255.255.0 Tunnel1 # undo ssh server compatible-ssh1x enable # user-interface con 0 authentication-mode password set authentication password cipher $1a$Le(646zngE$iuv)Su\U:SA)2v.=*e'(l@i<S8@K@ 4VkgQOPw\F%$ user-interface vty 0 4 authentication-mode aaa protocol inbound ssh user-interface vty 16 20 # sa # location # multi-interface mode proportion-of-weight # security-policy rule name untrust_to_local source-zone untrust destination-zone local source-address 1.1.1.2 32 destination-address 1.1.1.1 32 action permit # traffic-policy # policy-based-route # nat-policy # pcp-policy # dns-transparent-policy # return
FW_2配置
interface GigabitEthernet0/0/0 undo shutdown ip binding vpn-instance default ip address 192.168.0.1 255.255.255.0 service-manage http permit service-manage https permit service-manage ping permit service-manage ssh permit service-manage snmp permit service-manage telnet permit service-manage netconf permit # interface GigabitEthernet1/0/0 undo shutdown ip address 1.1.1.2 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/1 undo shutdown ip address 192.168.2.1 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/2 undo shutdown # interface GigabitEthernet1/0/3 undo shutdown # interface GigabitEthernet1/0/4 undo shutdown # interface GigabitEthernet1/0/5 undo shutdown # interface GigabitEthernet1/0/6 undo shutdown # interface Virtual-if0 # interface NULL0 # interface Tunnel1 ip address 10.1.1.2 255.255.255.0 tunnel-protocol gre source 1.1.1.2 destination 1.1.1.1 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/1 add interface Tunnel1 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/0 # firewall zone dmz set priority 50 # l2tp-group default-lns # ip route-static 192.168.1.0 255.255.255.0 Tunnel1 ip route-static 192.168.2.0 255.255.255.0 Tunnel1 # undo ssh server compatible-ssh1x enable # user-interface con 0 authentication-mode password set authentication password cipher $1a$2Y!g7:cbMY$awf#O:;`g2P0JkFM-uQ'eyG345_o~ V5}PxVC-~#R$ user-interface vty 0 4 authentication-mode aaa protocol inbound ssh user-interface vty 16 20 # sa # location # multi-interface mode proportion-of-weight # security-policy rule name untrust_to_local source-zone untrust destination-zone local source-address 1.1.1.1 32 destination-address 1.1.1.2 32 action permit # traffic-policy # policy-based-route # nat-policy # pcp-policy # dns-transparent-policy # return
验证相关命令
[FW_A]display firewall session table verbose Current Total Sessions : 23 icmp VPN: public --> public ID: c487fe49cbdbc9075185a9bcf07 Zone: trust --> trust TTL: 00:00:20 Left: 00:00:13 Interface: Tunnel1 NextHop: 192.168.2.2 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.1.2:975 --> 192.168.2.2:2048 PolicyName: --- gre VPN: public --> public ID: c487fe49cbdabb0771b5a9bc9db Zone: untrust --> local TTL: 00:10:00 Left: 00:09:59 Interface: InLoopBack0 NextHop: 127.0.0.1 MAC: 0000-0000-0000 <--packets: 0 bytes: 0 --> packets: 1174 bytes: 98,616 1.1.1.2:0 --> 1.1.1.1:0 PolicyName: untrust_to_local icmp VPN: public --> public ID: c487fe49cbdbe508f385a9bcf0d Zone: trust --> trust TTL: 00:00:20 Left: 00:00:07 Interface: Tunnel1 NextHop: 192.168.2.2 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.1.2:2511 --> 192.168.2.2:2048 PolicyName: ---
查看策略命中情况
[FW_A]display security-policy all Total:2 RULE ID RULE NAME STATE ACTION HITTED ------------------------------------------------------------------------------- 0 default enable deny 479 3 untrust_to_local enable permit 2 -------------------------------------------------------------------------------
[FW_A]display gre statistic
Packets forward to GRE for Decapsulation:
InPkts/InBytes:1,686/9,281,470,464
InPktSum/InSlicePkts:1,686/0
Hit tunnel failed:0, Hit pro failed:0
Version err :0, Checksum err :0, Key err :0
GRE Slice Pkts Recomp Failed :0
Transmit After Decap:1,686
Transmit Failed After Decap:0
Decode IP Err:0
Packets Deal on Local CPU/Other CPU:0/0
Packets forward to GRE for Encapsulation:
OutPkts/OutBytes:1,936/162,624
Outerr:0, Max cur err:0, Unknow pkt err:0
Total Trans After Encap:1,936
Trans to ipsec:0, Transmit without encrypt:0
Trans Common Pkts:0
To Other CPU or Local CPU Failed:0
Hit Fib Failed:0
关闭缺省包过渡
[USG6000V] security-policy [USG6000V-policy-security]default action permit
5.2.3 配置GRE安全机制
大家可能会有担忧,如果Internet上的恶意用户伪装成FW_A向FW_B发送GRE报文,那伪装者不就可以访问FW_B中的资源了吗,FW_A和FW_B在建立GRE隧道时,如何做到互信的呢?下面我们讲一下GRE安全机制。
1.关键字验证
下图展示了GRE头中的信息,其中Key位为1表示启用了关键字验证功能,下面的“Key:0x00003039”是关键字的值,转换为
十进制就是12345。
在FW_A上设置关键字为12345:
[FW_A-Tunnel1]gre key 12345
同时,在FW_B上设置关键字为12345:
[FW_B-Tunnel1]gre key 12345
2.校验和验证
虽然GRE隧道两端的防火墙实现了互信,但是如果报文在Internet传输途中也可能被恶意用户篡改,如何保证报文在传输时的完整性呢?这里又用到了GRE头中的"Checksum"字段。
防火墙在为报文封装GRE时将GRE头中的Checksum位的值置1,然后根据报文的信息计算检验和,并将校验和填到Checksum字段中。当隧道对端收到该报文时,也会根据报文信息计算检验和,并与报文中携带的校验和进行比较,如果检验结果一致,则接受此报文;如果不一致,则丢弃此报文。
校验和验证功能是单向的,对端防火墙是否开启不影响本端的校验和验证功能。实际环境 中,建议在隧道两端防火墙上则时开启。
下图中GRE的Checksum们为1,表示启用了校验和验证功能,下面的"Checksum 0x8f91" 是校验和的值。
配置校验和验证步骤也很简单,在FW_A上开启校验和验证 :
[FW_A-Tunnel1]gre checksum
的FW_B上开户校验和验证:
[FW_B-Tunnel1]gre checksum
3.Keepalive
GRE的安全机制可以实现隧道两端防火墙互信,并保证报文传输的完整性。但是这是还有一个问题,如果隧道对端出现故障时,
隧道本端如何感知呢?
GRE隧道是一种无状态类型的隧道,所谓的无状态类型是指隧道本端并不维护与对端的状态。换句话说假如隧道对端出现故障,那隧道本端是感受不到的。为了解决这个问题,GRE隧道提供了Keepalive保活机制。
FW_B Tunnel 1 口关闭模拟对端故障。FW_A无没有开启Keepalive功能 。
查看FW_A 的Tunnel 1端口状态,是UP的。
[FW_A]display interface Tunnel
Tunnel1 current state : UP
Line protocol current state : UP
Last line protocol up time : 2018-03-07 14:12:33
Description:Huawei, USG6000V1 Series, Tunnel1 Interface
Route Port,The Maximum Transmit Unit is 1500
Internet Address is 10.1.1.1/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 1.1.1.1 (GigabitEthernet1/0/0), destination 1.1.1.2
Tunnel protocol/transport GRE/IP, key enabled
keepalive disabled
Checksumming of packets enabled
Current system time: 2018-03-07 14:22:21
300 seconds input rate 0 bits/sec, 0 packets/sec
300 seconds output rate 200 bits/sec, 0 packets/sec
0 seconds input rate 0 bits/sec, 0 packets/sec
0 seconds output rate 0 bits/sec, 0 packets/sec
0 packets input, 0 bytes
0 input error
117 packets output, 10672 bytes
1 output error
Input:
Unicast: 0 packets, Multicast: 0 packets
Output:
Unicast: 117 packets, Multicast: 0 packets
Input bandwidth utilization : 0%
Output bandwidth utilization : 0%
FW_A开启Keepalive功能,查看FW_A 的Tunnel 1端口状态,是DOWN的。
Keepalive功能是单向的,对端是否开户Keepalive功能不影响本端的Keepalive功能。实际环境中,建议在隧道两端防火墙上同时开启。
下面给出开启Keepalive功能的命令,在FW_A上开启Keepalive功能:
[FW_A-Tunnel1]keepalive
在FW_B上开启Keepalive功能:
[FW_B-Tunnel1]keepalive
介绍到这里,大家是不是觉得有了GRE隧道就万事大吉呢,其实不然,GRE隧道自身有个缺陷:不带有安全加密功能。没有加密功能的GRE报文,只能是穿了个透明的马甲,隧道中的报文都是明文传输。所以我们在实际使用时,很少单纯使用GRE,
而是经常会把GRE与IPSec一同使用。由于IPSec技术具备很强的加密功能,就解决了GRE的安全性问题。这也是我们后面要介绍的
GRE over IPSec技术。
5.2.4安全策略配置思路
tunnel加到dmz 安全区
(1)我们先配置一个最宽泛的域间安全策略,以便调测GRE。
[FW_A]secu [FW_A]security-policy [FW_A-policy-security]def [FW_A-policy-security]default act [FW_A-policy-security]default action permit Warning:Setting the default packet filtering to permit poses security risks. You are advised to configure the security policy based on the actual data flows. Ar e you sure you want to continue?[Y/N]y [FW_A-policy-security](2)配置好GRE后,在PC_A上ping PC_B,然后查看会话表,以FW_A为例
[FW_A]display firewall session table ver Current Total Sessions : 6 icmp VPN: public --> public ID: c387f6c53182c90a655aa143f5 Zone: trust --> dmz TTL: 00:00:20 Left: 00:00:16 Interface: Tunnel1 NextHop: 192.168.2.2 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.1.2:64579 --> 192.168.2.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c53182f3046585aa143f6 Zone: trust --> dmz TTL: 00:00:20 Left: 00:00:17 Interface: Tunnel1 NextHop: 192.168.2.2 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.1.2:64835 --> 192.168.2.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c53182ad055805aa143f1 Zone: trust --> dmz TTL: 00:00:20 Left: 00:00:12 Interface: Tunnel1 NextHop: 192.168.2.2 MAC: 0000-0000-0000 <--packets: 0 bytes: 0 --> packets: 1 bytes: 60 192.168.1.2:63555 --> 192.168.2.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c53182bb0656c5aa143f3 Zone: trust --> dmz TTL: 00:00:20 Left: 00:00:14 Interface: Tunnel1 NextHop: 192.168.2.2 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.1.2:64067 --> 192.168.2.2:2048 PolicyName: default gre VPN: public --> public ID: c487f6c53180e50771b5aa140ff Zone: untrust --> local TTL: 00:10:00 Left: 00:09:58 Interface: InLoopBack0 NextHop: 127.0.0.1 MAC: 0000-0000-0000 <--packets: 153 bytes: 4,896 --> packets: 277 bytes: 21,200 1.1.1.2:0 --> 1.1.1.1:0 PolicyName: untrust_to_local icmp VPN: public --> public ID: c487f6c53182d70cc145aa143f4 Zone: trust --> dmz TTL: 00:00:20 Left: 00:00:15 Interface: Tunnel1 NextHop: 192.168.2.2 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.1.2:64323 --> 192.168.2.2:2048 PolicyName: default
从上述信息可知,PC_A可以ping 通PC_B, GRE会话也正常创建。
从会话表中我们可以看到两条流,一条是trust-->dmz之间的ICMP报文,一条是untrust-->local之间的GRE报文。由此我们可以
得到FW_A上的报文走向。FW_A需要配置trust-->dmz区域的安全策略,允许PC_A到PC_B的报文通过。
还需要配置untrust-->local区域安全策略,允许FW_A与FW_B建立GRE隧道.
PC_B ping PC_A,查看会话表:
[FW_A]display firewall session table verbose Current Total Sessions : 13 icmp VPN: public --> public ID: c387f6c5317c2f03d05aa14967 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:08 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:26953 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c387f6c5317c4b09785aa14969 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:10 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:27465 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c5317df3016fa5aa14964 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:05 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:26185 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c5317c3d02cd15aa14966 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:07 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:26697 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c5317c05039565aa14960 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:01 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:25161 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c5317de5047885aa14961 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:02 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:25417 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c5317dd7057075aa14962 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:03 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:25673 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c5317c2106bcd5aa14965 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:06 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:26441 --> 192.168.1.2:2048 PolicyName: default gre VPN: public --> public ID: c487f6c53180e50771b5aa140ff Zone: untrust --> local TTL: 00:10:00 Left: 00:09:59 Interface: InLoopBack0 NextHop: 127.0.0.1 MAC: 0000-0000-0000 <--packets: 432 bytes: 13,824 --> packets: 832 bytes: 64,448 1.1.1.2:0 --> 1.1.1.1:0 PolicyName: untrust_to_local icmp VPN: public --> public ID: c487f6c5317c13080a45aa14963 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:04 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:25929 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c5317c91090895aa14968 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:07 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:27209 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487f6c5317dbb0f8535aa1495e Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:00 Interface: GigabitEthernet1/0/1 NextHop: 192.168.1.2 MAC: 5489-9834-5d12 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:24649 --> 192.168.1.2:2048 PolicyName: default
从会话表中我们可以看到两条流,一条是dmz-->trust之间的ICMP报文,一条是untrust-->local之间的GRE报文。由此我们可以
得到FW_A上的报文走向。FW_A需要配置dmz--trust区域的安全策略,允许PC_B到PC_A的报文通过。
还需要配置untrust-->local区域安全策略,允许FW_A与FW_B建立GRE隧道.
FW_B分析
PC_A ping PC_B
[FW_B]display firewall session table verbose Current Total Sessions : 6 icmp VPN: public --> public ID: c487fb7898279101fa65aa14a65 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:17 Interface: GigabitEthernet1/0/1 NextHop: 192.168.2.2 MAC: 5489-98e9-2490 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.1.2:26954 --> 192.168.2.2:2048 PolicyName: default icmp VPN: public --> public ID: c487fb789827c9047cf5aa14a64 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:16 Interface: GigabitEthernet1/0/1 NextHop: 192.168.2.2 MAC: 5489-98e9-2490 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.1.2:26698 --> 192.168.2.2:2048 PolicyName: default gre VPN: public --> public ID: c487fb78982d050507a5aa14097 Zone: untrust --> local TTL: 00:10:00 Left: 00:09:58 Interface: InLoopBack0 NextHop: 127.0.0.1 MAC: 0000-0000-0000 <--packets: 502 bytes: 32,128 --> packets: 1168 bytes: 77,696 1.1.1.1:0 --> 1.1.1.2:0 PolicyName: untrust_to_local icmp VPN: public --> public ID: c487fb789827bb061d85aa14a66 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:18 Interface: GigabitEthernet1/0/1 NextHop: 192.168.2.2 MAC: 5489-98e9-2490 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.1.2:27210 --> 192.168.2.2:2048 PolicyName: default icmp VPN: public --> public ID: c487fb78982767065675aa14a63 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:15 Interface: GigabitEthernet1/0/1 NextHop: 192.168.2.2 MAC: 5489-98e9-2490 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.1.2:26442 --> 192.168.2.2:2048 PolicyName: default icmp VPN: public --> public ID: c487fb78982775067195aa14a61 Zone: dmz --> trust TTL: 00:00:20 Left: 00:00:13 Interface: GigabitEthernet1/0/1 NextHop: 192.168.2.2 MAC: 5489-98e9-2490 <--packets: 0 bytes: 0 --> packets: 1 bytes: 60 192.168.1.2:25930 --> 192.168.2.2:2048 PolicyName: default
两条隧道
gre建立
PC_A到PC_B 报文通过
PC_B ping PC_A
[FW_B]display firewall session table verbose Current Total Sessions : 6 gre VPN: public --> public ID: c487fb78982d050507a5aa14097 Zone: untrust --> local TTL: 00:10:00 Left: 00:09:59 Interface: InLoopBack0 NextHop: 127.0.0.1 MAC: 0000-0000-0000 <--packets: 534 bytes: 34,176 --> packets: 1208 bytes: 79,456 1.1.1.1:0 --> 1.1.1.2:0 PolicyName: untrust_to_local icmp VPN: public --> public ID: c487fb789826670515c5aa14b06 Zone: trust --> dmz TTL: 00:00:20 Left: 00:00:18 Interface: Tunnel1 NextHop: 192.168.1.2 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:2635 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487fb789827f30564f5aa14b02 Zone: trust --> dmz TTL: 00:00:20 Left: 00:00:14 Interface: Tunnel1 NextHop: 192.168.1.2 MAC: 0000-0000-0000 <--packets: 0 bytes: 0 --> packets: 1 bytes: 60 192.168.2.2:1611 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487fb789826050694b5aa14b04 Zone: trust --> dmz TTL: 00:00:20 Left: 00:00:16 Interface: Tunnel1 NextHop: 192.168.1.2 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:2123 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487fb7898262107c7e5aa14b07 Zone: trust --> dmz TTL: 00:00:20 Left: 00:00:19 Interface: Tunnel1 NextHop: 192.168.1.2 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:2891 --> 192.168.1.2:2048 PolicyName: default icmp VPN: public --> public ID: c487fb7898263d0b5205aa14b05 Zone: trust --> dmz TTL: 00:00:20 Left: 00:00:17 Interface: Tunnel1 NextHop: 192.168.1.2 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 192.168.2.2:2379 --> 192.168.1.2:2048 PolicyName: default
两条gre隧道建立
PC_B到PC_A报文通过