1. 引言
security parameter以 λ \lambda λ表示,除非明确说明,所有算法和adversaries都是probabilistic (interactive) Turing machines that run in polynomial time in this security parameter。
n e g l ( λ ) negl(\lambda) negl(λ) 表示a function that is negligible in λ \lambda λ。
1.1 Cryptographic Groups
-
G \mathbb{G} G:表示a cyclic group of prime order p p p。
-
O \mathcal{O} O:表示the identity of a group。
-
G \mathbb{G} G中的scalars of elements 为 scalar field F \mathbb{F} F of size p p p 中 的元素。
-
以大写字母来表示group element,以小写或希腊字母来表示scalar。
-
以粗体字来表示向量,即 a ∈ F n \mathbf{a} \in \mathbb{F}^n a∈Fn and G ∈ G n \mathbf{G} \in \mathbb{G}^n G∈Gn。
-
group operation为加法运算。
-
scalar a a a与group element G G G的乘积表示为 [ a ] G [a]G [a]G。
-
⟨ a , b ⟩ \langle \mathbf{a},\mathbf{b}\rangle ⟨a,b⟩表示2个相同长度scalar向量 a , b ∈ F n \mathbf{a},\mathbf{b}\in\mathbb{F}^n a,b∈Fn的inner product。
-
⟨ a , G ⟩ \langle \mathbf{a},\mathbf{G}\rangle ⟨a,G⟩ with a ∈ F n , G ∈ G n \mathbf{a}\in\mathbb{F}^n,\mathbf{G}\in\mathbb{G}^n a∈Fn,G∈Gn表示multiscalar multiplication。
-
0 n \mathbf{0}^n 0n表示a vector of length n n n that only contains zeroes in F \mathbb{F} F。
扫描二维码关注公众号,回复: 13196792 查看本文章
-
Discrete Log Relation Problem:
The advantage metric
Adv G , n dl-rel ( A , λ ) = Pr [ G G , n dl-rel ( A , λ ) ] \text{Adv}_{\mathbb{G},n}^{\text{dl-rel}}(\mathcal{A}, \lambda) = \textnormal{Pr} \left[ \mathsf{G}_{\mathbb{G},n}^{\text{dl-rel}}(\mathcal{A}, \lambda) \right] AdvG,ndl-rel(A,λ)=Pr[GG,ndl-rel(A,λ)]
is defined with respect the following game.
G a m e G G , n dl-rel ( A , λ ) : ‾ G ← G λ n a ← A ( G ) Return ( ⟨ a , G ⟩ = O ∧ a ≠ 0 n ) \begin{array}{ll} &\underline{\bold{Game} \, \mathsf{G}^{\text{dl-rel}}_{\mathbb{G},n}(\mathcal{A}, \lambda):} \\ &\mathbf{G} \gets \mathbb{G}^n_\lambda \\ &\mathbf{a} \gets \mathcal{A}(\mathbf{G}) \\ &\textnormal{Return} \, \left( \langle \mathbf{a}, \mathbf{G} \rangle = \mathcal{O} \land \mathbf{a} \neq \mathbf{0}^n \right) \end{array} GameGG,ndl-rel(A,λ):G←Gλna←A(G)Return(⟨a,G⟩=O∧a=0n)
即已知 n n n-length vector G ∈ G n \mathbf{G}\in\mathbb{G}^n G∈Gn group elements,discrete log relation problem 会ask for g ∈ F n \mathbf{g}\in\mathbb{F}^n g∈Fn,使得 g ≠ 0 n \mathbf{g}\neq \mathbf{0}^n g=0n 且 ⟨ a , G ⟩ = O \langle \mathbf{a},\mathbf{G}\rangle=\mathcal{O} ⟨a,G⟩=O,可将其称为 non-trivial discrete log relation。
该problem的hardness与 JT20 Lemma3中的 hardness of the discrete log problem in the group 紧密相连。可使用game G G , n dl-rel \mathsf{G}_{\mathbb{G},n}^{\text{dl-rel}} GG,ndl-rel 来定义该problem。
1.2 Interactive Proofs
interactive proof由3个算法组成 IP = ( Setup , P , V ) \text{IP}=(\text{Setup},\mathcal{P},\mathcal{V}) IP=(Setup,P,V):
- Setup ( 1 λ ) \text{Setup}(1^{\lambda}) Setup(1λ):输出为 p p \mathbf{pp} pp,为public parameters。
Prover P \mathcal{P} P 和 Verifier V \mathcal{V} V 为interactive machines (with access to p p \mathbf{pp} pp),以 ⟨ P ( x ) , V ( y ) ⟩ \langle\mathcal{P}(x),\mathcal{V}(y)\rangle ⟨P(x),V(y)⟩来表示execute a two-party protocol between Prover P \mathcal{P} P 和 Verifier V \mathcal{V} V on inputs x , y x,y x,y 的算法。在协议的最后,Verifier输出a decision bit。
1.3 Zero knowledge Arguments of Knowledge
Proofs of knowledge为:interactive proofs,Prover致力于令Verifier相信,针对某statement x x x,其知道某witness ω \omega ω,使得 ( x , ω ) ∈ R (x,\omega)\in\mathcal{R} (x,ω)∈R,其中 R \mathcal{R} R为polynomial-time decidable relation R \mathcal{R} R。
Halo2中主要关注具有computationally-bounded prover的argument of knowledge。
argument of knowledge主要有以下4个安全视角:
- Completeness:若Prover基于valid witness运算,则其总是可使Verifier信服。
- Soundness:cheating Prover无法在不知道valid witness的情况下,使Verifier信服错误的proof。cheating Prover成功的概率为soundness error。
- Knowledge soundness:若Verifier信服该statement是正确的,Prover是否实际处理的(”知道“)就是相应的valid witness。cheating Prover成功的概率为knowledge error。
- Zero knowledge:即Verifier是否可从proof中知道相应的valid witness。
1.3.1 Completeness

1.3.2 Soundness
-
Public coin是指:all of the messages sent by the verifier are each sampled with fresh randomness。
-
Fiat-Shamir transformation是指:In this transformation an interactive, public coin argument can be made non-interactive in the random oracle model by replacing the verifier algorithm with a cryptographically strong hash function that produces sufficiently random looking output。
-
State-Restoration Soundness:
详细参见论文 GT20- Tight State-Restoration Soundness in the Algebraic Group Model:
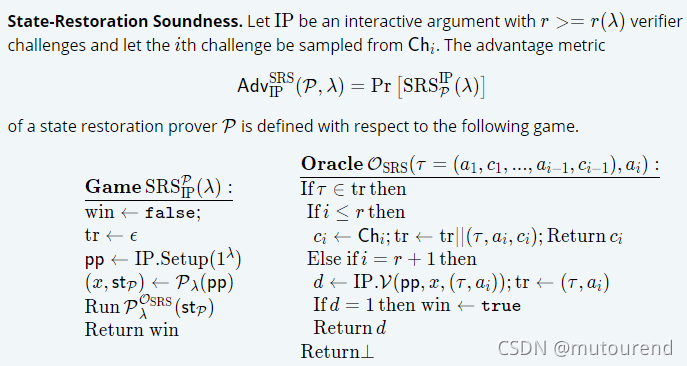
-
Knowledge Soundness:又名 witness extended emulation,是指:any successful prover algorithm there exists an efficient emulator that can extract a witness from it by rewinding it and supplying it with fresh randomness。
Halo2中对 witness extended emulation 的定义做了小调整,即Halo2中的provers为state restoration provers,定义为可rewind the verifier。此外,为了避免在witness extraction过程中对state restoration prover的rewind,Halo2中将协议定义在了algebraic group model:

algebraic group支持所谓的“online” extraction:即the extractor can obtain the witness from the representations themselves for a single (accepting) transcript。 -
State Restoration Witness Extended Emulation:

1.3.3 Zero Knowledge
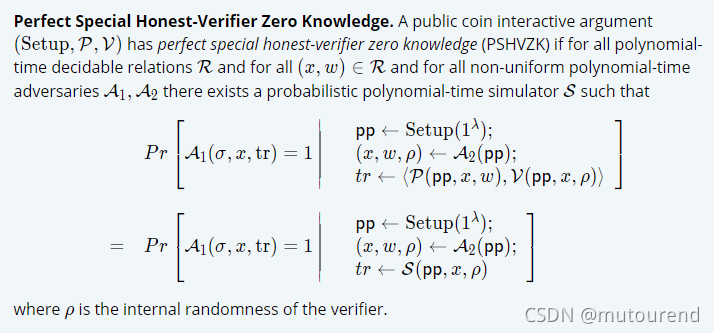
通常zero-knowledge定义中,要求Verifier act “honestly”,并send challenges that correspond only with their internal randomness,Verifier不可adaptively respond to the prover based on the prover’s messages。Halo2中使用了增强版定义:即强制要求the simulator to output a transcript with the same (adversarially provided) challenges that the verifier algorithm sends to the prover
2. Protocol
令 ω ∈ F \omega\in\mathbb{F} ω∈F为a n = 2 k n=2^k n=2k primitive root of unity,形成domain D = ( ω 0 , ω 1 , ⋯ , ω n − 1 ) D=(\omega^0,\omega^1,\cdots,\omega^{n-1}) D=(ω0,ω1,⋯,ωn−1) with vanishing polynomial t ( X ) = X n − 1 t(X)=X^n-1 t(X)=Xn−1 over 该domain。
令 k , n g , n a k,n_g,n_a k,ng,na为正整数。
接下来展现的是 interactive argument halo = ( Setup , P , V ) \textsf{halo} = (\textnormal{Setup}, \mathcal{P}, \mathcal{V}) halo=(Setup,P,V) for the relation:
R = { ( ( g ( X , C 0 , C 1 , . . . , C n a − 1 ) ) ; ( a 0 ( X ) , a 1 ( X , C 0 ) , . . . , a n a − 1 ( X , C 0 , C 1 , . . . , C n a − 1 ) ) ) : g ( ω i , C 0 , C 1 , . . . , C n a − 1 ) = 0 ∀ i ∈ [ 0 , 2 k ) } \mathcal{R} = \left\{ \begin{array}{ll} &\left( \begin{array}{ll} \left( g(X, C_0, C_1, ..., C_{n_a - 1}) \right); \\ \left( a_0(X), a_1(X, C_0), ..., a_{n_a - 1}(X, C_0, C_1, ..., C_{n_a - 1}) \right) \end{array} \right) : \\ \\ & g(\omega^i, C_0, C_1, ..., C_{n_a - 1}) = 0 \, \, \, \, \forall i \in [0, 2^k) \end{array} \right\} R=⎩⎪⎪⎨⎪⎪⎧((g(X,C0,C1,...,Cna−1));(a0(X),a1(X,C0),...,ana−1(X,C0,C1,...,Cna−1))):g(ωi,C0,C1,...,Cna−1)=0∀i∈[0,2k)⎭⎪⎪⎬⎪⎪⎫
其中 a 0 , a 1 , ⋯ , a n a − 1 a_0,a_1,\cdots,a_{n_a-1} a0,a1,⋯,ana−1 为(multivariate)polynomials with degree n − 1 n-1 n−1 in X X X and g g g has degree n g ( n − 1 ) n_g(n-1) ng(n−1) in X X X。
Setup ( λ ) \textnormal{Setup}(\lambda) Setup(λ):输出 p p = ( G , F , G ∈ G n , U , W ∈ G ) \mathsf{pp} = (\mathbb{G}, \mathbb{F}, \mathbf{G} \in \mathbb{G}^n, U, W \in \mathbb{G}) pp=(G,F,G∈Gn,U,W∈G)。
对于所有的 i ∈ [ 0 , n a ) i\in[0,n_a) i∈[0,na):
- 令 p i \mathbf{p_i} pi为exhaustive set of integers j j j (modulo n n n) 使得 a i ( ω j X , ⋯ ) a_i(\omega^j X, \cdots) ai(ωjX,⋯) appears as a term in g ( X , ⋯ ) g(X, \cdots) g(X,⋯)。
- 令 q \mathbf{q} q为a list of distinct sets of integers containing p i \mathbf{p_i} pi and the set q 0 = { 0 } \mathbf{q_0}=\{0\} q0={ 0}。
- 当 q j = p i \mathbf{q}_j=\mathbf{p_i} qj=pi时,令 σ ( i ) = q j \sigma(i)=\mathbf{q}_j σ(i)=qj
令 n q n_q nq表示 q \mathbf{q} q的size, n e n_e ne表示每个 p i \mathbf{p_i} pi的size。
接下来,协议证明对于每个多项式 a i ( X , ⋯ ) a_i(X,\cdots) ai(X,⋯),有 n e + 1 n_e+1 ne+1个blinding factors,且存在an evaluation of a i ( X , ⋯ ) a_i(X,\cdots) ai(X,⋯) over the domain D D D:
- 1) P \mathcal{P} P和 V \mathcal{V} V将进行 n a n_a na轮以下交互,对于其中第 j j j轮(从 0 0 0开始)有:
- P \mathcal{P} P 设置 a j ′ ( X ) = a j ( X , c 0 , c 1 , ⋯ , c j − 1 ) a_j'(X)=a_j(X,c_0,c_1,\cdots,c_{j-1}) aj′(X)=aj(X,c0,c1,⋯,cj−1)
- P \mathcal{P} P 发送hiding commitment A j = ⟨ a ′ , G ⟩ + [ ⋅ ] W A_j=\langle \mathbf{a}',\mathbf{G}\rangle+[\cdot]W Aj=⟨a′,G⟩+[⋅]W,其中 a ′ \mathbf{a}' a′为单变量多项式 a j ′ ( X ) a_j'(X) aj′(X)的系数, ⋅ \cdot ⋅为某随机值。
- V \mathcal{V} V respond with a challenge c j c_j cj。
- 2) P \mathcal{P} P和 V \mathcal{V} V 均设置 g ′ ( X ) = g ( X , c 0 , c 1 , ⋯ , c n a − 1 ) g'(X)=g(X,c_0,c_1,\cdots,c_{n_a-1}) g′(X)=g(X,c0,c1,⋯,cna−1)。
- 3) P \mathcal{P} P 发送commitment R = ⟨ r , G ⟩ + [ ⋅ ] W R=\langle \mathbf{r},\mathbf{G}\rangle+[\cdot]W R=⟨r,G⟩+[⋅]W,其中 r ∈ F n \mathbf{r}\in\mathbb{F}^n r∈Fn 为degree n − 1 n-1 n−1 随机单变量多项式 r ( X ) r(X) r(X)的系数。
- 4) P \mathcal{P} P计算单变量多项式 h ( X ) = g ′ ( X ) t ( X ) h(X)=\frac{g'(X)}{t(X)} h(X)=t(X)g′(X) of degree n g ( n − 1 ) − n n_g(n-1)-n ng(n−1)−n。
- 5) P \mathcal{P} P 最多计算 n − 1 n-1 n−1 degree polynomials h 0 ( X ) , h 1 ( X ) , ⋯ , h n g − 2 ( X ) h_0(X),h_1(X),\cdots,h_{n_g-2}(X) h0(X),h1(X),⋯,hng−2(X),使得:
h ( X ) = ∑ i = 0 n g − 2 X n i h i ( X ) h(X)=\sum_{i=0}^{n_g-2}X^{ni}h_i(X) h(X)=∑i=0ng−2Xnihi(X)。 - 6)对于所有的 i i i, P \mathcal{P} P发送commitments H i = ⟨ h i , G ⟩ + [ ⋅ ] W H_i=\langle \mathbf{h_i},\mathbf{G}\rangle + [\cdot]W Hi=⟨hi,G⟩+[⋅]W,其中 h i \mathbf{h_i} hi表示 h i ( X ) h_i(X) hi(X)的系数向量。
- 7) V \mathcal{V} V responds with challenge x x x 并计算 H ′ = ∑ i = 0 n g − 2 [ x n i ] H i H'=\sum_{i=0}^{n_g-2}[x^{ni}]H_i H′=∑i=0ng−2[xni]Hi。
- 8) P \mathcal{P} P 设置 h ′ ( X ) = ∑ i = 0 n g − 2 X n i h i ( X ) h'(X)=\sum_{i=0}^{n_g-2}X^{ni}h_i(X) h′(X)=∑i=0ng−2Xnihi(X)。
- 9) P \mathcal{P} P 发送 r = r ( x ) r=r(x) r=r(x),对于所有的 i ∈ [ 0 , n a ) i\in[0,n_a) i∈[0,na),发送 a i \mathbf{a_i} ai使得 ( a i ) j = a i ′ ( ω ( p i ) j x ) (\mathbf{a_i})_j=a_i'(\omega^{(\mathbf{p_i})_j}x) (ai)j=ai′(ω(pi)jx) for all j ∈ [ 0 , n e ] j\in[0,n_e] j∈[0,ne]。
- 10)对于所有的 i ∈ [ 0 , n a ) i\in[0,n_a) i∈[0,na), P \mathcal{P} P和 V \mathcal{V} V 设置 s i ( X ) s_i(X) si(X)为the lowest degree univariate polynomial ,满足 s i ( ω ( p i ) j x ) = ( a i ) j s_i(\omega^{(\mathbf{p_i})_j}x)=(\mathbf{a_i})_j si(ω(pi)jx)=(ai)j for all j ∈ [ 0 , n e ) j\in[0,n_e) j∈[0,ne)。
- 11) V \mathcal{V} V responds with challenges x 1 , x 2 x_1,x_2 x1,x2,并初始化 Q 0 , Q 1 , ⋯ , Q n q − 1 = O Q_0,Q_1,\cdots,Q_{n_q-1}=\mathcal{O} Q0,Q1,⋯,Qnq−1=O。
- 从 i = 0 i=0 i=0开始到 n a − 1 n_a-1 na−1, V \mathcal{V} V 设置 Q σ ( i ) = [ x 1 ] Q σ ( i ) + A i Q_{\sigma(i)}=[x_1]Q_{\sigma(i)}+A_i Qσ(i)=[x1]Qσ(i)+Ai。
- V \mathcal{V} V 最终设置 Q 0 = [ x 1 2 ] Q i + [ x 1 ] H ′ + R Q_0=[x_1^2]Q_i+[x_1]H'+R Q0=[x12]Qi+[x1]H′+R。
- 12) P \mathcal{P} P 初始化 q 0 ( X ) , q 1 ( X ) , ⋯ , q n q − 1 = 0 q_0(X),q_1(X),\cdots,q_{n_q-1}=0 q0(X),q1(X),⋯,qnq−1=0。
- 从 i = 0 i=0 i=0开始到 n a − 1 n_a-1 na−1, P \mathcal{P} P设置 q σ ( i ) = x 1 q σ ( i ) + a ′ ( X ) q_{\sigma(i)}=x_1q_{\sigma(i)}+a'(X) qσ(i)=x1qσ(i)+a′(X)。
- P \mathcal{P} P最终设置 q 0 ( X ) = x 1 2 q 0 ( X ) + x 1 h ′ ( X ) + r ( X ) q_0(X)=x_1^2q_0(X)+x_1h'(X)+r(X) q0(X)=x12q0(X)+x1h′(X)+r(X)。
- 13) P \mathcal{P} P和 V \mathcal{V} V设置 r 0 ( X ) , r 1 ( X ) , ⋯ , r n q − 1 ( X ) = 0 r_0(X),r_1(X),\cdots,r_{n_q-1}(X)=0 r0(X),r1(X),⋯,rnq−1(X)=0。
- 从 i = 0 i=0 i=0开始到 n a − 1 n_a-1 na−1, P \mathcal{P} P和 V \mathcal{V} V 设置 r σ ( i ) = x 1 r σ ( i ) + s i ( X ) r_{\sigma(i)}=x_1r_{\sigma(i)}+s_i(X) rσ(i)=x1rσ(i)+si(X)。
- 最终 P \mathcal{P} P和 V \mathcal{V} V 设置 r 0 ( X ) = x 1 2 r 0 + x 1 h + r r_0(X)=x_1^2r_0+x_1h+r r0(X)=x12r0+x1h+r。其中, V \mathcal{V} V是使用 P \mathcal{P} P提供的 r , a r,\mathbf{a} r,a根据 g ′ ( x ) t ( x ) \frac{g'(x)}{t(x)} t(x)g′(x)来计算出 h h h的。
- 14) P \mathcal{P} P发送 Q ′ = ⟨ q ′ , G ⟩ + [ ⋅ ] W Q'=\langle \mathbf{q}',\mathbf{G}\rangle +[\cdot]W Q′=⟨q′,G⟩+[⋅]W,其中 q ′ \mathbf{q}' q′为如下多项式的系数:
q ′ ( X ) = ∑ i = 0 n q − 1 x 2 i ( q i ( X ) − r i ( X ) ∏ j = 0 n e − 1 ( X − ω ( q i ) j x ) ) q'(X)=\sum_{i=0}^{n_q-1}x_2^i\left( \frac {q_i(X) - r_i(X)} {\prod\limits_{j=0}^{n_e - 1} \left( X - \omega^{\left( \mathbf{q_i} \right)_j} x \right) } \right) q′(X)=∑i=0nq−1x2i⎝⎜⎛j=0∏ne−1(X−ω(qi)jx)qi(X)−ri(X)⎠⎟⎞ - 15) V \mathcal{V} V responds with challenge x 3 x_3 x3。
- 16) P \mathcal{P} P 发送 u ∈ F n q \mathbf{u}\in\mathbb{F}^{n_q} u∈Fnq,使得对于所有的 i ∈ [ 0 , n q ) i\in[0,n_q) i∈[0,nq),有 u i = q i ( x 3 ) \mathbf{u}_i=q_i(x_3) ui=qi(x3)。
- 17) V \mathcal{V} V responds with challenge x 4 x_4 x4。
- 18) P \mathcal{P} P和 V \mathcal{V} V 设置 P = Q ′ + x 4 ∑ i = 0 n q − 1 [ x 4 i ] Q i P = Q' + x_4 \sum\limits_{i=0}^{n_q - 1} [x_4^i] Q_i P=Q′+x4i=0∑nq−1[x4i]Qi and v = v = v=
∑ i = 0 n q − 1 ( x 2 i ( u i − r i ( x 3 ) ∏ j = 0 n e − 1 ( x 3 − ω ( q i ) j x ) ) ) + x 4 ∑ i = 0 n q − 1 x 4 u i \sum\limits_{i=0}^{n_q - 1} \left( x_2^i \left( \frac { \mathbf{u}_i - r_i(x_3) } {\prod\limits_{j=0}^{n_e - 1} \left( x_3 - \omega^{\left( \mathbf{q_i} \right)_j} x \right) } \right) \right)+ x_4 \sum\limits_{i=0}^{n_q - 1} x_4 \mathbf{u}_i i=0∑nq−1⎝⎜⎜⎜⎛x2i⎝⎜⎜⎜⎛j=0∏ne−1(x3−ω(qi)jx)ui−ri(x3)⎠⎟⎟⎟⎞⎠⎟⎟⎟⎞+x4i=0∑nq−1x4ui - 19) P \mathcal{P} P设置 p ( X ) = q ′ ( X ) + [ x 4 ] ∑ i = 0 n q − 1 x 4 i q i ( X ) p(X)=q'(X)+[x_4]\sum\limits_{i=0}^{n_q - 1} x_4^iq_i(X) p(X)=q′(X)+[x4]i=0∑nq−1x4iqi(X)。
- 20) P \mathcal{P} P samples a random polynomial s ( X ) s(X) s(X) of degree n − 1 n-1 n−1 with a root at x 3 x_3 x3 and sends a commitment S = ⟨ s , G ⟩ + [ ⋅ ] W S = \langle{\mathbf{s}},{\mathbf{G}}\rangle + [\cdot] W S=⟨s,G⟩+[⋅]W 其中 s \mathbf{s} s为 s ( X ) s(X) s(X)的系数。
- 21) V \mathcal{V} V responds with challenge ξ , z \xi,z ξ,z。
- 22) P \mathcal{P} P和 V \mathcal{V} V设置 P ′ = P − [ v ] G 0 + [ ξ ] S P'=P-[v]\mathbf{G}_0+[\xi]S P′=P−[v]G0+[ξ]S。
- 23) P \mathcal{P} P设置 p ′ ( X ) = p ( X ) − v + ξ s ( X ) p'(X)=p(X)-v+\xi s(X) p′(X)=p(X)−v+ξs(X)。
- 24)初始化 p ′ \mathbf{p}' p′为 p ′ ( X ) p'(X) p′(X)的系数, G ′ = G \mathbf{G}'=\mathbf{G} G′=G 且 b = ( x 3 0 , x 3 1 , ⋯ , x 3 n − 1 ) \mathbf{b}=(x_3^0,x_3^1,\cdots,x_3^{n-1}) b=(x30,x31,⋯,x3n−1)。 P \mathcal{P} P和 V \mathcal{V} V将进行 k k k轮以下交互,从 j = 0 j=0 j=0开始到 j = k − 1 j=k-1 j=k−1,对于其中的第 j j j轮,有:
- P \mathcal{P} P发送 L j = ⟨ p h i ′ , G l o ′ ⟩ + [ z ⟨ p h i ′ , b l o ⟩ ] U + [ ⋅ ] W L_j=\langle \mathbf{p}'_{hi},\mathbf{G}'_{lo}\rangle+[z\langle\mathbf{p}'_{hi}, \mathbf{b}_{lo}\rangle]U+[\cdot]W Lj=⟨phi′,Glo′⟩+[z⟨phi′,blo⟩]U+[⋅]W 和 R j = ⟨ p l o ′ , G h i ′ ⟩ + [ z ⟨ p l o ′ , b h i ⟩ ] U + [ ⋅ ] W R_j=\langle \mathbf{p}'_{lo},\mathbf{G}'_{hi}\rangle+[z\langle\mathbf{p}'_{lo}, \mathbf{b}_{hi}\rangle]U+[\cdot]W Rj=⟨plo′,Ghi′⟩+[z⟨plo′,bhi⟩]U+[⋅]W。
- V \mathcal{V} V responds with challenge u j u_j uj。
- P \mathcal{P} P和 V \mathcal{V} V设置 G ′ = G l o ′ + u j G h i ′ \mathbf{G}'=\mathbf{G}'_{lo}+u_j\mathbf{G}'_{hi} G′=Glo′+ujGhi′ 和 b = b l o + u j b h i \mathbf{b}=\mathbf{b}_{lo}+u_j\mathbf{b}_{hi} b=blo+ujbhi。
- P \mathcal{P} P设置 p ′ = p l o ′ + u j − 1 p h i ′ \mathbf{p}'=\mathbf{p}'_{lo}+u_j^{-1}\mathbf{p}'_{hi} p′=plo′+uj−1phi′。
- 25) P \mathcal{P} P发送 c = p 0 ′ c=\mathbf{p}'_0 c=p0′以及合成的blinding factor f f f。
- 26) V \mathcal{V} V accepts only if ∑ j = 0 k − 1 [ u j − 1 ] L j + P ′ + ∑ j = 0 k − 1 [ u j ] R j = [ c ] G ′ 0 + [ c b 0 z ] U + [ f ] W \sum_{j=0}^{k - 1} [u_j^{-1}] L_j + P' + \sum_{j=0}^{k - 1} [u_j] R_j = [c] \mathbf{G'}_0 + [c \mathbf{b}_0 z] U + [f] W ∑j=0k−1[uj−1]Lj+P′+∑j=0k−1[uj]Rj=[c]G′0+[cb0z]U+[f]W。