- Dashboard是运行于Pod对象中的应用,其连接APIServer的账户应为ServiceAccount类型
- 访问权限也取决于kubeconfig或token认证时的ServiceAccount用户的权限
- ServiceAccount的集群资源访问权限取决于它绑定的角色或集群角色
- 为登录的用户授权集群级别的管理权限时可直接绑定内建的集群角色cluster-admin
- 授权名称空间级别的管理权限时,可直接绑定内建的集群角色admin
dashboard部署
/opt/certs/
生成私钥
(umask 077;openssl genrsa -out dashboard.od.com.key 2048)
生成证书请求文件
openssl req -new -key dashboard.od.com.key -out dashboard.od.com.csr -subj "/CN=dashboard.od.com/C=CN/ST=BJ/L=Beijing/O=OldboyEdu/OU=ops"
生成证书
openssl x509 -req -in dashboard.od.com.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out dashboard.od.com.crt -days 3650
有负载均衡的操作
证书私钥存放位置
/etc/nginx/certs/dashboard.od.com.crt
/etc/nginx/certs/dashboard.od.com.key
vim /etc/nginx/conf.d/dashboard.od.com.conf
server {
listen 80;
server_name dashboard.od.com;
rewrite ^(.*)$ https://${server_name}$1 permanent;
}
server {
listen 443 ssl;
server_name dashboard.od.com;
ssl_certificate "certs/dashboard.od.com.crt";
ssl_certificate_key "certs/dashboard.od.com.key";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://default_backend_traefik;
proxy_set_header Host $http_host;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
}
}
vim /etc/nginx/conf.d/od.com.conf
upstream default_backend_traefik {
server 10.4.7.21:81 max_fails=3 fail_timeout=10s;
server 10.4.7.22:81 max_fails=3 fail_timeout=10s;
}
server {
server_name *.od.com;
location / {
proxy_pass http://default_backend_traefik;
proxy_set_header Host $http_host;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
}
}
Secret(无负载均衡此操作)
将 dashboard.od.com.key 和 dashboard.od.com.crt 放入 /certs
kubectl create secret generic kubernetes-dashboard-certs --from-file=/certs -n kube-system
查看secrets对应yaml格式
kubectl get secrets -n kube-system kubernetes-dashboard-certs-1 -o yaml
apiVersion: v1
data:
dashboard.od.com.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURSVENDQWkwQ0NRQ1RNWHZPSGJTeURUQU5CZ2txaGtpRzl3MEJBUXNGQURCZ01Rc3dDUVlEVlFRR0V3SkQKVGpFUU1BNEdBMVVFQ0JNSFltVnBhbWx1WnpFUU1BNEdBMVVFQnhNSFltVnBhbWx1WnpFTE1Ba0dBMVVFQ2hNQwpiMlF4RERBS0JnTlZCQXNUQTI5d2N6RVNNQkFHQTFVRUF4TUpUMnhrWW05NVJXUjFNQjRYRFRJd01EWXdNakUwCk5UYzBPVm9YRFRNd01EVXpNVEUwTlRjME9Wb3dhVEVaTUJjR0ExVUVBd3dRWkdGemFHSnZZWEprTG05a0xtTnYKYlRFTE1Ba0dBMVVFQmhNQ1EwNHhDekFKQmdOVkJBZ01Ba0pLTVJBd0RnWURWUVFIREFkQ1pXbHFhVzVuTVJJdwpFQVlEVlFRS0RBbFBiR1JpYjNsRlpIVXhEREFLQmdOVkJBc01BMjl3Y3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCCkJRQURnZ0VQQURDQ0FRb0NnZ0VCQU9ybFRiRzJuWDJvdzh3K2RmWkUxbDgwd1hzbVltRTBjZnJhTHZKeng2dGYKMldKMzU2dktJU01zZTQvNThwSVZjK3hIV3hvTWNneWxkUEs5b1hXV0c0YngvUGJBV1NQU0hpOU83cHgxOG5sOApiazFGOWYweUNYVlhaRVU1dW9YQ0psNUFDakxKeEs3SlBHSGNpSml5UWdwWFc4aHZCSFY4cVpLdkdnd0MwR2tBCjVGNGpGdkU3MFA3djhuWWhBQVF2WG9pWStpR3R6SXIyZStobzJob1NyTGN3cGZTb0FMYkJJeExyL2lKQkJYaVYKMGFWZXQyYnVkN3FsdW5rQ3lQRHU5Wmt1UlFwUHRqNnVBU0JXQ0dOU2FFS0gvdExRcFBaeVVweTBFenUwS0dXUwpIdzMxM3Q1OXlqRWVSV05SUkJrVlFwb0NFdDNPVVZaZlR6TTVTVW85VXMwQ0F3RUFBVEFOQmdrcWhraUc5dzBCCkFRc0ZBQU9DQVFFQUxnSFNsNnBvaWJJNkl6R05Qc09Ca1pySnBtRjc0d0NWL3VKK1dzd01hNld2NE9PdjlHQ00KVCttc0VYVkpXYzNOQjh2NFNhYzA0aTRUMk5LWExHeVpuUmYxOFpFZlJtZHBtSXdmV21aMk96UUlsMUVVR0FLSApQSDNiU2orc09meGN2RVk0U0I2NmFKSVV0M1dJQnZqQTJnNEMxVkViZlVJVTF2NFYwdlF5Q0lJL2M2SjVkNDFhCmhsRUtKS2ZpdWNEZTZSdmNRbCtoZUtKeGVYbHltNnZvOU1KSWRjMnJNdFJOVmtFbWk4K3VNR0d2eFBsVGtzQlEKRkJTS2srdnYwNW9xYkwvVU1jc21mWkNyMldqd295ZjNiYjZjY1Vlbk9IL2pYYmFEd0kxdzJ6MStmUGc0NkZhSQpxVGJ6YkhIbE0weWRNWGpTVWNSb1FlWlg4MlhTNmE4cXVBPT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
dashboard.od.com.key: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBNnVWTnNiYWRmYWpEekQ1MTlrVFdYelRCZXlaaVlUUngrdG91OG5QSHExL1pZbmZuCnE4b2hJeXg3ai9ueWtoVno3RWRiR2d4eURLVjA4cjJoZFpZYmh2SDg5c0JaSTlJZUwwN3VuSFh5ZVh4dVRVWDEKL1RJSmRWZGtSVG02aGNJbVhrQUtNc25FcnNrOFlkeUltTEpDQ2xkYnlHOEVkWHlwa3E4YURBTFFhUURrWGlNVwo4VHZRL3UveWRpRUFCQzllaUpqNklhM01pdlo3NkdqYUdoS3N0ekNsOUtnQXRzRWpFdXYrSWtFRmVKWFJwVjYzClp1NTN1cVc2ZVFMSThPNzFtUzVGQ2srMlBxNEJJRllJWTFKb1FvZiswdENrOW5KU25MUVRPN1FvWlpJZkRmWGUKM24zS01SNUZZMUZFR1JWQ21nSVMzYzVSVmw5UE16bEpTajFTelFJREFRQUJBb0lCQUU5dm1sVzJEdzZXeXhoQQpLejVNU3o3SkpZRlRHc1FLcTEwTStnRnVIQ0VkZWZOdDN6L2VURlNMejRHQ0lvRTZsZ2hhblRseTZnTFMxWGpkCm5rT1lydGgwNzNvMjFDNWorV2RBUnp0TU8rTFByTEdmTGpBaEFzZlc5UWJnSGU3c0dIT1pMcG04V0RKUHhZYkcKd0w3NjBaQ1R1R3RROSs0UGFYMDhrQTl0eURNcHZ4SDNQRWxBS0pYeDZITHlDYlNpWlhRZy9XanovbTYyUWtKRApxa0lKTVJJWE1XZ3NKakMvN1Z6bUN1VlFZT3U4VWdsaEpaTXVFOVFJRW52amo5T3JyZm5qRVBkWjdNVjRFWklmCnJlcDl1UEpLUkVBSU41WWJjcGx3TVhWdnFRSHRuQjFtOFNudURsbkJLWkIyWjZyVE1pYWhyQUJmMWhZSlNvcjgKczE5c3h4VUNnWUVBLzNIUVQycjJHSFFBUFR0dnJBa0RWU3lNcitlWWxVU3l2cm1EbFMyTkMyYjYxNVBFVUFJdQphekZlZXJlK29ickZCeHU1SU9LQVJ2c00yNEZXS1NpR3NYbnFOTjR5bG1CQm9rWEVxcXoyc3NsbmdlZllyTSsrCkdUN3BjSnVCNGF6ZlJub2pCNisyZjNxL295cjJGT1BxVGxIeXpvakoxY2ZiS2l4R2tUNEVBQk1DZ1lFQTYyZ04KUTQwYTgwRVFPdm83MDNLai9ZeHd6MmgzVmRwUWhxdERoSUM4aDU4QnJ1dmxpN1daaXlLbDkvNTF5K3FxSERkNwo1dFp4NjlYUGVpUWgrNzliYi9Cek54VURjaGdrK1lROEFWeWl6SVJPTy8rK096d0ExUStKa2lXbkczZnpDSUJpCkNtWi9Oak5NQ0lHME9sY0pTTEpVTWRhNUhybDdFaEd3QWs1b2ZaOENnWUFJMFE3Vmp1V0xsb1ZqbDZlVkVvS1EKOEFhekU1VktvYUpodnRseHpxNnRsQkpZV250T0g2VW1nZisyMEp5OXpFcDhvbEpUZGozak5Vc09VSHArMVMxQQo5dXBFaE43T0hlaG1CMjV3VGFQK0s4RnMxR25BSFROOGY1VmpFNXI2QlJOM3hVTnNRbjVVREJLTk9UQmhMRFNzCkcxdjhFUENXZGwxMEtTOE9XRXVmRFFLQmdRRFUvd2JSVWtGS1RGcUZJcGt6RHcxMmdyWW4xRnYxb0Ywd0hKSXcKdDlMZDIyOUllRVR3RGxacFgrWlA1enRxVUYrdXZEMHRkbWNKZmlJR1g5OG55OUxPREFBVG5MM0xaREZBV3ZkNApPL3RKbFlTOElRQmMxRVBrZy9SeitnR2podnF0Zkl3NDROakZqOUNCK2VtNng3bXN2ejRUQWpmcHB1WEdTWjY1CjEzd1AvUUtCZ0czTTdPTVlsOTBTQmtlTFllNFZPZG1tYlh4bHY1MnRmbHpielc0cDZDYm1GTk5WaVpUUWgvSFoKUis4QVBNODN4NEg4K2xuMFR3MktVSDk0ZTQzZlcrcmNqeU9Qdy9PUDZZekowUFJobDFzRTI3UEJXRzJPcDBtMgpyUXgrcTYzRWwxRDVSQUtEME1QZTVMbHZ4T1RsNVFncXA4T2YwK2hDRTFpUWhpMy9YZGlyCi0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
kind: Secret
metadata:
name: kubernetes-dashboard-certs-1
namespace: kube-system
type: Opaque
密文解密
echo "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURSVENDQWkwQ0NRQ1RNWHZPSGJTeURUQU5CZ2txaGtpRzl3MEJBUXNGQURCZ01Rc3dDUVlEVlFRR0V3SkQKVGpFUU1BNEdBMVVFQ0JNSFltVnBhbWx1WnpFUU1BNEdBMVVFQnhNSFltVnBhbWx1WnpFTE1Ba0dBMVVFQ2hNQwpiMlF4RERBS0JnTlZCQXNUQTI5d2N6RVNNQkFHQTFVRUF4TUpUMnhrWW05NVJXUjFNQjRYRFRJd01EWXdNakUwCk5UYzBPVm9YRFRNd01EVXpNVEUwTlRjME9Wb3dhVEVaTUJjR0ExVUVBd3dRWkdGemFHSnZZWEprTG05a0xtTnYKYlRFTE1Ba0dBMVVFQmhNQ1EwNHhDekFKQmdOVkJBZ01Ba0pLTVJBd0RnWURWUVFIREFkQ1pXbHFhVzVuTVJJdwpFQVlEVlFRS0RBbFBiR1JpYjNsRlpIVXhEREFLQmdOVkJBc01BMjl3Y3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCCkJRQURnZ0VQQURDQ0FRb0NnZ0VCQU9ybFRiRzJuWDJvdzh3K2RmWkUxbDgwd1hzbVltRTBjZnJhTHZKeng2dGYKMldKMzU2dktJU01zZTQvNThwSVZjK3hIV3hvTWNneWxkUEs5b1hXV0c0YngvUGJBV1NQU0hpOU83cHgxOG5sOApiazFGOWYweUNYVlhaRVU1dW9YQ0psNUFDakxKeEs3SlBHSGNpSml5UWdwWFc4aHZCSFY4cVpLdkdnd0MwR2tBCjVGNGpGdkU3MFA3djhuWWhBQVF2WG9pWStpR3R6SXIyZStobzJob1NyTGN3cGZTb0FMYkJJeExyL2lKQkJYaVYKMGFWZXQyYnVkN3FsdW5rQ3lQRHU5Wmt1UlFwUHRqNnVBU0JXQ0dOU2FFS0gvdExRcFBaeVVweTBFenUwS0dXUwpIdzMxM3Q1OXlqRWVSV05SUkJrVlFwb0NFdDNPVVZaZlR6TTVTVW85VXMwQ0F3RUFBVEFOQmdrcWhraUc5dzBCCkFRc0ZBQU9DQVFFQUxnSFNsNnBvaWJJNkl6R05Qc09Ca1pySnBtRjc0d0NWL3VKK1dzd01hNld2NE9PdjlHQ00KVCttc0VYVkpXYzNOQjh2NFNhYzA0aTRUMk5LWExHeVpuUmYxOFpFZlJtZHBtSXdmV21aMk96UUlsMUVVR0FLSApQSDNiU2orc09meGN2RVk0U0I2NmFKSVV0M1dJQnZqQTJnNEMxVkViZlVJVTF2NFYwdlF5Q0lJL2M2SjVkNDFhCmhsRUtKS2ZpdWNEZTZSdmNRbCtoZUtKeGVYbHltNnZvOU1KSWRjMnJNdFJOVmtFbWk4K3VNR0d2eFBsVGtzQlEKRkJTS2srdnYwNW9xYkwvVU1jc21mWkNyMldqd295ZjNiYjZjY1Vlbk9IL2pYYmFEd0kxdzJ6MStmUGc0NkZhSQpxVGJ6YkhIbE0weWRNWGpTVWNSb1FlWlg4MlhTNmE4cXVBPT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=" |base64 -d > 123.pem
验证证书
cfssl-certinfo -cert 123.pem
Secret(有负载均衡此操作)
vi /data/k8s-yaml/dashboard/secret.yaml
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
# Allows editing resource and makes sure it is created first.
addonmanager.kubernetes.io/mode: EnsureExists
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
RBAC
vi /data/k8s-yaml/dashboard/rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin
namespace: kube-system
deployment
vi /data/k8s-yaml/dashboard/deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ''
spec:
priorityClassName: system-cluster-critical
containers:
- name: kubernetes-dashboard
image: harbor.od.com/public/dashboard:v1.10.1
resources:
limits:
cpu: 100m
memory: 300Mi
requests:
cpu: 50m
memory: 100Mi
ports:
- containerPort: 8443
protocol: TCP
args:
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
- name: tmp-volume
mountPath: /tmp
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {
}
serviceAccountName: kubernetes-dashboard-admin
tolerations:
- key: "CriticalAddonsOnly"
operator: "Exists"
imagePullSecrets:
- name: harbor
service
vi /data/k8s-yaml/dashboard/svc.yaml
apiVersion: v1
kind: Service
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
k8s-app: kubernetes-dashboard
ports:
- port: 443
targetPort: 8443
ingress
vi /data/k8s-yaml/dashboard/ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: kubernetes-dashboard
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: dashboard.od.com
http:
paths:
- backend:
serviceName: kubernetes-dashboard
servicePort: 443
获取token登录dashboard
kubectl get secrets -n kube-system
NAME TYPE DATA AGE
coredns-token-cmv2k kubernetes.io/service-account-token 3 37d
default-token-k9tht kubernetes.io/service-account-token 3 38d
heapster-token-sdl5m kubernetes.io/service-account-token 3 35d
kube-state-metrics-token-9cnvq kubernetes.io/service-account-token 3 30d
kubernetes-dashboard-admin-token-4hmt9 kubernetes.io/service-account-token 3 37d
kubernetes-dashboard-certs Opaque 0 37d
kubernetes-dashboard-key-holder Opaque 2 37d
kubernetes-dashboard-token-rcn6w kubernetes.io/service-account-token 3 35d
traefik-ingress-controller-token-r6mtr kubernetes.io/service-account-token 3 37d
查看这个secrets
kubernetes-dashboard-admin-token-4hmt9
kubectl describe secrets -n kube-system kubernetes-dashboard-admin-token-4hmt9
Name: kubernetes-dashboard-admin-token-4hmt9
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: kubernetes-dashboard-admin
kubernetes.io/service-account.uid: 5fb39275-a05c-472e-bf63-25b8e9e7df62
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1346 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC1hZG1pbi10b2tlbi00aG10OSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjVmYjM5Mjc1LWEwNWMtNDcyZS1iZjYzLTI1YjhlOWU3ZGY2MiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTprdWJlcm5ldGVzLWRhc2hib2FyZC1hZG1pbiJ9.YhO5mlQsA6qJz25_46L_yBPUnGwQO8YMwvrGnWxxYMzxnEJEhuQmJU2uaGpVuW389SL1t0FNsRh0TqRv--oEGcMqNqAKUf7Lx41OriCqx4H69JvjcC9l_t0Q9wZQiBR2zsWPuiRcxYpW-SmdAwudZsyIk-Wf7hxjUQ1vDw5woHC7fhg0I4vCQwWwxbYzYhuQ1r8MsdP_2IqDhX_RY1XyHf7vzCxkDsYP652W-KvvcTe8uU8ZeE0LcFt5wJk22-WxPVnTBsM20Y_0PPyqIKlJ_EdX31pnIwpIlLVPtGeKk56xjZFxslcdNPJZKD6SFUABtlRTT5wz0InhvFOZuZtdqQ
普通认证
创建serviceaccount
kubectl create serviceaccount def-ns-admin -n default
创建rolebinding
kubectl create rolebinding def-ns-admin --clusterrole=admin --serviceaccount=default:def-ns-admin
查看secrets
kubectl get secrets
NAME TYPE DATA AGE
def-ns-admin-token-w9qr2 kubernetes.io/service-account-token 3 84s
default-token-vx4pr kubernetes.io/service-account-token 3 39d
查看token
kubectl describe secrets def-ns-admin-token-w9qr2
Name: def-ns-admin-token-w9qr2
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: def-ns-admin
kubernetes.io/service-account.uid: f8a61824-2f28-476d-a571-c617d058dcb6
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1346 bytes
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1hZG1pbi10b2tlbi13OXFyMiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWYtbnMtYWRtaW4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJmOGE2MTgyNC0yZjI4LTQ3NmQtYTU3MS1jNjE3ZDA1OGRjYjYiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkZWYtbnMtYWRtaW4ifQ.txWzIET1i7wErd25q83IvuizjHi_OwaSDnxYkauICYXAFDomRn4USNLAbqM6fqE_CzXqaSkZmiUlk0I0dm1lzlqwfd8BxukDovH8Jqk8jaubWJcU6GXtfewsJF6zsEvX-wKcog7nuEnpu7OfIbsKbYMXmDXNq_XUWJWfm8LPxp9JaKKTbV8stbe3UQhyC06C4vO_CLgerw5TnnLw_UNnprVI-AS4po6NSqsTxRWnar3J-wigL0zGkxgkXLMQGFYgHl9YjelBThMjwx7JnzK0GMT47pW-qv9epP3o4hJ3rvxCS5rW7eet0qpvWMOMPnoV5xSWo4Pj7goCtB9ip1KAIg
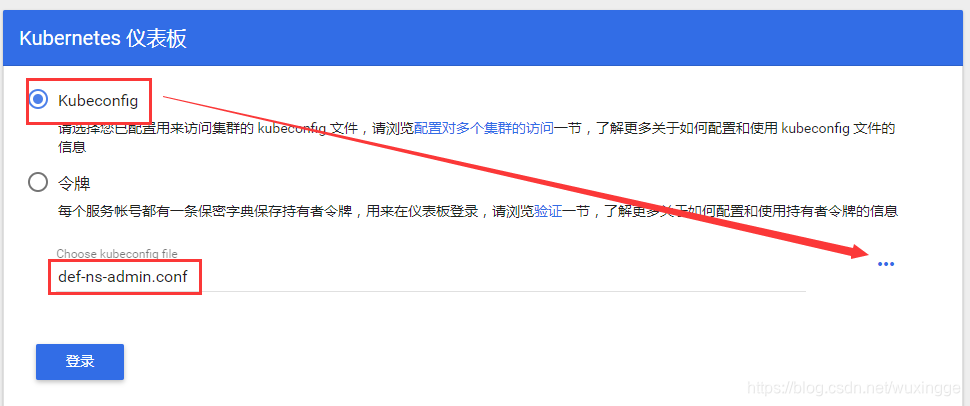
生成Kubeconfig文件
设置集群
kubectl config set-cluster kubernetes --certificate-authority=/opt/kubernetes/server/bin/cert/ca.pem --server=https://10.4.7.10:7443 --embed-certs=true --kubeconfig=/root/def-ns-admin.conf
设置用户
DEF_NS_ADMIN_TOKEN=$(kubectl get secrets def-ns-admin-token-w9qr2 -o jsonpath={
.data.token} |base64 -d)
kubectl config set-credentials def-ns-admin --token=$DEF_NS_ADMIN_TOKEN --kubeconfig=/root/def-ns-admin.conf
设置context
kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=/root/def-ns-admin.conf
使用context
kubectl config use-context def-ns-admin@kubernetes --kubeconfig=/root/def-ns-admin.conf
此文件(def-ns-admin.conf)为k8s认证文件
Kubeconfig文件认证