REVERSE-PRACTICE-BUUCTF-9
[ACTF新生赛2020]usualCrypt
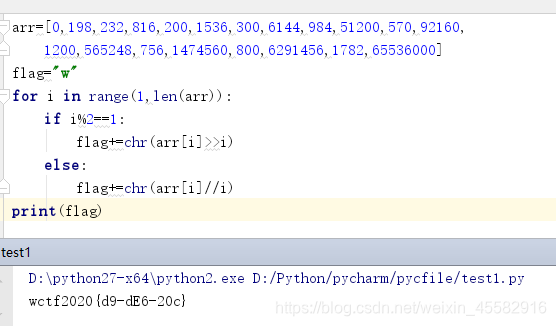
exe程序,运行后提示输入flag,无壳,ida分析
main函数逻辑清晰,获取输入,sub_401080函数对输入进行变表base64变换,结果存储到v5,然后check,验证输入
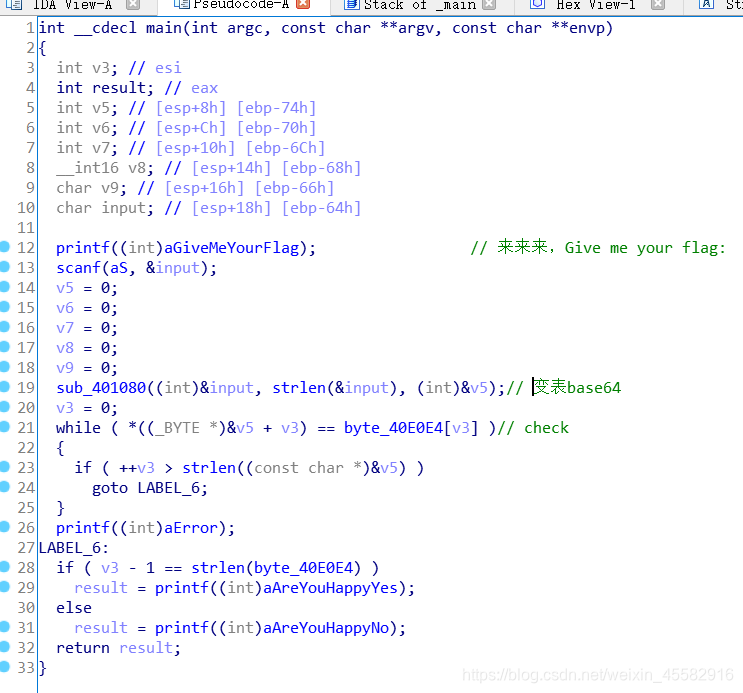
sub_401080函数是很明显的base64,在函数开始部分,sub_401000函数对表进行了变换,在函数结束返回部分,sub_401030函数对变表后的base64字符串进行了英文字母的大小写转换
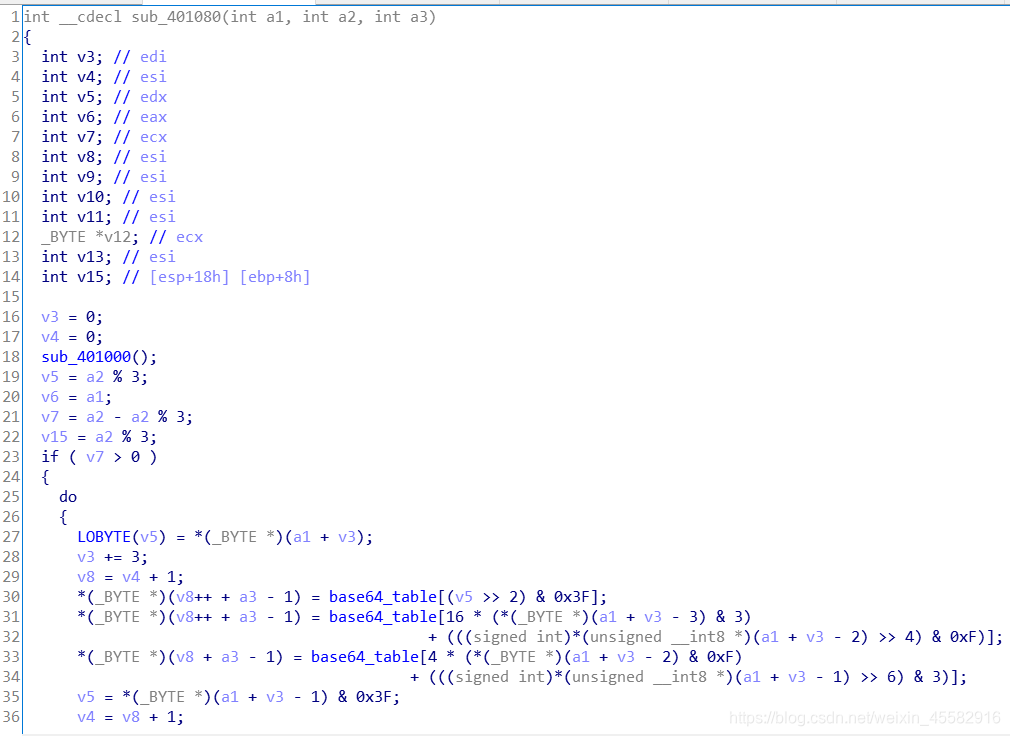
sub_401000函数,将byte_40E0AA[6]到byte_40E0AA[14]和base64_table[6]到base64_table[14]两段交换
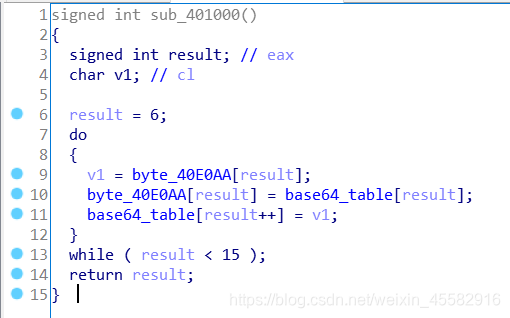
sub_401030函数,对变表后的base64字符串英文字母的大小写转换,其他字符不变
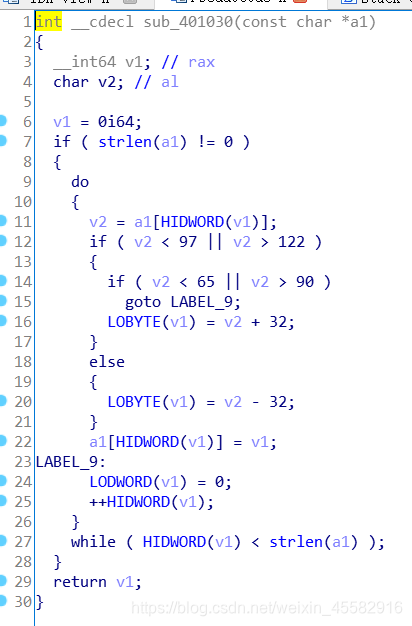
写脚本即可得到flag
#coding:utf-8
#base="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" 原表
base=[0x41, 0x42, 0x43, 0x44, 0x45, 0x46, 0x47, 0x48, 0x49, 0x4A,
0x4B, 0x4C, 0x4D, 0x4E, 0x4F, 0x50, 0x51, 0x52, 0x53, 0x54,
0x55, 0x56, 0x57, 0x58, 0x59, 0x5A, 0x61, 0x62, 0x63, 0x64,
0x65, 0x66, 0x67, 0x68, 0x69, 0x6A, 0x6B, 0x6C, 0x6D, 0x6E,
0x6F, 0x70, 0x71, 0x72, 0x73, 0x74, 0x75, 0x76, 0x77, 0x78,
0x79, 0x7A, 0x30, 0x31, 0x32, 0x33, 0x34, 0x35, 0x36, 0x37,
0x38, 0x39, 0x2B, 0x2F] #原表的ascii码表示,方便进行原表变换
#对原表进行变换
for i in range(6,15):
base[i],base[10+i]=base[10+i],base[i]
#base_changed是变表,需要转成字符串的形式
base_changed=''.join(chr(i) for i in base)
print("Current Base:\n%s " %base_changed) #打印base_changed变表
def base64_decode(inputs): #inputs是base64字符串
# 将字符串转化为2进制
bin_str = []
for i in inputs:
if i != '=':
x = str(bin(base_changed.index(i))).replace('0b', '')
bin_str.append('{:0>6}'.format(x))
# 输出的字符串
outputs = ""
nums = inputs.count('=')
while bin_str:
temp_list = bin_str[:4]
temp_str = "".join(temp_list)
# 补足8位字节
if (len(temp_str) % 8 != 0):
temp_str = temp_str[0:-1 * nums * 2]
# 将四个6字节的二进制转换为三个字符
for i in range(0, int(len(temp_str) / 8)):
outputs += chr(int(temp_str[i * 8:(i + 1) * 8], 2))
bin_str = bin_str[4:]
print("Decoded String:\n%s " % outputs)
#enc是经变表base64以及大小写转换后的字符串
enc="zMXHz3TIgnxLxJhFAdtZn2fFk3lYCrtPC2l9"
#c将enc大小写转换回去 再解变表base64
c=""
for i in enc:
if i.isupper():
c+=i.lower()
elif i.islower():
c+=i.upper()
else:
c+=i
base64_decode(c)
运行结果
[MRCTF2020]Transform
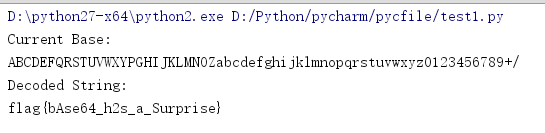
exe程序,运行后提示输入code,输入错误打印Wrong,无壳,ida分析
main函数逻辑清晰,获取输入,检验输入的长度,对输入的内容变换位置后存储到byte_414040,byte_414040再异或一下,最后check
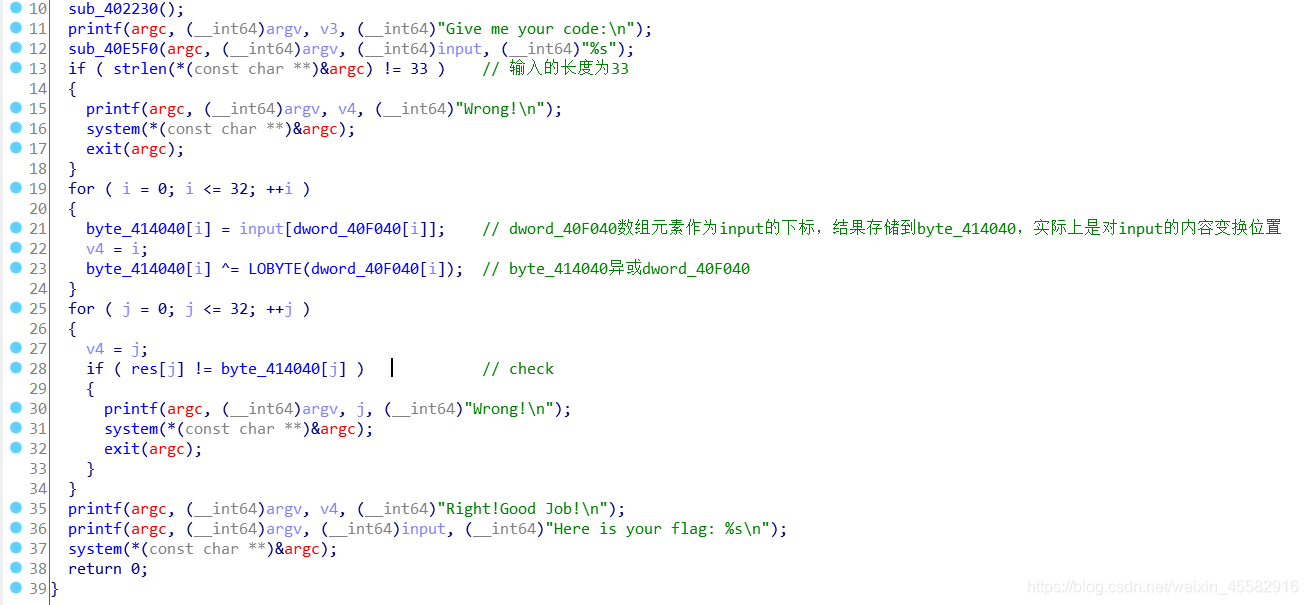
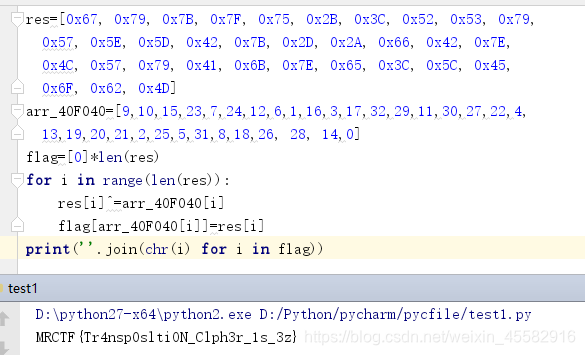
写脚本即可得到flag
[V&N2020 公开赛]CSRe
exe程序,运行出错
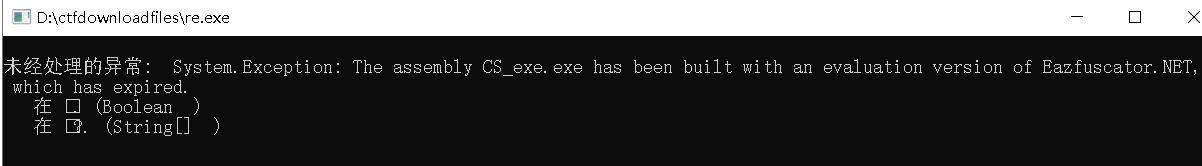
查壳,发现是.NET,而且加了de4dot壳
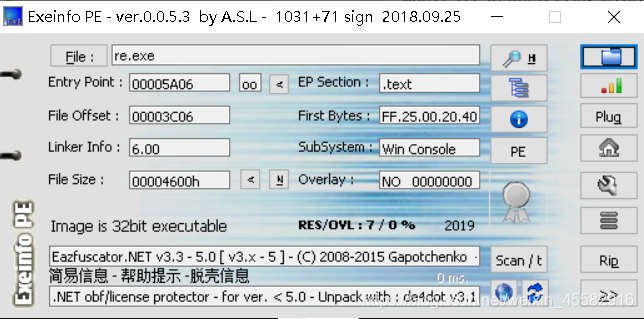
脱壳后用dnSpy打开,找到主逻辑函数
method_0函数是将两个传入的参数顺序异或的结果返回
smethod_0函数是对传入的参数进行sha1散列的结果返回
main函数,先获取输入的str,头部加个“3”,尾部加个“9”,拼接后的字符串进行sha1散列,与已知的值比较,验证输入的str是否正确
再获取输入的text,头部加“re”,拼接后的字符串进行sha1散列,散列的结果与已知的值进行异或,结果为全0,说明两个传入的参数完全相同,验证输入的text是否正确
flag即为flag{str+text}
using System;
using System.Security.Cryptography;
using System.Text;
// Token: 0x02000006 RID: 6
internal sealed class Class3
{
// Token: 0x0600000D RID: 13 RVA: 0x000022C8 File Offset: 0x000004C8
public string method_0(string string_0, string string_1)
{
string text = string.Empty;
char[] array = string_0.ToCharArray();
char[] array2 = string_1.ToCharArray();
int num = (array.Length < array2.Length) ? array.Length : array2.Length;
for (int i = 0; i < num; i++)
{
text += (int)(array[i] ^ array2[i]);
}
return text;
}
// Token: 0x0600000E RID: 14 RVA: 0x0000231C File Offset: 0x0000051C
public static string smethod_0(string string_0)
{
byte[] bytes = Encoding.UTF8.GetBytes(string_0);
byte[] array = SHA1.Create().ComputeHash(bytes);
StringBuilder stringBuilder = new StringBuilder();
foreach (byte b in array)
{
stringBuilder.Append(b.ToString("X2"));
}
return stringBuilder.ToString();
}
// Token: 0x0600000F RID: 15 RVA: 0x00002374 File Offset: 0x00000574
private static void Main(string[] args)
{
if (!Class1.smethod_1())
{
return;
}
bool flag = true;
Class3 @class = new Class3();
string str = Console.ReadLine();
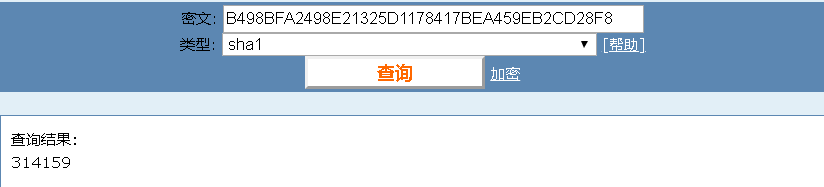
if (Class3.smethod_0("3" + str + "9") != "B498BFA2498E21325D1178417BEA459EB2CD28F8")
{
flag = false;
}
string text = Console.ReadLine();
string string_ = Class3.smethod_0("re" + text);
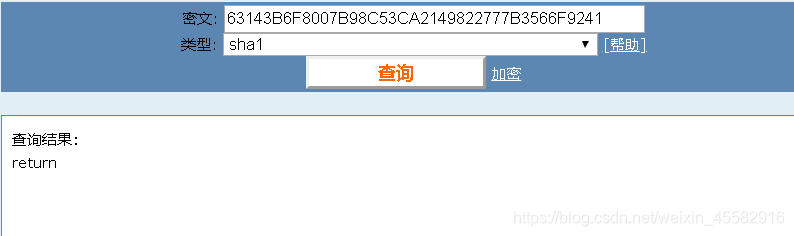
string text2 = @class.method_0(string_, "63143B6F8007B98C53CA2149822777B3566F9241");
for (int i = 0; i < text2.Length; i++)
{
if (text2[i] != '0')
{
flag = false;
}
}
if (flag)
{
Console.WriteLine("flag{" + str + text + "}");
}
}
}
用在线网站解第一段sha1,可知str为“1415”
用在线网站解第二段sha1,可知text为“turn”
[WUSTCTF2020]level1
elf文件,无壳,ida分析
main函数逻辑清晰,从文件读取flag,下标从1开始,下标为奇数,flag的内容移位,下标为偶数,flag的内容乘以下标
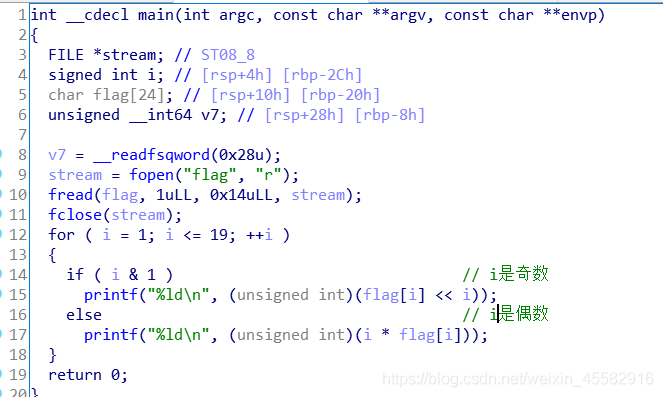
写脚本即可得到flag