Scanning and Enumeration
INFORMATION GATHERING
- Scanning
- Process of looking at some number of "things" to determine characteristics
- Commonly used in pen testing to uncover target vulnerabilities
- Many types of scan targets
- Networks
- Network devices
- Computers
- Applications/services
Enumeration
- Counting the detected instances of some target class
- Pen testing target classes
- Hosts
- Networks
- Domains
- Users
- Groups
- Network shares
- Web pages
- Applications
- Services
- Tokens
- Social networking sites
QUICK REVIEW
- Scanning helps to determine what is "out there"
- Don't just scan for computers - look for all devices and services
- Start collecting and classifying target information
- Use more than just utilities that scan networks
Demo
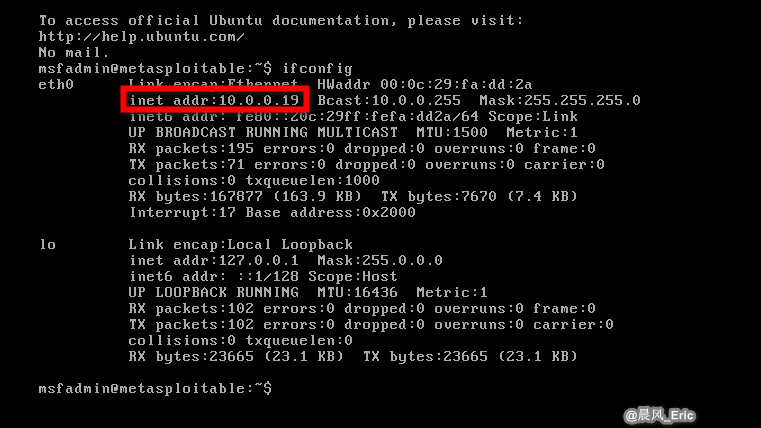
Target 1: Metasploitable VM
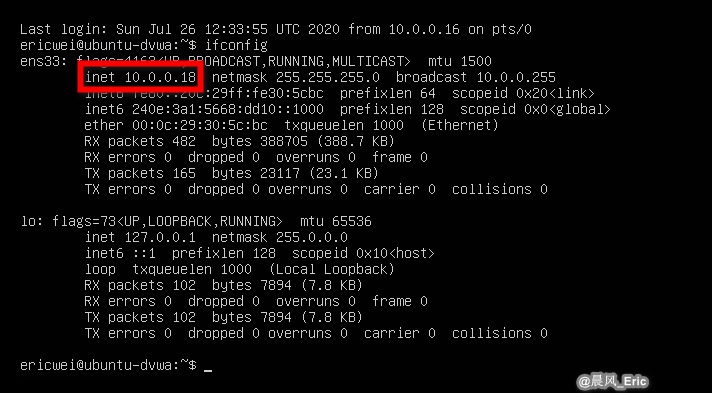
Target 2: DVWA VM
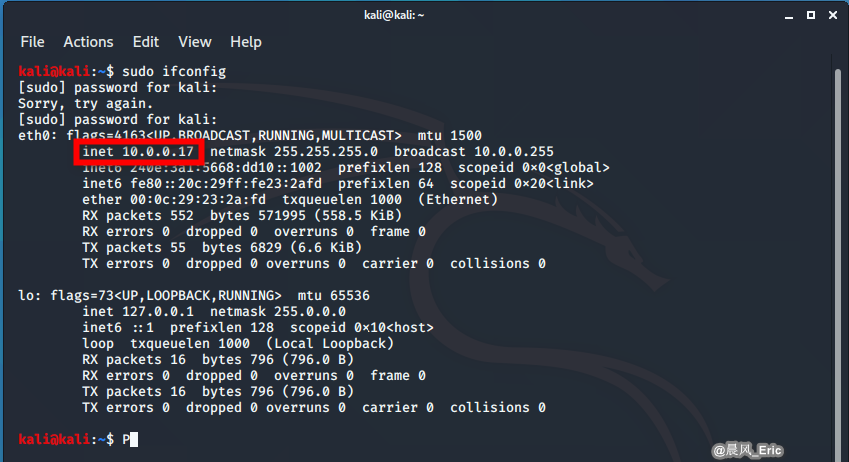
Attacker: Kali Linux VM
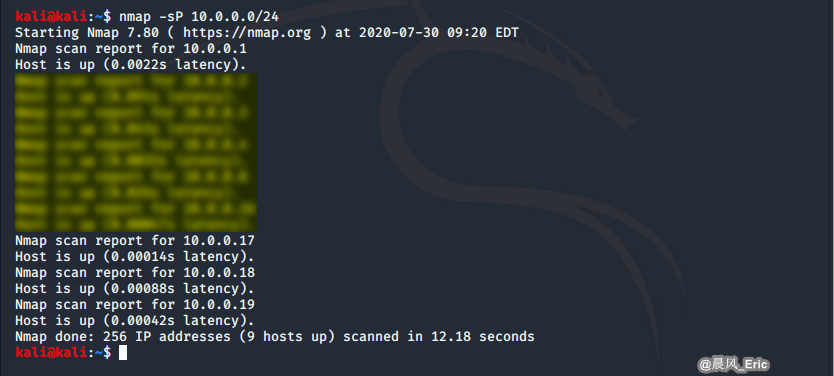
Scan Method 1 - nmap
nmap -sP 10.0.0.0/24
Scan Method 2 - ARP
arp-scan 10.0.0.0/24
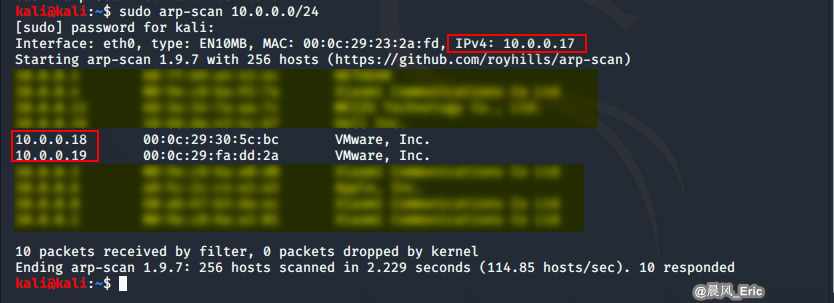
Scan Method 3 - Whois Lookup http://whois.domaintools.com/
QUICK REVIEW
- nmap is the most common tool you'll see
- Know how to use nmap and what the main options do
- Be able to explain nmap output