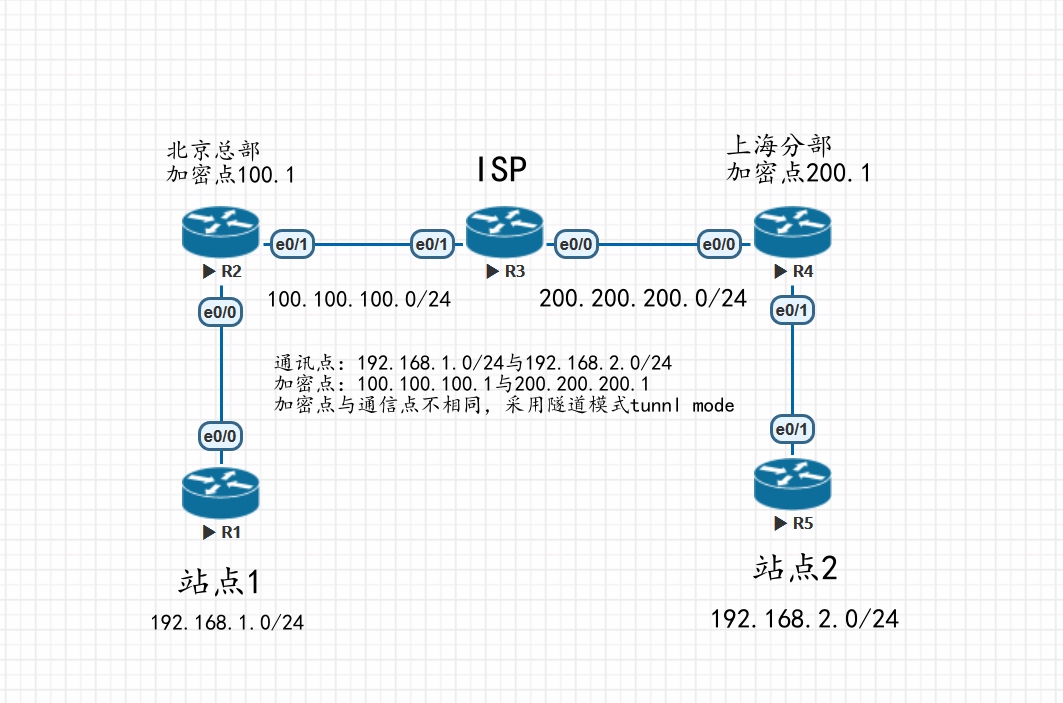
拓扑图
R1
interface Ethernet0/0
ip address 192.168.1.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 192.168.1.254
R2
interface Ethernet0/0
ip address 192.168.1.254 255.255.255.0
interface Ethernet0/1
ip address 100.100.100.1 255.255.255.0
crypto map ipsec
ip route 192.168.2.0 255.255.255.0 100.100.100.254 #去往远端通信点路由
ip route 200.200.200.0 255.255.255.0 100.100.100.254 #去往远端加密点路由
配置L2L-IPSec
配置ISAKMP SA 第一阶段策略
R2(config)#crypto isakmp enable #激活ISAKMP,默认开启
R2(config)#crypto isakmp policy 10 #建立isakmp优先级
R2(config-isakmp)#encryption 3des #IKE数据包的加密算法 默认des
R2(config-isakmp)#hash md5 #IKE数据包完整性校验 默认sha
R2(config-isakmp)#authentication pre-share #定义验证的方式域共享密钥 默认rsa-sig
R2(config-isakmp)#group 2 #DH组强度 默认1
默认lifetime为一天,不建议修改
配置ISAKMP 预共享密码
R2(config)#crypto isakmp key cisco address 0.0.0.0 #配置密钥,此处配置远端加密点,为了方便我这里写成了匹配所有。
配置第二阶段,IPSEC SA
配置感兴趣流
R2(config)#ip access-list extended ipsec
R2(config-ext-nacl)#permit ip permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
配置 配置IPSec 策略(转换集)
R2(config)#crypto ipsec transform-set ipsec esp-3des esp-md5-hmac #此处确定了感兴趣流实际的加密和认证算法
R2(cfg-crypto-trans)#mode tunnel #默认是隧道模式
配置 配置Crypto map
R2(config)#crypto map ipsec 10 ipsec-isakmp
R2(config-crypto-map)#match address ipsec #匹配感兴趣流量
R2(config-crypto-map)#set transform-set ipsec #匹配转换集ipsec策略
R2(config-crypto-map)#set peer 200.200.200.1 #匹配远端加密点
调用Crypto map
R2(config)#interface e0/0
R2(config-if)#crypto map ipsec
R3
interface Ethernet0/0
ip address 200.200.200.254 255.255.255.0
!
interface Ethernet0/1
ip address 100.100.100.254 255.255.255.0
R4
interface Ethernet0/0
ip address 200.200.200.1 255.255.255.0
crypto map ipsec
!
interface Ethernet0/1
ip address 192.168.2.254 255.255.255.0
ip route 100.100.100.0 255.255.255.0 200.200.200.254
ip route 192.168.1.0 255.255.255.0 200.200.200.254
配置L2L-IPSec 此处同R2,就不做详细介绍
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key l2lkey address 0.0.0.0
ip access-list extended ipsec
permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
crypto ipsec transform-set ipsec esp-3des esp-md5-hmac
mode tunnel
crypto map ipsec 10 ipsec-isakmp
set peer 100.100.100.1
set transform-set ipsec
match address ipsec
R5
interface Ethernet0/1
ip address 192.168.2.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 192.168.2.254
在R2上查看ipsec配置
R2# show crypto session
Crypto session current status
Interface: Ethernet0/1
Session status: UP-ACTIVE
Peer: 200.200.200.1 port 500
IKEv1 SA: local 100.100.100.1/500 remote 200.200.200.1/500 Active
IPSEC FLOW: permit ip 192.168.1.0/255.255.255.0 192.168.2.0/255.255.255.0
Active SAs: 2, origin: crypto map
R2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
200.200.200.1 100.100.100.1 QM_IDLE 1001 ACTIVE
R2#show crypto isakmp policy
Global IKE policy
Protection suite of priority 10
encryption algorithm: Three key triple DES
hash algorithm: Message Digest 5
authentication method: Pre-Shared Key
Diffie-Hellman group: #2 (1024 bit)
lifetime: 86400 seconds, no volume limit
测试R1站点是否可以访问R5站点
R1#ping 192.168.2.1 repeat 10
Type escape sequence to abort.
Sending 10, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 1/1/2 ms