一、介绍
在前面分析了MSP的基本的流程和源码,但是还是有些疏漏,这里补充一下,同时把相关的BCCSP的部分分析一下,充实整个的加密系统。在MSP中主要对配置管理和证书验证进行一下分析;BCCSP则从整体流程和相关源码进行一下分析。
二、MSP的补遗
1、配置管理
在前面的Peer节点的启动里,从主函数里mainCmd.AddCommand(node.Cmd()),而在node.Cmd()中会有:
var nodeCmd = &cobra.Command{
Use: nodeFuncName,
Short: fmt.Sprint(nodeCmdDes),
Long: fmt.Sprint(nodeCmdDes),
PersistentPreRun: common.InitCmd,
}
在PersistentPreRun(即common.Initcmd)中调用InitCrypto(mspMgrConfigDir, mspID, mspType)。
其流程为:调用mainCmd.Execute(),从这里开始其实已经是第三方的命令库cobra,会逐次调用ExecuteC–>cmd.execute,在这个函数里调用PersistentPreRun(common.InitCmd)。其又会调用InitCrypto这个函数:
看一下这个函数:
//fabric\peer\common\common.go
// InitCrypto initializes crypto for this peer
func InitCrypto(mspMgrConfigDir, localMSPID, localMSPType string) error {
var err error
// Check whether msp folder exists
fi, err := os.Stat(mspMgrConfigDir)
if os.IsNotExist(err) || !fi.IsDir() {
// No need to try to load MSP from folder which is not available
return errors.Errorf("cannot init crypto, folder \"%s\" does not exist", mspMgrConfigDir)
}
// Check whether localMSPID exists
if localMSPID == "" {
return errors.New("the local MSP must have an ID")
}
// Init the BCCSP
SetBCCSPKeystorePath()
var bccspConfig *factory.FactoryOpts
err = viperutil.EnhancedExactUnmarshalKey("peer.BCCSP", &bccspConfig)
if err != nil {
return errors.WithMessage(err, "could not parse YAML config")
}
err = mspmgmt.LoadLocalMspWithType(mspMgrConfigDir, bccspConfig, localMSPID, localMSPType)
if err != nil {
return errors.WithMessage(err, fmt.Sprintf("error when setting up MSP of type %s from directory %s", localMSPType, mspMgrConfigDir))
}
return nil
}
这个函数其实就是开始了加密的初始化,这其中肯定会包括相关的配置:
// LoadLocalMspWithType loads the local MSP with the specified type from the specified directory
func LoadLocalMspWithType(dir string, bccspConfig *factory.FactoryOpts, mspID, mspType string) error {
if mspID == "" {
return errors.New("the local MSP must have an ID")
}
conf, err := msp.GetLocalMspConfigWithType(dir, bccspConfig, mspID, mspType)
if err != nil {
return err
}
return GetLocalMSP().Setup(conf)
}
// GetLocalMspConfigWithType returns a local MSP
// configuration for the MSP in the specified
// directory, with the specified ID and type
func GetLocalMspConfigWithType(dir string, bccspConfig *factory.FactoryOpts, ID, mspType string) (*msp.MSPConfig, error) {
switch mspType {
case ProviderTypeToString(FABRIC):
return GetLocalMspConfig(dir, bccspConfig, ID)
case ProviderTypeToString(IDEMIX):
return GetIdemixMspConfig(dir, ID)
default:
return nil, errors.Errorf("unknown MSP type '%s'", mspType)
}
}
最后都会调用:
func GetLocalMspConfig(dir string, bccspConfig *factory.FactoryOpts, ID string) (*msp.MSPConfig, error) {
//签名者身份证书文件路径
signcertDir := filepath.Join(dir, signcerts)
//私钥存储文件路径
keystoreDir := filepath.Join(dir, keystore)
//基于私钥文件位置来创建BCCSP配置对象
bccspConfig = SetupBCCSPKeystoreConfig(bccspConfig, keystoreDir)
//由创建的BCCSP对象来初始化BCCSP工厂组件
err := factory.InitFactories(bccspConfig)
if err != nil {
return nil, errors.WithMessage(err, "could not initialize BCCSP Factories")
}
//从指定的路径读取签名身份证书文件列表
signcert, err := getPemMaterialFromDir(signcertDir)
if err != nil || len(signcert) == 0 {
return nil, errors.Wrapf(err, "could not load a valid signer certificate from directory %s", signcertDir)
}
/* FIXME: for now we're making the following assumptions
1) there is exactly one signing cert
2) BCCSP's KeyStore has the private key that matches SKI of
signing cert
*/
//基于只有一个身份证书构建签名者身份ID信息
sigid := &msp.SigningIdentityInfo{PublicSigner: signcert[0], PrivateSigner: nil}
//构建MSP配置对象
return getMspConfig(dir, ID, sigid)
}
这个函数在前面已经分析过了。看一下最后一个函数:
func getMspConfig(dir string, ID string, sigid *msp.SigningIdentityInfo) (*msp.MSPConfig, error) {
//CA证书路径
cacertDir := filepath.Join(dir, cacerts)
//Administration证书路径
admincertDir := filepath.Join(dir, admincerts)
//中间CA证书路径
intermediatecertsDir := filepath.Join(dir, intermediatecerts)
//CRL可撤销证书路径
crlsDir := filepath.Join(dir, crlsfolder)
//配置文件路径
configile := filepath.Join(dir, configfilename)
//TLS认证CA证书路径
tlscacertDir := filepath.Join(dir, tlscacerts)
//TLS中间CA证书路径
tlsintermediatecertsDir := filepath.Join(dir, tlsintermediatecerts)
cacerts, err := getPemMaterialFromDir(cacertDir)
if err != nil || len(cacerts) == 0 {
return nil, errors.WithMessage(err, fmt.Sprintf("could not load a valid ca certificate from directory %s", cacertDir))
}
admincert, err := getPemMaterialFromDir(admincertDir)
if err != nil && !os.IsNotExist(err) {
return nil, errors.WithMessage(err, fmt.Sprintf("could not load a valid admin certificate from directory %s", admincertDir))
}
intermediatecerts, err := getPemMaterialFromDir(intermediatecertsDir)
if os.IsNotExist(err) {
mspLogger.Debugf("Intermediate certs folder not found at [%s]. Skipping. [%s]", intermediatecertsDir, err)
} else if err != nil {
return nil, errors.WithMessage(err, fmt.Sprintf("failed loading intermediate ca certs at [%s]", intermediatecertsDir))
}
//根据指定的路径来读取身份证书上所有的签名者身份证书文件列表Signcert(格式可能随版本变化 )
tlsCACerts, err := getPemMaterialFromDir(tlscacertDir)
tlsIntermediateCerts := [][]byte{}
if os.IsNotExist(err) {
mspLogger.Debugf("TLS CA certs folder not found at [%s]. Skipping and ignoring TLS intermediate CA folder. [%s]", tlsintermediatecertsDir, err)
} else if err != nil {
return nil, errors.WithMessage(err, fmt.Sprintf("failed loading TLS ca certs at [%s]", tlsintermediatecertsDir))
} else if len(tlsCACerts) != 0 {
tlsIntermediateCerts, err = getPemMaterialFromDir(tlsintermediatecertsDir)
if os.IsNotExist(err) {
mspLogger.Debugf("TLS intermediate certs folder not found at [%s]. Skipping. [%s]", tlsintermediatecertsDir, err)
} else if err != nil {
return nil, errors.WithMessage(err, fmt.Sprintf("failed loading TLS intermediate ca certs at [%s]", tlsintermediatecertsDir))
}
} else {
mspLogger.Debugf("TLS CA certs folder at [%s] is empty. Skipping.", tlsintermediatecertsDir)
}
crls, err := getPemMaterialFromDir(crlsDir)
if os.IsNotExist(err) {
mspLogger.Debugf("crls folder not found at [%s]. Skipping. [%s]", crlsDir, err)
} else if err != nil {
return nil, errors.WithMessage(err, fmt.Sprintf("failed loading crls at [%s]", crlsDir))
}
// Load configuration file
// if the configuration file is there then load it
// otherwise skip it
var ouis []*msp.FabricOUIdentifier
var nodeOUs *msp.FabricNodeOUs
_, err = os.Stat(configFile)
if err == nil {
// load the file, if there is a failure in loading it then
// return an error
raw, err := ioutil.ReadFile(configFile)
if err != nil {
return nil, errors.Wrapf(err, "failed loading configuration file at [%s]", configFile)
}
configuration := Configuration{}
err = yaml.Unmarshal(raw, &configuration)
if err != nil {
return nil, errors.Wrapf(err, "failed unmarshalling configuration file at [%s]", configFile)
}
// Prepare OrganizationalUnitIdentifiers =OUS
if len(configuration.OrganizationalUnitIdentifiers) > 0 {
for _, ouID := range configuration.OrganizationalUnitIdentifiers {
f := filepath.Join(dir, ouID.Certificate)
raw, err = readFile(f)
if err != nil {
return nil, errors.Wrapf(err, "failed loading OrganizationalUnit certificate at [%s]", f)
}
oui := &msp.FabricOUIdentifier{
Certificate: raw,
OrganizationalUnitIdentifier: ouID.OrganizationalUnitIdentifier,
}
ouis = append(ouis, oui)
}
}
// Prepare NodeOUs
if configuration.NodeOUs != nil && configuration.NodeOUs.Enable {
mspLogger.Debug("Loading NodeOUs")
nodeOUs = &msp.FabricNodeOUs{
Enable: true,
}
if configuration.NodeOUs.ClientOUIdentifier != nil && len(configuration.NodeOUs.ClientOUIdentifier.OrganizationalUnitIdentifier) != 0 {
nodeOUs.ClientOuIdentifier = &msp.FabricOUIdentifier{OrganizationalUnitIdentifier: configuration.NodeOUs.ClientOUIdentifier.OrganizationalUnitIdentifier}
}
if configuration.NodeOUs.PeerOUIdentifier != nil && len(configuration.NodeOUs.PeerOUIdentifier.OrganizationalUnitIdentifier) != 0 {
nodeOUs.PeerOuIdentifier = &msp.FabricOUIdentifier{OrganizationalUnitIdentifier: configuration.NodeOUs.PeerOUIdentifier.OrganizationalUnitIdentifier}
}
if configuration.NodeOUs.AdminOUIdentifier != nil && len(configuration.NodeOUs.AdminOUIdentifier.OrganizationalUnitIdentifier) != 0 {
nodeOUs.AdminOuIdentifier = &msp.FabricOUIdentifier{OrganizationalUnitIdentifier: configuration.NodeOUs.AdminOUIdentifier.OrganizationalUnitIdentifier}
}
if configuration.NodeOUs.OrdererOUIdentifier != nil && len(configuration.NodeOUs.OrdererOUIdentifier.OrganizationalUnitIdentifier) != 0 {
nodeOUs.OrdererOuIdentifier = &msp.FabricOUIdentifier{OrganizationalUnitIdentifier: configuration.NodeOUs.OrdererOUIdentifier.OrganizationalUnitIdentifier}
}
// Read certificates, if defined
// ClientOU
if nodeOUs.ClientOuIdentifier != nil {
nodeOUs.ClientOuIdentifier.Certificate = loadCertificateAt(dir, configuration.NodeOUs.ClientOUIdentifier.Certificate, "ClientOU")
}
// PeerOU
if nodeOUs.PeerOuIdentifier != nil {
nodeOUs.PeerOuIdentifier.Certificate = loadCertificateAt(dir, configuration.NodeOUs.PeerOUIdentifier.Certificate, "PeerOU")
}
// AdminOU
if nodeOUs.AdminOuIdentifier != nil {
nodeOUs.AdminOuIdentifier.Certificate = loadCertificateAt(dir, configuration.NodeOUs.AdminOUIdentifier.Certificate, "AdminOU")
}
// OrdererOU
if nodeOUs.OrdererOuIdentifier != nil {
nodeOUs.OrdererOuIdentifier.Certificate = loadCertificateAt(dir, configuration.NodeOUs.OrdererOUIdentifier.Certificate, "OrdererOU")
}
}
} else {
mspLogger.Debugf("MSP configuration file not found at [%s]: [%s]", configFile, err)
}
// Set FabricCryptoConfig密码配置对象
cryptoConfig := &msp.FabricCryptoConfig{
SignatureHashFamily: bccsp.SHA2,
IdentityIdentifierHashFunction: bccsp.SHA256,
}
// Compose FabricMSPConfig
fmspconf := &msp.FabricMSPConfig{
Admins: admincert,
RootCerts: cacerts,
IntermediateCerts: intermediatecerts,
SigningIdentity: sigid,
Name: ID,
OrganizationalUnitIdentifiers: ouis,
RevocationList: crls,
CryptoConfig: cryptoConfig,
TlsRootCerts: tlsCACerts,
TlsIntermediateCerts: tlsIntermediateCerts,
FabricNodeOus: nodeOUs,
}
fmpsjs, _ := proto.Marshal(fmspconf)
mspconf := &msp.MSPConfig{Config: fmpsjs, Type: int32(FABRIC)}
return mspconf, nil
}
这里其实重点要搞明白OU,节点组织单元对象:一个文件 config.yaml 用来包含已经考虑过的 OU 的信息;他们会在之后被定义为一组在被称为 OrganizationalUnitIdentifiers 的yaml数组中的实体,也即 <Certificate, OrganizationalUnitIdentifier>,其中的 Certificate 代表着到证书机构的证书(root 的或者 intermediate 的)的相对路径。这些证书是被认为是组织单元(organizational unit 也就是 OU)中的已证明成员说拥有的。而 OrganizationalUnitIdentifier 代表着理应在 X.509 证书中的 OU-field 中出现的实际字符串。
getMspConfig这个函数,首先得到基本的信息如各种证书的路径,并通过这些路径来得到相关的对象(列表)。然后对MSP组件的节点组织单元对象进行处理,最后设置密码配置对象,包括相关的签名和生成ID的哈希函数(前者为SHA2,后者为SHA256)。
2、身份证书的验证
身份证书的验证在前面MSP源码分析newBccspMsp中看到过验证的初始化函数,theMsp.internalValidateIdentityOusFunc = theMsp.validateIdentityOUsV1类似这些代码。看下面提供的验证流程代码:
//msp/mspimpl.go
func (msp *bccspmsp) Validate(id Identity) error {
mspLogger.Debugf("MSP %s validating identity", msp.name)
switch id := id.(type) {
// If this identity is of this specific type,
// this is how I can validate it given the
// root of trust this MSP has
case *identity:
return msp.validateIdentity(id)
default:
return errors.New("identity type not recognized")
}
}
//msp/mspimplvalidate.go
func (msp *bccspmsp) validateIdentity(id *identity) error {
//获得身份验证的证书的验证链,也就是创建所有从根证书池认证签发路径上的证书所组成的有序证书链
validationChain, err := msp.getCertificationChainForBCCSPIdentity(id)
if err != nil {
return errors.WithMessage(err, "could not obtain certification chain")
}
//验证是不是属于CRL,证书撤销列表中的项,从而判断其有效性
err = msp.validateIdentityAgainstChain(id, validationChain)
if err != nil {
return errors.WithMessage(err, "could not validate identity against certification chain")
}
//验证身份证书的组织单元 和MSP组件包含的组织单元是否有交集
err = msp.internalValidateIdentityOusFunc(id)
if err != nil {
return errors.WithMessage(err, "could not validate identity's OUs")
}
return nil
}
下来分别看一看validateIdentity中调用的三个函数:
// getCertificationChainForBCCSPIdentity returns the certification chain of the passed bccsp identity within this msp
func (msp *bccspmsp) getCertificationChainForBCCSPIdentity(id *identity) ([]*x509.Certificate, error) {
if id == nil {
return nil, errors.New("Invalid bccsp identity. Must be different from nil.")
}
// we expect to have a valid VerifyOptions instance
if msp.opts == nil {
return nil, errors.New("Invalid msp instance")
}
// CAs cannot be directly used as identities..
if id.cert.IsCA {
return nil, errors.New("An X509 certificate with Basic Constraint: " +
"Certificate Authority equals true cannot be used as an identity")
}
return msp.getValidationChain(id.cert, false)
}
func (msp *bccspmsp) getValidationChain(cert *x509.Certificate, isIntermediateChain bool) ([]*x509.Certificate, error) {
//获取证书验证选项
validationChain, err := msp.getUniqueValidationChain(cert, msp.getValidityOptsForCert(cert))
if err != nil {
return nil, errors.WithMessage(err, "failed getting validation chain")
}
// we expect a chain of length at least 2
//长度至少为2,因为一定不会用根证书去验证
if len(validationChain) < 2 {
return nil, errors.Errorf("expected a chain of length at least 2, got %d", len(validationChain))
}
// check that the parent is a leaf of the certification tree
// if validating an intermediate chain, the first certificate will the parent
parentPosition := 1
if isIntermediateChain {
parentPosition = 0
}
//检查父证书是否是证书树的一个叶子节点
//true表示为中间节点证书,false表示是叶子节点证书,MSP的签名必须为false,即叶子节点,否则报错
if msp.certificationTreeInternalNodesMap[string(validationChain[parentPosition].Raw)] {
return nil, errors.Errorf("invalid validation chain. Parent certificate should be a leaf of the certification tree [%v]", cert.Raw)
}
return validationChain, nil
}
func (msp *bccspmsp) getUniqueValidationChain(cert *x509.Certificate, opts x509.VerifyOptions) ([]*x509.Certificate, error) {
// ask golang to validate the cert for us based on the options that we've built at setup time
if msp.opts == nil {
return nil, errors.New("the supplied identity has no verify options")
}
validationChains, err := cert.Verify(opts)
if err != nil {
return nil, errors.WithMessage(err, "the supplied identity is not valid")
}
// we only support a single validation chain;
// if there's more than one then there might
// be unclarity about who owns the identity
if len(validationChains) != 1 {
return nil, errors.Errorf("this MSP only supports a single validation chain, got %d", len(validationChains))
}
return validationChains[0], nil
}
第一个函数主要是用来获取身份证书链,也就是从根CA到中间CA到应用CA的所有证书。它最后又调用了getValidationChain这个函数,它才是真正获取证书链的函数。在这个函数里,首先调用getUniqueValidationChain来得到证书链,certificationTreeInternalNodesMap表示由中间证书和根证书组成的树形结构,而中间证书都是叶子节点,这也是前面说必须为叶子节点签名才可以。
下面来看第二个函数:

func (msp *bccspmsp) validateIdentityAgainstChain(id *identity, validationChain []*x509.Certificate) error {
return msp.validateCertAgainstChain(id.cert, validationChain)
}
func (msp *bccspmsp) validateCertAgainstChain(cert *x509.Certificate, validationChain []*x509.Certificate) error {
// here we know that the identity is valid; now we have to check whether it has been revoked
// identify the SKI of the CA that signed this cert
SKI, err := getSubjectKeyIdentifierFromCert(validationChain[1])
if err != nil {
return errors.WithMessage(err, "could not obtain Subject Key Identifier for signer cert")
}
// check whether one of the CRLs we have has this cert's
// SKI as its AuthorityKeyIdentifier
for _, crl := range msp.CRL {
aki, err := getAuthorityKeyIdentifierFromCrl(crl)
if err != nil {
return errors.WithMessage(err, "could not obtain Authority Key Identifier for crl")
}
// check if the SKI of the cert that signed us matches the AKI of any of the CRLs
if bytes.Equal(aki, SKI) {
// we have a CRL, check whether the serial number is revoked
for _, rc := range crl.TBSCertList.RevokedCertificates {
if rc.SerialNumber.Cmp(cert.SerialNumber) == 0 {
// We have found a CRL whose AKI matches the SKI of
// the CA (root or intermediate) that signed the
// certificate that is under validation. As a
// precaution, we verify that said CA is also the
// signer of this CRL.
err = validationChain[1].CheckCRLSignature(crl)
if err != nil {
// the CA cert that signed the certificate
// that is under validation did not sign the
// candidate CRL - skip
mspLogger.Warningf("Invalid signature over the identified CRL, error %+v", err)
continue
}
// A CRL also includes a time of revocation so that
// the CA can say "this cert is to be revoked starting
// from this time"; however here we just assume that
// revocation applies instantaneously from the time
// the MSP config is committed and used so we will not
// make use of that field
return errors.New("The certificate has been revoked")
}
}
}
}
return nil
}
第二个函数主要调用validateCertAgainstChain函数来验证证书是否存在于CRL可撤销证书列表中。它首先获取上级签发的CA证书的使用者密钥标识符SKI,遍历MSP组件所有的证书列表msp.CRL,获取每个CRL的颁发机构密钥标识符AKI,然后基于字节比较SKI 、AKI是否相同,如果二者匹配,则继续检查CRL中撤销证书的序列号rc.SerialNumber。如果该序列号与指定的身份证书的序列号cert.SerialNumber相同,则调用CheckCRLSignature方法继续级签发CA节点是否为该CRL的签名者,如果确定仍然为同一个签名者,则说明指定身份证书cert已经被撤销。
再看第三个函数,在前面的newBccspMsp函数中,发现不同的MSP版本,提供了不同的internalValidateIdentityOusFunc,来看一下最新的:
func (msp *bccspmsp) validateIdentityOUsV143(id *identity) error {
// Run the same checks as per V1
err := msp.validateIdentityOUsV1(id)
if err != nil {
return err
}
// -- Check for OU enforcement
if !msp.ouEnforcement {
// No enforcement required
return nil
}
// Make sure that the identity has only one of the special OUs
// used to tell apart clients, peers and admins.
counter := 0
validOUs := make(map[string]*OUIdentifier)
if msp.clientOU != nil {
validOUs[msp.clientOU.OrganizationalUnitIdentifier] = msp.clientOU
}
if msp.peerOU != nil {
validOUs[msp.peerOU.OrganizationalUnitIdentifier] = msp.peerOU
}
if msp.adminOU != nil {
validOUs[msp.adminOU.OrganizationalUnitIdentifier] = msp.adminOU
}
if msp.ordererOU != nil {
validOUs[msp.ordererOU.OrganizationalUnitIdentifier] = msp.ordererOU
}
for _, OU := range id.GetOrganizationalUnits() {
// Is OU.OrganizationalUnitIdentifier one of the special OUs?
nodeOU := validOUs[OU.OrganizationalUnitIdentifier]
if nodeOU == nil {
continue
}
// Yes. Then, enforce the certifiers identifier in this is specified.
// If is not specified, it means that any certification path is fine.
if len(nodeOU.CertifiersIdentifier) != 0 && !bytes.Equal(nodeOU.CertifiersIdentifier, OU.CertifiersIdentifier) {
return errors.Errorf("certifiersIdentifier does not match: [%v], MSP: [%s]", id.GetOrganizationalUnits(), msp.name)
}
//保证证书只能为客户端、PEER、ORDER或者Admin中的一个。
counter++
if counter > 1 {
break
}
}
if counter != 1 {
return errors.Errorf("the identity must be a client, a peer, an orderer or an admin identity to be valid, not a combination of them. OUs: [%v], MSP: [%s]", id.GetOrganizationalUnits(), msp.name)
}
return nil
}
func (msp *bccspmsp) validateIdentityOUsV1(id *identity) error {
// Check that the identity's OUs are compatible with those recognized by this MSP,
// meaning that the intersection is not empty.
if len(msp.ouIdentifiers) > 0 {
found := false
//遍历组织单元标识列表
for _, OU := range id.GetOrganizationalUnits() {
certificationIDs, exists := msp.ouIdentifiers[OU.OrganizationalUnitIdentifier]
if exists {
//遍历证书标识符ID列表
for _, certificationID := range certificationIDs {
if bytes.Equal(certificationID, OU.CertifiersIdentifier) {
found = true
break
}
}
}
}
if !found {
if len(id.GetOrganizationalUnits()) == 0 {
return errors.New("the identity certificate does not contain an Organizational Unit (OU)")
}
return errors.Errorf("none of the identity's organizational units [%v] are in MSP %s", id.GetOrganizationalUnits(), msp.name)
}
}
return nil
}
其它的验证还有包括类似诸如零知识证明等的方式,有兴趣可以看一看源码。
二、BCCSP
1、整体架构
BCCSP是整个Fabric中的基础的模块,所有的加密签名部分基本都需要从这里来支持。看一下他的基础的类图:
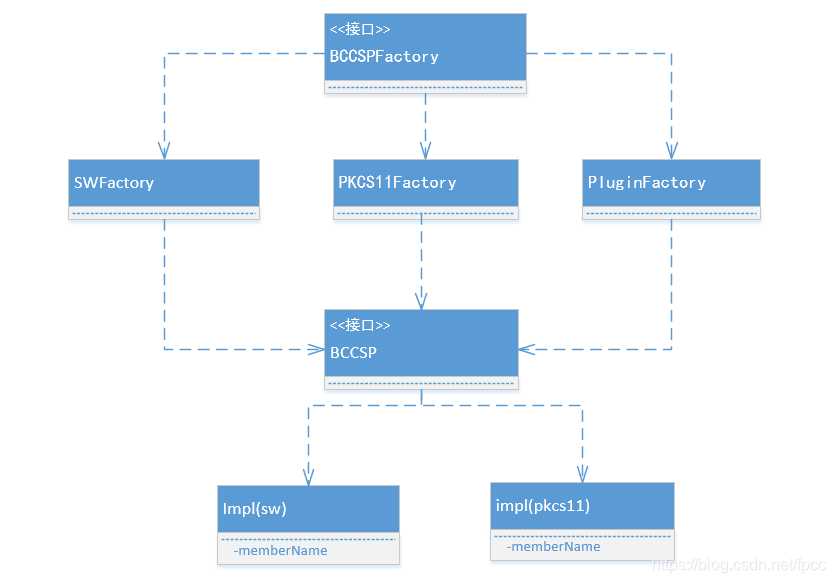
包图:
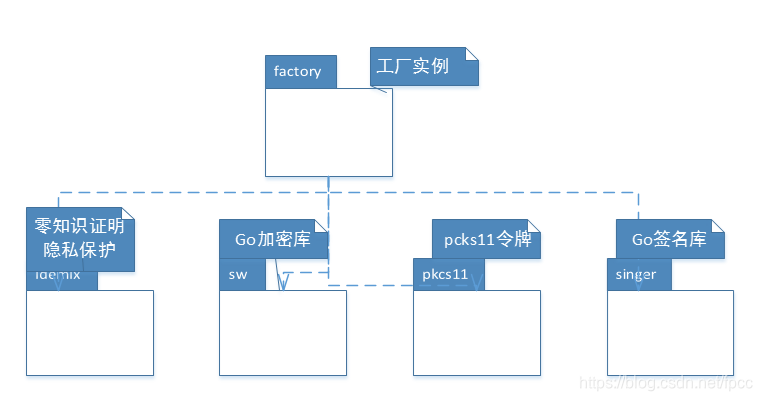
2、启动流程
BCCSP是整个Fabric中的基础模块之一加密模块,整个系统运行需要的加密、解密、签名及验证、哈希以及相关的零知识证明以及后续的迭代演进,诸如支持国密或者其它加密算法的接口都在这个模块之中。它主要提供了两大类的加密方式即硬件加密方式(PKCS11,基于HSM硬件安全模块)和SM类型的软件加密服务(使用的GO本身提供的算法库)。在提供的这两类加密算法的基础上,抽象出来了相关的对象工厂以及相关的加密函数接口。
在Fabric中很多地方都会启动对BCCSP包的调用,这里在分析MSP,所以就把其相关的factory和BCCSP包启动看一下:
BCCSP工厂启动和初始化的过程:
函数调用GetLocalMspConfig()->InitFactories()
func InitFactories(config *FactoryOpts) error {
factoriesInitOnce.Do(func() {
setFactories(config)
})
return factoriesInitError
}
func setFactories(config *FactoryOpts) error {
// Take some precautions on default opts
if config == nil {
config = GetDefaultOpts()
}
if config.ProviderName == "" {
config.ProviderName = "SW"
}
if config.SwOpts == nil {
config.SwOpts = GetDefaultOpts().SwOpts
}
// Initialize factories map
bccspMap = make(map[string]bccsp.BCCSP)
// Software-Based BCCSP
if config.SwOpts != nil {
f := &SWFactory{}
err := initBCCSP(f, config)
if err != nil {
factoriesInitError = errors.Wrap(err, "Failed initializing SW.BCCSP")
}
}
// PKCS11-Based BCCSP
if config.Pkcs11Opts != nil {
f := &PKCS11Factory{}
err := initBCCSP(f, config)
if err != nil {
factoriesInitError = errors.Wrapf(err, "Failed initializing PKCS11.BCCSP %s", factoriesInitError)
}
}
// BCCSP Plugin
if config.PluginOpts != nil {
f := &PluginFactory{}
err := initBCCSP(f, config)
if err != nil {
factoriesInitError = errors.Wrapf(err, "Failed initializing PKCS11.BCCSP %s", factoriesInitError)
}
}
var ok bool
defaultBCCSP, ok = bccspMap[config.ProviderName]
if !ok {
factoriesInitError = errors.Errorf("%s\nCould not find default `%s` BCCSP", factoriesInitError, config.ProviderName)
}
return factoriesInitError
}
func initBCCSP(f BCCSPFactory, config *FactoryOpts) error {
//在此处其实是实现了三个工厂类即:pck11,plugin,sw
csp, err := f.Get(config)
if err != nil {
return errors.Errorf("Could not initialize BCCSP %s [%s]", f.Name(), err)
}
logger.Debugf("Initialize BCCSP [%s]", f.Name())
//csp的映射存储,在以后就可以通过工厂Name来得到相应的BCCSP操作对象
bccspMap[f.Name()] = csp
return nil
}
BCCSP的启动和初始化过程:
函数调用的顺序:GetLocalMSP()->LoadLocalMsp()->New()->newBccspMsp():
unc newBccspMsp(version MSPVersion) (MSP, error) {
mspLogger.Debugf("Creating BCCSP-based MSP instance")
bccsp := factory.GetDefault()
......
return theMsp, nil
}
这个函数中前面提到好多次,这个函数一开始就创建相关的BCCSP对象实例。调用相关工厂类的默认创建函数。看一下他的实现:
func GetDefault() bccsp.BCCSP {
if defaultBCCSP == nil {
logger.Debug("Before using BCCSP, please call InitFactories(). Falling back to bootBCCSP.")
bootBCCSPInitOnce.Do(func() {
var err error
f := &SWFactory{}
bootBCCSP, err = f.Get(GetDefaultOpts())
if err != nil {
panic("BCCSP Internal error, failed initialization with GetDefaultOpts!")
}
})
return bootBCCSP
}
return defaultBCCSP
}
直接就跳到了BCCSP模块的factory包下,在下面的源码分析中将对其进行展开分析。
三、源码
顺着上面的初始启动代码分析相关的数据结构和相关的代码:
type BCCSP interface {
// KeyGen generates a key using opts.
KeyGen(opts KeyGenOpts) (k Key, err error)
// KeyDeriv derives a key from k using opts.
// The opts argument should be appropriate for the primitive used.
KeyDeriv(k Key, opts KeyDerivOpts) (dk Key, err error)
// KeyImport imports a key from its raw representation using opts.
// The opts argument should be appropriate for the primitive used.
KeyImport(raw interface{}, opts KeyImportOpts) (k Key, err error)
// GetKey returns the key this CSP associates to
// the Subject Key Identifier ski.
GetKey(ski []byte) (k Key, err error)
// Hash hashes messages msg using options opts.
// If opts is nil, the default hash function will be used.
Hash(msg []byte, opts HashOpts) (hash []byte, err error)
// GetHash returns and instance of hash.Hash using options opts.
// If opts is nil, the default hash function will be returned.
GetHash(opts HashOpts) (h hash.Hash, err error)
// Sign signs digest using key k.
// The opts argument should be appropriate for the algorithm used.
//
// Note that when a signature of a hash of a larger message is needed,
// the caller is responsible for hashing the larger message and passing
// the hash (as digest).
Sign(k Key, digest []byte, opts SignerOpts) (signature []byte, err error)
// Verify verifies signature against key k and digest
// The opts argument should be appropriate for the algorithm used.
Verify(k Key, signature, digest []byte, opts SignerOpts) (valid bool, err error)
// Encrypt encrypts plaintext using key k.
// The opts argument should be appropriate for the algorithm used.
Encrypt(k Key, plaintext []byte, opts EncrypterOpts) (ciphertext []byte, err error)
// Decrypt decrypts ciphertext using key k.
// The opts argument should be appropriate for the algorithm used.
Decrypt(k Key, ciphertext []byte, opts DecrypterOpts) (plaintext []byte, err error)
}
type BCCSPFactory interface {
// Name returns the name of this factory
Name() string
// Get returns an instance of BCCSP using opts.
Get(opts *FactoryOpts) (bccsp.BCCSP, error)
}
func (f *SWFactory) Get(config *FactoryOpts) (bccsp.BCCSP, error) {
// Validate arguments
if config == nil || config.SwOpts == nil {
return nil, errors.New("Invalid config. It must not be nil.")
}
swOpts := config.SwOpts
var ks bccsp.KeyStore
if swOpts.Ephemeral == true {
//虚拟存储路径--密钥并不被加载和保存
ks = sw.NewDummyKeyStore()
} else if swOpts.FileKeystore != nil {
//设置私钥的路径
fks, err := sw.NewFileBasedKeyStore(nil, swOpts.FileKeystore.KeyStorePath, false)
if err != nil {
return nil, errors.Wrapf(err, "Failed to initialize software key store")
}
ks = fks
} else if swOpts.InmemKeystore != nil {
//内存存储密钥
ks = sw.NewInMemoryKeyStore()
} else {
// Default to ephemeral key store
//默认为临时存储
ks = sw.NewDummyKeyStore()
}
return sw.NewWithParams(swOpts.SecLevel, swOpts.HashFamily, ks)
}
//默认是使用软件的SW加密方式
func GetDefaultOpts() *FactoryOpts {
return &FactoryOpts{
ProviderName: "SW",
SwOpts: &SwOpts{
HashFamily: "SHA2",
SecLevel: 256,
Ephemeral: true,
},
}
}
看一看最后的NewWithParams:
func NewWithParams(securityLevel int, hashFamily string, keyStore bccsp.KeyStore) (bccsp.BCCSP, error) {
// Init config
conf := &config{}
err := conf.setSecurityLevel(securityLevel, hashFamily)
if err != nil {
return nil, errors.Wrapf(err, "Failed initializing configuration at [%v,%v]", securityLevel, hashFamily)
}
//生成一个CSP提供者,看下面的详细代码分析
swbccsp, err := New(keyStore)
if err != nil {
return nil, err
}
// Notice that errors are ignored here because some test will fail if one
// of the following call fails.
// Set the Encryptors设置加密器
swbccsp.AddWrapper(reflect.TypeOf(&aesPrivateKey{}), &aescbcpkcs7Encryptor{})
// Set the Decryptors设置解密器
swbccsp.AddWrapper(reflect.TypeOf(&aesPrivateKey{}), &aescbcpkcs7Decryptor{})
// Set the Signers设置签名器
swbccsp.AddWrapper(reflect.TypeOf(&ecdsaPrivateKey{}), &ecdsaSigner{})
swbccsp.AddWrapper(reflect.TypeOf(&rsaPrivateKey{}), &rsaSigner{})
// Set the Verifiers
swbccsp.AddWrapper(reflect.TypeOf(&ecdsaPrivateKey{}), &ecdsaPrivateKeyVerifier{})
swbccsp.AddWrapper(reflect.TypeOf(&ecdsaPublicKey{}), &ecdsaPublicKeyKeyVerifier{})
swbccsp.AddWrapper(reflect.TypeOf(&rsaPrivateKey{}), &rsaPrivateKeyVerifier{})
swbccsp.AddWrapper(reflect.TypeOf(&rsaPublicKey{}), &rsaPublicKeyKeyVerifier{})
// Set the Hashers
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.SHAOpts{}), &hasher{hash: conf.hashFunction})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.SHA256Opts{}), &hasher{hash: sha256.New})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.SHA384Opts{}), &hasher{hash: sha512.New384})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.SHA3_256Opts{}), &hasher{hash: sha3.New256})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.SHA3_384Opts{}), &hasher{hash: sha3.New384})
// Set the key generators
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.ECDSAKeyGenOpts{}), &ecdsaKeyGenerator{curve: conf.ellipticCurve})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.ECDSAP256KeyGenOpts{}), &ecdsaKeyGenerator{curve: elliptic.P256()})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.ECDSAP384KeyGenOpts{}), &ecdsaKeyGenerator{curve: elliptic.P384()})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.AESKeyGenOpts{}), &aesKeyGenerator{length: conf.aesBitLength})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.AES256KeyGenOpts{}), &aesKeyGenerator{length: 32})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.AES192KeyGenOpts{}), &aesKeyGenerator{length: 24})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.AES128KeyGenOpts{}), &aesKeyGenerator{length: 16})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.RSAKeyGenOpts{}), &rsaKeyGenerator{length: conf.rsaBitLength})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.RSA1024KeyGenOpts{}), &rsaKeyGenerator{length: 1024})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.RSA2048KeyGenOpts{}), &rsaKeyGenerator{length: 2048})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.RSA3072KeyGenOpts{}), &rsaKeyGenerator{length: 3072})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.RSA4096KeyGenOpts{}), &rsaKeyGenerator{length: 4096})
// Set the key generators
swbccsp.AddWrapper(reflect.TypeOf(&ecdsaPrivateKey{}), &ecdsaPrivateKeyKeyDeriver{})
swbccsp.AddWrapper(reflect.TypeOf(&ecdsaPublicKey{}), &ecdsaPublicKeyKeyDeriver{})
swbccsp.AddWrapper(reflect.TypeOf(&aesPrivateKey{}), &aesPrivateKeyKeyDeriver{conf: conf})
// Set the key importers
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.AES256ImportKeyOpts{}), &aes256ImportKeyOptsKeyImporter{})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.HMACImportKeyOpts{}), &hmacImportKeyOptsKeyImporter{})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.ECDSAPKIXPublicKeyImportOpts{}), &ecdsaPKIXPublicKeyImportOptsKeyImporter{})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.ECDSAPrivateKeyImportOpts{}), &ecdsaPrivateKeyImportOptsKeyImporter{})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.ECDSAGoPublicKeyImportOpts{}), &ecdsaGoPublicKeyImportOptsKeyImporter{})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.RSAGoPublicKeyImportOpts{}), &rsaGoPublicKeyImportOptsKeyImporter{})
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.X509PublicKeyImportOpts{}), &x509PublicKeyImportOptsKeyImporter{bccsp: swbccsp})
return swbccsp, nil
}
这个函数通过相关的参数配置来新建BCCSP。在这个函数里出现了CSP这个加密提供者,看一下相关的代码:
type CSP struct {
ks bccsp.KeyStore
KeyGenerators map[reflect.Type]KeyGenerator
KeyDerivers map[reflect.Type]KeyDeriver
KeyImporters map[reflect.Type]KeyImporter
Encryptors map[reflect.Type]Encryptor
Decryptors map[reflect.Type]Decryptor
Signers map[reflect.Type]Signer
Verifiers map[reflect.Type]Verifier
Hashers map[reflect.Type]Hasher
}
//在这个函数里,设置上在CPS结构中相应的各种操作者的对象
func New(keyStore bccsp.KeyStore) (*CSP, error) {
if keyStore == nil {
return nil, errors.Errorf("Invalid bccsp.KeyStore instance. It must be different from nil.")
}
encryptors := make(map[reflect.Type]Encryptor)
decryptors := make(map[reflect.Type]Decryptor)
signers := make(map[reflect.Type]Signer)
verifiers := make(map[reflect.Type]Verifier)
hashers := make(map[reflect.Type]Hasher)
keyGenerators := make(map[reflect.Type]KeyGenerator)
keyDerivers := make(map[reflect.Type]KeyDeriver)
keyImporters := make(map[reflect.Type]KeyImporter)
csp := &CSP{keyStore,
keyGenerators, keyDerivers, keyImporters, encryptors,
decryptors, signers, verifiers, hashers}
return csp, nil
}
在New函数中创建了CSP结构中的相关操作集合,这些集合分别实现了一些相应的接口,比如:
// Encryptor is a BCCSP-like interface that provides encryption algorithms
type Encryptor interface {
// Encrypt encrypts plaintext using key k.
// The opts argument should be appropriate for the algorithm used.
Encrypt(k bccsp.Key, plaintext []byte, opts bccsp.EncrypterOpts) (ciphertext []byte, err error)
}
// Decryptor is a BCCSP-like interface that provides decryption algorithms
type Decryptor interface {
// Decrypt decrypts ciphertext using key k.
// The opts argument should be appropriate for the algorithm used.
Decrypt(k bccsp.Key, ciphertext []byte, opts bccsp.DecrypterOpts) (plaintext []byte, err error)
}
// Signer is a BCCSP-like interface that provides signing algorithms
type Signer interface {
// Sign signs digest using key k.
// The opts argument should be appropriate for the algorithm used.
//
// Note that when a signature of a hash of a larger message is needed,
// the caller is responsible for hashing the larger message and passing
// the hash (as digest).
Sign(k bccsp.Key, digest []byte, opts bccsp.SignerOpts) (signature []byte, err error)
}
在CSP这个类中提供了AddWrapers这个增加打包器函数,用来绑定各种类型的数据结构。
// AddWrapper binds the passed type to the passed wrapper.
// Notice that that wrapper must be an instance of one of the following interfaces:
// KeyGenerator, KeyDeriver, KeyImporter, Encryptor, Decryptor, Signer, Verifier, Hasher.
func (csp *CSP) AddWrapper(t reflect.Type, w interface{}) error {
if t == nil {
return errors.Errorf("type cannot be nil")
}
if w == nil {
return errors.Errorf("wrapper cannot be nil")
}
switch dt := w.(type) {
case KeyGenerator:
csp.KeyGenerators[t] = dt
case KeyImporter:
csp.KeyImporters[t] = dt
case KeyDeriver:
csp.KeyDerivers[t] = dt
case Encryptor:
csp.Encryptors[t] = dt
case Decryptor:
csp.Decryptors[t] = dt
case Signer:
csp.Signers[t] = dt
case Verifier:
csp.Verifiers[t] = dt
case Hasher:
csp.Hashers[t] = dt
default:
return errors.Errorf("wrapper type not valid, must be on of: KeyGenerator, KeyDeriver, KeyImporter, Encryptor, Decryptor, Signer, Verifier, Hasher")
}
return nil
}
来分析一下这个AddlWrapper的作用,随便取一个增加函数代码:
swbccsp.AddWrapper(reflect.TypeOf(&bccsp.ECDSAP256KeyGenOpts{}), &ecdsaKeyGenerator{curve: elliptic.P256()})
可以看出:
key(t) = reflect.TypeOf(&bccsp.ECDSAP256KeyGenOpts{})
value(dt) = ecdsaKeyGenerator{curve: elliptic.P256()}
前面是类型,后面是类型的实例对象,针对这个对象看一下定义:
type ecdsaKeyGenerator struct {
curve elliptic.Curve
}
func (kg *ecdsaKeyGenerator) KeyGen(opts bccsp.KeyGenOpts) (bccsp.Key, error) {
privKey, err := ecdsa.GenerateKey(kg.curve, rand.Reader)
if err != nil {
return nil, fmt.Errorf("Failed generating ECDSA key for [%v]: [%s]", kg.curve, err)
}
return &ecdsaPrivateKey{privKey}, nil
}
这样,它就和CSP类中实现的相关接口对应上了,还是看这个接口,其在CSP中实现为:
func (csp *CSP) KeyGen(opts bccsp.KeyGenOpts) (k bccsp.Key, err error) {
// Validate arguments
if opts == nil {
return nil, errors.New("Invalid Opts parameter. It must not be nil.")
}
//这里得到上面的KV中的产生器
keyGenerator, found := csp.KeyGenerators[reflect.TypeOf(opts)]
if !found {
return nil, errors.Errorf("Unsupported 'KeyGenOpts' provided [%v]", opts)
}
//开始调用真正的ecdsaKeyGenerator.KeyGen()函数
k, err = keyGenerator.KeyGen(opts)
if err != nil {
return nil, errors.Wrapf(err, "Failed generating key with opts [%v]", opts)
}
// If the key is not Ephemeral, store it.
if !opts.Ephemeral() {
// Store the key
err = csp.ks.StoreKey(k)
if err != nil {
return nil, errors.Wrapf(err, "Failed storing key [%s]", opts.Algorithm())
}
}
return k, nil
}
BCCSP内部的加密算法,会开辟专门的一节来分析。这里就不再展开了。
四、总结
通过上述分析可以看到,做为基础模块,其实BCCSP在整个Fabric是非常重要的,从另外一个角度来看,如果没有密码学做为基础,区块链的安全性肯定会极大的降低。密码学其实就是整个BCCSP的核心,包括对称的、非对称的等等,这些都构成了整个Fabric安全应用的基石。
