1、iptables有几个表以及几个链
4个表:filter,nat,mangle,raw,默认表是filter(没有指定表的时候就是filter表)。表的处理优先级:raw>mangle>nat>filter。
5个链:PREROUTING,INPUT,FORWARD,OUTPUT,POSTROUTING。
2、iptables的几个表以及每个表对应链的作用,对应企业应用场景。
Filter 是默认的主机防火墙,过滤流入流出主机的数据包。里边包含INPUT,OUTPUT,FOWARD三个链
INPUT 过滤进入主机的数据包
OUTPUT 处理从本机发出去的数据包
FOWARD 处理流经本主机的数据包,与NAT有关系
Filter表是企业实现防火墙功能的重要手段
NAT 负责网络地址转换(来源于目的地址的IP与端口的转换),一般用于局域网的共享上网,与网络交换机acl类似,包含OUTPUT,PREROUTING,POSTROUTING三条链
OUTPUT 改变主机发出去的数据包的目标地址
PREROUTING 数据包到达防火墙时进行分路由判断之前执行的规则,改变数据包的目的地址,目的端口
POSTROUTING 数据包离开防火墙时进行分路由判断之前执行的规则,改变数据包的源的地址,源的端口
Mangle 在企业中应用比较少
3、请写出查看iptables当前所有规则的命令
iptables -nL (查看filter表)
iptables -nL -t nat (查看NAT表)
4、禁止来自192.168.100.20 ip地址访问80端口的请求
[root@localhost ~]# iptables -A INPUT -p tcp -s 192.168.100.20 --dport 80 -j DROP
[root@localhost ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
INPUT_direct all -- 0.0.0.0/0 0.0.0.0/0
INPUT_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0
INPUT_ZONES all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
DROP tcp -- 192.168.100.20 0.0.0.0/0 tcp dpt:80
5、实现把访问192.168.100.20:80的请求转到192.168.100.30:80
[root@localhost ~]# iptables -t nat -A PREROUTING -d 192.168.100.20 -p tcp --dport 80 -j DNAT --to-destination 192.168.100.30:80
[root@localhost ~]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
PREROUTING_direct all -- 0.0.0.0/0 0.0.0.0/0
PREROUTING_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0
PREROUTING_ZONES all -- 0.0.0.0/0 0.0.0.0/0
DNAT tcp -- 0.0.0.0/0 192.168.100.20 tcp dpt:80 to:192.168.100.30:80
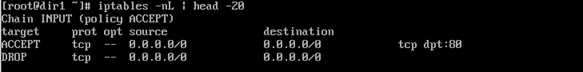
6、写一个防火墙配置脚本,只允许远程主机访问本机的80端口。
[root@localhost ~]# vi /usr/local/sbin/iptables.sh
#!/bin/bash
iptables -F
iptables -A INPUT -p tcp --dport 80 -j ACCEPT
iptables -A INPUT -p tcp -j DROP
执行脚本后
7、限制客户端对本机telnet服务并发连接数小于等于3
[root@localhost ~]# iptables -A INPUT -p tcp --dport 23 -m connlimit --connlimit-upto 2 -j ACCEPT
[root@localhost ~]# iptables -A INPUT -p tcp --dport 23 -j DROP
[root@localhost ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
INPUT_direct all -- 0.0.0.0/0 0.0.0.0/0
INPUT_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0
INPUT_ZONES all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:23 #conn src/32 <= 2
DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:23
8、仅允许周2、4、6,9点到18点访问本机telnet
[root@localhost ~]# iptables -I INPUT -d 192.168.88.84 -p tcp --dport 23 -m time --timestart 09:00:00 --timestop 18:00:00 --weekdays Tue,Thu,Sat -j ACCEPT
[root@localhost ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 192.168.88.84 tcp dpt:23 TIME from 09:00:00 to 18:00:00 on Tue,Thu,Sat UTC
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
INPUT_direct all -- 0.0.0.0/0 0.0.0.0/0
INPUT_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0
INPUT_ZONES all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
9、iptables只开启ssh、web、telnet访问
[root@localhost ~]# iptables -A INPUT -d 192.168.88.84 -p tcp -m multiport --dports 22:23,80 -j ACCEPT
[root@localhost ~]# iptables -A OUTPUT -s 192.168.88.84 -p tcp -m multiport --sports 22:23,80 -j ACCEPT
[root@localhost ~]# iptables -A INPUT -d 192.168.88.84 -j DROP
[root@localhost ~]# iptables -A OUTPUT -s 192.168.88.84 -j DROP
[root@localhost ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
INPUT_direct all -- 0.0.0.0/0 0.0.0.0/0
INPUT_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0
INPUT_ZONES all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
ACCEPT tcp -- 0.0.0.0/0 192.168.88.84 multiport dports 22:23,80
DROP all -- 0.0.0.0/0 192.168.88.84
``
``
``
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
OUTPUT_direct all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 192.168.88.84 0.0.0.0/0 multiport sports 22:23,80
DROP all -- 192.168.88.84 0.0.0.0/0
10、指定ip地址范围可以访问本机mysql
[root@localhost ~]# iptables -I INPUT 2 -d 192.168.88.84 -p tcp --dport 3306 -m iprange --src-range 192.168.88.80-192.168.88.100 -j ACCEPT
[root@localhost ~]# iptables -I OUTPUT 2 -d 192.168.88.84 -p tcp --dport 3306 -m iprange --dst-range 192.168.88.80-192.168.88.100 -j ACCEPT
[root@localhost ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
ACCEPT tcp -- anywhere 192.168.88.84 tcp dpt:mysql source IP range 192.168.88.80-192.168.88.100
ACCEPT all -- anywhere anywhere
INPUT_direct all -- anywhere anywhere
INPUT_ZONES_SOURCE all -- anywhere anywhere
INPUT_ZONES all -- anywhere anywhere
ACCEPT icmp -- anywhere anywhere
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
OUTPUT_direct all -- anywhere anywhere
ACCEPT tcp -- anywhere 192.168.88.84 tcp dpt:mysql destination IP range 192.168.88.80-192.168.88.100
