Hashcat是一款密码爆破神器,信息安全必备工具之一,特此写篇文章记录总结之,以备不时之需。
简介
Hashcat是世界上最快的密码破解程序,是一个支持多平台、多算法的开源的分布式工具。
官方:https://hashcat.net/hashcat/
Github:https://github.com/hashcat/hashcat
安装
macOS
# 安装hashcat
brew install hashcat
# 查看版本
hashcat --version
Linux
Kali Linux内置Hashcat,在Deepin Linux和Ubuntu Linux下可以直接使用APT来安装:
apt update && apt install hashcat
# 查看版本
hashcat --version
也可以手动解压运行二进制文件 https://github.com/hashcat/hashcat/releases 下载最新版压缩包:
# 解压
tar zxvf hashcat-5.1.0.7z
cd hashcat-5.1.0
# 根据自己的平台执行对应的二进制文件
./hashcat64.bin
./hashcat32.bin
Windows
https://github.com/hashcat/hashcat/releases 下载最新版压缩包,解压根据自己的平台运行hashcat64.exe或者hashcat32.exe
常用参数
-m 破解hash类型
指定要破解的hash类型,后面跟hash类型对应的数字,具体类型详见下表:
- [ Hash modes ] -<span class="token comment" spellcheck="true"># | Name | Category</span>
++==
900 | MD4 | Raw Hash
0 | MD5 | Raw Hash
5100 | Half MD5 | Raw Hash
100 | SHA1 | Raw Hash
1300 | SHA2-224 | Raw Hash
1400 | SHA2-256 | Raw Hash
10800 | SHA2-384 | Raw Hash
1700 | SHA2-512 | Raw Hash
17300 | SHA3-224 | Raw Hash
17400 | SHA3-256 | Raw Hash
17500 | SHA3-384 | Raw Hash
17600 | SHA3-512 | Raw Hash
17700 | Keccak-224 | Raw Hash
17800 | Keccak-256 | Raw Hash
17900 | Keccak-384 | Raw Hash
18000 | Keccak-512 | Raw Hash
600 | BLAKE2b-512 | Raw Hash
10100 | SipHash | Raw Hash
6000 | RIPEMD-160 | Raw Hash
6100 | Whirlpool | Raw Hash
6900 | GOST R 34.11-94 | Raw Hash
11700 | GOST R 34.11-2012 (Streebog) 256-bit, big-endian | Raw Hash
11800 | GOST R 34.11-2012 (Streebog) 512-bit, big-endian | Raw Hash
10 | md5(
salt) | Raw Hash, Salted and/or Iterated
20 | md5(
pass) | Raw Hash, Salted and/or Iterated
30 | md5(utf16le(
salt) | Raw Hash, Salted and/or Iterated
40 | md5(
pass)) | Raw Hash, Salted and/or Iterated
3800 | md5(
pass.
salt.md5(
salt.md5(
pass)) | Raw Hash, Salted and/or Iterated
4110 | md5(
pass.
pass)) | Raw Hash, Salted and/or Iterated
3910 | md5(md5(
salt)) | Raw Hash, Salted and/or Iterated
4300 | md5(strtoupper(md5(
pass)) | Raw Hash, Salted and/or Iterated
110 | sha1(
salt) | Raw Hash, Salted and/or Iterated
120 | sha1(
pass) | Raw Hash, Salted and/or Iterated
130 | sha1(utf16le(
salt) | Raw Hash, Salted and/or Iterated
140 | sha1(
pass)) | Raw Hash, Salted and/or Iterated
4500 | sha1(sha1(
salt.sha1(
pass)) | Raw Hash, Salted and/or Iterated
4900 | sha1(
pass.
pass.
salt.
pass).
salt.utf16le(
pass.
salt.
pass).
salt.utf16le(
pass) | Raw Hash, Authenticated
60 | HMAC-MD5 (key =
pass) | Raw Hash, Authenticated
160 | HMAC-SHA1 (key =
pass) | Raw Hash, Authenticated
1460 | HMAC-SHA256 (key =
pass) | Raw Hash, Authenticated
1760 | HMAC-SHA512 (key =
pass), big-endian | Raw Hash, Authenticated
11760 | HMAC-Streebog-256 (key =
pass), big-endian | Raw Hash, Authenticated
11860 | HMAC-Streebog-512 (key =
salt, key =
salt, key =
salt, key = KaTeX parse error: Expected 'EOF', got '&' at position 5151: …oken operator">&̲gt;</span> v1.1…apr1$ MD5, md5apr1, MD5 (APR) | HTTP, SMTP, LDAP Server
12600 | ColdFusion 10+ | HTTP, SMTP, LDAP Server
1421 | hMailServer | HTTP, SMTP, LDAP Server
101 | nsldap, SHA-1(Base64), Netscape LDAP SHA | HTTP, SMTP, LDAP Server
111 | nsldaps, SSHA-1(Base64), Netscape LDAP SSHA | HTTP, SMTP, LDAP Server
1411 | SSHA-256(Base64), LDAP {SSHA256} | HTTP, SMTP, LDAP Server
1711 | SSHA-512(Base64), LDAP {SSHA512} | HTTP, SMTP, LDAP Server
16400 | CRAM-MD5 Dovecot | HTTP, SMTP, LDAP Server
15000 | FileZilla Server >= 0.9.55 | FTP Server
11500 | CRC32 | Checksums
3000 | LM | Operating Systems
1000 | NTLM | Operating Systems
1100 | Domain Cached Credentials (DCC), MS Cache | Operating Systems
2100 | Domain Cached Credentials 2 (DCC2), MS Cache 2 | Operating Systems
15300 | DPAPI masterkey file v1 | Operating Systems
15900 | DPAPI masterkey file v2 | Operating Systems
12800 | MS-AzureSync PBKDF2-HMAC-SHA256 | Operating Systems
1500 | descrypt, DES (Unix), Traditional DES | Operating Systems
12400 | BSDi Crypt, Extended DES | Operating Systems
500 | md5crypt, MD5 (Unix), Cisco-IOS
(MD5) | Operating Systems
3200 | bcrypt
, Blowfish (Unix) | Operating Systems
7400 | sha256crypt
, SHA256 (Unix) | Operating Systems
1800 | sha512crypt
, SHA512 (Unix) | Operating Systems
122 | macOS v10.4, MacOS v10.5, MacOS v10.6 | Operating Systems
1722 | macOS v10.7 | Operating Systems
7100 | macOS v10.8+ (PBKDF2-SHA512) | Operating Systems
6300 | AIX {smd5} | Operating Systems
6700 | AIX {ssha1} | Operating Systems
6400 | AIX {ssha256} | Operating Systems
6500 | AIX {ssha512} | Operating Systems
2400 | Cisco-PIX MD5 | Operating Systems
2410 | Cisco-ASA MD5 | Operating Systems
500 | Cisco-IOS
(MD5) | Operating Systems
5700 | Cisco-IOS type 4 (SHA256) | Operating Systems
9200 | Cisco-IOS
(PBKDF2-SHA256) | Operating Systems
9300 | Cisco-IOS
(scrypt) | Operating Systems
22 | Juniper NetScreen/SSG (ScreenOS) | Operating Systems
501 | Juniper IVE | Operating Systems
15100 | Juniper/NetBSD sha1crypt | Operating Systems
7000 | FortiGate (FortiOS) | Operating Systems
5800 | Samsung Android Password/PIN | Operating Systems
13800 | Windows Phone 8+ PIN/password | Operating Systems
8100 | Citrix NetScaler | Operating Systems
8500 | RACF | Operating Systems
7200 | GRUB 2 | Operating Systems
9900 | Radmin2 | Operating Systems
125 | ArubaOS | Operating Systems
7700 | SAP CODVN B (BCODE) | Enterprise Application Software (EAS)
7701 | SAP CODVN B (BCODE) via RFC_READ_TABLE | Enterprise Application Software (EAS)
7800 | SAP CODVN F/G (PASSCODE) | Enterprise Application Software (EAS)
7801 | SAP CODVN F/G (PASSCODE) via RFC_READ_TABLE | Enterprise Application Software (EAS)
10300 | SAP CODVN H (PWDSALTEDHASH) iSSHA-1 | Enterprise Application Software (EAS)
8600 | Lotus Notes/Domino 5 | Enterprise Application Software (EAS)
8700 | Lotus Notes/Domino 6 | Enterprise Application Software (EAS)
9100 | Lotus Notes/Domino 8 | Enterprise Application Software (EAS)
133 | PeopleSoft | Enterprise Application Software (EAS)
13500 | PeopleSoft PS_TOKEN | Enterprise Application Software (EAS)
11600 | 7-Zip | Archives
12500 | RAR3-hp | Archives
13000 | RAR5 | Archives
13200 | AxCrypt | Archives
13300 | AxCrypt in-memory SHA1 | Archives
13600 | WinZip | Archives
14700 | iTunes backup < 10.0 | Backup
14800 | iTunes backup >= 10.0 | Backup
62XY | TrueCrypt | Full-Disk Encryption (FDE)
X | 1 = PBKDF2-HMAC-RIPEMD160 | Full-Disk Encryption (FDE)
X | 2 = PBKDF2-HMAC-SHA512 | Full-Disk Encryption (FDE)
X | 3 = PBKDF2-HMAC-Whirlpool | Full-Disk Encryption (FDE)
X | 4 = PBKDF2-HMAC-RIPEMD160 + boot-mode | Full-Disk Encryption (FDE)
Y | 1 = XTS 512 bit pure AES | Full-Disk Encryption (FDE)
Y | 1 = XTS 512 bit pure Serpent | Full-Disk Encryption (FDE)
Y | 1 = XTS 512 bit pure Twofish | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit pure AES | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit pure Serpent | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit pure Twofish | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit cascaded AES-Twofish | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit cascaded Serpent-AES | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit cascaded Twofish-Serpent | Full-Disk Encryption (FDE)
Y | 3 = XTS 1536 bit all | Full-Disk Encryption (FDE)
8800 | Android FDE <= 4.3 | Full-Disk Encryption (FDE)
12900 | Android FDE (Samsung DEK) | Full-Disk Encryption (FDE)
12200 | eCryptfs | Full-Disk Encryption (FDE)
137XY | VeraCrypt | Full-Disk Encryption (FDE)
X | 1 = PBKDF2-HMAC-RIPEMD160 | Full-Disk Encryption (FDE)
X | 2 = PBKDF2-HMAC-SHA512 | Full-Disk Encryption (FDE)
X | 3 = PBKDF2-HMAC-Whirlpool | Full-Disk Encryption (FDE)
X | 4 = PBKDF2-HMAC-RIPEMD160 + boot-mode | Full-Disk Encryption (FDE)
X | 5 = PBKDF2-HMAC-SHA256 | Full-Disk Encryption (FDE)
X | 6 = PBKDF2-HMAC-SHA256 + boot-mode | Full-Disk Encryption (FDE)
X | 7 = PBKDF2-HMAC-Streebog-512 | Full-Disk Encryption (FDE)
Y | 1 = XTS 512 bit pure AES | Full-Disk Encryption (FDE)
Y | 1 = XTS 512 bit pure Serpent | Full-Disk Encryption (FDE)
Y | 1 = XTS 512 bit pure Twofish | Full-Disk Encryption (FDE)
Y | 1 = XTS 512 bit pure Camellia | Full-Disk Encryption (FDE)
Y | 1 = XTS 512 bit pure Kuznyechik | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit pure AES | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit pure Serpent | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit pure Twofish | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit pure Camellia | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit pure Kuznyechik | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit cascaded AES-Twofish | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit cascaded Camellia-Kuznyechik | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit cascaded Camellia-Serpent | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit cascaded Kuznyechik-AES | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit cascaded Kuznyechik-Twofish | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit cascaded Serpent-AES | Full-Disk Encryption (FDE)
Y | 2 = XTS 1024 bit cascaded Twofish-Serpent | Full-Disk Encryption (FDE)
Y | 3 = XTS 1536 bit all | Full-Disk Encryption (FDE)
14600 | LUKS | Full-Disk Encryption (FDE)
16700 | FileVault 2 | Full-Disk Encryption (FDE)
18300 | Apple File System (APFS) | Full-Disk Encryption (FDE)
9700 | MS Office <= 2003 $0/$1, MD5 + RC4 | Documents
9710 | MS Office <= 2003 $0/$1, MD5 + RC4, collider #1 | Documents
9720 | MS Office <= 2003 $0/$1, MD5 + RC4, collider #2 | Documents
9800 | MS Office <= 2003 $3/$4, SHA1 + RC4 | Documents
9810 | MS Office <= 2003 $3, SHA1 + RC4, collider #1 | Documents
9820 | MS Office <= 2003 $3, SHA1 + RC4, collider #2 | Documents
9400 | MS Office 2007 | Documents
9500 | MS Office 2010 | Documents
9600 | MS Office 2013 | Documents
10400 | PDF 1.1 - 1.3 (Acrobat 2 - 4) | Documents
10410 | PDF 1.1 - 1.3 (Acrobat 2 - 4), collider #1 | Documents
10420 | PDF 1.1 - 1.3 (Acrobat 2 - 4), collider #2 | Documents
10500 | PDF 1.4 - 1.6 (Acrobat 5 - 8) | Documents
10600 | PDF 1.7 Level 3 (Acrobat 9) | Documents
10700 | PDF 1.7 Level 8 (Acrobat 10 - 11) | Documents
16200 | Apple Secure Notes | Documents
9000 | Password Safe v2 | Password Managers
5200 | Password Safe v3 | Password Managers
6800 | LastPass + LastPass sniffed | Password Managers
6600 | 1Password, agilekeychain | Password Managers
8200 | 1Password, cloudkeychain | Password Managers
11300 | Bitcoin/Litecoin wallet.dat | Password Managers
12700 | Blockchain, My Wallet | Password Managers
15200 | Blockchain, My Wallet, V2 | Password Managers
16600 | Electrum Wallet (Salt-Type 1-3) | Password Managers
13400 | KeePass 1 (AES/Twofish) and KeePass 2 (AES) | Password Managers
15500 | JKS Java Key Store Private Keys (SHA1) | Password Managers
15600 | Ethereum Wallet, PBKDF2-HMAC-SHA256 | Password Managers
15700 | Ethereum Wallet, SCRYPT | Password Managers
16300 | Ethereum Pre-Sale Wallet, PBKDF2-HMAC-SHA256 | Password Managers
16900 | Ansible Vault | Password Managers
18100 | TOTP (HMAC-SHA1) | One-Time Passwords
99999 | Plaintext | Plaintext
-a 破解模式
指定要使用的破解模式,其值参考后面对参数
- [ Attack Modes ] -
# | Mode
=+
0 | Straight # 直接字典破解
1 | Combination # 组合破解
3 | Brute-force # 掩码暴力破解
6 | Hybrid Wordlist + Mask # 字典+掩码破解
7 | Hybrid Mask + Wordlist # 掩码+字典破解
–increment
启用增量破解模式,让hashcat在指定的密码长度范围内执行破解
–increment-min
密码最小长度,后面直接等于一个整数即可,配置increment模式一起使用
–increment-max
密码最大长度,后面直接等于一个整数即可,配置increment模式一起使用
–force
忽略破解过程中的警告信息
–remove
删除已被破解成功的hash
–username
忽略hash文件中的指定的用户名,在破解linux系统用户密码hash会用到
–potfile-disable
不在potfile中记录破解成功的hash
-I
--opencl-info显示有关检测到的OpenCL平台/设备的信息,如果有一块好的显卡的话破解速度会快很多。
我的MacBook检测到了3个设备,分别是CPU、核显和独显
# sqlsec @ com in ~ [14:42:33] C:130
$ hashcat -I
hashcat (v5.1.0) starting...
OpenCL Info:
Platform ID #1
Vendor : Apple
Name : Apple
Version : OpenCL 1.2 (Sep 5 2019 21:59:08)
Device ID #1
Type : CPU
Vendor ID : 4
Vendor : Intel
Name : Intel(R) Core(TM) i7-9750H CPU @ 2.60GHz
Version : OpenCL 1.2
Processor(s) : 12
Clock : 2600
Memory : 4096/16384 MB allocatable
OpenCL Version : OpenCL C 1.2
Driver Version : 1.1
Device ID #2
Type : GPU
Vendor ID : 2147483648
Vendor : Intel Inc.
Name : Intel(R) UHD Graphics 630
Version : OpenCL 1.2
Processor(s) : 24
Clock : 1150
Memory : 384/1536 MB allocatable
OpenCL Version : OpenCL C 1.2
Driver Version : 1.2(Sep 25 2019 21:33:26)
Device ID #3
Type : GPU
Vendor ID : 1
Vendor : AMD
Name : AMD Radeon Pro 555X Compute Engine
Version : OpenCL 1.2
Processor(s) : 12
Clock : 300
Memory : 1024/4096 MB allocatable
OpenCL Version : OpenCL C 1.2
Driver Version : 1.2 (Sep 25 2019 21:23:46)
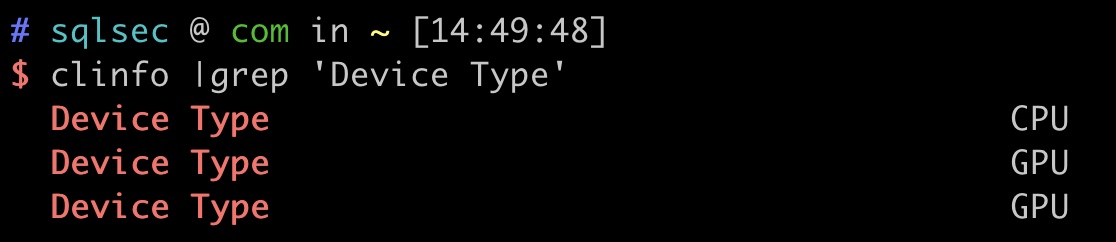
使用clinfo命令也可以看到你的设备的OpenCL相关信息:
# Linux 安装 clinfo
apt install clinfo
# macOS 安装 clinfo
brew install clinfo
# 查询 OpenCL 设备相关信息
clinfo |grep ‘Device Type’
-o
--outfile 指定破解成功后的hash及所对应的明文密码的存放位置
-O
--optimized-kernel-enable 启用优化的内核(限制密码长度)
-d
--opencl-devices指定opencl的设备,我这里支持的设备列表如下:
* Device #1: Intel(R) Core(TM) i7-9750H CPU @ 2.60GHz, skipped.
* Device #2: Intel(R) UHD Graphics 630, 384/1536 MB allocatable, 24MCU
* Device #3: AMD Radeon Pro 555X Compute Engine, 1024/4096 MB allocatable, 12MCU-D
--opencl-device-types指定opencl的设备类型,Hashcat支持如下设备类型:
1 | CPU
2 | GPU
3 | FPGA, DSP, Co-Processor一般常用-D 2指定GPU破解
所有参数
| 参数 | 类型 | 描述 | 案例 |
|---|---|---|---|
-m, --hash-type |
Num | Hash-type, see references below | -m 1000 |
-a, --attack-mode |
Num | Attack-mode, see references below | -a 3 |
-V, --version |
Print version | ||
-h, --help |
Print help | ||
--quiet |
Suppress output | ||
--hex-charset |
Assume charset is given in hex | ||
--hex-salt |
Assume salt is given in hex | ||
--hex-wordlist |
Assume words in wordlist are given in hex | ||
--force |
Ignore warnings | ||
--status |
Enable automatic update of the status screen | ||
--status-timer |
Num | Sets seconds between status screen updates to X | --status-timer=1 |
--stdin-timeout-abort |
Num | Abort if there is no input from stdin for X seconds | --stdin-timeout-abort=300 |
--machine-readable |
Display the status view in a machine-readable format | ||
--keep-guessing |
Keep guessing the hash after it has been cracked | ||
--self-test-disable |
Disable self-test functionality on startup | ||
--loopback |
Add new plains to induct directory | ||
--markov-hcstat2 |
File | Specify hcstat2 file to use | --markov-hcstat2=my.hcstat2 |
--markov-disable |
Disables markov-chains, emulates classic brute-force | ||
--markov-classic |
Enables classic markov-chains, no per-position | ||
-t, --markov-threshold |
Num | Threshold X when to stop accepting new markov-chains | -t 50 |
--runtime |
Num | Abort session after X seconds of runtime | --runtime=10 |
--session |
Str | Define specific session name | --session=mysession |
--restore |
Restore session from –session | ||
--restore-disable |
Do not write restore file | ||
--restore-file-path |
File | Specific path to restore file | --restore-file-path=x.restore |
-o, --outfile |
File | Define outfile for recovered hash | -o outfile.txt |
--outfile-format |
Num | Define outfile-format X for recovered hash | --outfile-format=7 |
--outfile-autohex-disable |
Disable the use of $HEX[] in output plains | ||
--outfile-check-timer |
Num | Sets seconds between outfile checks to X | --outfile-check=30 |
--wordlist-autohex-disable |
Disable the conversion of $HEX[] from the wordlist | ||
-p, --separator |
Char | Separator char for hashlists and outfile | -p : |
--stdout |
Do not crack a hash, instead print candidates only | ||
--show |
Compare hashlist with potfile; show cracked hashes | ||
--left |
Compare hashlist with potfile; show uncracked hashes | ||
--username |
Enable ignoring of usernames in hashfile | ||
--remove |
Enable removal of hashes once they are cracked | ||
--remove-timer |
Num | Update input hash file each X seconds | --remove-timer=30 |
--potfile-disable |
Do not write potfile | ||
--potfile-path |
File | Specific path to potfile | --potfile-path=my.pot |
--encoding-from |
Code | Force internal wordlist encoding from X | --encoding-from=iso-8859-15 |
--encoding-to |
Code | Force internal wordlist encoding to X | --encoding-to=utf-32le |
--debug-mode |
Num | Defines the debug mode (hybrid only by using rules) | --debug-mode=4 |
--debug-file |
File | Output file for debugging rules | --debug-file=good.log |
--induction-dir |
Dir | Specify the induction directory to use for loopback | --induction=inducts |
--outfile-check-dir |
Dir | Specify the outfile directory to monitor for plains | --outfile-check-dir=x |
--logfile-disable |
Disable the logfile | ||
--hccapx-message-pair |
Num | Load only message pairs from hccapx matching X | --hccapx-message-pair=2 |
--nonce-error-corrections |
Num | The BF size range to replace AP’s nonce last bytes | --nonce-error-corrections=16 |
--keyboard-layout-mapping |
File | Keyboard layout mapping table for special hash-modes | --keyb=german.hckmap |
--truecrypt-keyfiles |
File | Keyfiles to use, separated with commas | --truecrypt-keyf=x.png |
--veracrypt-keyfiles |
File | Keyfiles to use, separated with commas | --veracrypt-keyf=x.txt |
--veracrypt-pim |
Num | VeraCrypt personal iterations multiplier | --veracrypt-pim=1000 |
-b, --benchmark |
Run benchmark of selected hash-modes | ||
--benchmark-all |
Run benchmark of all hash-modes (requires -b) | ||
--speed-only |
Return expected speed of the attack, then quit | ||
--progress-only |
Return ideal progress step size and time to process | ||
-c, --segment-size |
Num | Sets size in MB to cache from the wordfile to X | -c 32 |
--bitmap-min |
Num | Sets minimum bits allowed for bitmaps to X | --bitmap-min=24 |
--bitmap-max |
Num | Sets maximum bits allowed for bitmaps to X | --bitmap-max=24 |
--cpu-affinity |
Str | Locks to CPU devices, separated with commas | --cpu-affinity=1,2,3 |
--example-hashes |
Show an example hash for each hash-mode | ||
-I, --opencl-info |
Show info about detected OpenCL platforms/devices | -I | |
--opencl-platforms |
Str | OpenCL platforms to use, separated with commas | --opencl-platforms=2 |
-d, --opencl-devices |
Str | OpenCL devices to use, separated with commas | -d 1 |
-D, --opencl-device-types |
Str | OpenCL device-types to use, separated with commas | -D 1 |
--opencl-vector-width |
Num | Manually override OpenCL vector-width to X | --opencl-vector=4 |
-O, --optimized-kernel-enable |
Enable optimized kernels (limits password length) | ||
-w, --workload-profile |
Num | Enable a specific workload profile, see pool below | -w 3 |
-n, --kernel-accel |
Num | Manual workload tuning, set outerloop step size to X | -n 64 |
-u, --kernel-loops |
Num | Manual workload tuning, set innerloop step size to X | -u 256 |
-T, --kernel-threads |
Num | Manual workload tuning, set thread count to X | -T 64 |
--spin-damp |
Num | Use CPU for device synchronization, in percent | --spin-damp=50 |
--hwmon-disable |
Disable temperature and fanspeed reads and triggers | ||
--hwmon-temp-abort |
Num | Abort if temperature reaches X degrees Celsius | --hwmon-temp-abort=100 |
--scrypt-tmto |
Num | Manually override TMTO value for scrypt to X | --scrypt-tmto=3 |
-s, --skip |
Num | Skip X words from the start | -s 1000000 |
-l, --limit |
Num | Limit X words from the start + skipped words | -l 1000000 |
--keyspace |
Show keyspace base:mod values and quit | ||
-j, --rule-left |
Rule | Single rule applied to each word from left wordlist | -j ‘c’ |
-k, --rule-right |
Rule | Single rule applied to each word from right wordlist | -k ‘^-‘ |
-r, --rules-file |
File | Multiple rules applied to each word from wordlists | -r rules/best64.rule |
-g, --generate-rules |
Num | Generate X random rules | -g 10000 |
--generate-rules-func-min |
Num | Force min X functions per rule | |
--generate-rules-func-max |
Num | Force max X functions per rule | |
--generate-rules-seed |
Num | Force RNG seed set to X | |
-1, --custom-charset1 |
CS | User-defined charset ?1 | -1 ?l?d?u |
-i, --increment |
Enable mask increment mode | ||
--increment-min |
Num | Start mask incrementing at X | --increment-min=4 |
--increment-max |
Num | Stop mask incrementing at X | --increment-max=8 |
-S, --slow-candidates |
Enable slower (but advanced) candidate generators | ||
--brain-server |
Enable brain server | ||
-z, --brain-client |
Enable brain client, activates -S | ||
--brain-client-features |
Num | Define brain client features, see below | --brain-client-features=3 |
--brain-host |
Str | Brain server host (IP or domain) | --brain-host=127.0.0.1 |
--brain-port |
Port | Brain server port | --brain-port=13743 |
--brain-password |
Str | Brain server authentication password | --brain-password=bZfhCvGUSjRq |
--brain-session |
Hex | Overrides automatically calculated brain session | --brain-session=0x2ae611db |
--brain-session-whitelist |
Hex | Allow given sessions only, separated with commas | --brain-session-whitelist=0x2ae611db |
掩码破解
掩码规则
? | Charset
===+=========
l | abcdefghijklmnopqrstuvwxyz # 小写字母 a-z
u | ABCDEFGHIJKLMNOPQRSTUVWXYZ # 大写字母 A-Z
d | 0123456789 # 数字 0-9
h | 0123456789abcdef # 数字 + abcdef
H | 0123456789ABCDEF # 数字 + ABCDEF
s | !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~ # 特殊字符
a | ?l?u?d?s # 键盘上所有可见的字符
b | 0x00 - 0xff # 可能是用来匹配像空格这种密码的自定义掩码规则
--custom-charset1 [chars]等价于 -1
--custom-charset2 [chars]等价于 -2
--custom-charset3 [chars]等价于 -3
--custom-charset4 [chars]等价于 -4在掩码中用?1、?2、?3、?4来表示
一些案例:
--custom-charset1 abcd123456!@-+此时?1就表示abcd123456!@-+
--custom-charset2 ?l?d此时?2就表示?l?d即?h 数字 + 小写字母
-3 abcdef -4 123456 此时?3?3?3?3?4?4?4?4就表示为前四位可能是abcdef,后四位可能是123456
字典破解
1q2w3e4r的MD5值为5416d7cd6ef195a0f7622a9c56b55e84
hashcat -a 0 -m 0 '5416d7cd6ef195a0f7622a9c56b55e84' hashpass.txt -o success.txt删除已破解密码
有时候破解的时候会出现如下提示:
INFO: All hashes found in potfile! Use --show to display them.这表明在之前该密码已经被我们破解成功了,Hashcat故不再显示出来,可以在后面添加参数--show来显示密码:
hashcat -a 0 -m 0 'cbc8f5435c87e13c5d14e6ce92358d68' hashpass.txt --show
cbc8f5435c87e13c5d14e6ce92358d68:123456@abcHashcat存放已经成功破解的密码文件位置为:~/.hashcat/hashcat.potfile
如果想要直接显示破解的密码的话,可以直接删除掉该文件。
批量破解
# 删除之前破解成功的记录
rm ~/.hashcat/hashcat.potfile
# hash.txt为要破解的密码 hashpass.txt为字典 导出破解的结果到success.txt 并从hash.txt删除掉破解成功的
hashcat -a 0 -m 0 hash.txt hashpass.txt -o success.txt --remove
组合破解
多字典破解
hashcat -a 1 -m 0 '5416d7cd6ef195a0f7622a9c56b55e84' hashpass1.txt hashpass1.txt字典+掩码破解
echo -n admin888 |openssl md5
7fef6171469e80d32c0559f88b377245破解admin888的MD5值:
hashcat -a 6 -m 0 '7fef6171469e80d32c0559f88b377245' hashpass.txt -O掩码+字典破解
hashcat -a 7 -m 0 '7fef6171469e80d32c0559f88b377245' 'admi?l?d?d?d' hashpass.txt -O破解案例
8位MD5加密的数字破解
对23323323进行MD5加密:
$ echo -n 23323323 |openssl md5
5a745e31dbbd93f4c86d1ef82281688b使用Hashcat来进行破解:
hashcat -a 3 -m 0 --force '5a745e31dbbd93f4c86d1ef82281688b' '?d?d?d?d?d?d?d?d' -O8位MD5加密的大小写字母破解
$ echo -n PassWord |openssl md5
a9d402bfcde5792a8b531b3a82669585使用Hashcat来进行破解:
hashcat -a 3 -m 0 -1 '?l?u' --force 'a9d402bfcde5792a8b531b3a82669585' '?1?1?1?1?1?1?1?1' -O这里面定义了个自定义规则-1,此时?1就表示?l?u,即大小写字母。
5-7位MD5加密的大小写字母+数字破解
Admin88的MD5值为d41e98d1eafa6d6011d3a70f1a5b92f0
hashcat -a 3 -m 0 -1 '?l?u?d' --force '2792e40d60bac94b4b163b93566e65a9' --increment --increment-min 5 --increment-max 7 '?1?1?1?1?1?1?1' -O这里面定义了个自定义规则-1,此时?1就表示?l?u?d,即大小写字母+数字。
admin开头10位MD5加密的大小写字母+数字破解
admin23323的MD5值为a9991129897a44e0d1c2855c3d7dccc4
hashcat -a 3 -m 0 -1 '?l?u?d' --force 'a9991129897a44e0d1c2855c3d7dccc4' 'admin?1?1?1?1?1' -OMySQL4.1/MySQL5
查看MySQL的密码:
mysql> select Password from mysql.user;
+-------------------------------------------+
| Password |
+-------------------------------------------+
| *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B |
| *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B |
| *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B |
| *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B |
+-------------------------------------------+
4 rows in set (0.00 sec)然后开始使用字典破解:
hashcat -a 0 -m 300 --force '81F5E21E35407D884A6CD4A731AEBFB6AF209E1B' hashpass.txt -OLinux /etc/shadow sha512crypt $6$, SHA512 (Unix)
查看/etc/shadow密码文件:
root@kali-linux:~# cat /etc/shadow
root:$6$4ojiBMDPrehqrLkX$d2T7Cn8LKkLk4SDXgCh1IEqjhnsUekXaNUXSxiZIwUTndSqyd.9sEcu80sX9DuEHGmHOeoMev2O0ACYtjMett1:18201:0:99999:7:::
daemon:*:18024:0:99999:7:::
bin:*:18024:0:99999:7:::
sys:*:18024:0:99999:7:::
sync:*:18024:0:99999:7:::
games:*:18024:0:99999:7:::
man:*:18024:0:99999:7:::
lp:*:18024:0:99999:7:::
mail:*:18024:0:99999:7:::
news:*:18024:0:99999:7:::
uucp:*:18024:0:99999:7:::
proxy:*:18024:0:99999:7:::
www-data:*:18024:0:99999:7:::
backup:*:18024:0:99999:7:::
list:*:18024:0:99999:7:::
irc:*:18024:0:99999:7:::
gnats:*:18024:0:99999:7:::
nobody:*:18024:0:99999:7:::
_apt:*:18024:0:99999:7:::
systemd-timesync:*:18024:0:99999:7:::
systemd-network:*:18024:0:99999:7:::
systemd-resolve:*:18024:0:99999:7:::
mysql:!:18024:0:99999:7:::
ntp:*:18024:0:99999:7:::
messagebus:*:18024:0:99999:7:::
arpwatch:!:18024:0:99999:7:::
Debian-exim:!:18024:0:99999:7:::
uuidd:*:18024:0:99999:7:::
redsocks:!:18024:0:99999:7:::
tss:*:18024:0:99999:7:::
rwhod:*:18024:0:99999:7:::
iodine:*:18024:0:99999:7:::
miredo:*:18024:0:99999:7:::
dnsmasq:*:18024:0:99999:7:::
postgres:*:18024:0:99999:7:::
usbmux:*:18024:0:99999:7:::
rtkit:*:18024:0:99999:7:::
stunnel4:!:18024:0:99999:7:::
sshd:*:18024:0:99999:7:::
Debian-snmp:!:18024:0:99999:7:::
sslh:!:18024:0:99999:7:::
pulse:*:18024:0:99999:7:::
speech-dispatcher:!:18024:0:99999:7:::
avahi:*:18024:0:99999:7:::
saned:*:18024:0:99999:7:::
inetsim:*:18024:0:99999:7:::
colord:*:18024:0:99999:7:::
geoclue:*:18024:0:99999:7:::
king-phisher:*:18024:0:99999:7:::
Debian-gdm:*:18024:0:99999:7:::
dradis:*:18024:0:99999:7:::
beef-xss:*:18024:0:99999:7:::
systemd-coredump:!!:18082::::::可以看到root是有密码的,前面使用的是$6表面hash的加密方式为:sha512crypt $6$, SHA512 (Unix)。
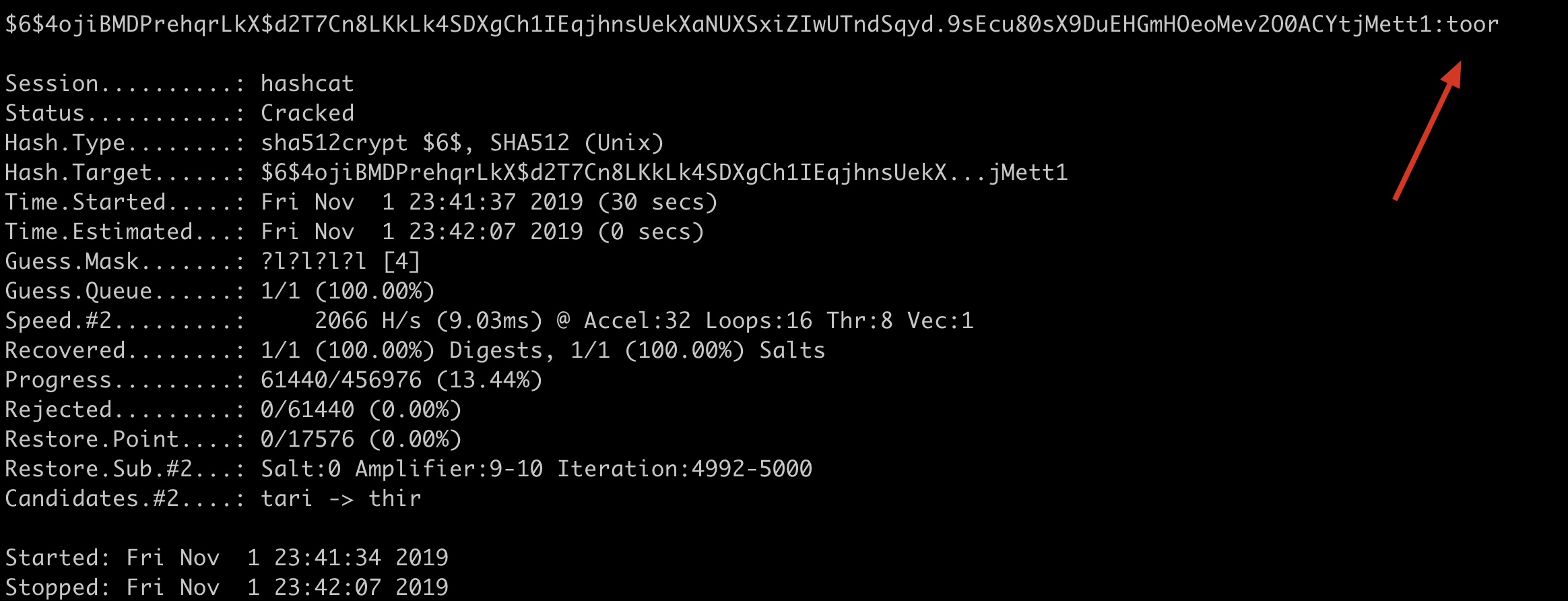
# 掩码破解root密码 不在potfile中记录破解成功的hash 指定设备2(核显)来跑密码 并开启优化
hashcat -a 3 -m 1800 --force '$6$4ojiBMDPrehqrLkX$d2T7Cn8LKkLk4SDXgCh1IEqjhnsUekXaNUXSxiZIwUTndSqyd.9sEcu80sX9DuEHGmHOeoMev2O0ACYtjMett1' '?l?l?l?l' -O -d 2 --potfile-disable
# 掩码破解root密码 忽略用户名 不在potfile中记录破解成功的hash 指定设备2(核显)来跑密码 并开启优化
hashcat -a 3 -m 1800 --force ‘root:$6
d2T7Cn8LKkLk4SDXgCh1IEqjhnsUekXaNUXSxiZIwUTndSqyd.9sEcu80sX9DuEHGmHOeoMev2O0ACYtjMett1’ ‘?l?l?l?l’ -O -d 2 --username --potfile-disable
macOS下自带的CPU和独显无法破解,这里国光本人手动切换了-d 2用核显才成功跑出来:
字典破解Windows LM Hash
hashcat -a 0 -m 3000 --force '921988ba001dc8e14a3b108f3fa6cb6d' password.txt字典破解Windows NTLM Hash
hashcat -a 0 -m 1000 --force 'e19ccf75ee54e06b06a5907af13cef42' password.txt分布破解
该功能目前有点坑,现在本地测试还没有顺利成功过,留在这边待以后完善
| 参数 | 类型 | 说明 | 国光的理解 | 示例 |
|---|---|---|---|---|
| –brain-server | Enable brain server | 启用主服务器 | ||
| -z, –brain-client | Enable brain client, activates -S | 启用分布式客户端 | ||
| –brain-client-features | Num | Define brain client features, see below | 定义客户端功能 | –brain-client-features=3 |
| –brain-host | Str | Brain server host (IP or domain) | 主服务器的IP或者域 | –brain-host=127.0.0.1 |
| –brain-port | Port | Brain server port | 主服务器端口 | –brain-port=13743 |
| –brain-password | Str | Brain server authentication password | 主服务器的认证密码 | –brain-password=e8acfc7280c48009 |
| –brain-session | Hex | Overrides automatically calculated brain session | 自动覆盖已经计算的主会话 | –brain-session=0x2ae611db |
| –brain-session-whitelist | Hex | Allow given sessions only, separated with commas | 仅允许给定的对话,以逗号分隔 | –brain-session-whitelist=0x2ae611db |
客户端功能
- [ Brain Client Features ] -
# | Features
=+==
1 | Send hashed passwords # 发送已破解的密码
2 | Send attack positions # 发送已破解的位置
3 | Send hashed passwords and attack positions # 发送已破解的密码和已破解的位置
参考链接
转自:https://www.sqlsec.com/2019/10/hashcat.html
作者:国光
