First, the four promoters ways:
1、mysqld
Start mysql server: ./mysqld --defaults-File = / etc / my.cnf --user = root
Client connection: MySQL --defaults-File = / etc / or the my.cnf mysql -S /tmp/mysql.sock
2、mysqld_safe
Start mysql server:. / = The mysqld_safe --defaults-File / etc / = the root & --user the my.cnf client connection: mysql --defaults-File = / etc / or the my.cnf mysql -S / tm / mysql .sock
3、mysql.server
cp -v /usr/local/mysql/support-files/mysql.server /etc/init.d/ chkconfig --add mysql.server Start mysql server: Start-Service the mysql.server { | STOP | the restart | reload | Force-reload | Status} Client connection: with 1, 2
4、mysqld_multi
mkdir $MYSQL_BASE/data2 cat <<-EOF>> /etc/my.cnf [mysqld_multi] mysqld = /usr/local/mysql/bin/mysqld_safe mysqladmin = /user/local/mysql/bin/mysqladmin user = mysqladmin password = mysqladmin [mysqld3306] port = 3306 socket = /tmp/mysql3306.sock pid-file = /tmp/mysql3306.pid skip-external-locking key_buffer_size = 16M max_allowed_packet = 1M table_open_cache = 64 sort_buffer_size = 512K net_buffer_length = 8K read_buffer_size = 256K read_rnd_buffer_size = 512K myisam_sort_buffer_size = 8M basedir = /usr/local/mysql datadir = /usr/local/mysql/data [mysqld3307] port = 3307 socket = /tmp/mysql3307.sock pid-file = /tmp/mysql3307.pid skip-external-locking key_buffer_size = 16M max_allowed_packet = 1M table_open_cache = 64 sort_buffer_size = 512K net_buffer_length = 8K read_buffer_size = 256K read_rnd_buffer_size = 512K myisam_sort_buffer_size = 8M basedir = /usr/local/mysql datadir = /usr/local/mysql/data2 EOF #mysql -S /tmp/mysql3306.sock mysql>GRANT SHUTDOWN ON *.* TO 'mysqladmin'@'localhost' identified by 'mysqladmin' with grant option; #mysql -S /tmp/mysql3307.sock mysql>GRANT SHUTDOWN ON *.* TO 'mysqladmin'@'localhost' identified by 'mysqladmin' with grant option; Start mysql server: / mysqld_multi --defaults-File = / etc / my.cnf Start 3306 - 3307 Close mysql server: mysqladmin shutdown
Second, start-up and shut down mysql service
1. windows below:
Start: mysqld - Console or net start mysql
Close: mysqladmin -u root the shutdown or net stop mysql
linux under:
Start: service mysql start
Stop: service mysql stop
Restart service: service mysql restart
Third, create a user assign permissions
1. New User: Create a file called: buff, password: buff users
// root user login MySQL MySQL-uroot-- the p- Enter password: // Create a new user MySQL> INSERT INTO the mysql.user (Host, the User, Password) values ( " localhost " , " BUFF " , password ( " BUFF " )); // Refresh system permissions table mysql> flush privileges;
Login Test
MySQL> Exit // user buff landing MySQL MySQL -ubuff - the p- Enter password: MySQL > // successful login Description New users buff
User Authorization
// root user login MySQL MySQL-uroot-- the p- Enter password: // buff create a database for the user bluebuff MySQL> the Create Database bluebuff; // authorized users buff has all the permissions database bluebuff MySQL> Grant All privileges ON bluebuff to buff * @ localhost IDENTIFIED by. ' Buff ' ; mysql>flush privileges;
Login Test
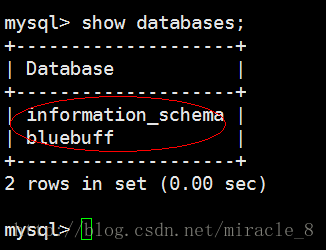
// user login buff database MySQL -ubuff - the p- Enter privileges: // display the database mysql> show databases;
The results shown below, illustrated as buff successfully authorized users
5, modify the user's password buff
// root user login MySQL MySQL-uroot-- the p- Enter password: // modify the user's password buff MySQL> Table Update the mysql.user SET password = password ( ' Buffer ' ) WHERE the User = ' buff ' and the Host = ' localhost ' ; mysql>flush privileges;
6, delete users
// root user login MySQL MySQL-uroot-- the p- Enter password: // 删除用户 buff mysql>delete from mysql.user where User = 'buff' and Host = 'localhost'; mysql>flush privileges;
7, delete the database
mysql>drop database bluebuff;
Fourth, view the user to grant permission
In mysql, privileges granted to users may be sub-global level permissions, database-level permissions, surface-level permissions, column-level permissions layer, the subroutine-level permissions
1. Global level:
Global privileges apply to all database servers in a given. These privileges are stored in mysql.user table. GRANT ALL ON *. * And REVOKE ALL ON *. * Only global grant and revoke privileges. Example: a create a test account test, granted permission to the global level. mysql> grant select,insert on *.* to test@'%' identified by 'test'; mysql> flush privileges; b. query privileges granted to the test show grants for test; select * from mysql.user where user='test'\G;
2, the database level:
Database privileges apply to all targets in a given database. These privileges are stored in mysql.db and mysql.host table. GRANT ALL ON db_name. * And REVOKE ALL ON db_name. * Only grant and revoke database privileges Example:. A create a test account test, grant database-level permissions drop user test; grant select,insert,update,delete on MyDB.* to test@'%' identified by 'test'; b. query privileges granted to the test SELECT * from the mysql.user WHERE User = ' Test ' \ G; - can be seen without any authorization SELECT * from the mysql.db WHERE User = ' Test ' \ G; show grants for test;
3, surface level:
Table privileges apply to all columns in a given table to. These privileges are stored in mysql.tables_priv table. GRANT ALL ON db_name.tbl_name and REVOKE ALL ON db_name.tbl_name grant and revoke only table privileges. Example:. A create a test account test, the surface level of permissions granted drop user test; flush privileges; grant all on MyDB.kkk to test@'%' identified by 'test'; b. query privileges granted to the test show grants for test; select * from mysql.tables_priv\G;
4, the column level:
Column privileges apply to a single column in a given table to. These privileges are stored in mysql.columns_priv table. When using REVOKE, you must specify the column authorized the same column. Example: a create a test account test, grant column level permissions. drop user test; flush privileges; grant select (id, col1) on MyDB.TEST1 to test@'%' identified by 'test'; flush privileges; b. query privileges granted to the test select * from mysql.columns_priv; show grants for test;
5, the subroutine level:
CREATE ROUTINE, ALTER ROUTINE, EXECUTE, and GRANT privileges apply to stored routines. These permissions can be granted to a global level and the database level. Moreover, in addition to the CREATE ROUTINE, these privileges can be granted to a subroutine hierarchy and stored in mysql.procs_priv table. Example: a create a test account test, awarded subroutine-level permissions. DROP PROCEDURE IF EXISTS PRC_TEST; DELIMITER // CREATE PROCEDURE PRC_TEST() -> BEGIN -> SELECT * FROM kkk; -> END // DELIMITER ; grant execute on MyDB.PRC_TEST to test@'%' identified by 'test'; flush privileges; b. query privileges granted to the test show grants for test; select * from mysql.procs_priv where User='test';
to sum up:
1. If you need permission to view the user is granted, it is necessary to see these five levels of permissions are granted. From top to bottom or from small to examine individual rights granted at all levels.
2. grant create routine, alter routine, select, create, insert, update, delete, execute on ….
3. If the client can not connect to the server, view the host entry in the user table is '%', and has authorized