1, the remote connection service concept introduced
SSH: the system can use the default configuration of 22 default root user login data is encrypted
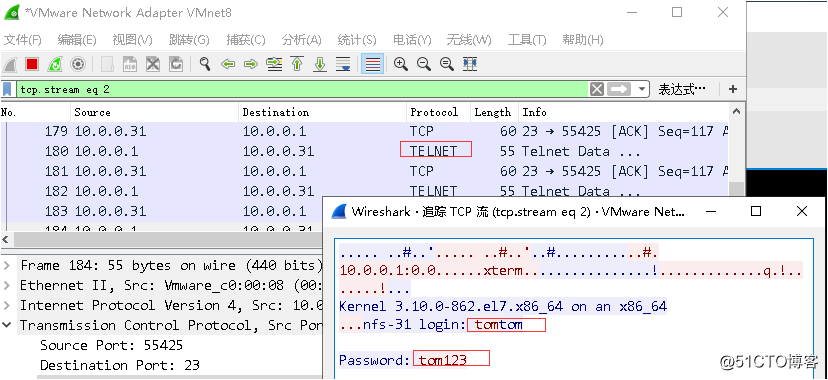
TELNET: 23 default network devices enabled by default only use ordinary user to log data in plain text information display
capture with wireshark: were arrested SSH protocol Telnet login packet and the packet (a ciphertext, a plaintext) 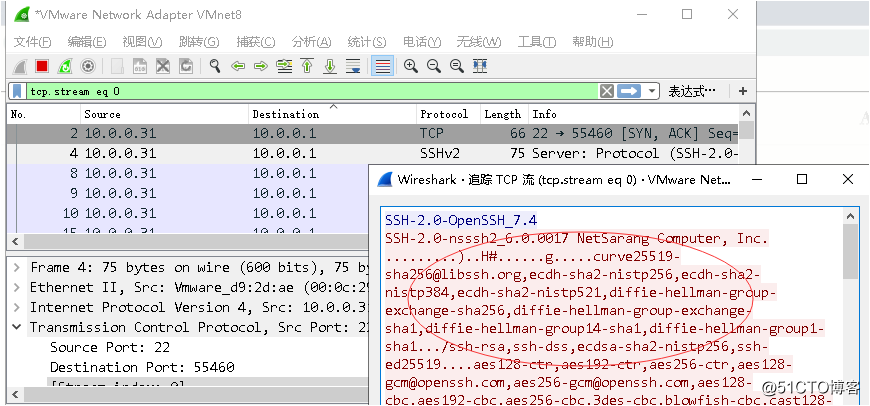
2, the SSH protocol log key principle:
1) the service key pair is generated (i.e. public and private keys and locks)
2) to other server host-initiated public key file or locks to store this /root/.ssh/authorized_keys
3) by the server private key to sign in to other hosts
3, the operation
to create a key pair
ssh-keygen 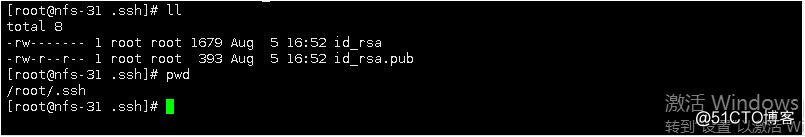
sent to another host 2, the public key or lock 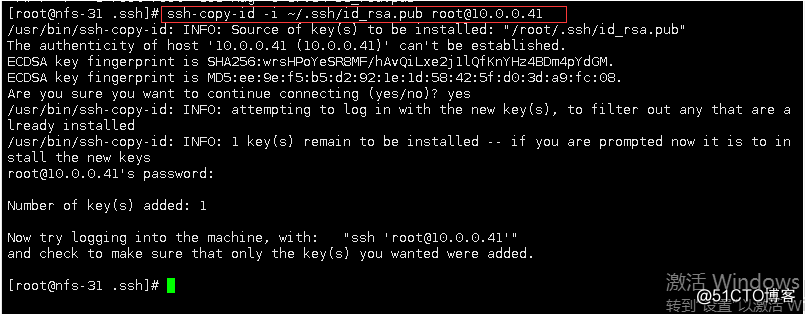
-free dense Login 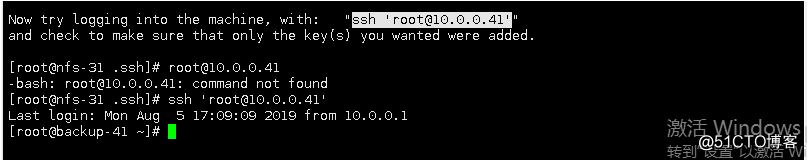
4, sends the public key to solve the first time there are yes / no question
1) find StrictHostKeyChecking by man ssh
command: ssh- copy-id -i /root/.ssh/id_rsa.pub 10.0.0.41 -o StrictHostKeyChecking = no
Sends the public key to solve the first problem or to enter a password
1) to put on a sshpass tool
yum -y install sshpass
sshpass SSH-Copy-the above mentioned id -i -o /root/.ssh/id_rsa.pub 10.0.0.41 StrictHostKeyChecking -proot123 = no
5, bursting the public key to multiple hosts
for i in {41,200}
do
sshpass -proot123 ssh-copy-id -i /root/.ssh/id_rsa.pub 10.0.0.${i} -o StrictHostKeyChecking=no
[ $? -eq 0 ] && echo "ok"
done 6, even if the operation of step 5, but still have to manually generate a key pair Enter operation, if production can be key to avoid interaction, the whole step we can achieve batch managed
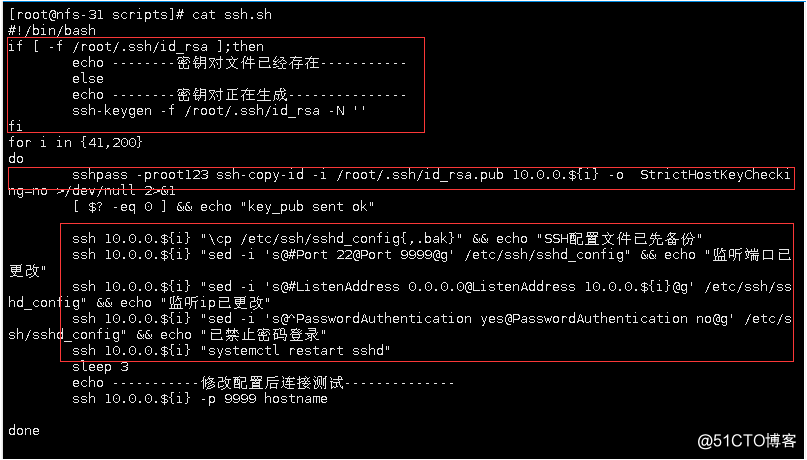
to write a better pace
#!/bin/bash
if [ -f /root/.ssh/id_rsa ];then
echo -------密钥对文件已经存在--------
else
echo -------正在生成密钥对文件--------
ssh-keygen -f /root/.ssh/id/id_rsa -N ''
fi(To manually generate a key pair Enter the part it is necessary to specify the file location, we -f parameter specifies the first, second, to confirm the password we -N parameter specifies a new password '' indicates that the following empty, that no new password. Such generate a key pair of operation
is a free interactive)
for i in {41}
do
sshpass -proot123 ssh-copy-id -i /root/.ssh/id_rsa.pub 10.0.0.${i} -o StrictHostKeyChecking=no >/dev/null 2>&1
[ $? -eq 0 ] && echo "ok"
done 7, optimized SSH
modifications on all other hosts
1) listening port 22
into 9999
2) monitor ip0.0.0.0 (all represented here, all the hosts themselves some ip, a host can have multiple ip. You even I time to write my own ip. I'm not indicate to connect the host ip, ssh not by limiting the client's ip to restrict access, with rysnc, nfs, nginx is not the same as not to be confused
into listening on a network segment or ip, 172.16.1.0 network representation allows the listener or ip, ssh remote
3) password authentication PasswordAuthentication yes
instead PasswordAuthentication no password can not. Other hosts want to sign the host by entering the account password is the board does not go, and this time only by the key management side of the Log