Title: Open Document and Open XML Security ( OpenOffice.org and MS Office 2007)
- summary,
OpenDocumentandOpen XMLare bothOfficea new format for opening files.OpenDocumentIsISOa standard popularized byOpenOffice.organdSun StarOffice.Open XMLIsMicrosoft Office 2007a new format for documentation,ECMAa standard. Both formats share the same basic principle: filesZIPin an archive , with an open schema, in contrastXMLto the older proprietary formats (MS Word,Excel, , ...).PowerPointHowever, they all suffer from a number of security issues, similar to the previous format: malicious actors can still embed and hide malware (Trojans and viruses)Officethanks to macros, scripts, objects and similar functions. This article covers security issues in technical detail, including antivirus and obfuscation techniquesOLEthat can be used to bypass antivirus , and describes how to design filters to safely remove unwanted parts.XMLZIP
1 Introduction
OfficeFile formats have always had security issues, mainly because they are rich in "active" features such as macros orOLEobjects[SSTIC03], or because documents hide information leakage[OSSIR03]. Recently, security researchers have paid more attention to these formats and related applications to discover many implementation vulnerabilities[CVEMSO,CVEOOo].- A typical scenario is as follows: A user receives a malicious document as an attachment to an email or through other means. Opening this file triggers some malicious code in a macro, object, or vulnerability, with or without user interaction, and the result can be damage to your computer. Many users currently feel
OpenOfficeorMS Office 2007are more secure than previous office suites for various reasons. - However, this may be an illusion, as announced in
Eric Filiol.SSTIC06 [ESAT1,ESAT2,ESAT3]For example, in2006March6, the firstStardust"proof-of-concept" virus, named , showed that the threatOpenOfficewas real for . Additionally,OpenOffice 2.0.2three vulnerabilities were discovered in that allow malicious code to bypass default security policies (bypassing macros andJavasandboxed warning popups). Open XMLis a new format based on open standards, the specification of which was just released byECMAandMicrosoftin2006, and a truly complete security analysis has not yet been released. This article highlights some of the security issues posed by these new formats and their associated office suites, and then proposes some solutions to protect our systems from the threats. It also shows thatZIPandXMLintroduce additional obfuscation potential for malicious code and highlights warnings about bypassing antivirus and content filters.- Original publication
www.springerlink.comavailable at: www.springerlink.com : http://dx.doi.org/10.1007/s11416-007-0060-2
1.1 Notes
These are the products and versions used for this analysis:
-
OpenDocumentnormv1.0 [ODSPEC10]. New version1.1 [ODSPEC11]has not been analyzed yet. -
OpenOffice v2.2.0 -
Open
XML ECMA-376specification, final version released in2006: .12[OXSPEC] -
Microsoft Office 2007version12.0.4518.1014. -
All tests are
Windows XP SP2performed on . -
This is not a complete security analysis, and some features such as encryption and digital signatures have not been thoroughly tested. This analysis focuses on security issues associated with the file format and the functionality of the application. The goal is not to find vulnerabilities such as buffer overflows. The research work for this article began in France
DGA / CELAR. An early version of this work was presented at the Security Conference in March2006and then in French at the Security Conference in March . In this document, may be referred to as or , and or simply .11PEPEC[PACSEC06]20076SSTIC[SSTIC07]OpenOffice.org"OpenOffice""OOo"Microsoft Office "MS Office""Office"
2 Two new “open” formats
OpenDocument v1YesOpenOffice v2uses an open format. It is also used by other office applications such asSun StarOffice,KofficeorAbiword. Has become the standard2006since January5. It is a new version of that was first released in month of year . There are many changes in the product, such as user interface and file formats. Yes The new default format for the main application: , and . It has been the standard since the end of the year and is gradually becoming the standard.OpenDocumentISOOffice 2007200612Microsoft OfficeOpen XMLMS OfficeWordExcelPowerPoint2006ECMAISO
OpenDocument and Open XML share similar features:
- They are both based on open file formats and are widely used: documents mainly consist of files
ZIPin compressed archivesXML. - Their specifications are open and freely available on the Internet:
[ODSPEC10,ODSPEC11,OXSPEC]. - They are all accepted as standards by international
OpenDocumentbodies :ISO,Open XML.ECMA - They all handle common office document formats: text, spreadsheets, presentations, vector drawings.
By studying the published specifications more closely, some differences can be highlighted:
Open XMLThe structure isOpenDocumentmore complex and the functions are richer than . Microsoft aims to handleOfficeall existing features of its suite;OpenDocumentrather it is more of a documentation model.OpenDocumentThe specification is only700pages long, andOpen XMLit reaches6045pages!Open XMLThere are many interesting features in the specification that are not yet covered by security, such asVBAmacros,OLEobjects or encryption. According to page[ECMA]115,MicrosofttheseECMAfeatures are consideredOpen XMLproprietary technologies beyond the scope of the standard. Therefore,MS Officethe resultingOpen XMLfile format is not fully disclosed and the standard should be considered only a subset of the file format. In practice, antivirus and content analysis filters must handle the entire format, including these unspecified proprietary features.OpenDocumentThe specification is not yet complete as this is still a work in progress and is not intended to protect the technology from leaks. More information about the security features can be found in other documentation, andOpenOffice.orgthe full source code is available.- Compared to proprietary file formats, security analysis of
OpenDocumentand is easier due to its open status.Open XMLHowever, the complexity of their specifications and the lack of some details does not make them oversimplified.
3 A few words about vulnerability exploitation
- Today,
Officethe most common threats to documents do not involve macros orOLEobjects, but are based on[CVEMSO,CVEOOo]vulnerabilities in office suites. SinceOpenDocumentand consists ofOpen XMLstructured and well-definedXMLrather than binary data, it can be assumed that vulnerabilities associated with format decoding are much less likely. Additionally, if office applications use strictXMLschema to validate data, malformed documents should not be able to trigger potential vulnerabilities. However,OpenDocumentandOpen XMLnot only includeXML: the binary parts (such as bitmap pictures andOLEobjects) are still present,Officethe suite also relies on external libraries to handle certain types of data, and these libraries may be vulnerable to attacks. Another problem is that due to its open specification, many third-party applications will be created to handle these formats. Since the format is not that simple , one can guess that vulnerabilities will also be found in these applications.
4 OpenDocument and OpenOffice.org
4.1 OpenDocument format
- The current
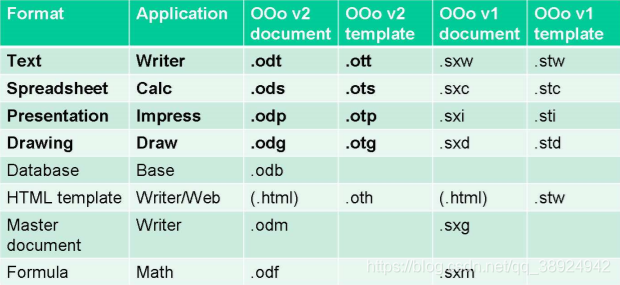
OpenDocumentspecification[ODSPEC11]covers onlyOpenOffice v2a subset of the various file formats handled by the suite. Only text documents, spreadsheets, presentations and vector drawings are described. Although other document types such as databases,HTMLtemplates, and mathematical formulas share a very similar structure. The following table shows the extensions associated with most native formats used byOpenOffice v1and . The format described in the specification is highlighted in bold.v2OpenDocument
4.2 Internal structure
- Each document is stored in
ZIPa compressed archive. It basically consists of severalXMLfiles, which are located in the root directory or subdirectories of the archive. The following are the main files in common documentationXML:
- content.xml:文档正文
- styles.xml:样式数据
- meta.xml:元数据(作者,标题,...)
- settings.xml:文档的 OOo 设置
- META-INF / manifest.xml:文件描述
- Note that other non-
XMLfiles may also be stored in the archive:
- 图片和缩略图:JPEG,PNG,SVG等
- 嵌入式图表/图纸/文档,OLE 对象
4.3 Macros
- The most important security issue involves macros.
OpenOffice v2Provides4three different languages for writing macros:Basic,JavaScript,Java(Beanshell) andPython. More languages may be added in the future. RegularOpenOfficeinstallations include these interpreters or rely on external interpreters such asJVM( virtual machines).Java - Each macro language has access to a
UNOvery powerful object called (Universal Network Object)API, which can run on the operating system. Therefore, effective malware can be written. Additionally, macros can be assigned to events and can be started automatically when a document is opened or read. - Since
2006, antivirus vendors have reported at least3threeOpenDocumentattempts to write viruses using macros:Stardust,StarbugsandBadBunny. However, none of them have the ability to run without user confirmation. - To protect users from malicious macros, security levels
OpenOfficeare provided , very similar to :4MS Office 2000/XP/2003
- 低(要避免):完全没有保护。
- 中(默认):用户可以在访问文档之前启用宏(简单弹出警告)。
- 高:仅允许签名的宏或受信任的目录。 如果已接受签名授权或来自受信任位置,则不会发出警告。
- 非常高:只有受信任的位置,没有签名,没有警告
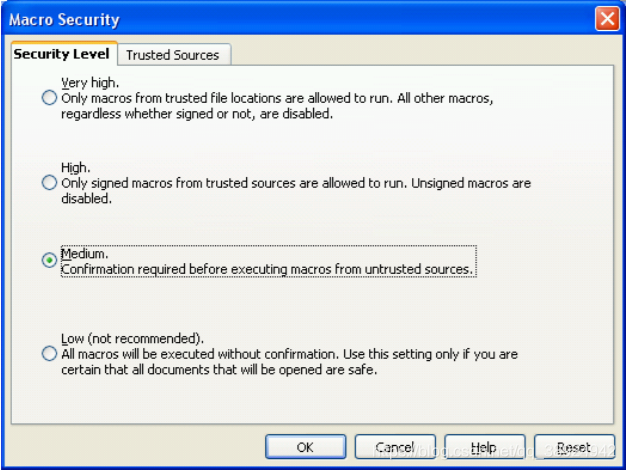
- The default level is Medium, so if there are macros in the document, a popup will ask the user if they want to enable or disable macros before allowing the file contents to be viewed.
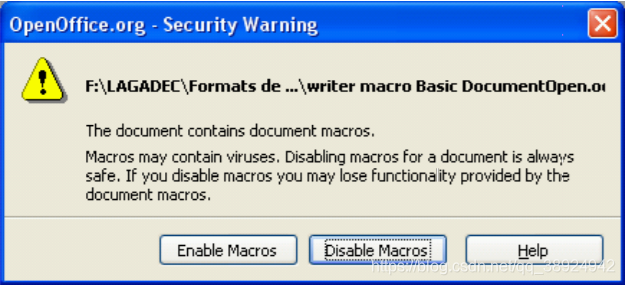
- Note that this
MS Office 97is the same as the default level in . Since2000version ,MS Officethe default level has been changed to High, and only signed macros have permission to run. - However, in the next release scheduled for month and year
2007, the default security level should be changed to High.9OpenOffice v2.3 - In
2006mid-year,OpenOffice 2.0.2a vulnerability was discovered in (and has since been patched) that could allow an attacker to bypass macro security warnings - Macro Storage: Macro files are located in different subdirectories
OpenDocumentwithin the file :2
- 基本宏存储在存档的 “基本” 目录中的 XML 文件中。
- Java(Beanshell),JavaScript 和 Python 宏存储在脚本文件的 “Scripts” 目录中。
- example:
- Basic / Standard / Module1.xml
- Scripts / beanshell / Library1 / MyMacro.bsh
- Scripts / javascript / Library1 / MyMacro.js
- Scripts / python / MyMacro.py
OpenOffice v2Macros can be created and edited from applications inBasic,Javaand using .JavascriptCurrently,Pythonmacros still require manual work (see[OSFP]): including the file in the archive, and editing itmanifest.xml.- Macro signing:
ESATOne of the main issues discovered by researchers is that macros are not signed with the rest of the document. The macros in the signed document can then be modified and fool the user into thinking he is opening a real document[ESAT1,ESAT2,ESAT3]. VBAMacros:2Starting from version ,OpenOfficeit is already possible to read the macro source codeMS Officein the documentVBA. Currently, it is not possibleOpenOfficeto actually runVBAmacros from .- When
MS Officea document is converted toOpenDocumentformat,VBAmacros are stored in clear textOOo Basicin the macro's comments. Therefore, even if there is no active code, the document will trigger the same warning as a normal macro. However, if you convert the document back to format, macrosMS Officewill be reactivated .VBA - Work is ongoing to provide native macro support using
UNOwrappers from . Some alternative versions have provided limited support for macros.OpenOfficeVBA2007Excel
4.4 OLE objects
- After macros, the second major security issue involves embedded
OLEobjects. You canOpenDocumentstore many types ofOLEobjects in files andWindowsopen them at least on . OLEObjects are typically stored in binary filesMicrosoft OLE2named in the archive root directory in the format (also known as structured storage) .“Object xxx”Therefore, even ifOpenDocumentit is an open format, it can also save parts of a closed format.- The most dangerous
OLEobject type isOLEa package: it may contain any file, including executable files or any command line. If the user double-clicks the object, the system will launch the file or command after a warning pops up. OLEThe warning before opening a package object only comes fromWindows(packager.exe), not fromOpenOffice. Therefore, this can beWindowsa significant security issue on older systems. For example,Windows 2000 SP4on , there are no warnings at all.- Additionally, a vulnerability was discovered in and that could trick users into launching a command
2006lineWindows XP.2003 [MS06-065]Just add a slash and the file name to the end of the command line andOLEthe package object will appear as a harmless text file. Here is an example:
cmd.exe /c [...malicious commands...] /joke.txt
4.5 Script
- Scripts can be embedded in documents using
Javascriptthe or language . These are not run directly by . However, if the documents are saved , they may be launched by the browser and the exploit can be triggered. Scripts are stored in tags in , for example:VBscriptHTMLOpenOfficeHTMLcontent.xml<text:script>
<text:script script:language=”JavaScript”>
alert("test script");
</text:script>
- The script's source code can be included directly in the markup or placed in an external script file,
“xlink:href”referenced by the attribute.
4.6 Java applets
JavaYou can also store applets in documents . ThisJavais different from macros written in the language. These compiles runappletin anOpenOfficeinternalJavasandbox. Because of the sandbox, malicious actorsappletcannot do harmful things. However, if a vulnerability exists, it is sometimes possible to avoid the sandbox, as isOpenOffice 2.0.2the case in .
4.7 URL links
- Documents can contain
URLlinks. When the user clicks on them, if externalURL,OpenOfficethe browser will be opened using the provided address. Hope it seems impossible to startjavascriptor in this wayvbscript URL, since those starting with“javascript:...”and are filtered out.“vbscript:...”URL - However, if the browser has
Webauthenticated within a sensitive application, it is still possible to direct the user to a malicious website, or launchXSRFan attack (cross-site request forgery,[XSRF]). - Additionally, a recently
OpenOffice v2.1discovered vulnerability in makes it possible to execute local commands onLinuxand by inserting an escape character for in .SolarisURL [OOoURL]shell
4.8 Hidden data - information leakage
- Just
MS Officelike in ,OpenDocumentfiles may hide sensitive data from users: metadata, hidden text, comments, revision marks, etc…InternetThis can become a problem when documents are published on or sent outside the corporate network. - To solve this problem,
OpenOfficesome interesting functions are provided toPDFwarn about hidden information when signing, exporting as or saving. However, this is not sufficient in all cases, as this does not includeOLEdata that may be hidden within the object.
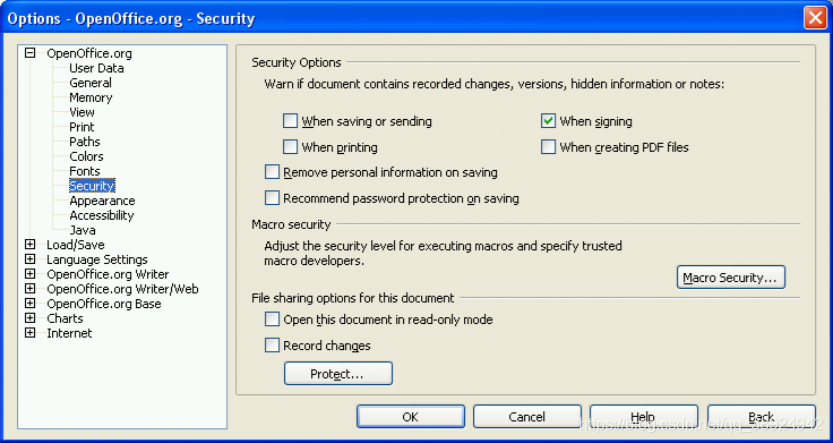
4.9 Conclusion on OpenDocument / OpenOffice security
- There are many ways to include active content into
OpenDocumentfiles and potentially launch malicious code. Even though there are some protections available to avoid this, none of them are completely safe. Additionally, vulnerabilities are nowOpenOffice [CVEOOo]frequently discovered in , which requires vigilance and frequent software updates. - Even if
OpenDocumentit is an open format, a file may sometimes contain parts of a closed format, such asMicrosoft OLEobjects. In summary, it can be saidOpenOfficethat is noMicrosoft Officemore secure or less secure than We have seen that we can find similar security issues in malware or hidden data. There are of course some differences, and certain features are more secure in one product than another. - However, analyzing and filtering
OpenDocumentactive content or hidden data in the format is much simpler than with typical proprietary office formats.
5 Open XML and Microsoft Office 2007
Open XMLIsMS Office 2007the new default file format for major applications:Word,ExcelandPowerPoint.Open XMLThe file has new extensions:
– Word: .docx, .docm, .dotx, .dotm
– Excel: .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xlam
– PowerPoint: .pptx, .pptm, .ppsx, .ppsm
– Access: .accdb (new binary format, not Open XML)
- Due to "compatibility mode", old binary formats from previous
Officeversions ( ) can still be read and written.OLE2Converter packages are also available for free fromMS Office 2000,XPand2003read and writeOpen XMLdocumentation. If the converter package is installed, most of the issues described below are related to these versions.
5.1 Open XML structure
- Basically,
Open XMLa document is aZIPcompressed archive whoseXMLfiles are justOpenDocumentlike . However, the structure is slightly more complex. It follows newMicrosoft Open Packaging Conventions, orOPC(see[OXSPEC]section2), shared by other formats, such asXPS [XPS](XPSis aPDFnewMicrosoftformat similar to ). - In
OPCan archive, each data file is called a part. The type of each section is described in the file in the root directory of the archive“[Content_Types] .xml”. There are also“.rels”files that store indirect relationships between parts. UnlikeOpenDocument, there is no direct relationship. - In
Open XMLDocuments, data is stored in multipleXMLfiles, which are different for each application. Here isWordan example of a document:
- word/document.xml:文档正文
- word/styles.xml:样式数据
- word/settings.xml:文档的设置
- docProps/app.xml 和 core.xml:元数据(作者,标题,...)
- There may also be optional binaries:
- 图片和其他媒体:JPEG,PNG,GIF,TIFF,WMF,......
- OLE对象,VBA宏,打印机设置,......
5.2 VBA macro
- As for
OpenDocument, the main security concern is thatOpen XMLdocuments may contain macros that provide enough functionality to write effective malicious code. These areVBAmacros, just like the previousMS Officeformat. - One big change is
MS Office 2007the distinction between "normal" and "macro-enabled" documents. Ordinary documents end with an "X" (for exampleDOCX,XLSX,PPTX) and cannot contain macros. To store macros in a document, it must be saved in a "macro-enabled" format, which ends with an "M" (for exampleDOCM,XLSM,PPTM). - If
DOCMthe file is renamedDOCX,Office 2007the file will be rejected as "corrupted". - Security levels:
Office 2007Macro security has also changed a lot. - In previous
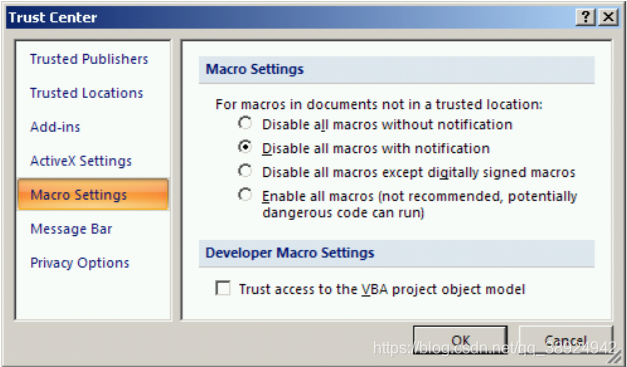
Officeversions, users could only launch signed or trusted macros by default because High Security mode was enabled by default. - In
Office 2007, there are no more medium or high security levels. The new default level is called "Disable all macros with notifications." New additional levels are also available in the new Trust Center, which is a central location for setting all security parameters.
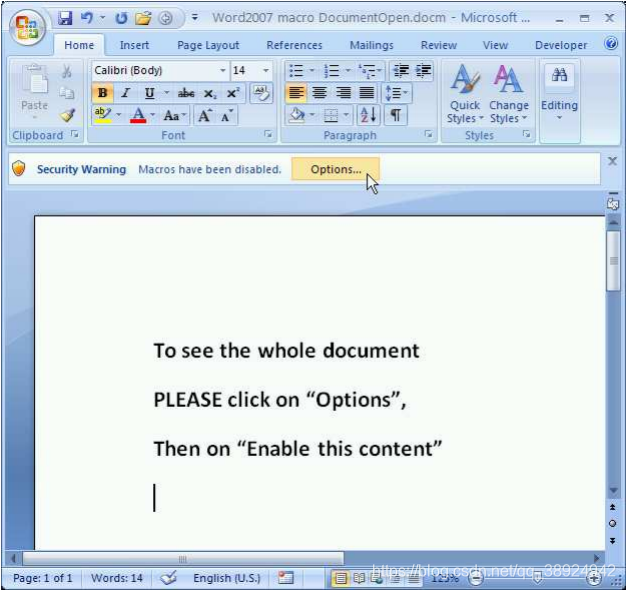
- Whenever a user opens a document that contains macros, the content is displayed, the macros are disabled, and a warning message is displayed under the Ribbon.
- By clicking on this message, the user gets a window that allows him to enable the signed macro.
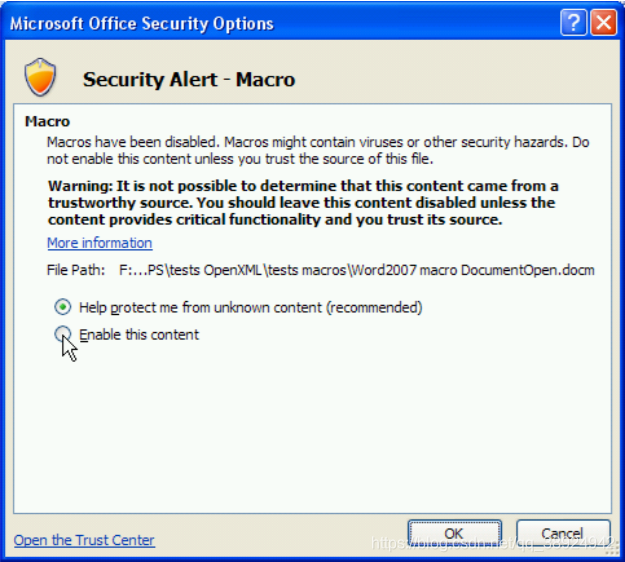
3The new default security level then allows users to launch unsigned macros with a few clicks without carefully reading all warning messages . Additionally, the documentation can be read before deciding to enable macros, which provides some social engineering possibilities.- Macro storage:
VBAMacros are stored invbaProject.bina file called , the path in the archive depends on the application:
– Word: word/vbaProject.bin
– Excel: xl/vbaProject.bin
– PowerPoint: ppt/vbaProject.bin
- This is a binary file using a format (structured storage) that is not described
Microsoft OLE2in the currentOpen XMLspecification .[OXSPEC] - If the macro has a specific name, such as
Word,“Document_Open”it may be triggered automatically when the document is opened.
5.3 OLE objects
- As in
OpenDocumentprevious versions, objects can be stored in documentsOfficewith the same security concerns .Open XMLOLE - These objects are usually stored in various locations in the archive in their original format depending on the application:
Worde.g. Store package objects“word/embeddings”in binary format .OLE2OLE Open XMLAs with macros, object storage is not described in the current specificationOLE.- Some situations can lead to strange results. For example, a workbook with macros (
.xlsm) can be stored as an object in a normal document without macros ( ). There are no warnings when opening the document. However, as soon as the user activates the object, a pop-up window appears asking if macros should be enabled. This is always the case even if the security level is "Disable all macros without notifications"...Excel.docxWordWordExcel
5.4 Excel 2007 Binary Workbook
Excel 2007Workbooks can be saved in a mixedOpen XMLformat, called a "binary workbook" with the extension“.xlsb”. This format is very closeOpen XML, except that some data is stored in binary files instead ofXML. This undocumented format looks like what previousExcelversions usedBIFF8. Binary workbooks may contain macros.
5.5 Hidden data - information leakage
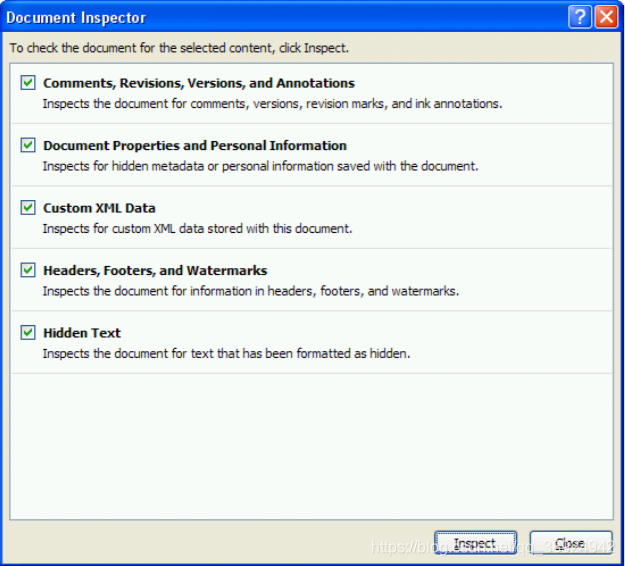
Office 2007A new tool called Document Inspector is available for detecting and removing many types of hidden data in documents. It isRHDToolan improved version of and canOffice 2003be installed with .- This is certainly a very interesting feature. Just
OpenOfficelike with ,OLEobjects are not detected as potentially hidden data, so the results are not always completely accurate.
5.6 Conclusion on the security of Open XML and MS Office 2007
- According to this analysis, the new format has the same malicious code and hidden data security concerns
Open XMLas the previous binary format.OfficeFor some aspects, such as macros, the default security settings may even be more permissive than before. - Even
Open XMLif based on an open specification,Microsoft Office 2007the generated documentation may contain some proprietary non-document formats (e.g.MS OLE2orBIFF), and these parts are often important for security issues. Furthermore, some major features (such as macros) are notOpen XMLpart of the specification, so the actual format cannot be considered100%open from a security perspective. - As
OpenDocumentwith ,Open XMLit is easier to parse and filter than the closed format; however, its internal structure is more complex and requires more sophisticated processing.
6 How to Prevent These Security Issues
- There are two main complementary technology solutions for protecting systems from malicious content and information leakage caused by office documents:
- 加强办公套件的安全设置
- 过滤网关或可移动设备上的文档
- We did not mention organizational solutions such as documentation to better inform users of malicious content and information leaks.
6.1 Security settings for OpenOffice and MS Office 2007
- Here are some general principles for improving the security settings of both office suites as needed
- 当然,如果可能的话,首先应用安全更新。
- 根据用户的实际需要,将宏和 ActiveX 安全级别加强到最高位置。
- 如果需要宏,请使用带有公司 PKI 的数字签名。 如果不可能,请仔细设置使用受信任的目录。(避免使用自签名证书,个人使用除外)
- 如果未使用,则禁用所有受信任的目录。 至少禁用用户具有写访问权限的那些。
- 防止很少使用的OLE包对象:禁止使用文件权限执行 “C:\Windows\System32\Packager.exe”。
Specific settings for MS Office 2007:
- 禁用通知消息,以避免使用未签名的宏。
- 或者,通过设置此注册表项,甚至可以禁用 VBA 引擎,但功能有所损失:HKLM\SOFTWARE\Microsoft\Office\12.0\Common\VBAOff = 1
- 在网络上部署安全设置以改进管理任务,例如使用 GPO。在 Microsoft 网站上查找 “2007 Office System 管理模板” 以获取模板。
- 如果无法做到这一点,例如在独立工作站上,请使用 HKLM 注册表项或文件/注册表权限保护安全设置,以便用户无法修改它们。可以在上述模板中找到 Office 2007 的 HKLM 和 HKCU 注册表项。与以前的 Office 版本不同,似乎并非所有安全设置都可以使用 HKLM 密钥进行保护。例如,用户可以在 HKCU 中修改宏安全级别,除非设置注册表权限以避免它。
- 有关详细信息,Microsoft 提供了一些文档,其中包含以下建议:http://go.microsoft.com/fwlink/ LinkID=85671
OpenOfficeSpecific settings for: ForOpenOffice, security settings such as macro security level are located inXMLFile (.xcu) and Other Settings.Program FilesGlobal settings are first read from a file in the application directory ( )XCU, and then user-Documents and Settingsspecific settings are read from the user profile ( ). You can also store some settings inLDAPa directory so that they can be easily deployed on the network.- By default, users can override any setting in their profile. However, you can protect selected settings from user error by adding the and attributes to the tag
XCUin the file .XML“finalized”“mandatory” - For example, macro support for all users can be disabled by adding the following line to the file
Common.xcu( in ).Program Files\OpenOffice.org 2.2\share\registry\data\org\openoffice\Office\This will also hide the macro security settings in the application.
<node oor:name="Security">
<node oor:name="Scripting">
<prop oor:name="MacroSecurityLevel" oor:type="xs:int" oor:finalized="true" oor:mandatory="true">
<value>3</value>
</prop>
<prop oor:name="DisableMacrosExecution" oor:type="xs:boolean"oor:finalized="true" oor:mandatory="true"
<value>true</value>
</prop>
</node>
</node>
- Note that this does not mean obtaining a fully trusted
OpenOfficeconfiguration on highly sensitive systems, as advanced users are often able to run applications from alternate directories or override settings by editing certain files. However, this protection is always better than the default setting. - Currently, there are no known tools and no comprehensive documentation to help administrators set up security settings. The best way to discover the available settings is to look at the files located
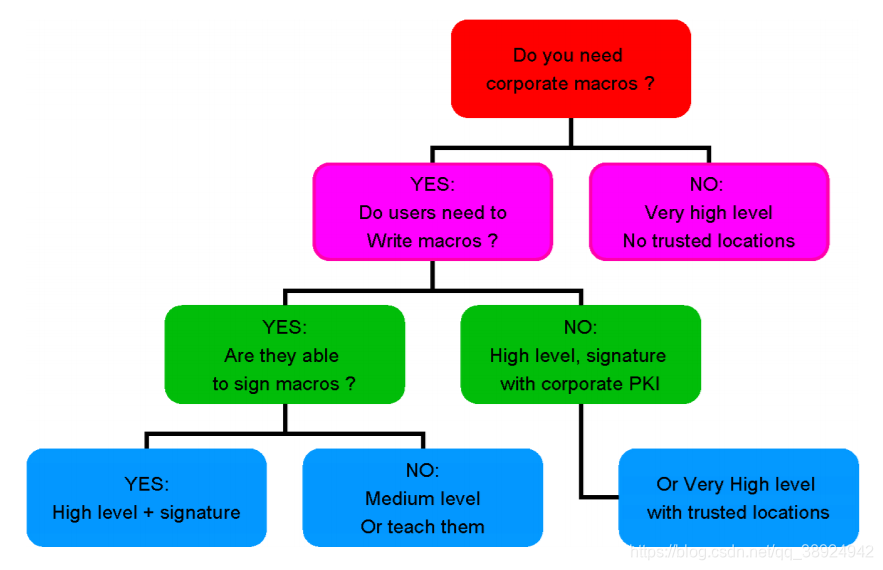
Program Files\OpenOffice.org 2.2\share\registry\schema\org\openoffice\inXCS, specificallyCommon.xcs. Label<group oor:name =“Security”>Contains most security settings along with comments about their effects. The following isOpenOfficean example of a decision tree for selecting security settings for a macro:
6.2 Filtering files - content analysis and anti-virus
- Documents can be filtered on the gateway (for email,
Web, file transfer...) or on removable devices. It can include the usual antivirus analysis or a more complex filtering process.OLEAn example of such a process is the removal of all active content from a document (macros, scripts, objects,…) or hidden data. - Since both
OpenDocumentand andOpen XMLuse standard techniques such as and , it can be assumed that these formats can be easily parsed and filtered using common tools and librariesZIP.XMLIn fact, all active elements such as macros and objects can be easily found. OpenDocumentExample filter for: To remove all active content:
- 宏:删除 Basic 和 Scripts 目录中的任何文件。
- OLE 对象:删除名称以 “Object” 开头的任何文件。
- 在 content.xml 中:
•删除 OLE 对象:<draw:object-ole>
•删除脚本:<text:script>
•删除小程序:<draw:applet>
•更新链接到宏的任何标记,例如:<office:event-listeners>
- Example filter for Open XML: To remove all active content:
- 宏:删除任何文件 “vbaProject.bin” 和 “vbaData.xml”
- OLE 对象:删除任何文件 “* .bin”
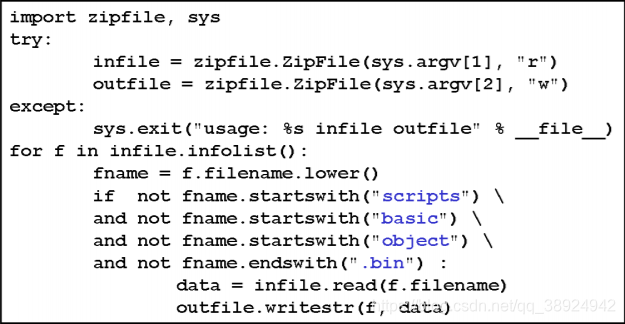
- Very simple filter for
OpenDocumentand : This is a very simple filter in and it only removes potentially active files in the document.Open XMLPython
6.3 Bypassing antivirus and filters
- As we have seen, it is very tempting to use simple techniques to analyze or filter these open formats using common
ZIPtools and libraries or text-based searches in files.XML - However, attackers may obfuscate malicious content in a variety of ways to bypass filtering gateways or antivirus software. To do this, just use the office suite,
XMLandZIPthe native functions of the format. Here are some potential confusion techniques: - Renaming Open XML documents using macros:
Open XMLFirst, it is unreliable to filter out documents with macros using just the file extension . Even though a file can never contain macros, the document can always be renamed“.docx”if blocked on the gateway .“.docm”“.docm”“.doc” - Rename OpenDocument macros:
OpenDocumentFiles containing macros can be renamed in the archive, replacing.xml,.bsh,.jsor.pywith any other extension. To do this, simply editmanifest.xmlandcontent.xmlto change the link to the macro file. In summary, file extensions are notOpenDocumenta good criterion for detecting macros in . Hopefully the directories“Basic”and“Scripts”have fixed names in the current implementation and they only contain macro-related files, so this is a safe way to detect or remove macros. - Renaming VBA macros in Open XML: Due to
Open XML(OPCthe modular structure of ), files containing macros of any name can be renamed“vbaProject.bin”. For example, inWordthe documentation:
- 将 “vbaProject.bin” 重命名为 “no_macros_here.txt”
- 更新 “word/_rels/document.xml.rels” 中的关系
- 在 n “[Content_Types].xml” 中,将 “bin” 替换为 “txt”
- This simple operation allows bypassing
Pythonthe filter shown above, keeping the macro active. Therefore, it is not possible to rely on filenames to detectOpen XMLmacros in . A safer solution is to use a realXMLparser that detects the and parts in[Content_Types].xml(orOLEobject's ) objects . Another solution is to analyze the contents of each file looking for binary headers with potential false positives .“oleObject”“vbaProject”“vbaData”OLE2 - Open XML - US-ASCII encoding and "obfuscated bits": As with
Internet Explorer(see[IEASCII]),Office 2007the handling of“USASCII”encoding is rather strange: all characters withASCIIcode greater than have only their bit content removed before being parsed. Therefore, this behavior allows very simple obfuscation of the filter/antivirus without checking it. Here are examples of tags being obfuscated:127XML8<HIDDENTAG>
<?xml version="1.0" encoding="us-ascii" standalone="yes"?>
1/4HIDDENTAG3/4 malware[...] 1/4/HIDDENTAG3/4
- Note: In this example,
“1/4”and“3/4”represent the characters ofASCIIcode188and respectively190. Open XML - UTF-7Encoding: Following the same principles,UTF-7encoding and alternative character representations can be used to hideXMLtags. Encoding is now prohibitedUTF, butOffice 2007is allowed (justInternet Explorerlike ). Here is an example:
<?xml version="1.0" encoding="UTF-7" standalone="yes"?>
+ADw-HIDDENTAG+AD4- malware[...] +ADw-/HIDDENTAG+AD4-
- However,
Open XMLthe specification[OXSPEC]clearly states that only andXMLare allowed in the file . It can be noted that the parser does not allow these obfuscations.UTF-8UTF-16OpenOffice XML - Malformed ZIP archive - Duplicate filenames: In standard
ZIParchives, filenames2are repeated in positions, a central directory at the end of the archive and a header before each file content. The same goes for file size and other information. By modifying just one of the file names, a malformedZIParchive can be created. Many applications do not check these names for consistency, and some only rely on one location or the other. The following is an example of such a malformedZIParchive:
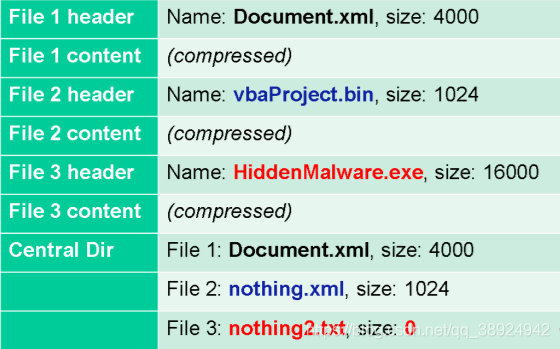
OpenOfficeRely on central directory only. This technique can be used to trick a filter or antivirus software if it only reads the file header.MS Office 2007Check for2consistency between filenames. However, if it detects any issues, it will ask the user if the file should be repaired. Strangely, the file is always fixed so that the macro remains executable regardless of whether the header or center directory has changed! This technique can then be used to bypass any filter/antivirus software that relies on just one of the filenames.- Zip64 Compression:
ZIPThe format has been improved over the past few years to increase the maximum size and compression ratio of archives.Open XMLThe specification explicitly allows the newZip64format; therefore, some filters/antivirus software can be bypassed if they do not handle this format correctly. - Recommendations for powerful filters or antivirus software:
OpenDocumentandOpen XMLanalysis cannot be considered a simple task, even if these are based on the open formats ofZIPandXML. Here are some important facts to check for security analysis:
- 使用强大的 ZIP 库,能够检测格式错误的档案。
- 在 ZIP 存档中,拒绝中央目录和文件头之间的任何不一致。
- 使用不区分大小写的函数来处理 ZIP 存档中的文件名和路径。
- 拒绝库不支持其格式的任何 ZIP 存档,或者规范不允许的任何 ZIP 存档:Zip64,新压缩算法,加密,......
- 始终使用完整而强大的 XML 解析器。 切勿对 XML 文件使用简单的文本搜索或正则表达式。
•Open XML 解析尤其复杂,因为它需要遵循 OPC 原则(Open Packaging Conventions,参见 [OXSPEC]第 2 部分)对 XML 数据进行更深入的分析。
- 检查 XML 文件编码:拒绝规范不允许的任何编码,并使用严格解码模式拒绝任何异常字符。
- 如果可能,请利用具有开放规范的供应商提供的 XML 模式。
- 拒绝文档的内部结构和文件名之间的任何不一致。(例如,Open XML 文档永远不应该命名为 “.doc”)
7 Conclusion
- The new office formats
OpenDocumentandOpen XMLare very promising, and their open specifications are very useful from a security perspective. Active content and hidden data filtering is much easier than before. - However, they still suffer from the same security issues as previous proprietary formats, and there's no real reason to feel any more secure. Some new features of these formats or office suites may even increase security concerns, such as
XMLandZIPobfuscation techniques - As you can guess, it will take some time before all antivirus and content analysis software can safely handle
OpenDocumentand .Open XMLThis article presents some ideas for improving the analysis of these formats.
reference
[ESAT1] An in-depth analysis of virus threats using OpenOffice.org documents, DeDrézigué, Fizaine, Hansma (ESAT), Journal of Computer Virology, 2006http://www.springerlink.com/content/17729904/?k=openoffice
[ESAT2] Le risque virus sous OpenOffice 2.0.x,Filiol,Fizaine (ESAT), MISC magazine n˚27,09/ 2006。
[FSECURE] OpenOffice Security, S. Rautiainen (F-Secure), VB2003 Conference,http//www.fsecure.com/weblog/archives/openoffice_security.pdf
[PACSEC06] OpenOffice/OpenDocument and MS Open XML Security, P. Lagadec, PacSec 2006 Conference,http://pacsec.jp/psj06archive.html
[SSTIC07] Security of OpenDocument and Open XML documents, P。Lagadec,http ://actes.sstic.org/SSTIC07/Securite_OpenDocument_OpenXML/
[ECMA] Ecma International, National Agency Comments on 30 Day Comments on Fast Track Ballot for ISO/IEC DIS 29500 (ECMA-376) “Office Open XML File Format”, Ecma/TC45/2007/006,http://www.ecmainternational.org/news/TC45_current_work/Ecma%20responses.pdf
[SSTIC03] File formats and malicious code,P。Lagadec,SSTIC03,http://actes.sstic.org/SSTIC03/Formats_de_fichiers/
[CVEMSO] Common vulnerabilities and exposures, keyword "Microsoft Office",http://cve.mitre.org/cgibin/cvekey.cgi keyword=microsoft+office
[CVEOOo] Common vulnerabilities and disclosures, keyword "OpenOffice",http://cve.mitre.org/cgi-bin/cvekey.cgi keyword=openoffice
[ESAT3] Analysis of risque virus sous OpenOffice.org 2.0.x, E. Filiol (ESAT), hip conference SSTIC06,http ://actes.sstic.org/SSTIC06/Rump_sessions/SSTIC06-rump-Filiol Risque_viral_sous_OpenOffice.pdf
[OOoURL] OpenOffice.org URL handling security vulnerability (Linux/Solaris),http://www.openoffice.org/security/CVE-2007-0239.html
[XSRF] Cross-site request forgery, Wikipedia,http://en.wikipedia.org/wiki/XSRF
[OSSIR03] Leaking information in proprietary documents,P。Chambet(EdelWeb),Eric Filiol(ESAT),E。Detoisien,OSSIR 6/10/2003,http ://www.ossir.org/windows/supports/2003/2003-10-06/OSSIR Fuite%20infos.pdf
[ODSPEC10] Open Document Format for Office Applications (OpenDocument) v1.0, OASIS Standard, May 1, 2005http://docs.oasisopen.org/office/v1.0/OpenDocument-v1.0-os.pdf
[ODSPEC11] Open Document Format (OpenDocument) v1.1 for Office Applications, OASIS Standard, February 1, 2007http://docs.oasisopen.org/office/v1.1/OpenDocument-v1.1.pdf
[OXSPEC] Office Open XML file format - Standard ECMA-376,http://www.ecma international.org/publications/standards/Ecma376.htm
[OSFP] OOo scripting framework and Python,http://udk.openoffice.org/python/scriptingframework/index.html
[OOoPy] OOoPy, a Python module for editing OpenDocument,http://ooopy.sourceforge.net
[MS06-065] Secunia MS06-065 Consulting,http://secunia.com/advisories/20717
[XPS] Microsoft XML Paper Specification - XPS,http://www.microsoft.com/whdc/xps/default.mspx
[IEASCII] http://www.securityfocus.com/archive/1/437948