Reprint: How to protect the code in the ios ipa file of the Apple mobile application?
Table of contents
Reprint: How to protect the code in the ios ipa file of the Apple mobile application?
1. Select the ipa file to be obfuscated and protected
2. Select the class name to obfuscate
3. Select the function to be obfuscated and protected by
4. Configure signing certificate
5. Obfuscation and test running

Edit
In today's highly competitive environment of the mobile app market, code protection features are critical to the success of iOS apps. Code protection helps developers protect against risks such as theft, reverse engineering, and unauthorized access. By protecting the code of your iOS IPA files, you can ensure that your intellectual property rights are fully respected and avoid property damage and business competition. Here are a few common ways to protect iOS IPA file code:
-
Use code obfuscation techniques: Code obfuscation is a technique that converts source code into an incomprehensible form, making reverse engineering difficult. By using code obfuscation tools, you can obfuscate your iOS app code, making it more difficult to crack and reverse analyze.
-
Implement encryption: Encryption is an important means of protecting code security. You can encrypt critical code, sensitive data, and algorithms to ensure that only authorized users can decrypt and access them.
-
Introducing runtime protection mechanisms: Runtime protection technology can detect and prevent attacks such as malicious code injection, dynamic debugging, and memory corruption during application execution. By using runtime protection mechanisms, you can increase the security of your application and prevent hackers from tampering with and attacking the code.
-
Update and fix vulnerabilities in a timely manner: It is very important to update and fix vulnerabilities in the application in a timely manner. Continue to pay attention to the latest security vulnerabilities and fixes, and promptly repair and upgrade applications to improve application security.
Whether it is encryption or a runtime virtual machine, the original code can be reversely generated through execution debugging. Although it can resist low-end hacker attacks, it is useless against high-end hackers. Code obfuscation makes the code difficult to understand and decompile by modifying the source code structure and variable names. This allows a hacker to obtain the code of the application and make it difficult to understand it. Whether he is a high-end or low-end hacker, there is currently no effective way to restore it to the original code, and it is recognized as one of the most effective methods. The following uses ipaguard as an example to introduce how to comprehensively modify and obfuscate the classes, methods, method parameters, variables, etc. in the ipa file, so that their names become meaningless garbled characters, which greatly increases the difficulty of application cracking. The ipaguard code obfuscation tool supports apps developed on various development platforms such as OC, Swift, Flutter, H5, HBuilder, Unity3D, Cocos2dx, etc.
Code obfuscation steps
1. Select the ipa file to be obfuscated and protected

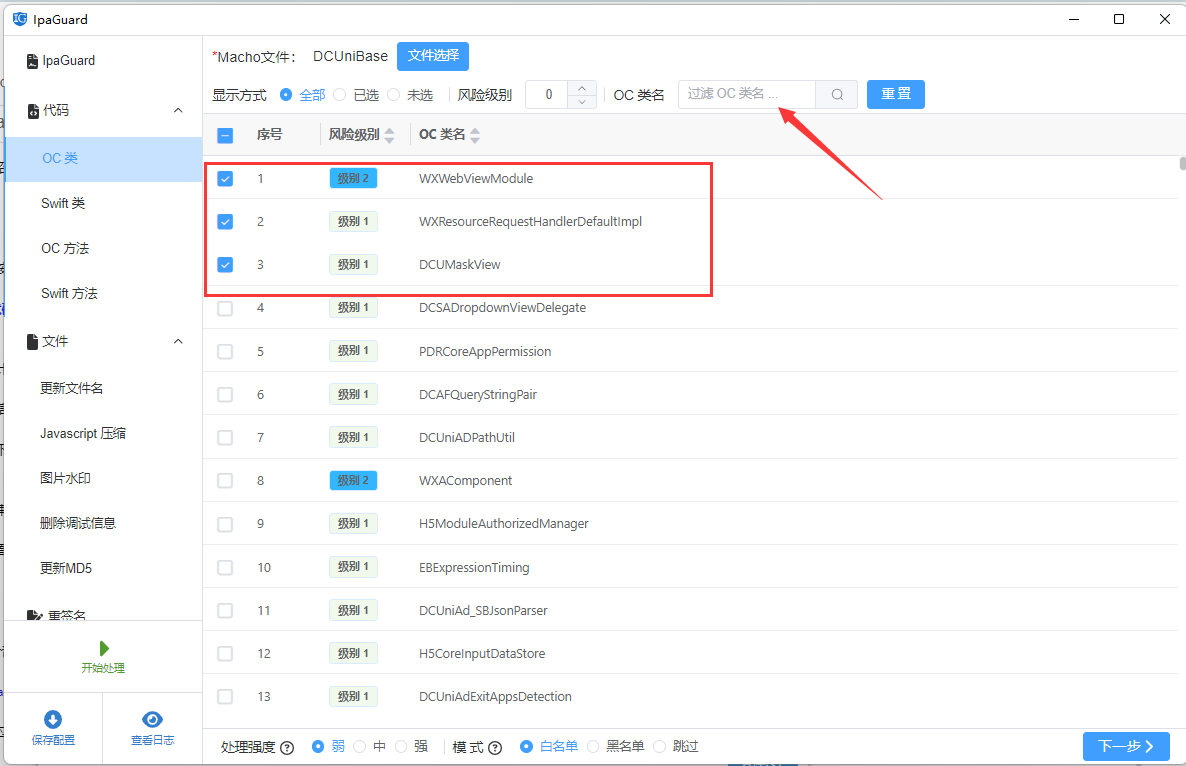
2. Select the class name to obfuscate
Select the OC class name or Swift class name in the code module on the left, select the IPA binary file to be obfuscated, and then check the class name in the executable file code. If there are too many classes, you can use the search and view function. ipaguard provides level selection, name search, and selected and unselected filtering to help configure obfuscated objects.
3. Select the function to be obfuscated and protected by
Select the oc method or swift method under the code module on the left, click Select File on the right to select an executable binary file, and check the methods and functions that need obfuscation protection. ipaguard provides risk level filtering, name search filtering, and assists in configuring obfuscation targets based on class name filtering conditions.

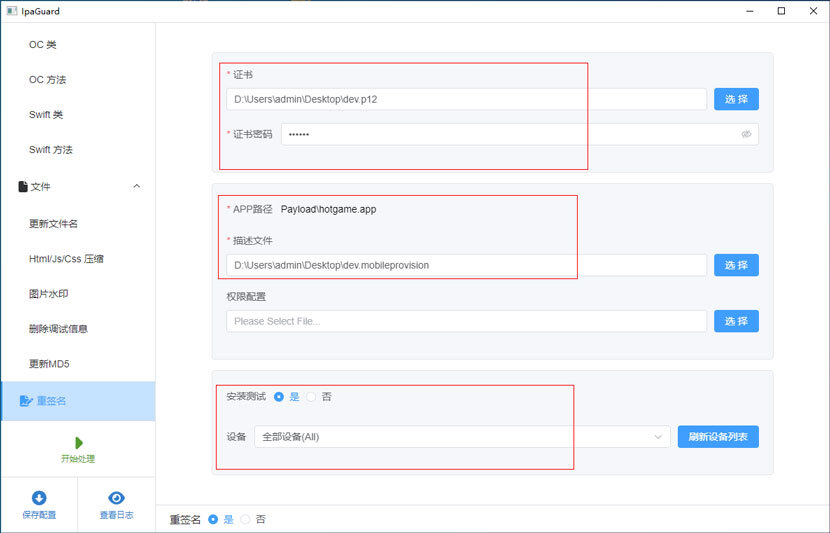
4. Configure signing certificate
Click Signature Configuration on the left to set the ios signature certificate, description file and other information. The development certificate is used during the testing phase, so that it can be easily installed on the test machine to check whether the tested app runs normally; the final configuration test is ok, and it will be changed to a publishing certificate when publishing. After the obfuscation configuration is completed, it can be submitted for release.
5. Obfuscation and test running
Click the Start Processing button, ipaguard will obfuscate the content selected in the ipa, and install the obfuscated ipa on the mobile phone. If it runs ok, click to save the configuration. You can directly load the configuration next time. There is no need to configure obfuscation every time. content.
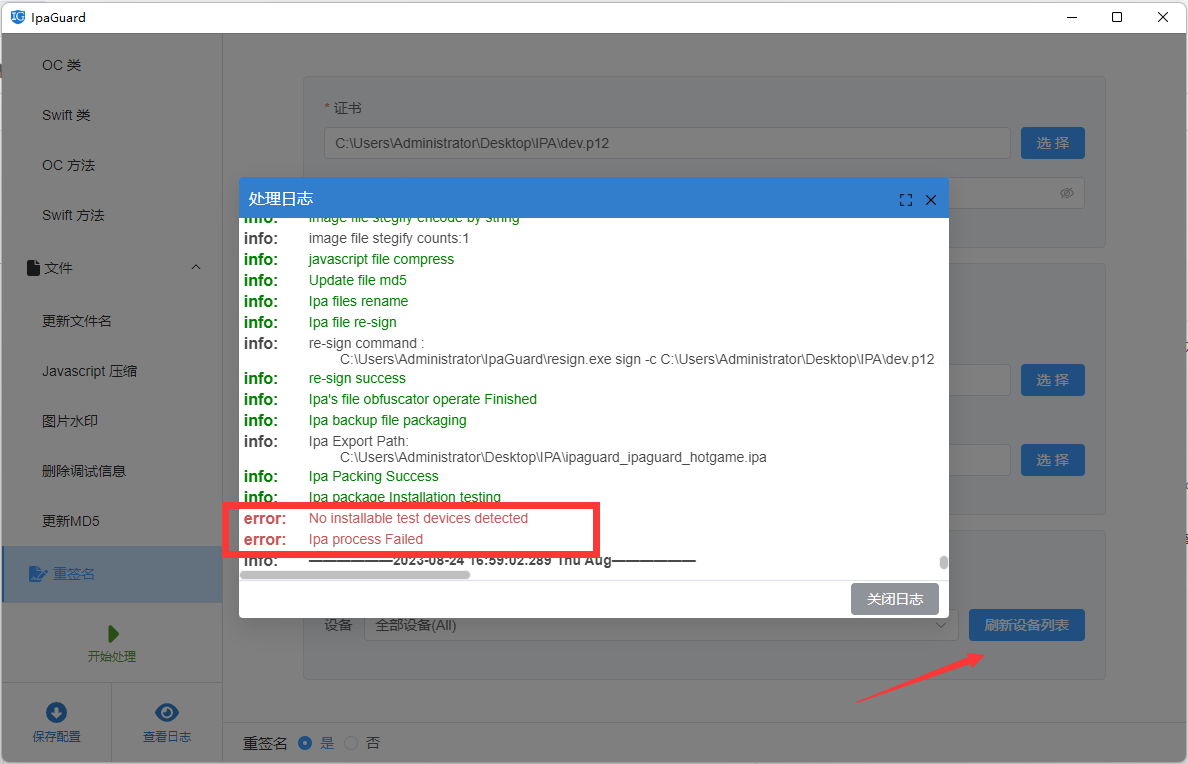
ipaguard is very user-friendly when it comes to obfuscation. The obfuscation target and intensity are controllable, which greatly simplifies the process of configuring obfuscation content, and the visual operation is also very convenient.