Reverse engineering is the process of analyzing and restoring an application, revealing its inner workings and code structure. Next, we will give a comprehensive introduction to reverse engineering on iOS, including its concepts, common tools and specific examples.
1. What is iOS reverse engineering?
iOS platform reverse engineering is the process of restoring an application's binary code (usually compiled) to source code, thereby revealing the inner workings of the application. Reverse engineers can gain insights into an application's design and functionality by analyzing its code, data structures, and algorithms. This helps developers learn new technologies and optimize code; for security researchers, it helps discover potential vulnerabilities and security risks.
2. Basic process of iOS reverse engineering
A basic process of iOS reverse engineering is as follows:
(1) Obtain the application binary file: First, you need to obtain the application binary file (usually an ipa file) from the target device or the App Store.
(2) Parse binary files: Use tools such as Hopper Disassembler, IDA Pro, etc. to convert binary files into readable assembly code for analysis.
(3) Analyze the code structure: Read the assembly code and understand the logic, classes and methods of the application. This step requires the reverse engineer to have some understanding of assembly and Objective-C.
(4) Identify key functions: Find the functions that handle key logic in the application, such as verification, encryption, network communication, etc.
Dynamic debugging: Use dynamic analysis tools (such as Cycript, LLDB, etc.) to observe and modify the execution process of the code while the application is running.
(5) Modify the code: According to specific needs, change the behavior of the application by modifying the assembly code, method calling parameters, etc.
(6) Compilation and testing: Recompile the modified code, generate a new executable file, and verify the modification effect in the test environment.
3. Tools required for reverse engineering
Reverse engineering of the iOS platform involves a series of tools used to analyze and modify applications. Here are some common tools:
Hopper Disassembler: This is a powerful disassembly tool that converts an application's binary code into assembly code. It enables reverse engineers to understand the execution flow and underlying logic of a program.
IDA Pro: Similar to Hopper, IDA Pro is also a widely used static disassembly tool. It provides in-depth code analysis capabilities, including advanced code navigation and cross-reference analysis.
Cycript: This is a powerful dynamic analysis tool that allows developers to interact with applications while they are running. Using Cycript, you can modify variables, call functions, and dynamically view your application's view hierarchy in real time.
class-dump: This is a tool for extracting Objective-C class definitions to help reverse engineers understand the classes and methods used in the application.
4. What can reverse engineering do?
As the saying goes, if you know yourself and the enemy, you will be victorious in any battle. Research on iOS development and learning reverse engineering is of great value for in-depth understanding of the internal mechanisms of applications, improving technical capabilities, discovering security vulnerabilities, innovating customization, strengthening security defense and other fields. Through reverse engineering, we can explore the algorithms, logic and design hidden behind the binary code to learn new technologies, improve security, and even develop plug-ins and extend application functions. In addition, reverse engineering can help understand attack patterns, design countermeasures, and have applications in education and academic research.
Example 1: WeChat red envelope grabbing plug-in
The WeChat red envelope grabbing plug-in is a popular iOS application extension that can automatically detect and snatch red envelopes in WeChat chats. This is a typical reverse engineering example because it requires analyzing the communication protocol and red envelope logic of the WeChat application.
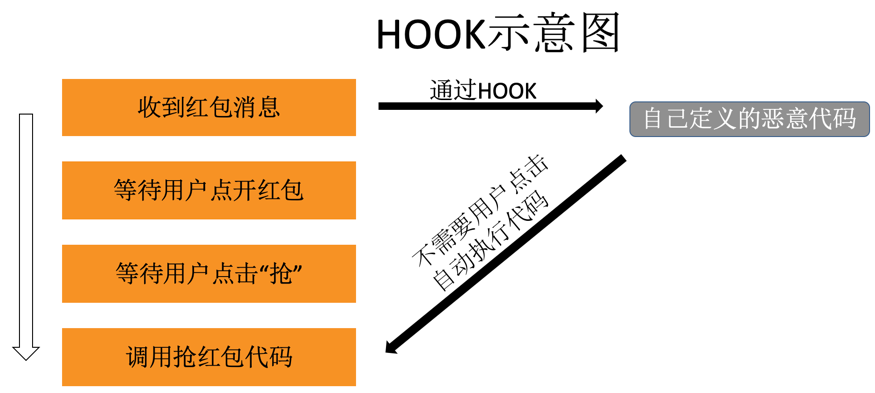
Implementing such a plug-in requires the use of tools for dynamic analysis, such as monitoring the WeChat process through Cycript and finding the function that processes red envelopes. Here is a simplified example code:
Class targetClass = NSClassFromString(@"MessageViewController");
Method originalMethod = class_getInstanceMethod(targetClass, @selector(onReceiveRedPacket:));
IMP newImplementation = imp_implementationWithBlock(^void(id _self, id redPacket) {
// 修改红包逻辑,自动领取红包
[self performRedPacketHack:redPacket];
// 调用原始方法
((void (*)(id, SEL, id))originalMethod)(_self, @selector(onReceiveRedPacket:), redPacket);
});
// 将新方法替换原始方法
method_setImplementation(originalMethod, newImplementation);Example 2: Simulated positioning of Pokemon Go
Simulated positioning is a common reverse behavior in games like Pokemon Go, allowing players to move around in the real world to acquire virtual items in the game. This requires modifying the app's location data in order to trick the game server.
To achieve simulated positioning, reverse engineers can use tools like IDA Pro to analyze the positioning-related parts of the game code, and then modify the positioning verification logic.
5. Summary
iOS reversing is a fascinating and challenging field that allows you to delve deeply into the inner workings of an application. Through reverse engineering tools, developers can better understand how applications work, providing inspiration for code optimization and innovation. Learning iOS reverse engineering reveals the deeper mysteries behind application development. It also prompts us to think about the underlying implementation of the system and improve the technical depth.