Recently, Fortinet® (NASDAQ: FTNT), a global network security leader focused on promoting the integration of networks and security, released the "Global Threat Situation Research Report for the First Half of 2023". The report shows that in the first half of 2023, the number of ransomware detections continued to decline, the activity of advanced persistent threat (APT) groups increased significantly, and the MITER ATT&CK technology used by attackers showed rapid changes and other threat development trends.
Organizations continue to be on the defensive due to the increasing sophistication of tactics and techniques used by malicious actors and the escalation of targeted attacks. The "Global Threat Situation Research Report for the First Half of 2023" continuously tracks and analyzes the threat situation, helps to provide high-value intelligence, and serves as an early warning system for potential threat activities, helping security managers formulate more informed security strategies and clarify Bug fix priority.
Here are the four key findings of this report:
Key findings 1. The number of variants and the number of detections are at odds with each other.
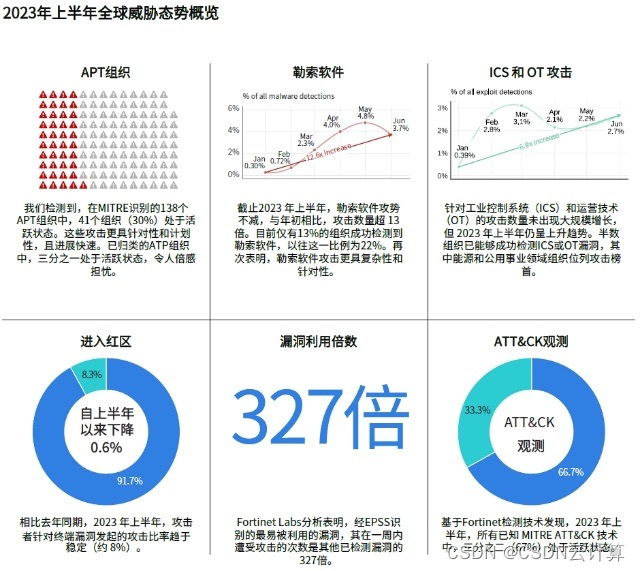
Reports show that the number of ransomware variants has surged significantly in recent years, a trend largely driven by the rise of the ransomware-as-a-service (RaaS) model. However, bucking this trend is that only 13% of organizations successfully detected ransomware in the first half of 2023, compared with 22% five years ago.
Fortinet FortiGuard Global Threat Research and Response Labs (FortiGuard Labs) summarized the threat development trends in the past few years and found that this trend in the number of variants and detection volume is due to the tactics and techniques used by attackers. Ransomware and other attacks are becoming more targeted due to increasing sophistication and a strong intent to increase return on investment (ROI) per attack. In other words, ransomware attacks have become "easy not to take action, but to do it when everything is ready and determined to win."
Key findings 2. The threat of high-scoring vulnerabilities increases sharply during the 7-day danger period
In this report, FortiGuard Labs analyzed nearly six years of historical vulnerability exploitation data, which involved more than 11,000 publicly disclosed CVE vulnerabilities. The analysis found that Common Vulnerabilities and Exposures (CVE) with the highest score (top 1% high-risk vulnerabilities) in the Predictive Exploit Scoring System (EPSS) were 327 times more likely to be exploited within 7 days than other vulnerabilities.
Key Finding 3: Red Zones Combined with Effective Patch Management Strategies
FortiGuard Labs defines red zones based on analysis results of vulnerabilities exploited in the wild in EPSS scores, helping chief information security officers prioritize vulnerability remediation while quantifying the proportion of exploitable vulnerabilities on endpoints that are subject to active attacks. The report shows that the number of discovered, existing and exploited vulnerabilities continues to fluctuate, and organizations implementing effective patch management strategies guided by remediation priorities have significantly reduced the red zone area.
Key findings 4. Nearly one-third of APT organizations are active
In this report, FortiGuard Labs tracks the number of threat actors behind the current trend for the first time. Research shows that in the first half of 2023, 41 (30%) of the 138 cyber threat groups tracked by MITER were active. Based on the malware detection results, organizations such as Turla, StrongPity, Winnti, OceanLotus and WildNeutron are currently the most active hacker groups. The evolution and number of activities of APT organizations will become the focus of future reports.
All-round joint efforts to combat cybercrime
As a leader in enterprise-level network security and network innovation solutions, Fortinet continues to protect various enterprises, service providers and government organizations around the world, with a user base of more than 500,000. It is worth mentioning that Fortinet continues to develop artificial intelligence (AI) technology for network security use cases and incorporates it into FortiGuard Labs laboratories and various product portfolios. This innovative move can effectively accelerate the detection of known and unknown threats. prevention, detection and response.
FortiGuard AI-powered security services leverage security control components deployed across endpoints and applications across network and cloud infrastructure. Dedicated detection and response technologies based on AI engines and cloud analytics (including EDR, NDR, etc.) can also be deployed as integrated extensions of such control components. In addition, Fortinet also provides centralized response tools such as XDR, SIEM, SOAR, DRPS, etc., leveraging different AI technologies, automation and orchestration capabilities to accelerate threat remediation, thereby significantly defeating cybercriminal activities across the entire attack surface and network attack kill chain.