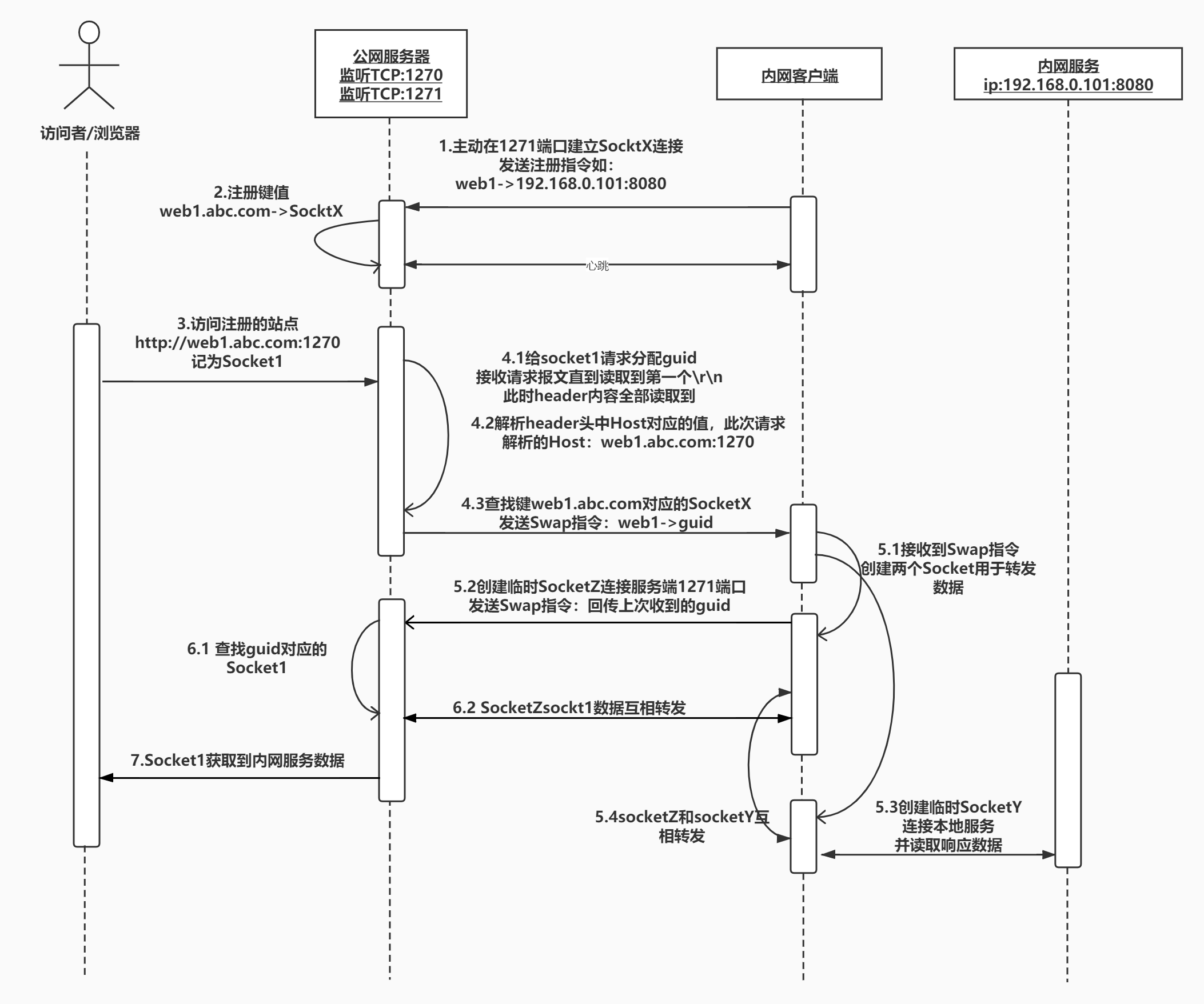
Intranet penetration, that is, NAT (Network Address Translation) penetration
The essence of intranet penetration is the realization of intranet mapping and conversion of intranet addresses to external addresses. The implementation process requires end-to-end data transmission and the principle of port forwarding. The intranet mapping method can solve the problem of no public network IP and a general solution for accessing the internal network from the external network.
The purpose of achieving intranet penetration is to ensure that data packets with a specific source IP address and source port number are not shielded by the NAT device and correctly routed to the intranet host (because the NAT device automatically shields the connection initiated by the non-intranet host, Thereby protecting the attack of the external network but also bringing difficulties for P2P communication).
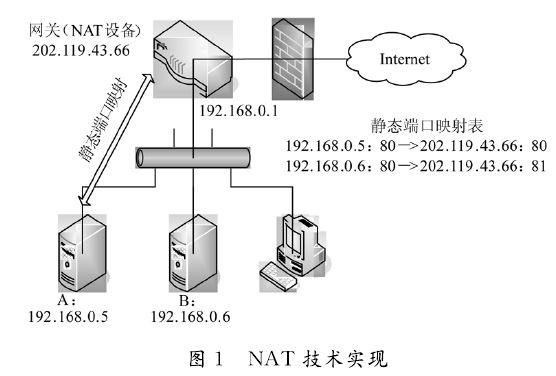
The principle of intranet penetration : NAT equipment (or software) maintains a state table, which is used to map the private IP address of the internal network to the legal IP address of the external network. The IP address and port information in each packet header are modified and translated into a correct IP address in the NAT device (or software) and sent to the next level. When an internal network host opens an "outgoing" TCP or UDP session through NAT, NAPT assigns this session a public network IP and port to receive the response data packet from the external network, and notify the internal network host after conversion . In this way, NAPT establishes a port binding between [private IP: private port] and [public IP: public port]
Intranet penetration projects or tools
no installation required
- GitHub - LiangXiaoWei1024/net-penetrate-http-and-https-simple: Intranet penetration, GUI, one-key startup, unlimited speed, built-in log : (2022) There seems to be a problem with the POST request
- i996 Intranet Penetration/Certificate Issuance : Open source, free, and build-free intranet penetration service for all platforms, no need to install any programs
- https://serveo.net/ : Serveo is a free intranet penetration service. Serveo can expose local computers to the Internet. It is officially called an excellent alternative to Ngrok
- ngrok - Online in One Line : ngrok is a reverse proxy. By establishing a secure channel between the public endpoint and the locally running Web server, the services of the internal network host can be exposed to the external network. ngrok can capture and analyze traffic on all channels for later analysis and replay
- Tunnel FastTunnel|Free Intranet Penetration|Home Building Station|NAT Penetration|Peanut Shell|FRP|ngrok : based on FastTunnel
Requires installation (admin privileges)
- cpolar - Safe intranet penetration tool : cpolar intranet port mapping, to register, you can use the free plan
-
smartGate, no public network IP required, open source : smarGate "mobile gateway" exposes the server network located in the intranet on demand through the mobile client, and all shared access entrances are on the client, which is not oriented like other penetrating tools. Domain name's public access portal
Penetration tool (you need to configure the server and client yourself)
- frp: A high-performance reverse proxy application focused on intranet penetration, which can expose intranet services to the public network in a safe and convenient manner through transit with public IP nodes

- GitHub - FastTunnel/FastTunnel: expose a local server to the internet. High-performance cross-platform intranet penetration solution Remote intranet computer domain name access intranet site reverse proxy Intranet service port forwarding http proxy: FastTunnel high-performance cross- platform Intranet penetration tool, which can expose intranet services to the public network for anyone to access