Article directory
- [Chapter 1 - Macro Knowledge]
- [Chapter Two - Linux Basic Commands]
-
-
- 1. Linux directory structure
- 2. What is a command, command line
- 3. General format of Linux commands
- 4. Root directory, Home directory
- 5. Command: ls - list folder information
- 6. Command: cd - switch working directory
- 7. Command: pwm - show current working directory
- 8. Relative path and absolute path
- 9. Special path characters: . .. ~ /
- 10. Command: mkdir -p - create folder
- 11. Command: touch - create file
- 12. Command: cat - view file content
- 13. Command: more - view file content
- 14. Command: cp -r - copy file folder
- 15. Command: mv - move file folder
- 16. Command: rm -r - delete file folder
- 17. Wildcard * - stands for everything
- 18. What is the Linux command
- 18. Command: which - check the command body
- 19. Command: find - search for files
- 20. Command: grep - filter
- 21. Command: wc - Statistics
- 22. Pipe character |
- 22. Reaction number ``
- 22. Redirection characters >, >>
- 23. Command: echo
- 23. Command: tail - trace file
- 24. vi, vim editor
-
- [Chapter Three - Linux Rights Management]
- [Chapter 4 - Practical Operation of Linux]
-
-
- 1. Shortcut keys
- 2. Software installation yum, apt
- 3. Command: systemctl - software control
- 4. Command: ln - create a soft connection
- 5. Date, time zone
- 6. Special IP address
- 7. Host name
- 8. Domain name resolution
- 9. Set a fixed IP for the virtual machine
- 10. Command: ping - test whether the network is connected
- 11. Command: wget -download
- 12. Command: curl - download
- 13. What is the port
- 14. Command: nmap - view port occupancy
- 15. What is the process
- 16. Command: ps - view process
- 17. Command: kill - close the process
- 18. Command: top - View system resource usage
- 19. Command: df - disk information monitoring
- 20. $ symbol - value
- 21. What is an environment variable
- 22. Custom environment variables
- 23. What is PATH
- 24. Customize the environment variable PATH
- 25. Command: rz, sz - shell software upload and download
- 26. Compression format
- 27. Command: tar
- 28. Command: zip
-
- [Chapter Five - Various Software Deployment]
- [Chapter 6 - Scripting and Automation]
- [Chapter Seven - Project Combat]
- 【Chapter Eight - Cloud Platform Technology】
Note content source: linux quick start video for dark horse programmers on beep station, highly recommended.
"No more words, no less words, use the shortest time to teach more practical techniques" ——Dark Horse Programmer
Notes are for sorting out, memorizing, consulting
The purpose of drawing pictures is to facilitate memory, so there is no need to waste too much time.
[Chapter 1 - Macro Knowledge]
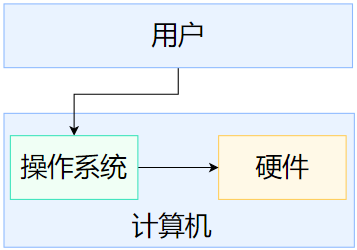
1. The relationship between hardware and software
Hardware: Physical devices such as CPU, memory, and hard disk.
Software: It is the bridge between the user and the hardware, and the user communicates with the computer system through the software. An operating system is a type of software.
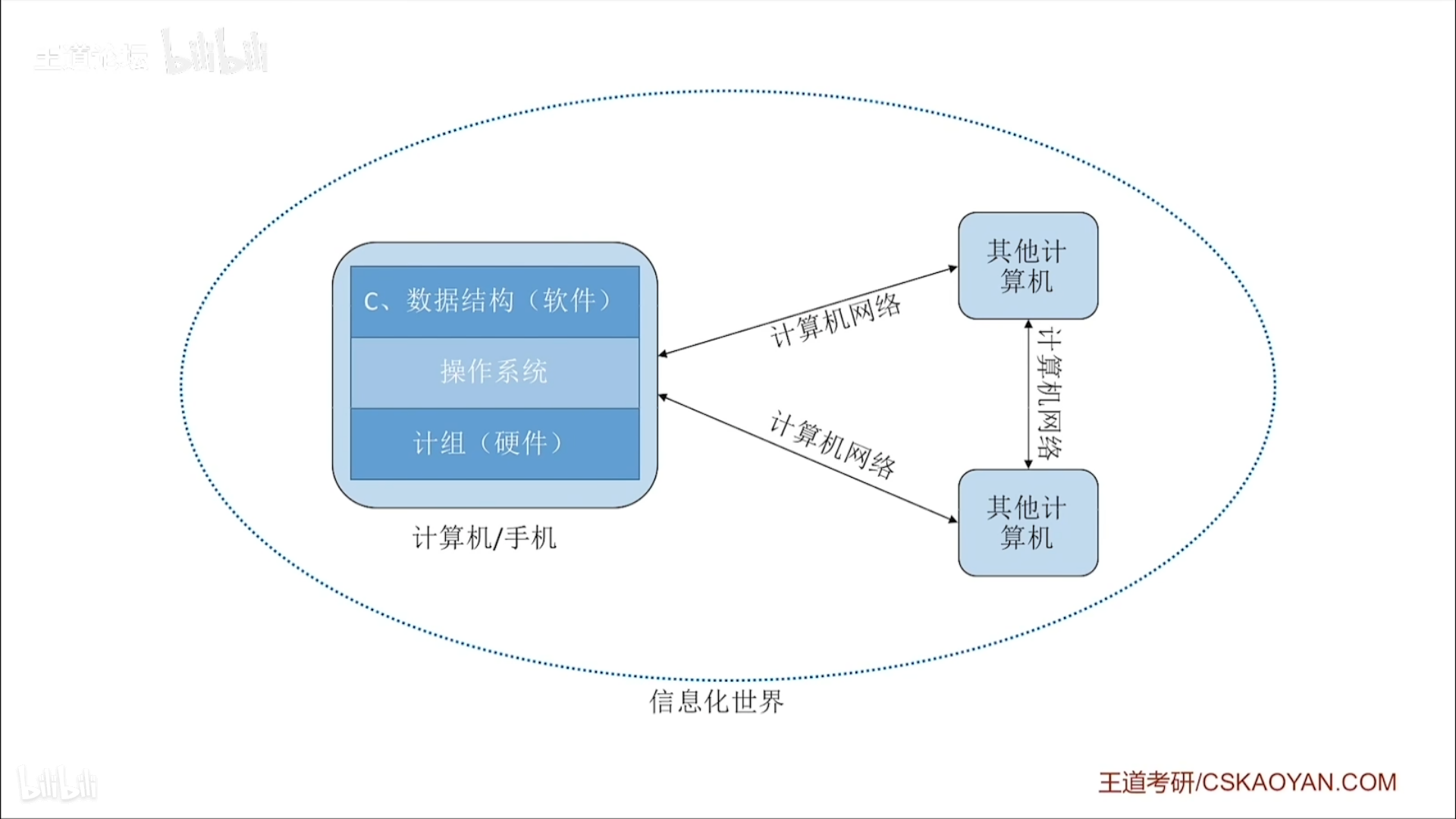
Four-piece set of computer courses:
-
Principles of computer composition (hardware)
-
Operating system (software, middle layer)
-
Data structures (software, application layer)
-
Computer Networks (Network Communications)
2. What is the operating system and what is its function
Operating system: is a type of software.
Role: It acts as a bridge between users and hardware. The user uses the operating system, and the operating system arranges the hardware to work.
3. Common operating systems
PC端:Windows、Linux、MacOS
Mobile terminal: Android, IOS, Hongmeng
4. Birth of Linux
Linus Benadict Torvalds in 1991.
Coincidentally, python's first interpreter was also born in 1991.
5. What is the Linux kernel
The Linux system consists of two parts:
- Linux kernel
- system application
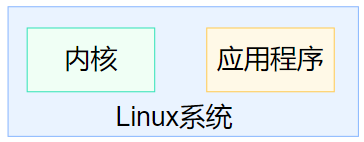
Kernel: Provides the most core functions of the system, such as: scheduling CPU, scheduling memory, scheduling file system, scheduling network communication, scheduling IO and other hardware scheduling management capabilities.
System application program: call the relevant functions provided by the kernel, and then the kernel schedules the hardware work.
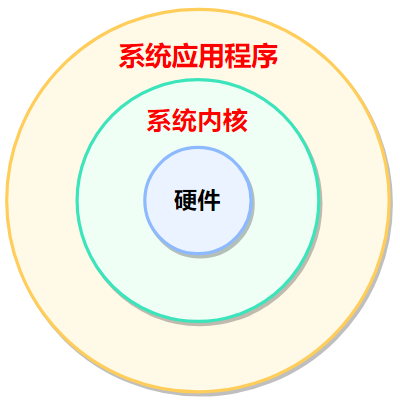
The kernel is the core of the Linux operating system, and system applications are just the icing on the cake.
Linux kernel official website: The Linux Kernel Archives
6. What is a Linux distribution
The kernel cannot be used directly by the user, and needs to cooperate with the application program to be used by the user.
A Linux distribution refers to a Linux system that can be used normally by users.
It provides a complete package of kernel + system-level programs, which is called a Linux distribution.
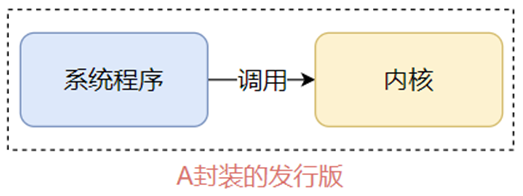
The common Linux distributions currently on the market are:

7. What is WSL
WSL: Windows Subsystem for Linux, is a Linux subsystem for Windows systems.
The function is very simple, you can get the Linux system environment in the Windows system, and completely directly connect the computer hardware without virtual hardware through the virtual machine.
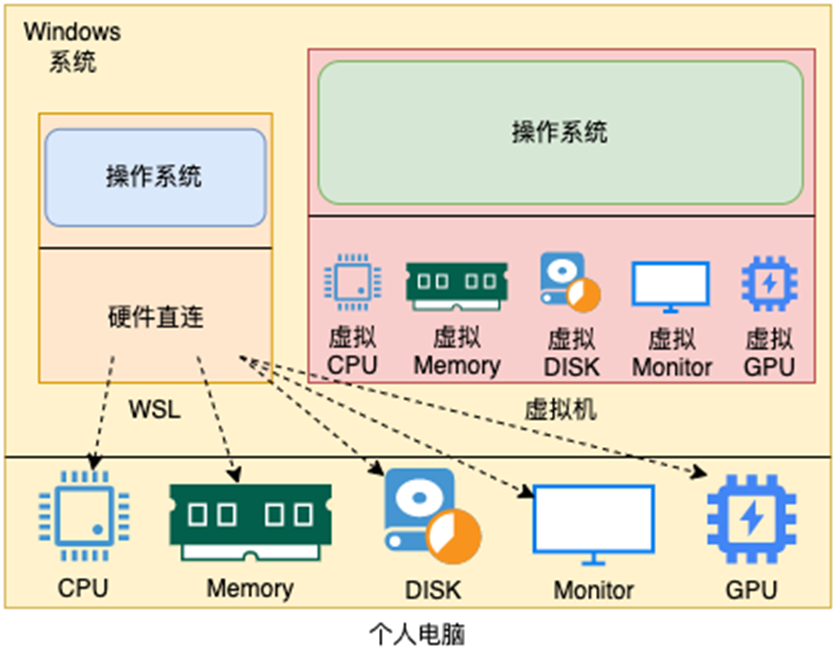
8. Virtual machine snapshot
Archive functionality provided by VMware.
9. FinalShell (Xshell alternative)
Official Website: SSH Tools SSH Client (hostbuf.com)
[Chapter Two - Linux Basic Commands]
1. Linux directory structure
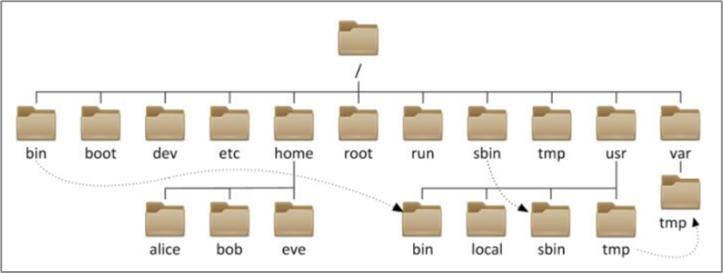
Linux has no concept of a drive letter, only one root directory /, and all files are under it.
In the Linux system, the hierarchical relationship between paths is represented by: /
In the Windows system, the hierarchical relationship between paths is represented by: \
The / symbol means in the linux system:
-
The / that appears at the beginning means: the root directory
-
The / that appears in the back indicates: hierarchical relationship
2. What is a command, command line
-
Command: It is a Linux operation instruction, which is a built-in program of the system.
Ontologies are binary executable programs one by one, which means the same as .exe in windows.
You can check the specific location through which. For example which cd.
-
Command line: that is, Linux interrupt, providing a command execution page.
3. General format of Linux commands
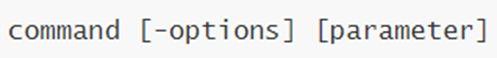
- the command itself
- optional options
- optional parameters
4. Root directory, Home directory
- Root directory: /
- Home directory: the exclusive directory of each user in the Linux system
- The default home directory of ordinary users is: /home/username
- The Home directory of the root user defaults to: /root
5. Command: ls - list folder information
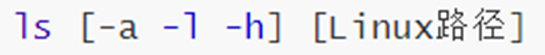
-
-a list all content
In the Linux system, files/folders starting with "." will be automatically hidden
Only through the -a option can it be displayed
-
-l display in list
-
-h more human readable size
6. Command: cd - switch working directory
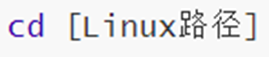
- The cd command has no options, only parameters.
- When no parameter is used, it defaults to the home directory.
7. Command: pwm - show current working directory
- Output the current working directory
8. Relative path and absolute path
-
Absolute path: starting from the root directory, a way to describe the path, the path description starts with /
-
Relative path: Starting from the current directory, a way to describe the path, the path description does not need to start with /
9. Special path characters: . … ~ /
- . represents the current directory
- … indicates the upper level directory
- ~ represents the Home directory
10. Command: mkdir -p - create folder
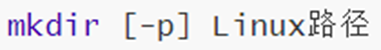
- Options: -p, create multi-level directories.
- Parameters: path, required. Relative paths, absolute paths, and special path symbols are available.
Remember one: mkdir -p path
Differentiate between files and folders
The operation instructions of files and folders in Linux are often different.
for example:
Create: the file is the touch command, the folder is the mkdir command
The copy command cp, delete command rm, and the option -r must be added when dealing with folders. Add -R to the permission modification command chmod for the file.
11. Command: touch - create file
[External link picture transfer failed, the source site may have an anti-leeching mechanism, it is recommended to save the picture and upload it directly (img-ihiyboNM-1673421351451)(null)]
-
Create a file. It's not a folder.
-
No options.
-
Parameters: path, required.
12. Command: cat - view file content
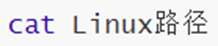
-
View file contents.
-
No options.
-
Parameters: path, required.
13. Command: more - view file content
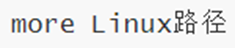
-
View file contents.
-
more supports page turning, if the content of the file is too much, it can be displayed page by page.
-
Space to turn the page, q to exit.
14. Command: cp -r - copy file folder
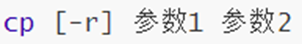
- Options: -r, copy the entire folder.
- Parameter 1: path, indicating the source file.
- Parameter 2: path, indicating the target location.
Remember one: cp -r xxx xxx
15. Command: mv - move file folder
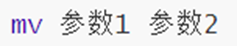
- No options.
- Parameter 1: path, indicating the source file or folder
- Parameter 2: path, indicating the target location. If the target does not exist, rename it to ensure that the target exists.
16. Command: rm -r - delete file folder

- Option: -r, delete the entire folder
- Option: -f, force delete (required only for root users)
- Parameter N: target folder, multiple. space separated
The rm command is dangerous, so be careful, especially when switching to the root user.
Do not execute it under the root user: rm -rf / will clear everything and crash directly.
Can be used with wildcards
17. Wildcard * - stands for everything
-
The symbol * represents a wildcard, that is, matches any content (including empty), for example:
test*, means match any content that starts with test
*test, means match any content that ends with test
test , which means match any content containing test
18. What is the Linux command
- The linux commands we use, their bodies are binary executable programs one by one.
- It has the same meaning as the .exe file in the Windows system.
- You can use the which command to view where the program files of the series of commands used are stored
18. Command: which - check the command body
- View where the program files for the series of commands used are stored
19. Command: find - search for files

-
Find files and folders by filename.
Can be used with wildcards
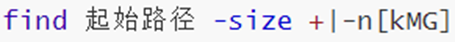
-
Find files and folders by size.
-
+, - means greater than and less than
n means big and small numbers
kMG means size unit, k (lowercase letter) means kb, M means MB, G means GB
20. Command: grep - filter
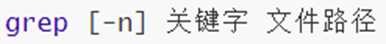
-
Filter content by keywords.
-
Options: -n, display line numbers in the result.
-
Parameters: keywords, which represent filtered keywords (surrounded by "")
-
Parameters: file path, indicating the target file, which can be used as a content input port
21. Command: wc - Statistics
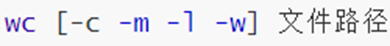
-
Option, -c, count the number of bytes
option, -m, count the number of characters
option, -l, count the number of lines
option, -w, count the number of words
Parameters, file paths, and files to be counted can be used as content input ports
22. Pipe character |
-
The meaning of the pipe symbol is: use the result of the command on the left of the pipe symbol as the input of the command on the right
-
There are many applications.
ls | grep Desktop, filter the results of ls
find / -name "test" | grep "/usr/lib64", filter the results, only find the results with /usr/lib64 in the path
22. Reaction number ``
- The content surrounded by ` will be executed as a command instead of ordinary characters
22. Redirection characters >, >>
-
• >, overwrite the result of the command on the left to the file specified on the right of the symbol
• >>, append the result of the command on the left to the file specified on the right of the symbol
23. Command: echo

-
No options, only one parameter, indicating the content to be output, complex content can be surrounded by ""
-
With backticks, commands can be used. echo pwd
-
Used with redirectors, content can be written to the file. • echo “Hello Linux” > itheima.txt
23. Command: tail - trace file
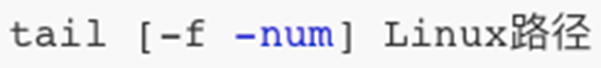
-
View the contents of the tail of the file and track the latest changes to the file
-
Parameter, Linux path, indicates the tracked file path
Option, -f, means keep track
Option, -num, means, how many lines to check at the end, if not filled, the default is 10 lines
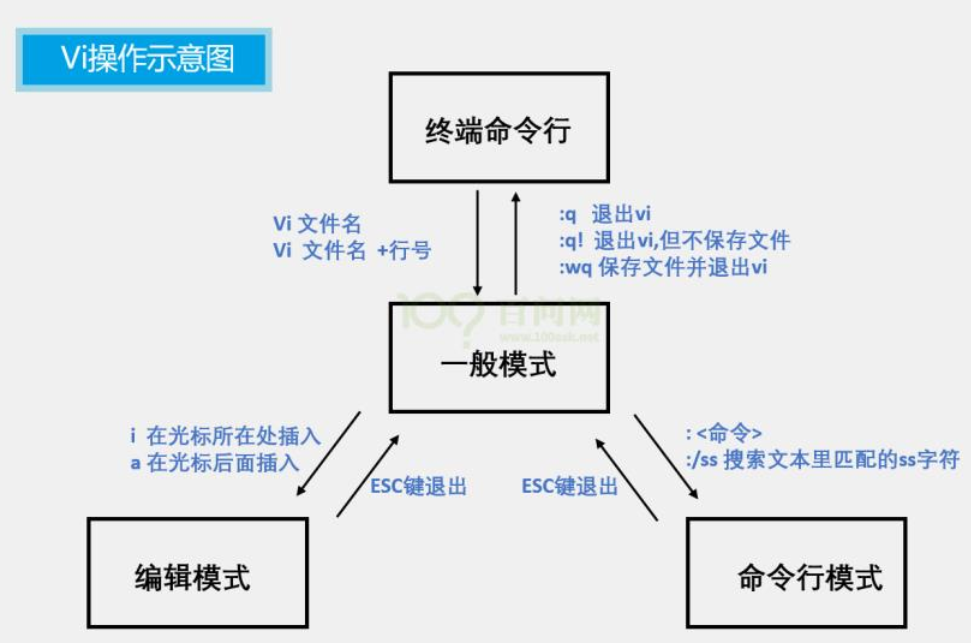
24. vi, vim editor
- vi\vim is the abbreviation of visual interface, the most classic text editor in Linux
- Like the text editor in the graphical interface, vi is an excellent choice for editing text files on the command line.
- vim is an enhanced version of vi. It is compatible with all commands of vi. It can not only edit text, but also has the function of editing shell programs. It can distinguish the correctness of grammar with fonts of different colors, which greatly facilitates the design and editing of programs.
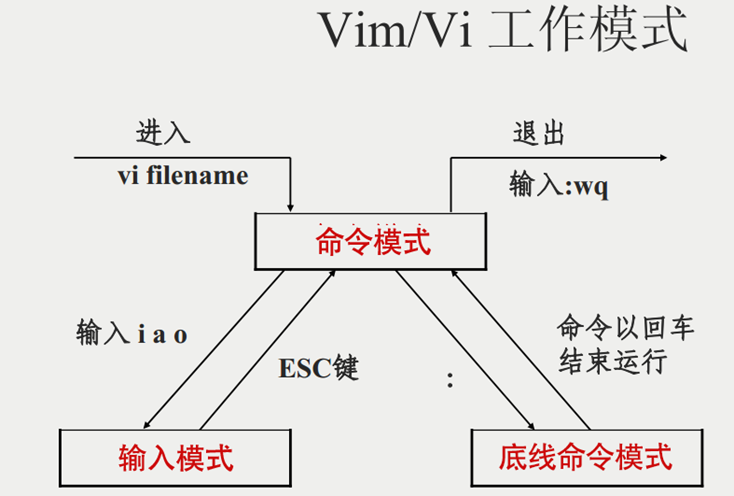
-
Command mode: In command mode, the editor understands all keystrokes as commands, and uses commands to drive and execute different functions. Under this model, free text editing is not possible.
-
Input mode: In this mode, the content of the file can be edited freely.
-
Bottom line command mode: for saving and exiting files.
-
If you need to edit the file through the vi/vim editor, please use the following command:
vi file path
vim file path
can be used to create files. If the file indicated by the file path does not exist, then this command will be used to edit the new file.
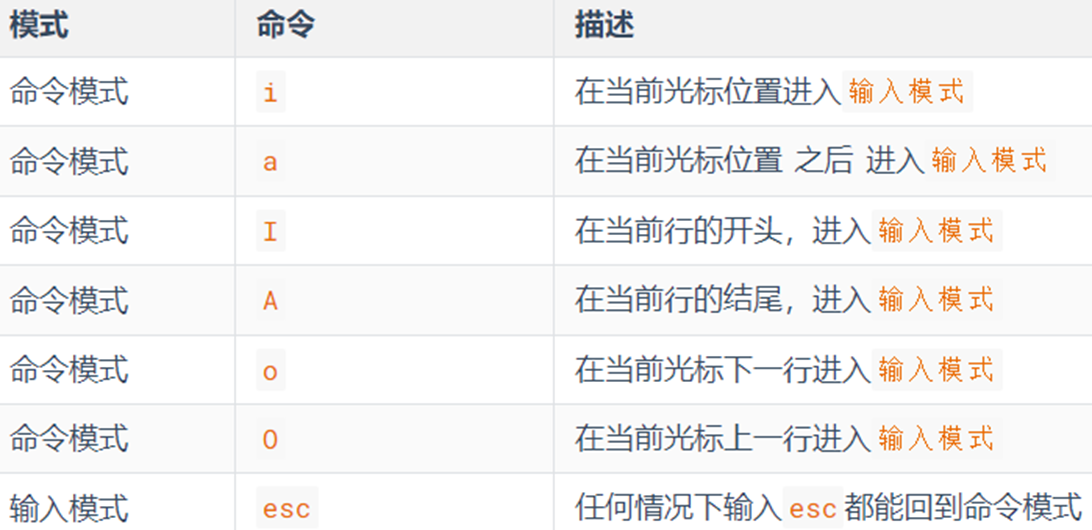
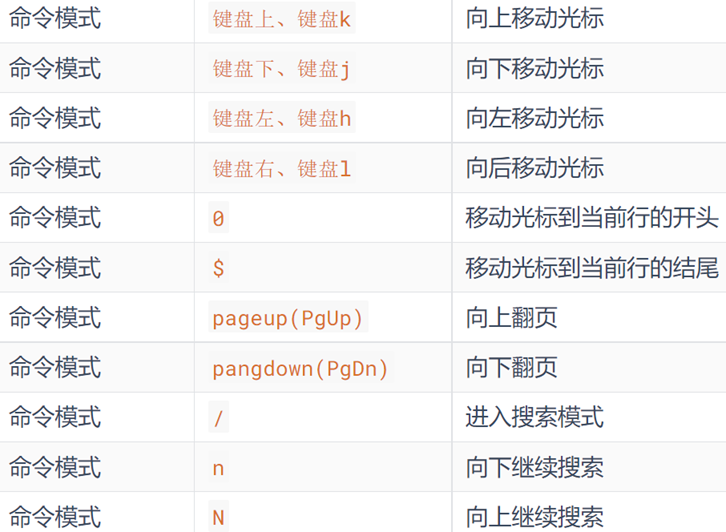
-
command mode shortcut
Regular use: io
Commonly used: / search, dd delete line, yy copy line, p paste, u undo
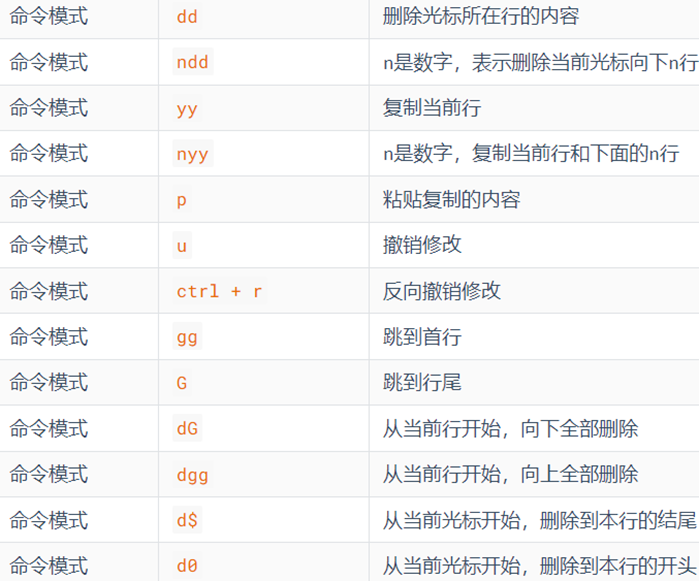
-
bottom line command pattern
Commonly used: :wq, :q!
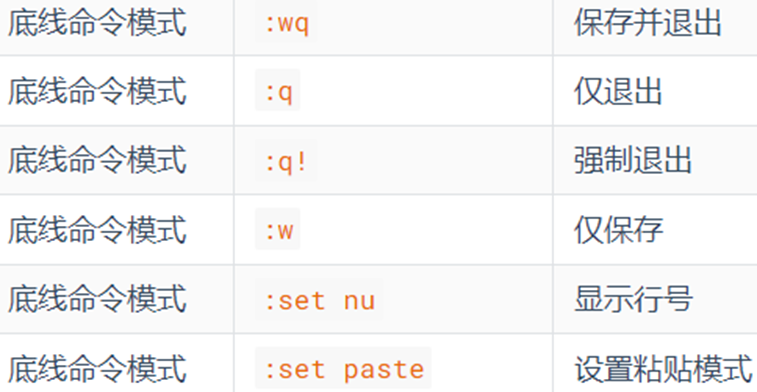
[Chapter Three - Linux Rights Management]
1. root user
-
Whether it is Windows, MacOS, or Linux, it adopts a multi-user management mode for authority management.
-
In the Linux system, the account with the highest authority is named: root (super administrator)
-
The root user has the maximum system operation authority, while the authority of ordinary users is limited in many places.
The permissions of ordinary users are generally unlimited in their HOME directory
Once out of the HOME directory, in most places, ordinary users only have read-only and execute permissions, and no modification permissions
2. Command: su - switch user

-
The su command is a system command for account switching, and its source is the English word: Switch User
-
Options: - Indicates whether to load environment variables after switching users
-
After switching users, you can return to the previous user through the exit command, or you can use the shortcut key: ctrl + d
-
As a normal user, you need to enter a password to switch to other users, such as switching to the root user
Use the root user to switch to other users without a password, you can switch directly
3. Command: sudo - temporary root
- Use the sudo command to authorize ordinary commands and temporarily execute them as root
But not all users have the right to use sudo, we need to configure sudo authentication for ordinary users
-
Switch to the root user, execute the visudo command, and it will be automatically opened through the vi editor: /etc/sudoers
Add at the end of the file:
Username ALL=(ALL) NOPASSWD:ALL
4. User, user group
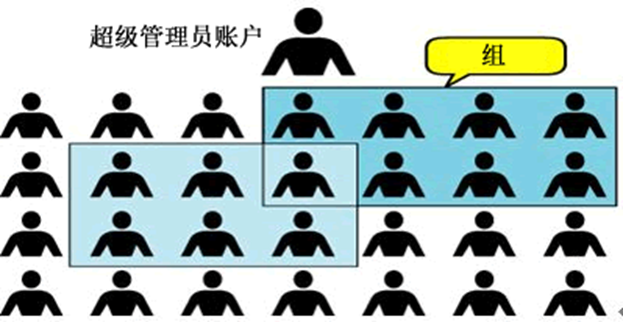
-
In the Linux system, you can:
• Configure multiple users
• Configure multiple user groups
•Users can join multiple user groups
-
There are two levels of control levels for permissions in Linux, namely:
• Permission control for users
• Permission control for user groups
For example, for a file, you can control the user's permissions, and you can also control the permissions of the user group.
5. User group management
创建用户组
groupadd 用户组名
删除用户组
groupdel 用户组名
查看当前系统中有哪些用户组
getent group
6. User Management
创建用户
useradd [-g -d] 用户名
选项:-g指定用户的组,不指定-g,会创建同名组并自动加入
选项:-d指定用户HOME路径,不指定,HOME目录默认在:/home/用户名
删除用户
userdel [-r] 用户名
选项:-r,删除用户的HOME目录,不使用-r,删除用户时,HOME目录保留
查看用户所属组
id [用户名]
参数:用户名,被查看的用户,如果不提供则查看自身
修改用户所属组
usermod -aG 用户组 用户名,将指定用户加入指定用户组
查看当前系统中有哪些用户
getent passwd
5. Linux file permissions
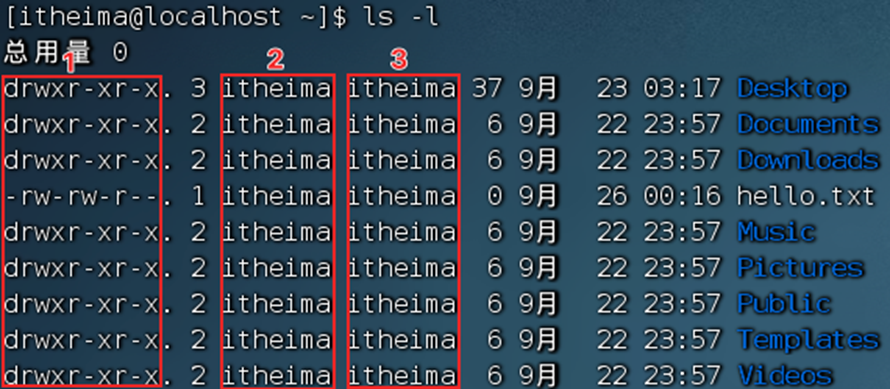
-
Serial number 1, indicating the permission information of files and folders
Sequence number 2, indicating the user to which the file or folder belongs
Serial number 3, indicating the user group to which the file or folder belongs
-
Permission information:
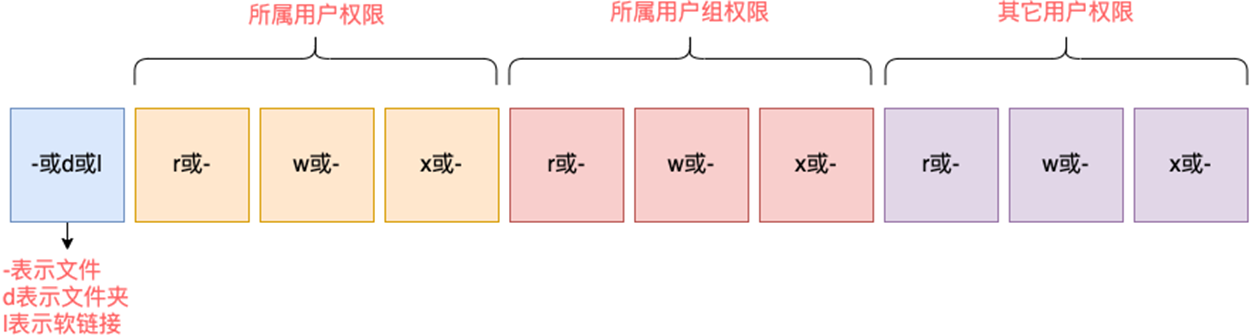
-
For example: drwxr-xr-x means:
This is a folder, the initial letter d means
The permissions of the user (number 2 in the upper right corner) are: r, w, x, rwx
The permissions of the user group (number 3 in the upper right corner) are: r, no w, x, rx (- means no such permission)
The permissions of other users are: with r, without w, with x, rx
-
rwx
r means read permission
w means write permission
x means execute permission
-
for files
r, you can view the contents of the file for the file
w, indicates that the file can be modified for the file
x, for a file indicates that the file can be executed as a program
-
for folder
r, for folders, you can view folder contents, such as ls command
w, for folders, you can: create, delete, rename, etc. in the folder
x, for the folder, means that the working directory can be changed to this folder, that is, cd enters
-
For example, in the / root directory, the root folder, and other users' permissions are -, then the ls and cd commands are not available.
6. Command: chmod - file permission modification

-
Use the chmod command to modify the permission information of files and folders.
-
Option: -R, apply the same operation to all contents of the folder
-
方式1:chmod u=rwx,g=rx,o=x hello.txt
u indicates the user authority to which the user belongs, g indicates the group group authority, and o indicates other user authority
-
Method 2: chmod 751 hello.txt
Remember one: chmod -R 777 file
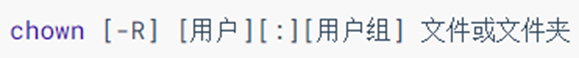
-
Use the chown command to modify the user and user group to which a file or folder belongs
Ordinary users cannot modify their membership to other users or groups, so this command is only applicable to root users
-
Option, -R, same as chmod, apply the same rules to all contents of the folder
option, user, modify user
-
Option, user group, modify the user group to which it belongs
- Used to separate users and user groups
[Chapter 4 - Practical Operation of Linux]
1. Shortcut keys
ctrl + l to clear the screen
-
Through the shortcut key ctrl + l, you can empty the terminal content
-
Or get the same effect by command clear
ctrl + c force stop
- The running of some programs in Linux, if you want to force stop it, you can use the shortcut key ctrl + c
- If the command is entered incorrectly, you can also use the shortcut key ctrl + c to exit the current input and re-enter
ctrl + d to exit or log out
- You can use the shortcut key: ctrl + d to log out of the account
- Or exit some specific program-specific pages. such as python interpreter
ctrl + r history command search history command
-
You can use the history command to view historically entered commands
-
You can pass: ! + prefix to automatically execute the last command matching the prefix
-
You can use the shortcut key: ctrl + r to enter content to match historical commands
If the searched content is what you need, then:
- Enter key can execute directly
- Press the left and right keys on the keyboard to get this command (not execute)
Shortcut keys for cursor movement
-
ctrl + a, jump to the beginning of the command
-
ctrl + e, jump to the end of the command
-
ctrl + left key on the keyboard, jump a word to the left
-
ctrl + right key, jump a word to the right
2. Software installation yum, apt
There are many ways to install software in the operating system, generally divided into:
- Download the installation package and install it yourself, such as the exe of win10.
- Install in the application store of the system, such as the software store of win.
The Linux system also supports these two methods. First of all, let’s learn to use: “App Store” in the Linux command line
- centos application store: yum
- Ubuntu's application store: apt
yum command
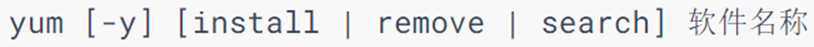
-
yum: RPM package software manager. It is used to automatically install and configure Linux software, and can automatically resolve dependency issues.
-
options:
-y, automatic confirmation, no need to manually confirm the installation or uninstallation process
install: install
remove: uninstall
search: Search for the installation package
The yum command requires root privileges, you can switch to root with su, or use sudo to escalate privileges.
The yum command needs to be connected to the Internet
apt command
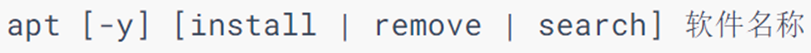
-
The various Linux commands learned earlier are common. But for software installation, CentOS system and Ubuntu use different package managers.
-
CentOS uses yum manager, Ubuntu uses apt manager
-
The usage is the same as that of yum, and root privileges are also required
apt install wget, install wget
apt remove wget, remove wget
apt search wget, search wget
3. Command: systemctl - software control

-
start start
stop off
status view status
enable Turn on the boot automatically
disable Disable autostart at boot
-
Many software (built-in or third-party) of the Linux system support the use of systemctl command control: start, stop, boot automatically
-
There are many built-in services in the system, such as:
NetworkManager, the main network service
network, secondary network service
firewalld, the firewall service
sshd, ssh service (this service is used by FinalShell to log in to Linux remotely)
-
In addition to built-in services, some third-party software can also be controlled by systemctl after installation.
yum install -y ntp, install ntp software
It can be controlled through the ntpd service name and systemctl
yum install -y httpd, install apache server software
It can be controlled through httpd service name and systemctl
Some software is not automatically integrated into systemctl after installation, we can add it manually.
4. Command: ln - create a soft connection
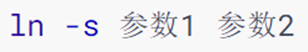
-
Create soft links in the system to link files and folders to other locations. Similar to "Shortcut" in Windows system
-
-s option, create a soft connection
Parameter 1: The file or folder to be linked
Parameter 2: The destination to link to
5. Date, time zone
date command

-
-d Display the date according to the given string, generally used for date calculation
-
Format string: Control the displayed date format through specific string tags
• %Y years
• %y Last two digits of the year (00…99)
• %m months (01…12)
• %d days (01…31)
• %H hours (00…23)
• %M minutes (00…59)
• %S seconds (00…60)
• %s the number of seconds since 1970-01-01 00:00:00 UTC
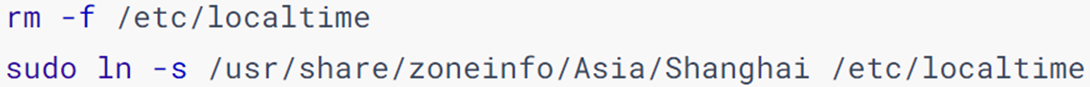
Modify Linux time zone
-
Careful students may find that the date and time viewed through date is inaccurate. This is because: the default time zone of the system is not the East Eighth District of China.
-
Use the root authority to execute the following command to modify the time zone to the East Eighth District time zone
Delete the localtime file that comes with the system, and link the /usr/share/zoneinfo/Asia/Shanghai file to a localtime file
ntp program
-
We can automatically calibrate the system time through the ntp program, and when ntpd is started, it will regularly help us calibrate the system time online.
-
Install ntp: yum -y install ntp
-
Start and set up to start automatically:
•systemctl start ntpd
•systemctl enable ntpd
6. Special IP address
-
Through the command: ifconfig, check the ip address of the machine

-
127.0.0.1, this IP address is used to refer to this machine
-
0.0.0.0, special IP address
can be used to refer to this machine
It can be used in port binding to determine the binding relationship (later explained)
In some IP address restrictions, it means all IPs. For example, if the release rule is set to 0.0.0.0, it means that any IP is allowed to access
7. Host name
-
In addition to the external contact address (IP address), each computer can also have a name, which is called the host name.
Whether it is a Windows or Linux system, you can set the host name for the system
-
Linux system host name
hostname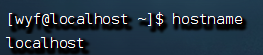
-
modify hostname
hostnamectl set-hostname 主机名
8. Domain name resolution
-
First check the local record (private address book)
Windows看:C:\Windows\System32\drivers\etc\hosts
Linux see: /etc/hosts
-
Reconnect to the DNS server (such as 114.114.114.114, 8.8.8.8, etc.) to inquire
9. Set a fixed IP for the virtual machine
-
Currently, the Linux operating system of our virtual machine obtains its IP address through the DHCP service.
DHCP: Obtain an IP address dynamically, that is, it will be obtained once every time the device is restarted, which may cause frequent changes in the IP address
-
Configuring a fixed IP requires 2 major steps:
1. Configure the IP address gateway and network segment (range of IP address) in VMware Workstation (or Fusion)
2. Manually modify the configuration file in the Linux system and fix the IP
-
virtual machine
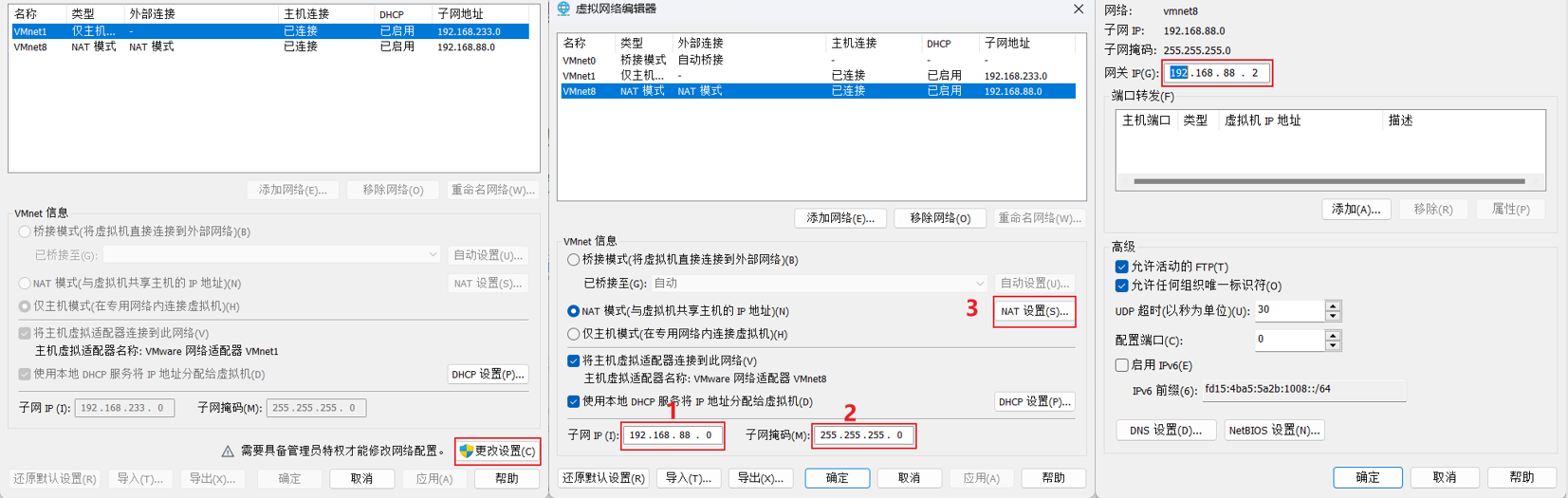
-
Now go to the second step, modify the fixed IP in the Linux system
Use vim to edit the /etc/sysconfig/network-scripts/ifcfg-ens33 file and fill in the following content
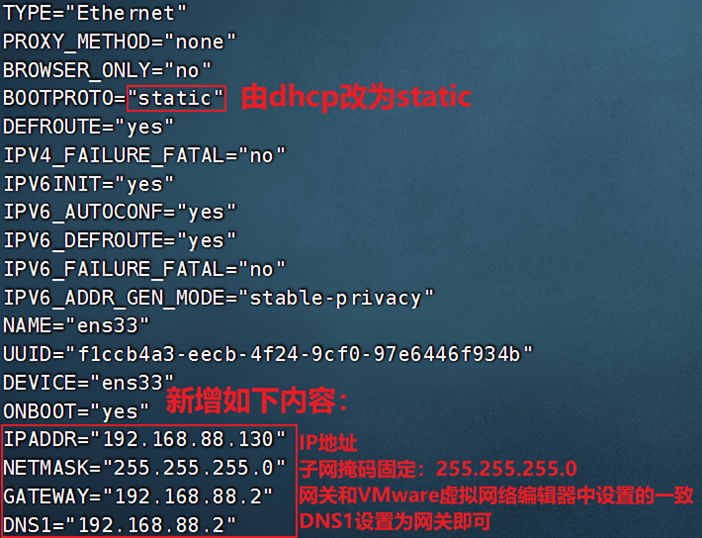
Execute: systemctl restart network to restart the network card, execute ifconfig to see that the ip address is fixed to 192.168.88.130
10. Command: ping - test whether the network is connected
ping [-c num] ip或主机名
-
You can use the ping command to check whether the specified network server is in a state of communication
-
Option: -c, the number of checks, without the -c option, it will continue to check for an infinite number of times
Parameters: ip or hostname, the ip address or hostname address of the server to be checked
11. Command: wget -download
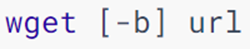
-
wget is a non-interactive file downloader that can download network files from the command line
-
Option: -b, optional, background download, will write the log to the wget-log file in the current working directory
Parameters: url, download link
Note: No matter whether the download is completed or not, the files to be downloaded will be generated. If the download is not completed, please clean up the incomplete and unusable files in time.
12. Command: curl - download
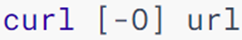
-
curl can send http network requests, which can be used to: download files, obtain information, etc.
-
Option: -O, for downloading files, when the url is a download link, you can use this option to save the file
Parameters: url, the network address to initiate the request
13. What is the port
-
The port is the entrance and exit for the device to communicate with the outside world. Ports can be divided into two types: physical ports and virtual ports
Physical port: It can also be called an interface, which is a visible port, such as USB interface, RJ45 network port, HDMI port, etc.
Virtual port: refers to the port inside the computer, which is invisible and is used for the interaction between the operating system and the outside world
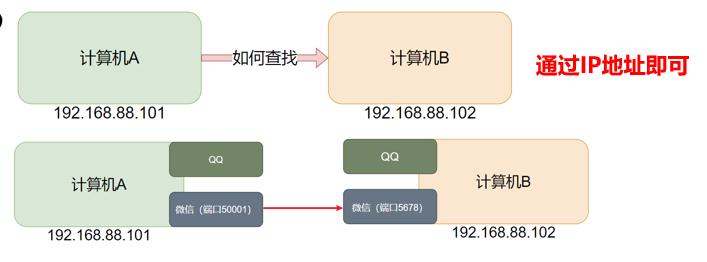
-
The communication between computer programs can only lock the computer through IP, but cannot lock the specific program.
The specific program on the computer can be locked through the port to ensure communication between programs
-
The Linux system can support 65,535 ports, and the more than 60,000 ports are divided into 3 categories for use:
(1) Recognized ports: 1~1023, usually reserved for some system built-in or well-known programs , such as port 22 for SSH service and port 443 for HTTPS service. For non-special needs, do not occupy ports in this range
(2) Registration port: 1024~49151, usually free to use , used to loosely bind some programs\services
(3) Dynamic ports: 49152~65535, usually not fixedly bound to the program , but used for temporary use when the program connects to the external network.
14. Command: nmap - view port occupancy
-
Use the nmap command to check the port usage.
语法:nmap ip地址 如:namp 127.0.0.1 查看本机端口情况 -
Use the netstat command to view the occupancy of the specified port
语法:netstat -anp | grep 端口号 如:netstat -anp | grep 6000
15. What is the process
-
Programs run in the operating system and are managed by the operating system.
In order to manage running programs, each program is registered by the operating system as one of the systems when it is running: a process
And each process will be assigned a unique: process ID (process number)
16. Command: ps - view process
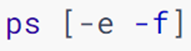
-
Option: -e, show all processes
Option: -f, display all information

View the specified process: ps -ef | grep keyword
17. Command: kill - close the process
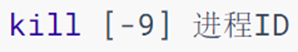
-
In the Windows system, after selecting the process through the task manager, click End Process to close it.
Likewise, in Linux, processes can be shut down with the kill command.
-
Option: -9, means to forcibly close the process. Not using this option will send a signal to the process to ask it to close, but whether to close depends on the processing mechanism of the process itself.
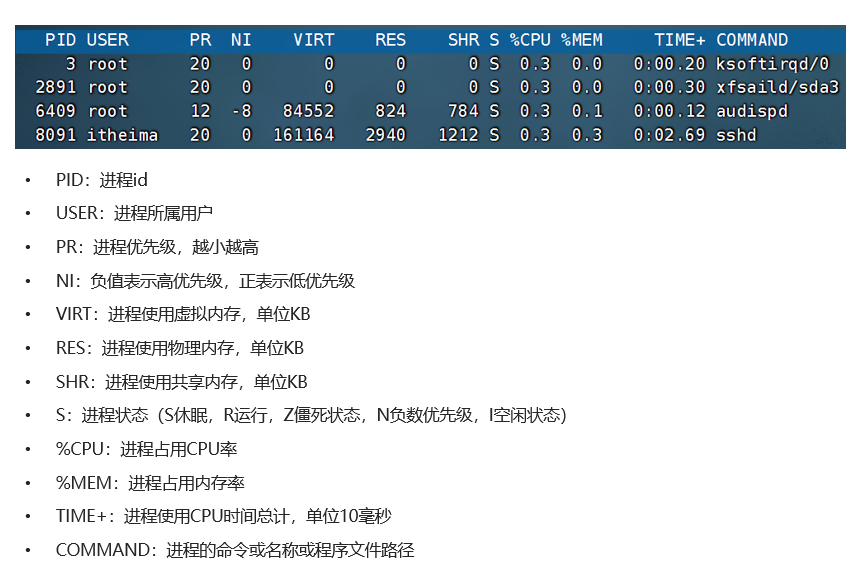
18. Command: top - View system resource usage
19. Command: df - disk information monitoring
df -h
20. $ symbol - value
-
In the Linux system, the $ sign is used to get the value of "variable".
The value of the environment variable can be obtained through the syntax: $environment variable name
For example: echo $PATH
21. What is an environment variable
-
Environment variables are some key information recorded when the operating system (Windows, Linux, Mac) is running to assist the system to run.
-
Execute in the Linux system: env command to view the environment variables recorded in the current system
-
Environment variable is a KeyValue type structure, that is, name and value
env
22. Custom environment variables
-
Linux environment variables can be set by the user, which are divided into:
(1) Temporary setting, syntax: export variable name = variable value
(2) Permanently effective
Effective for the current user, configured in the current user's: ~/.bashrc file
Effective for all users, configured in the system: /etc/profile file
And through the syntax: source configuration file, it will take effect immediately, or log in to FinalShell again to take effect
export variable name = variable value
vim ~/.bashrc
23. What is PATH
-
The PATH item in the environment variable records the search path for the system to execute any command.
-
No matter what the current working directory is, the program /usr/bin/cd can be executed. This is done with the help of the value of the item PATH in the environment variable.
-
Check out: env | grep PATH
echo $PATH
24. Customize the environment variable PATH
临时修改 export PATH=$PATH:要添加的路径
永久修改 将 【export PATH=$PATH:要添加的路径】 添加到用户环境变量文件 或者 系统环境变量文件。
25. Command: rz, sz - shell software upload and download
-
In addition to transferring files through the lower window of FinalShell, you can also transfer files through the rz and sz commands.
The rz and sz commands need to be installed, and can be installed by: yum -y install lrzsz.
-
rz command to upload, syntax: just enter rz directly
-
sz command to download, syntax: sz file to download
Note that the rz and sz commands need terminal software support to run normally
Common terminal software such as FinalShell, SecureCRT, XShell all support this operation
26. Compression format
-
zip format: Linux, Windows, MacOS, commonly used
7zip: commonly used in Windows systems
rar: commonly used in Windows systems
tar: commonly used on Linux and MacOS
gzip: Commonly used on Linux and MacOS
-
In Linux system: tar, gzip, zip these three compression formats
27. Command: tar
-
There are two compression formats commonly used in Linux and Mac systems, and the suffixes are:
.tar, simply assemble the files into a .tar file, and there is not much reduction in the file size, it is just a simple package
.gz, .tar.gz, gzip. • Even if the file is compressed into one file using the gzip compression algorithm, the compressed volume can be greatly reduced

-
-c, create a compressed file, for compressed mode
-v, display the compression and decompression process, used to view the progress
-x, decompression mode
-f, the file to be created, or the file to be decompressed, the -f option must be at the end of all options
-z, gzip mode, normal tarball format without -z
-C, select the decompression destination, used for decompression mode
-
Common combinations for tar compression are:
tar -cvf test.tar 1.txt 2.txt 3.txt 将1.txt 2.txt 3.txt 压缩到test.tar文件内tar -zcvf test.tar.gz 1.txt 2.txt 3.txt 将1.txt 2.txt 3.txt 压缩到test.tar.gz文件内,使用gzip模式Notice:
If the z option is used, it is generally the first option
-f option, must be the last option bit
-
tar decompression
tar -xvf test.tar 解压test.tar,将文件解压至当前目录tar -zxvf test.tar.gz gzip模式解压test.tar.gz,将文件解压至当前目录
28. Command: zip

-
You can use the zip command to compress the file into a zip archive
-
-r, when the folder is compressed, you need to use the -r option, which is consistent with the -r effect of rm, cp and other commands
示例: zip test.zip a.txt b.txt c.txt 将a.txt b.txt c.txt 压缩到test.zip文件内 zip -r test.zip test itheima a.txt 将test、itheima两个文件夹和a.txt文件,压缩到test.zip文件内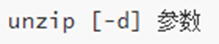
-
Using the unzip command, you can easily decompress the zip archive
-
-d, specify the location to decompress, the same as the -C option of tar
parameter, the zip archive file to be decompressed\
unzip test.zip,将test.zip解压到当前目录 unzip test.zip -d /home/itheima,将test.zip解压到指定文件夹内(/home/itheima)