[-= blog directory=-]
1-Practice goals
1.1- Information collection and vulnerability scanning
Master the most basic skills of information collection and the use of common tools.
1.2 - Practical content
Application of various search techniques
Query of DNS IP registration information
Basic scanning techniques: host discovery, port scanning, OS and service version detection, enumeration of specific services
Vulnerability Scanning: Can scan, read reports, check vulnerability descriptions, and patch vulnerabilities
1.3 - Practical requirements
- basic question answer
- Which organizations are responsible for DNS, IP management.
- What is 3R information.
- Evaluate the accuracy of the scan results.
- Experiment summary and experience
- practice process record
- Report score 1.5 points
- The overall perception of the report is 0.5 points
- Report format range, plus 0.5 for neat layout.
- Add 0 points if the report typesetting is confusing.
- 1 point for writing
- The text content of the report is very comprehensive, and the presentation is clear and accurate, plus 1 point.
- The logic of the report is clear, and 0.5 points are added for a brief introduction of its own operating goals and processes.
- 0 points may be added if the logic of the report is confusing, the expression is unclear or the text has obvious plagiarism
2-Practice process
I feel that the requirements of this blog are repeated with the previous ones...
2.1 Google hacking & ZoomEye
Google hacking:
Many services of Google are unavailable in China, but how can Hackers not have Google! Therefore, it is generally necessary to use the correct posture to open Google, such as VPN and the like, but my VPN has expired... I won't go into details.
First, some common operations:
intext: 把网页中的正文内容中的某个字符做为搜索条件
allintext: 使用方法和intext类似
intitle: 搜索网页标题中是否有我们所要找的字符
cache: 搜索GOOGLE里关于某些内容的缓存,有时候往往能找到一些好东西
define: 搜索某个词的定义
filetype: 搜索制定类型的文件
info: 查找指定站点的一些基本信息
inurl: 搜索我们指定的字符是否存在于URL中.常用于查找通用漏洞、注入点、管理员登录的URL
allinurl:也同INURL类似,可指定多个字符
LINKURL: 例如搜索:INURL:HDU.EDU.CN可以返回所有和HDU.EDU.CN做了链接的URL
site: 搜索指定域名,用于搜集二级域名and the connector:
+ 把GOOGLE可能忽略的字列如查询范围
– 把某个字忽略
~ 同意词
. 单一的通配符
* 通配符,可代表多个字母
“” 精确查询ZoomEye
cyberspace search engine, the search engine's back-end data plan includes two parts:
1. Website component fingerprints: including operating systems, web services, server-side languages, web development frameworks, web applications, front-end libraries and third-party components, etc. .
2. Host device fingerprint: integrated with NMAP large-scale scanning results.
Website: https://www.zoomeye.org/
The cool home page
is mainly used to search the web site and its component information. To test it, we search for keywords: WordPress 8080 http:

334,681,918 search results, just click on one:
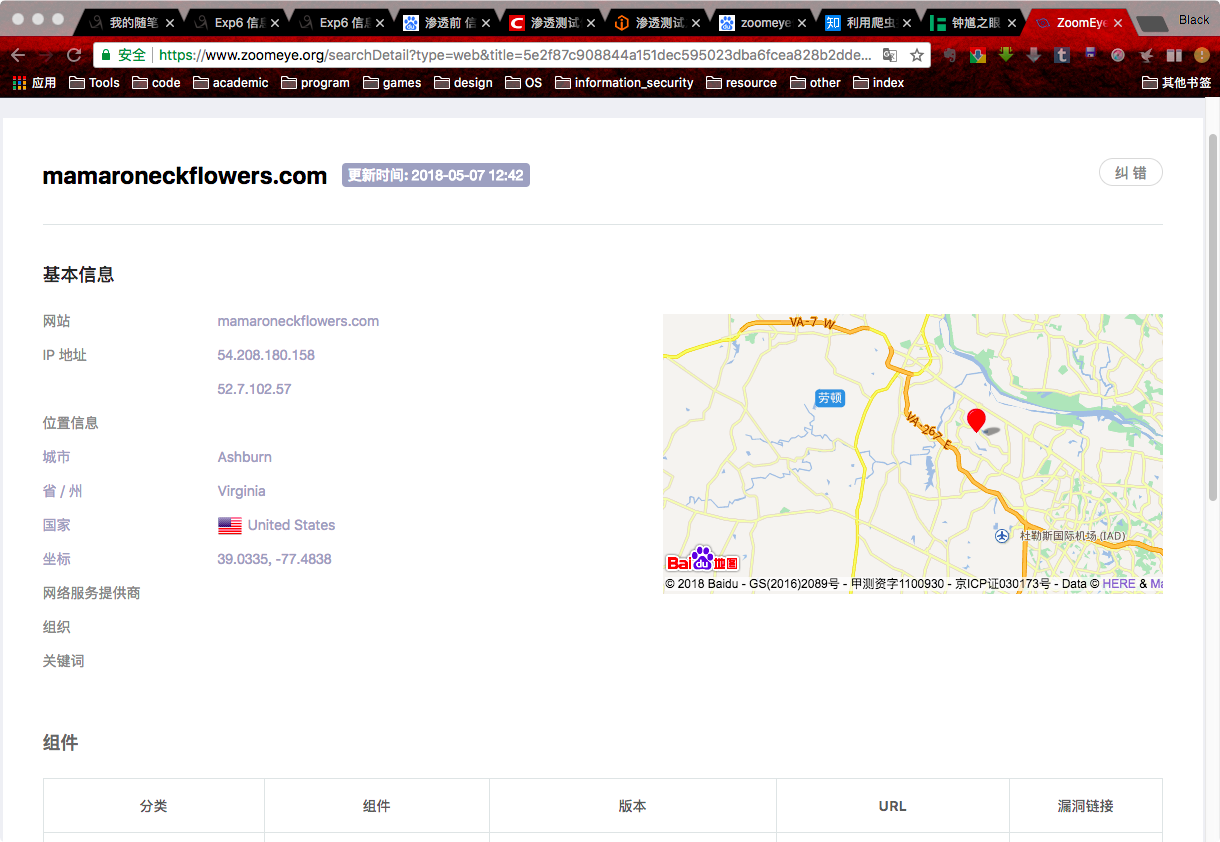
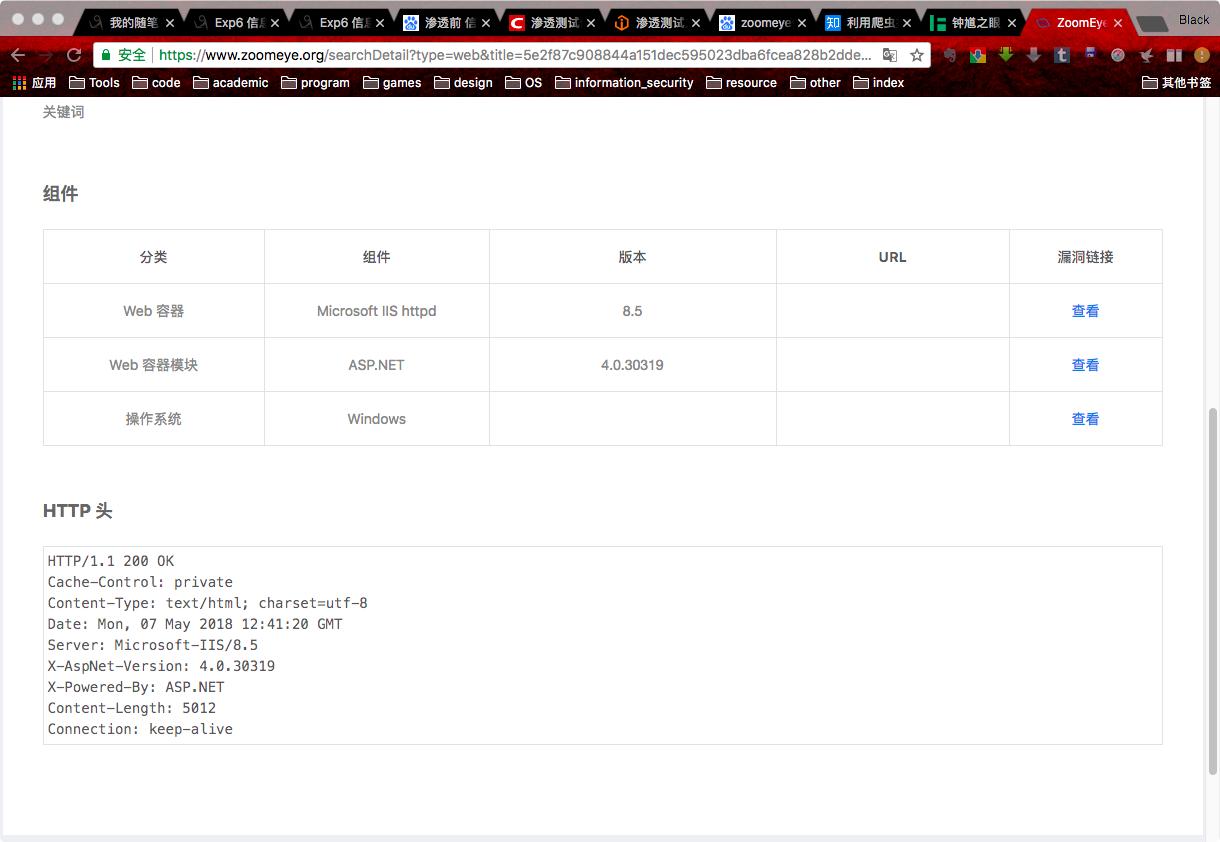
Learned its address, system, http header and other information
2.2 DNS and IP information collection
I once again sacrificed the software I bought for 18 Oceans in the third experiment...Network Utility X!
Well, let me just target mamaroneckflowers.com:
select the Whois option in the Network Utility X option, enter mamaroneckflowers.com, and get the query result:
whois: whois.verisign-grs.com
status: ACTIVE
remarks: Registration information: http://www.verisigninc.com
created: 1985-01-01
changed: 2017-10-05
source: IANA
Domain Name: MAMARONECKFLOWERS.COM
Registry Domain ID: 2005689576_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.namebright.com
Registrar URL: http://www.NameBright.com
Updated Date: 2018-03-14T14:29:33Z
Creation Date: 2016-02-23T19:12:03Z
Registry Expiry Date: 2019-02-23T19:12:03Z
Registrar: DropCatch.com 510 LLC
Registrar IANA ID: 1990
Registrar Abuse Contact Email:
Registrar Abuse Contact Phone:
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Name Server: NS1.NAMEBRIGHTDNS.COM
Name Server: NS2.NAMEBRIGHTDNS.COM
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2018-05-07T13:09:12Z <<<
Domain Name: MamaroneckFlowers.com
Registry Domain ID: 2005689576_DOMAIN_COM-VRSN
Registrar WHOIS server: whois.NameBright.com
Registrar URL: http://www.NameBright.com
Updated Date: 2018-02-09T00:00:00.000Z
Creation Date: 2016-02-23T19:12:03.000Z
Registrar Registration Expiration Date: 2019-02-23T00:00:00.000Z
Registrar: DropCatch.com 510 LLC
Registrar IANA ID: 1990
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.720.496.0020
Domain Status: clientTransferProhibited
Registry Registrant ID:
Registrant Name: marianne c huzar
Registrant Organization:
Registrant Street: 615 east boston post rd
Registrant City: mamaroneck
Registrant State/Province: NY
Registrant Postal Code: 10543
Registrant Country: US
Registrant Phone: +1.9146982585
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: [email protected]
Registry Admin ID:
Admin Name: marianne c huzar
Admin Organization:
Admin Street: 615 east boston post rd
Admin City: mamaroneck
Admin State/Province: NY
Admin Postal Code: 10543
Admin Country: US
Admin Phone: +1.9146982585
Admin Phone Ext:
Admin Fax:
Admin Fax Ext:
Admin Email: [email protected]
Registry Tech ID:
Tech Name: marianne c huzar
Tech Organization:
Tech Street: 615 east boston post rd
Tech City: mamaroneck
Tech State/Province: NY
Tech Postal Code: 10543
Tech Country: US
Tech Phone: +1.9146982585
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: [email protected]
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System:
http://wdprs.internic.net
--- Last update of WHOIS database: 2018-05-07T12:36:56.853Z ---
Domain Name: MamaroneckFlowers.com
Registry Domain ID: 2005689576_DOMAIN_COM-VRSN
Registrar WHOIS server: whois.NameBright.com
Registrar URL: http://www.NameBright.com
Updated Date: 2018-02-09T00:00:00.000Z
Creation Date: 2016-02-23T19:12:03.000Z
Registrar Registration Expiration Date: 2019-02-23T00:00:00.000Z
Registrar: DropCatch.com 510 LLC
Registrar IANA ID: 1990
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.720.496.0020
Domain Status: clientTransferProhibited
Registry Registrant ID:
Registrant Name: marianne c huzar
Registrant Organization:
Registrant Street: 615 east boston post rd
Registrant City: mamaroneck
Registrant State/Province: NY
Registrant Postal Code: 10543
Registrant Country: US
Registrant Phone: +1.9146982585
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: [email protected]
Registry Admin ID:
Admin Name: marianne c huzar
Admin Organization:
Admin Street: 615 east boston post rd
Admin City: mamaroneck
Admin State/Province: NY
Admin Postal Code: 10543
Admin Country: US
Admin Phone: +1.9146982585
Admin Phone Ext:
Admin Fax:
Admin Fax Ext:
Admin Email: [email protected]
Registry Tech ID:
Tech Name: marianne c huzar
Tech Organization:
Tech Street: 615 east boston post rd
Tech City: mamaroneck
Tech State/Province: NY
Tech Postal Code: 10543
Tech Country: US
Tech Phone: +1.9146982585
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: [email protected]
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System:
http://wdprs.internic.net
--- Last update of WHOIS database: 2018-05-07T12:36:56.853Z ---
Dig again:
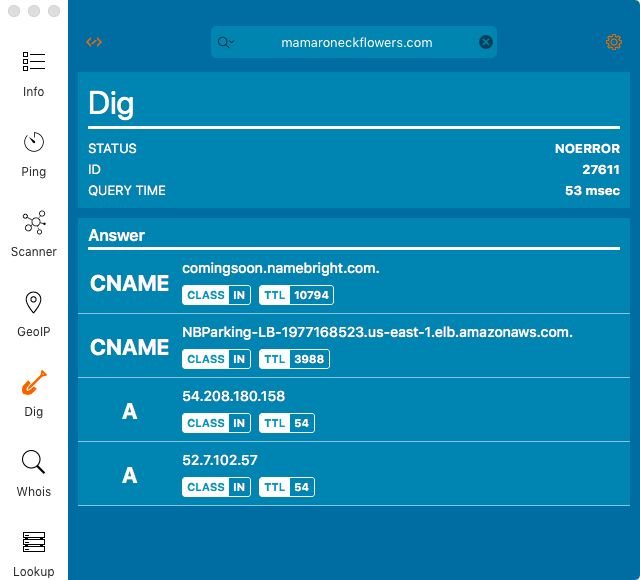
the information that appears is the same as zoomeye.
### The following is the collection of DNS information:
Open Kali, you can use the host command to search for the DNS server query:
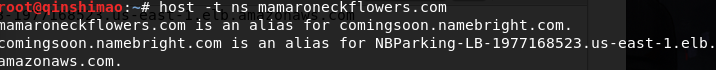
In fact, this information has been found in the whois part above. Let's check out the others below:
Query a record:
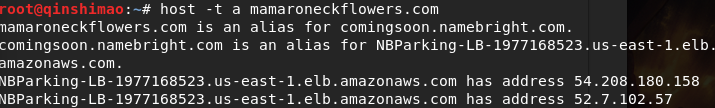
A (Address) record is used to specify the IP address record corresponding to the host name (or domain name). Users can point the website server under the domain name to their own web server. You can also set subdomains of the domain name. Generally speaking, the A record is the IP of the server, and the domain name binding A record is to tell the DNS, when you enter the domain name, it will guide you to the server corresponding to the A record set in the DNS.
It found its alias and two IP addresses.
query mx records
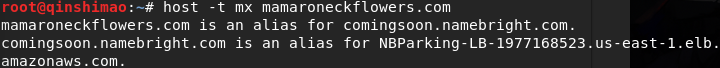
MX records are also called mail routing records. Users can point the mail server under the domain name to their own mail server, and then they can control all mailbox settings by themselves. You need to fill in the IP address of the server online, and then all the mails under the domain name can be transferred to the corresponding set mail server.
Domain name enumeration
After obtaining the main domain name information, if we can obtain all sub-domain name information through the main domain name, we can query the corresponding host IP through the sub-domain name, so that we can obtain a relatively complete information.
You can use the fierse tool integrated in Kali to query the domain name list:
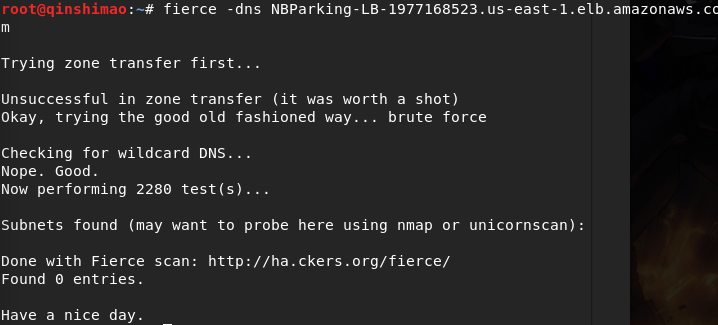
unfortunately, nothing was found. If you need to find more detailed, you can use an enumeration tool with a dictionary (if it is not too troublesome), such as dnsdict6, dnsenum, dnsmap, here Not one by one explained.
In fact, the dig tool in Kali is also a very powerful tool for collecting IP and DNS information. I will not introduce it in detail here because of the limited space. I will have the opportunity to open a single in the future~
2.3 The protagonist metasploit debuts
Metasploit provides us with powerful information collection help through auxiliary and nmap. Here are some simple operations!
- Auxiliary /arp-sweep

Damn, I was shocked . As shown
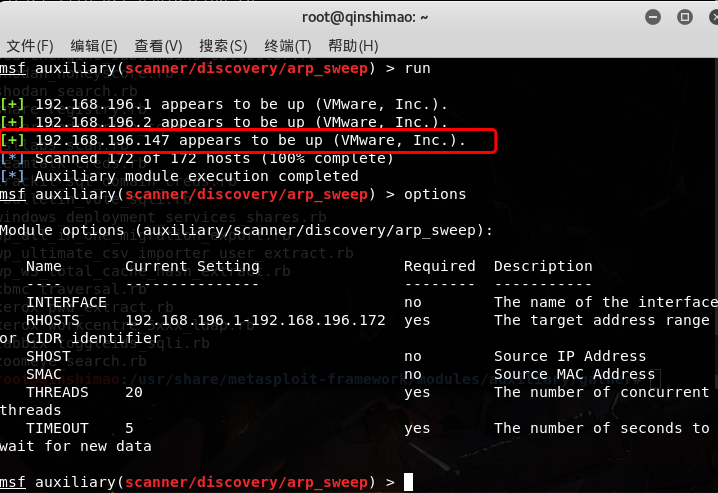
in the figure, I found the friend 192.168.196.147. - nmap is shown

in the figure, and I also found the friend 192.168.196.147. I have
determined the IP. Then I will learn more about the details. According to the routine, the port scanning portscan starts: - Auxiliary /portscan/SYN After
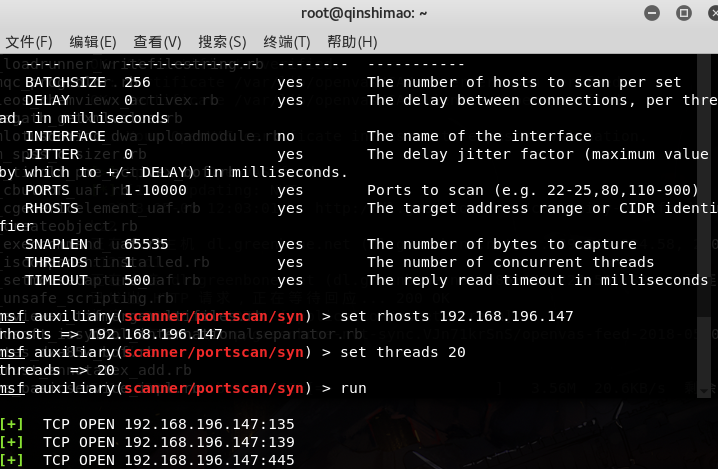
I played the king, it swept out three TCP ports (and deliberately raised the thread to 20) - nmap
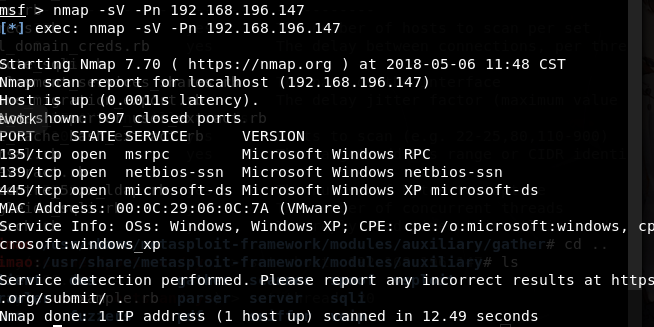
is worthy of being an old-fashioned scanning tool. It is very efficient and can be done in 12 seconds.
2.4 Vulnerability scanning openvas
In fact, I originally wanted to write openvas, but something went wrong during the installation:
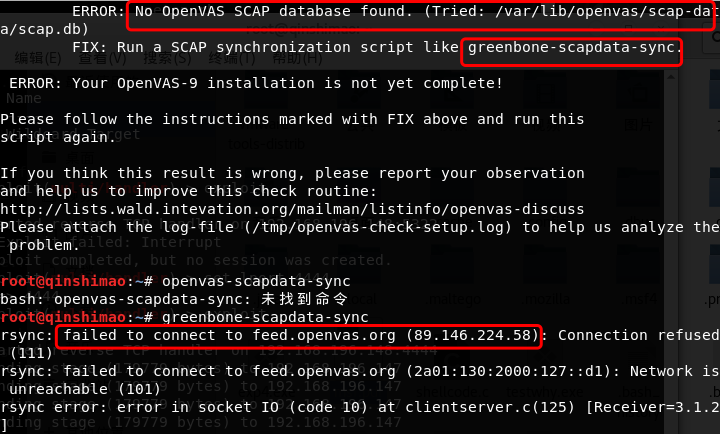
(The actual measurement on Kali in 2016.08.21 seems to be very different from the current situation...)
To be finished...
2.5 Answers to basic questions
- Which organizations are responsible for DNS, IP management.
The top management is ICANN, and the ICANN Council is the core authority of ICANN. It establishes three supporting organizations: the
Address Supporting Organization (ASO) is responsible for the management of the IP address system.
The Domain Name Supporting Organization (DNSO) is responsible for the management of the Domain Name System (DNS) on the Internet.
The Protocol Supporting Organization (PSO) is responsible for the assignment of unique parameters involving Internet Protocol.
5 regional registries:
ARIN is mainly responsible for North America business
RIPE is mainly responsible for Europe business
APNIC is mainly responsible for Asia Pacific business
LACNIC is mainly responsible for Latin America and America business
AfriNIC is mainly responsible for Africa business. - What is 3R information.
- Registrant: the registrant
- Registrar: Registrar
- Registry: Official Registry
- Evaluate the accuracy of the scan results.
The scan results given by OpenVAS are very detailed. Although there is no specific CVE number, they all give information on the servers with vulnerabilities, which are quite detailed. The penetration testing work provides certain ideas.
3- Reference materials & practical experience
Practical experience
I feel that the recent blogs have a certain connection, mainly focusing on information collection.