This is my 382th original article. It records every bit of the network engineer industry and makes friends with people in the IT industry.
At nine o'clock in the morning, I came to the 14F of Xi'an No.2 Long-distance Telecom Building with a very excited mood. I was quite nervous when facing the customer for the first time!
Try to take a few deep breaths, calm down, and start discussing the equipment and requirements involved in today's project with the customer.
Gradually, I and my colleagues entered the state of work
At this time, I realized that there were no other random thoughts in my mind, and some were merely engineering considerations.
Therefore, in the face of the first practice, when you are nervous, communicate with customers more and understand their needs in detail
Careful recording is more necessary than a better plan.
Next, the customer took out the equipment needed for this project—juniper igs1000 series firewall
We first quickly read the technical manual of the equipment, this is very necessary
Then began to assemble equipment with colleagues
Be careful and accurate in this process, because according to experience
In many cases, the instability of the equipment is caused by accidental damage during the assembly process.

After assembling, I started to debug the device, because it is my first time to contact the firewall of juniper
The company has a more experienced colleague as the main force, and I will study and test alongside.
Faced with customer requirements, we soon made the corresponding settings
Because the customer requires that the disconnection time must be guaranteed within 5 minutes, so we are too late to put it on the shelf
Fearing that there will be detailed errors that we did not notice, I simulated it several times in a virtual environment, no problem!
ok we enter the telecommunications room on the 14th floor and start connecting equipment.
As soon as I entered, I was shocked by the entire cabinet of servers, routers, switches, and firewalls!

I imagine that one day I will be able to debug all the equipment inside.
With temptation to come to the cabinet to connect the equipment
Just when we were about to disconnect the network connection, we found that the fiber that comes with Juniper could not be connected to the switch
At that time, the big guy was shocked. If the network was disconnected at that time, the amount of customer loss could not be estimated!
So we contacted the company and equipment manufacturers and telecom engineers
Finally, after waiting for more than 2 hours, we have a suitable fiber optic cable. After that, the network was disconnected, the connection was overdone, and the data was connected.
At this time, we let out a sigh of relief, and then waited for customers from Beijing to log in to the firewall
There was a problem, the other party could not log in, we started debugging

Time after time, one by one, one by one, and finally landed at 5 pm
In fact, it’s just because the other party doesn’t have a java virtual machine installed.
It’s such a small place that makes us all stumped. For such a problem
I believe there will be many such situations in future projects
All we can do is prepare the relevant equipment before departure
When facing customers, accurately understand customer needs, be careful in the process, and sum up experience in practice!
When we came out of the telecom building, the sky was full of stars! The mood is relaxed, the body is exhausted!
Juniper isg1000 firewall debugging process:
Requirements: There are three deployment modes for firewalls: NAT mode, routing mode, or transparent mode. It is required to be adjusted to transparent mode to realize remote management of the firewall.
1. Log in to the firewall
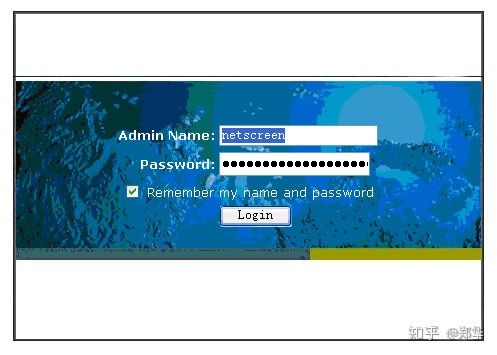
Managed through a web browser. It is recommended to use IE browser for login management (IE browser supports java language), you need to know the management IP address of the corresponding port of the firewall (default is 192.168.1.1); use a network cable to connect the local network card to the mgt port of the firewall. Username: netscreen Password: netscreen
Command line mode: supports two command line login management modes (same as cisco) through the console port, HyperTerminal connection and Telnet firewall management IP address connection.
After logging in by web, the interface is as follows (a part of it is intercepted)
Open the configuration, select admin and select permit ip
Add a manageable remote IP address or network segment
Open network, select zone, open interface list
Click edit to edit the type field is layer2 is
Transparent mode, tick the option of WebUI ssh ssl telnet
In this way, you can use these methods to log in to the firewall and put
Ethernet2/2 is set as an untrusted zone to connect to the external network, Ethernet2/1
Set up as a trusted zone to connect to the intranet, the configuration is as follows
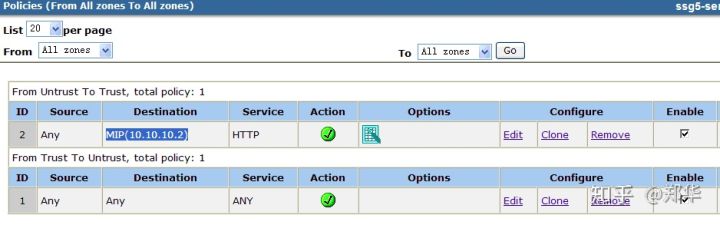
Open policies to edit access control
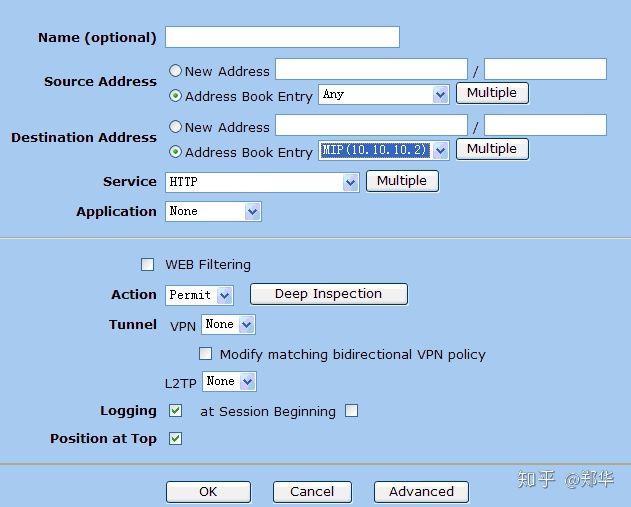
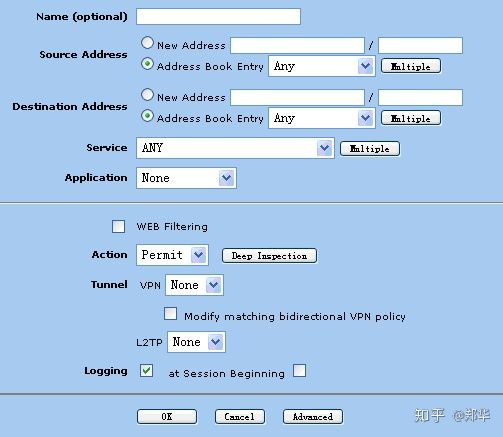
Name IP/Netmask Zone Type Link Configure
Ethernet1/0 0.0.0.0/0 null down edit
Ethernet1/1 0.0.0.0/0 null down edit
Ethernet1/2 0.0.0.0/0 null down edit
Ethernet1/3 0.0.0.0/0 null down edit
Ethernet2/1 0.0.0.0/0 v1-trust Layer2 up edit
Ethernet2/2 0.0.0.0/0 v1-untrust Layer2 up edit
mgt 192.168.1.1/24 up edit
Vlan1 10.0.0.1/24 Vlan Layer2 up edit