China Consumer News reported (Reporter Nie Guochun) "Let go of the code in your hands and be careful of getting caught!" Recently, this kind of joke is popular among programmers. The reason is that many companies involving crawling technology have recently been investigated by the police.

According to a recent press briefing by the Ministry of Public Security, since September 1 this year, cybersecurity and criminal investigation departments from all over the country have collected and eliminated 147 "routine loan" gangs, arrested 1,531 suspects, and adopted criminal coercive measures for 798, and eliminated A group of technical service providers and data support service providers that provide services for criminal acts have been established. Among them, in the "7.30" routine loan project in Qitaihe, Heilongjiang, the responsible persons of the crawler business of companies such as Xinyan Technology, Juxinli, Tongdun Technology, and Moxie Technology were all arrested by the police.
In this era, data has become a more valuable asset than gold and oil. With the maturity of the big data technology system, big data technology is being widely used in various industries. However, with big data technology, everyone may also become a victim.
More than 5,000 pieces of face information are sold for only 10 yuan
Relying on face recognition technology, face information is bound to important application scenarios such as authentication and payment, and thus becomes personal information as important as fingerprints and ID cards. Once stolen illegally, the consequences would be disastrous.
On October 28, due to opposition to the use of face recognition to enter the zoo, Guo Bing, a distinguished associate professor of Zhejiang Sci-Tech University, sued Hangzhou Wildlife World to the People’s Court of Fuyang District, Hangzhou City. The first case". On November 1, the Fuyang District Court formally accepted the case.
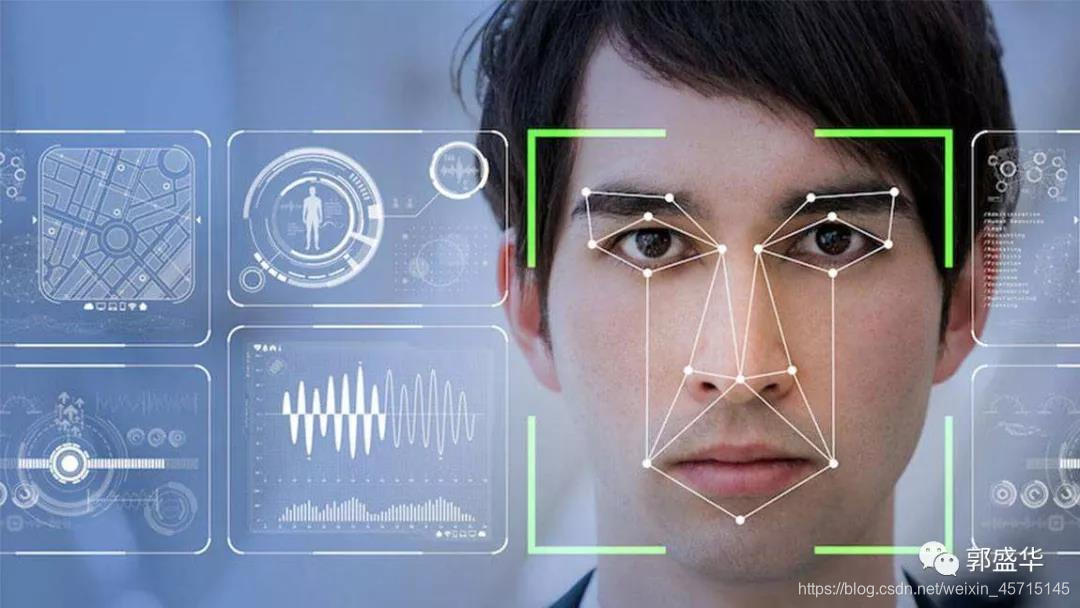
Guo Bing believes that the park will collect his facial features and other personal biometric information for facial recognition. This type of information is personally sensitive. Once it is leaked, illegally provided or abused, it will easily harm consumers, including the plaintiff. Personal and property safety.
Guo Bing's worries are not unfounded. CCTV reported on November 30 that a product named "Face Related Algorithm Training Data Set" was found on an APP platform with a price tag of 10 yuan. According to the product introduction, this data set contains more than 5,000 face photos, many of which are photos of a person's face with different expressions. On Taobao, there are also some shops that openly sell face information, the price is mostly 5 photos per person, 1 yuan per person. Reporters searched on multiple platforms such as IT communities and online shopping malls and found that there are many face photos available for free download or paid purchase. The payment amount is set by the post publisher, mostly around 10 to 20 yuan.
The reporter browsed multiple face download posts and found that the publicly downloadable photos in the IT community were marked as photos of foreign volunteers provided by foreign research institutions, some photos were crawled from websites, and some were screenshots from WeChat Moments. . Basically, none of the photos being sold has been explicitly authorized.
Broken crawler technology
"Crawler technology is a tool, but when used by people with bad intentions, big problems may occur." IT programmer Xiao Zhang said with emotion.
It is understood that in the early days of crawler technology, the crawled party not only did not resist, but was very welcome to be crawled by search engines, because only then could it be searched, and it would bring more visits and corresponding advertising revenue. After the rise of the big data industry, the value of a single piece of information is limited, but the value is great when aggregated together. Therefore, some companies use web crawlers to move a large number of content on other websites, cut the head and tail, and put it on their own website. Both parties This creates a conflict of interest. In the era of mobile Internet, crawler technologies are mainly divided into two categories, one is public crawlers, and the other is authorized crawlers. The former refers to only crawling publicly released data information, such as corporate business information, public social platform information, etc.; while authorized crawlers refer to requiring users to authorize in advance, thereby crawling users' personal address books, mailboxes, and judicial information , APP usage, e-commerce platform and other private data.
In Xiao Zhang’s view, the use of crawling technology in the online world is quite common, but European and American countries can only crawl public information or personal information authorized by users through crawling technology, and many apps in my country use crawling technology to excessively collect user privacy Information behavior. For example, a user authorizes an APP to only access information such as website pages or emails related to credit card bills in the mailbox that he has browsed, and mobile desktop APP download software, but in the actual operation, these APPs use crawler technology to capture the user's consumption on these websites Behavior, private email content, personal whereabouts and address location and other private information. "The use of web crawler technology has a special situation, that is, large companies do not do evil themselves, but help evil and provide services for some serious problem industries or scenarios." Wang Xinrui, senior partner of Beijing Anli Law Firm Said that many companies notified by the Ministry of Public Security are related to cash loans, routine loans, violent collections, and "714" antiaircraft gun loans. Big data companies provide them with risk control services, which may not be subjectively malicious, but it is easy to be taken away by customers' improper needs, and even play a role in "empowering evildoers".
Responsible application technology At
present, the domestic Internet industry has weak privacy protection and data security loopholes. New technologies such as crawling technology and face recognition technology are often intertwined with the illegal and abuse of information sources. Does this mean that new technologies will definitely spawn a large number of black and gray industrial chains?
Attorney Wang Xinrui believes that when technology has just emerged and the industry does not know how to apply it, there is nothing wrong with adopting a "technology neutrality" attitude. But once the technology becomes mature and deeply integrated with the industry, those who master the technology must be wary of whether the technology will be used by the black industry, whether it will become an accomplice, or even directly become the core technology of the black industry. All kinds of "cutting leeks" and infringing on legitimate rights and interests will inevitably lead to a large number of risks as time accumulates. Law enforcement will inevitably take action, and at this time "helpers" will also pay a price.

"Technology is not right or wrong, but people have good and evil." Zhang Xinbao, a professor at Renmin University of China Law School, said that technology neutrality should be a basic judgment. On this basis, analyze the main purpose of the technology application. If it is only used for crimes, such as gambling technology, copy number technology, etc., then it should be restricted. If technology can serve the economy and society, or it can be used by bad guys, it should be regulated. Therefore, it is necessary to strengthen the protection of personal sensitive and private information, and strengthen the regulation of the commercial use of personal general information and the use of the state for public management purposes (such as brushing the face to check in hotels, etc.) to achieve a balance between the interests of individuals, information operators and the state .
Some pictures are from the Internet, please contact to delete if infringement
Source: CNN
collation: Eastern Alliance