
Link to Alibaba Cloud Security Month Special Page: https://developer.aliyun.com/topic/securityapril
Internet of Things under the new trend of infrastructure
Recently, the Politburo Standing Committee meeting proposed to accelerate the development of 5G, data centers, artificial intelligence, Internet of Things and other new infrastructure construction progress. Eight provinces including Beijing, Shanghai, and Jiangsu announced nearly 34 trillion yuan in investment. The great attention and support of the state has become the core propeller of economic transformation and upgrading and future economic growth.
As a "powerhouse" for the country's long-term rapid development of science and technology and economy, the new infrastructure also conforms to the concept of "science and technology rejuvenating the country". The new infrastructure covers 5G base station construction, new energy vehicle charging piles, big data centers, artificial intelligence, industrial Internet, UHV, intercity and urban rail transportation, and involves seven major areas and related industrial chains. The Internet of Things technology has been deeply integrated into each module involved in the new infrastructure and integrated with it. In the future iteration of the development of the information foundation, the Internet of Things technology will be "ubiquitous."

According to the statistics of the Global System for Mobile Communications (GSMA), the number of IoT devices in the world has grown rapidly from 2010 to 2018, with a compound growth rate of nearly 21%. According to the GSMA's prediction, the number of global Internet of Things devices (including cellular and non-cellular) will reach 25.2 billion in 2025. At the end of 2019, China has become the world's largest Internet of Things market, with 960 million of the world's 1.5 billion cellular network connected devices from China, accounting for 64%.
IoT security becomes the fastest track for new infrastructure
Under the new national infrastructure, the already rapid development of the Internet of Things industry has encountered a golden opportunity for development. With the increasing number of Internet of Things devices, security has become an urgent issue. The huge device base, coupled with widespread fragmentation and software and hardware vulnerabilities, has made the Internet of Things equipment extremely low-cost, tending to scale and developing rapidly, and security threats have become the norm in the Internet of Things field. In 2018, global security spending reached 96 billion U.S. dollars, an increase of 8% from the 89 billion U.S. dollars in 2017. In 2019, the number of Chinese Internet of Things security incidents increased from 7648 in 2018 to 56121, an increase of nearly six times year-on-year.
How to securely connect and manage massive devices, how to break islands and make full use of data resources and terminal resources, how to ensure the security of the Internet of Things, how to ensure the reliability of intelligent terminals, how to identify and deal with malicious *** are all new infrastructures The issues that must be considered in the planning and construction of the Internet of Things and later operations, otherwise it will be difficult to maximize the effectiveness of the new infrastructure.
A series of IoT security policies and regulations issued in the past two years, such as the Cyber Security Law, Password Law, and Cyber Security Level Protection 2.0, etc., extend from the enterprise to the person in charge of operations, from traditional cyber security to IoT security. Actively bring the best interpretation of the determination of animal networking technology to improve safety capabilities in all directions.

Driven by the "new infrastructure", the Internet of Things security industry will also escort the vigorous development of China's digital industry. For enterprises, with independent and controllable technology as the core, combined with information security technology, vigorously develop Internet of Things security is one of the fastest and most complete tracks for the "new infrastructure".
Alibaba Cloud IoT new track, creating a new infrastructure security base
In March 2018, Alibaba entered the IoT in an all-round way, and IoT became the fifth major track of the Alibaba Group after e-commerce, finance, logistics, and cloud computing.
Alibaba Cloud IoT is positioned as the builder of the Internet of Things infrastructure and plans to connect 10 billion devices within 5 years. Behind this number, there is strong support for security. Alibaba Cloud Link Security IoT security platform has achieved high security, hundreds of millions of connections, and millions of concurrency capabilities. It has continuously promoted the security, maturity, and business processes of IoT technology, and constantly strengthened the new infrastructure security base.
Since the development of the Internet of Things industry, four core security pain points have been formed:
- Fragmentation, high security access requirements
- Long link and lack of overall security solution
- Lack of talents makes it difficult to operate safely
- Many scenes and uneven security standards
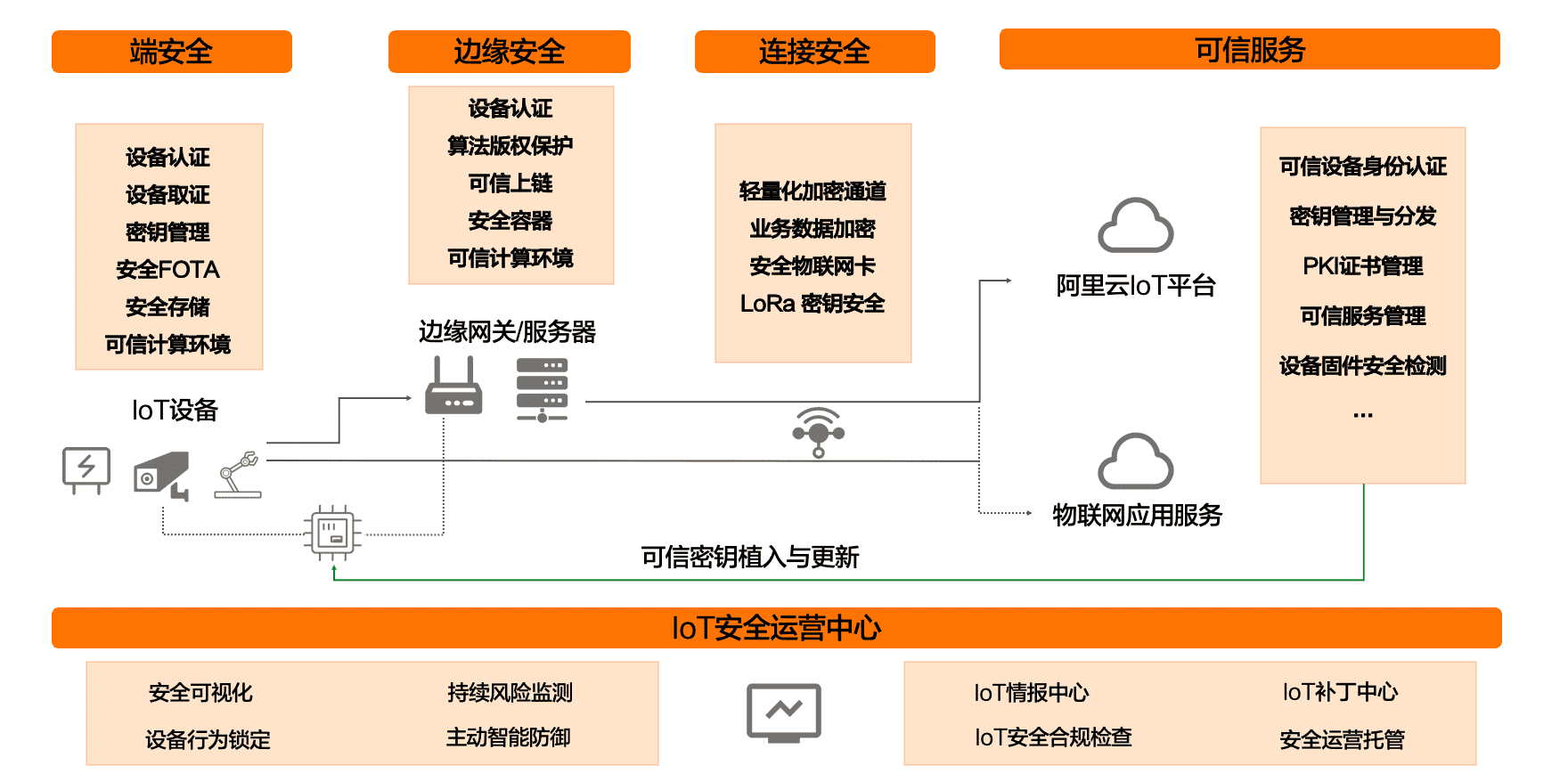
Faced with these pain points, Alibaba Cloud IoT has built a powerful Link Security IoT security platform. The platform defaults security genes throughout the entire life cycle of the development, testing, production, access and operation of IoT devices, and provides a series of lightweight and easy-to-adapt security products and solutions for IoT endogenous security. The core of the platform focuses on device security, edge security, access security, and trusted data collection on the cloud, and based on blockchain technology to ensure the reliable flow of data.

Link ID² device identity authentication is one of the core security measures in the process of device access to the platform. The device identity information of ID² has the characteristics of non-tampering, non-counterfeiting, and the world's only security. Protection of identity information. ID² provides a cloud root of trust for IoT devices. Based on the root of trust, it provides trusted services for upper-layer services, ensuring the legality of IoT devices and data security from the source. Up to now, the number of ID² certifications has exceeded 1.1 billion, and the peak value can reach 8000 times per second. ID² provides a variety of identity key algorithms including the national secret algorithm. In 2019, the commercial password application security assessment will be completed and the basic compliance conclusion will be obtained.
Link TEE is an important security guarantee on the end of the platform. It is based on hardware-isolated security technology, provides a secure computing environment for private data and sensitive code, and supports the development and expansion of secure applications. It is an important cornerstone for ensuring a trusted Internet of Things. Link TEE is also the only product in the world that has obtained the global configuration organization GlobalPlatform TEE full configuration safety certification.
Link SOC is the core component of platform linkage devices and systems. It provides one-stop, panoramic visualization of device security management. It dynamically monitors the security implementation status and operational risk status of connected IoT devices, helping companies identify and eliminate IoT systems. Potential security threats greatly reduce the period from "incident occurrence-monitoring abnormalities-response and disposal", timely contain the spread of risks, control the scope of risk events on business, and provide stable availability guarantee for business systems. At the same time, SOC provides value-added security operations and custody services to reduce the input of corporate security personnel.
At the same time, the platform helps IoT equipment and data upgrade from security to credibility by combining IoT security with blockchain and other technologies, enabling IoT technology to monitor manufacturing, supply chain management, off-site supervision, circulation anti-counterfeiting and quality traceability Such scenarios provide innovative solutions to facilitate the application of IoT technologies through security and credibility, accurately digitize the physical world, provide practical security guarantees for IoT data, and empower the industry.
The platform has been widely used in many fields such as single products, industry, real estate, parks and cities. It has opened up the ecological chain links such as chips, modules, equipment, software services, communication operations, testing and certification, and combined Taobao, Tmall, Alibaba Cloud Market and other sales resources build a complete ecological closed loop. Up to now, it has docked more than 70 types of security carrier hardware, cooperated with more than 100 manufacturers' projects, and shipped more than 40 million security terminals.
Alibaba Cloud actively responded to the national call. The platform took the lead in passing the Internet of Things security assessment based on Cyber Security Level Protection 2.0 (Level 3) and became the first IoT security service platform in China to pass the assessment. At the same time, the platform is to provide a one-stop isoguaranty solution to help companies quickly achieve isoguaranty security compliance. Alibaba Cloud's confidence and determination in the field of Internet of Things security is enough to verify the truth.
Alibaba Cloud is sinking the capabilities of the cloud seamlessly, creating a full range of security protection capabilities while realizing the intelligence of everything, and helping the "new infrastructure" security construction.